Everyone who drives should know how to use a car jack in case of a flat tire or blowout. Check your owner's manual to find out where your car jack and spare tire are located. In most cases, they are somewhere in the rear of the car. The video shows us how to use a telescoping jack, though the more common type of jack requires a scissor motion to raise the car and lifts from the side rail. The telescoping jack lifts from the axel and to raise the jack you need to insert the rod into the hole n...

This easy to follow silent and accurate video will guide you quickly and easily through what you'll need, (like a Power Supply, a sound system that has a Subwoofer Pre-output and a High Input adapter, which may already come with your amp.) First learn what colored wires should be connected to simulate your PC starting. Then connect the amp to the power supply to simulate the car Head-Unit starting. Once the power issues are handled, the video assists you with connecting your audio input. It i...

Awakening the sixth chakra – known as the third eye – also awakens your sixth sense, and unlocks psychic potential. In this tutorial, learn how to harness your spirituality and get in touch with your third eye.

This video describes how to take apart a first generation iPod. To open the iPod, the video recommends using a putty knife or similar flat tool to gently ply open the casing. The presenter recommends being especially careful if this is the first time opening the casing. Once you have the first side open slightly wide work your way around the casing, making sure the entire casing is spread evenly around. Once all the sides are loose, the back casing just slides off. There are then two componen...

This feature also comes with Windows 7. Right click on desktop then click "Personalize". You can see the numbers of themes for example choose Nature theme and click "Desktop Background". You can see the some pictures and a tick mark on the corner of the pictures which tells these pictures are the part of my slide show. Also you can set the time for new pictures to come.

This how-to video is about how to repair a leaky faucet. One of the most common problems with the faucet is the replacement of the rubber washer, which is located on the bottom of the valve unit. First, stop the water supply by turning off the stop valve at the bottom of the sink. Then, turn on the faucet until the water stops flowing. Next, remove the handle. To do this, we first need to remove the decorative cap using a screw driver or sharp pointed knife to expose the screw. Then, remove t...

Changing a toilet is really not the dirty and difficult job that you would imagine. Start by turning the water off using the valve that is located on the wall. Empty the tank by flushing the toilet and holding up the drain valve. Soak up the excess water with a sponge. Disconnect the water line and loosen the bolts that hold the toilet down. Cut through the caulk seal at the bottom of the toilet. Remove the toilet and the wax ring that is around the opening of the drain. Remove the wax ring a...

If you're interested in upgrading your RAM for the Samsung NC20 netbook, this video shows you how. This simple to follow video gives you a quick and simple way to make changes to your netbook. The only tool that is required is a small screwdriver.

Fight Enchant Angels, Trash Mobs, and Fortitudo in the Xbox 360 game Bayonetta. In Chapter 2 - Vigrid, City of Deja Vu, it's time to shine as one mean mama-san. In the first battle you can walk on walls. To get back to the floor quickly press down on the left stick while jumping. Because this fight takes place on six different surfaces it can sometimes be hard to locate Jeanne (your opponent). If you don't know where she is, just shoot her. Your guns don't do any damage, but you will see wher...

Mission 10 on the Sony PSP takes you through finding the ship for Kyrenia to deliver Alexander's message to the crewmen without being discovered. The path to the Crewman is relatively free of guards if you stick to rooftops as much as possible. Then, leap down to the docks below. The manifest is located on the big ship docked at the Port. Take the ladder down to the deck below and follow your nose to the manifest. With it now in your possession, take it to Alexander. For more info, watch the ...

