Wegmans recently partnered with Instacart, an online grocery-delivery app, to bring your groceries right to you. The collaboration will begin in the suburbs around Washington, DC, and Wegmans plans to expand to other areas later on.

You seriously won't even recognize Twitter after this. Twitter has launched a major redesign, their first in years and it seems the app is finally starting to listen to what users are looking for — starting to being the keywords.

If you've ever wanted to turn your favorite GIF into a live wallpaper for your iPhone or even just make it a 3D Touch-friendly Live Photo that you can share, there's a super simple way to do so.

Buying a smartphone used is an excellent way to save money, but those savings come with a risk that your seller isn't as forthcoming as they claim. You don't want to end up buying a stolen smartphone because it might not work correctly ... and, you know, it's wrong. Luckily, there's an easy way to check if the phone you're about to buy is legit.