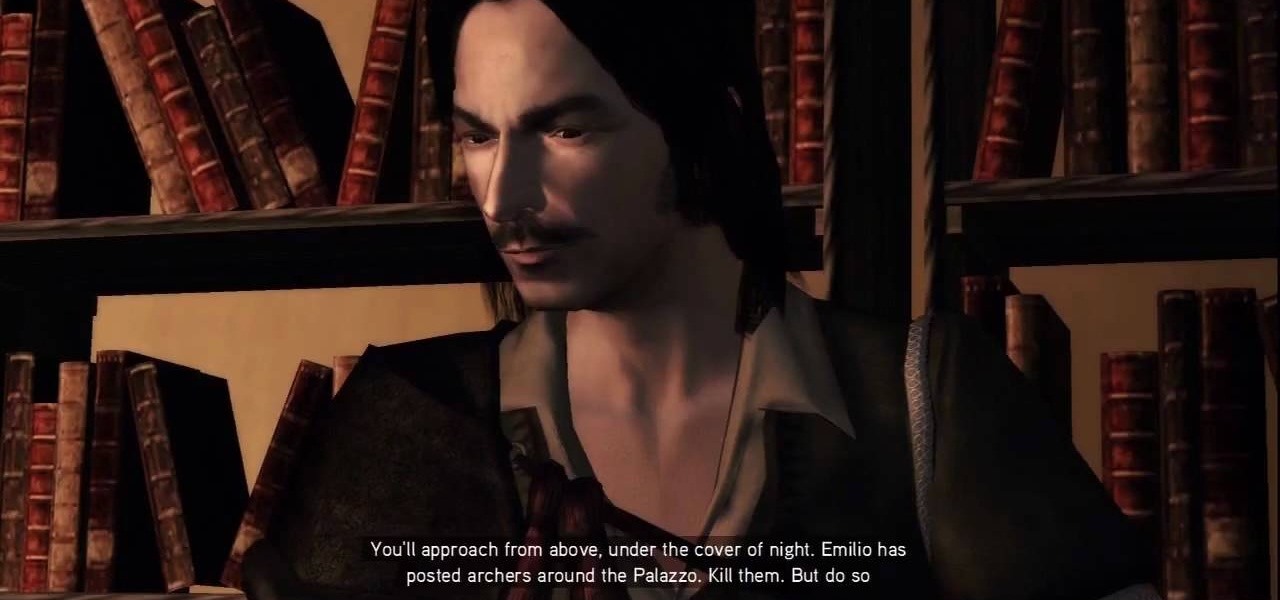
Everything Must Go: It's the truth. It's time to say goodbye to everything. See Antonio again and be ready for a quick time event during the cut scene after you accept the mission. The first order of business is to kill five archers surrounding the building in which Emilio is camping. Take to the rooftops and locate the guards. Once you've gotten near them, you can't let them get too far away from you. Kill all of 'em, being as stealthy or as brazen as you like. Personally, we like brazen.

Family Heirloom: Find the precious family peice passed down generation to generation. Go back to Giovanni's room and use eagle vision to locate the hidden door. Okay, it's not really very hidden. Open the door and step into the secret room. Open up the chest inside to get a snazzy new outfit, plus a useful sword.

Ever wanted to find out who stole the cookie from the cookie jar? Take a page from crime scene investigators and get the proof you need.

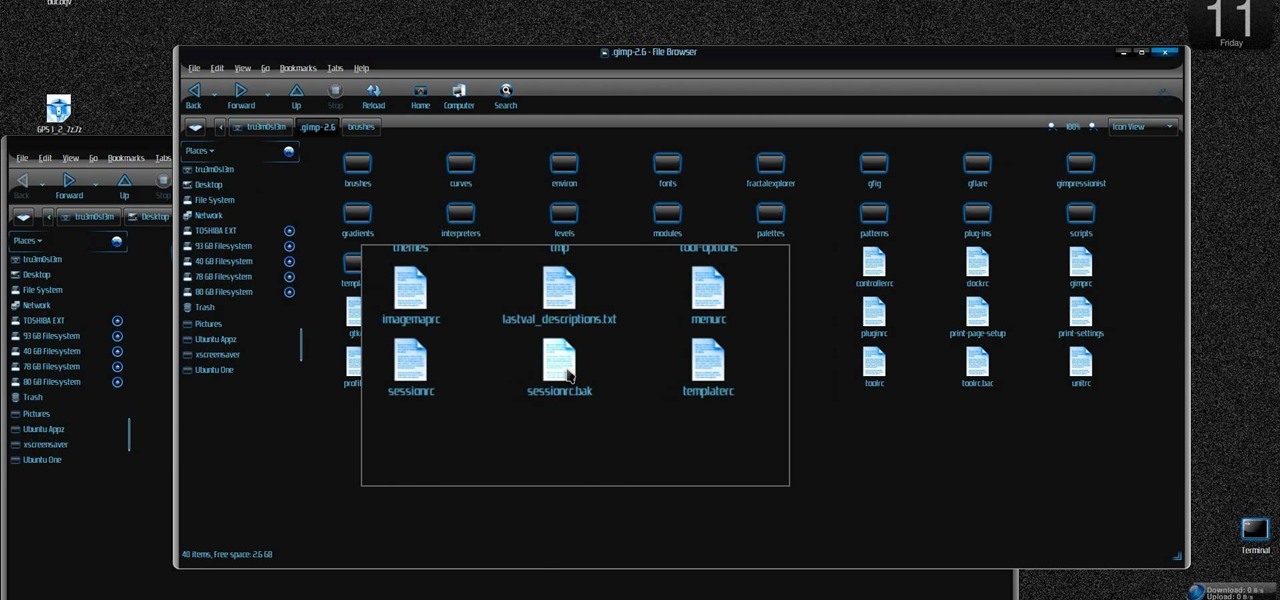
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install additional brushes for GIMP on Ubuntu Linux.

This is a 3 part video walkthrough of Chapter 6, "Getting Off the Athena" in the action first-person shooter, The Chronicles of Riddick: Assault on Dark Athena for the Xbox 360.

Learn how to tune your guitar using a Korg tuning box. To accurately tune your guitar, you will first need to locate a correctly tuned instrument to provide a reference note. A piano or electric keyboard will work if one is available. (You have to know the names of the keys to use this method.) Otherwise, you can use the fret board below to get your reference note. We'll use the "Low E" for your reference note.

Monitor Trap: Difficulty level 5 1) Cut a metal coat hanger, and bend it into shape. 2) Use cardboard to construct the launching platform for the paper hole punches. 3) Fasten the mousetrap to the back of the monitor and then tie the fishing line to the mouse cord. 4) Delicately pour a small pile of paper hole punches onto the platform.

Learn how to do single leg power hops with a stepback lunge twist while holding a weight. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do alternate lunges and scissor switches. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do side to side pop push ups across a step. Presented by Real Jock Gay Fitness Health & Life.

Who says Vegas is only good for gambling? This is a level-by-level walkthrough (on realistic difficulty) of Rainbow Six: Vegas for the PS3, XBox 360, and PC. A helpful voiceover commentary is included.

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

Apple's latest updates to its operating systems add another security feature to its Find My service, so you have an even better chance at locating your lost iPhone, iPad, or Mac should it ever happen. As long as you have the option enabled, you can leverage other Apple users' devices to find yours on the map.

When it comes to customizing Android, there's no better way to make it your own than by installing a custom ROM. You gain new features that were not accessible on the stock firmware that came with the phone, and you get complete control over how your system looks and feels. But there's definitely a learning curve.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

Improved security options in iOS 12 provide you with automatic password suggestions, a way to find and change weak passwords, auto-filling of 2FA codes, and Siri integration. Most of these apply to iCloud Keychain, but Apple hasn't forgotten about users of third-party password managers; In iOS 12, you can use 1Password, LastPass, and others with the AutoFill feature in websites and apps.

One of the primary marketing tactics used by Magic Leap in promoting the Magic Leap One was selling early adopters on the "magic" contained within the device. On Thursday, some of that magic was uncovered as the Magic Leap One was completely disassembled by repair engineers, revealing the delicate innards of the device and detailing how it delivers its augmented reality experiences.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

Getting new loot can be challenging in Fortnite Battle Royale. Whether you decide to pay for the Battle Pass or stick with the Free Pass, you still need to put in 50+ hours to unlock all the items. For those of us with Amazon Prime subscriptions, there's another way to unlock free items, and it won't cost you an extra dime.

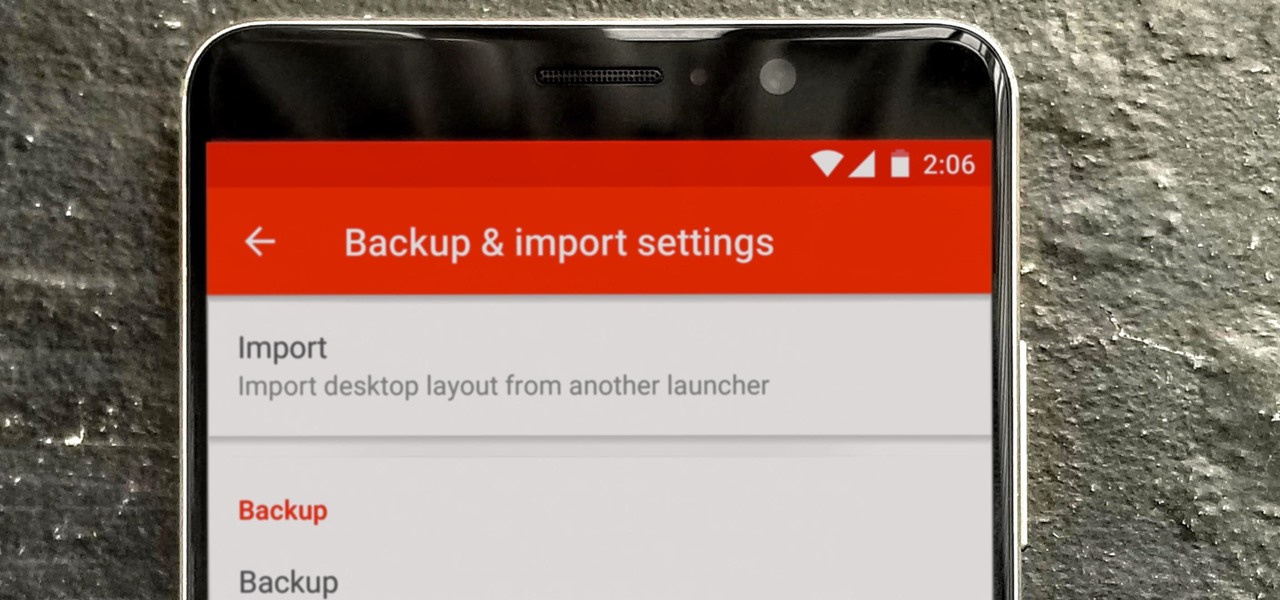
Over the years, Nova Launcher has widened its audience. No longer is it simply a tool to return your home screen to a more stock look. With Nova, you gain customization tweaks and functionality unavailable with the stock launcher. One example of this is all of the cool stuff you can do to organize your app drawer.

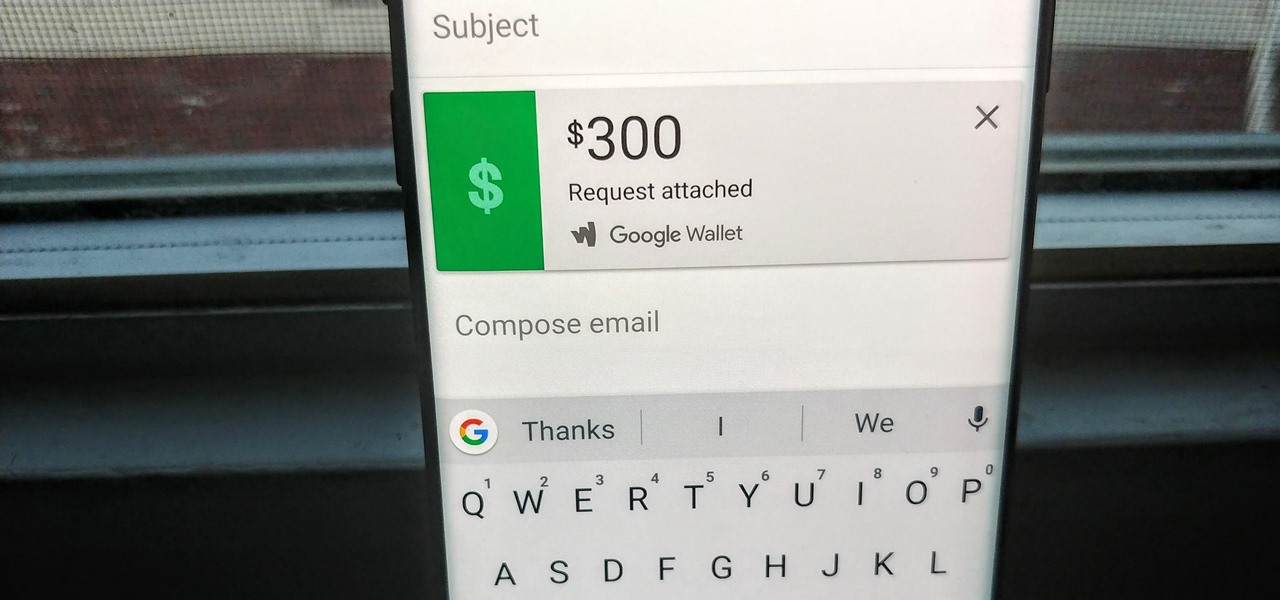
Since its debut in 2004, Gmail has become the go-to email service for the internet at large. Over 1.2 billion people use it, so Google has wisely continued to add features that address the needs and wants of its diverse user base. For US and UK users, one of these new features is the ability to transfer money.

So you spent all day customizing your phone. You tinkered with all the settings, searched the web high and low for the perfect wallpaper, and found an ideal icon pack to complement the color scheme. You go to sleep, proud of the work you accomplished when the unspeakable happens — your phone freezes and tech support is telling you to do a factory reset to fix the problem.

Wherever there are people, the party is sure to follow. Well, a party of microbes, at least. That is what scientists at NASA's Jet Propulsion Laboratory have found after a 30-day microbial observation of the inflatable lunar/Mars analog habitat (IMAH).

Devastating and deadly, land mines are a persistent threat in many areas of the world. Funding to clear regions of land mines has been decreasing, but new research may offer a less dangerous method of locating hidden, underground explosives by using glowing bacteria.

Hello there! This will probably be the final tutorial on functions where we will be looking over a method called pass by reference. This technique allows us to modify large amounts of data without the overhead and return multiple values. Let's go!

Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear and focused when reading the following article because it may prove to be confusing. Also, if you do not understand something, please verify all of your doubts, otherwise you may not completely understand when we touch on...

In this tutorial I will be explaining the purpose of unique encryption/decryption scripts ( I will be referring to these at "UEDS" for this tutorial). Then, I will show you how to make one. Finally I will talk about the downsides to the method I use. I will also provide links explaining the concepts and algorithms used in encryption to anyone who wants to see what is going on under the hood.

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

Back in August, Google introduced Android Device Manager. This new service allowed you to locate, lock, or wipe a lost or stolen Android device from either a companion app or a web interface. Effectively, this is the "kill switch" that legislators are clamoring for.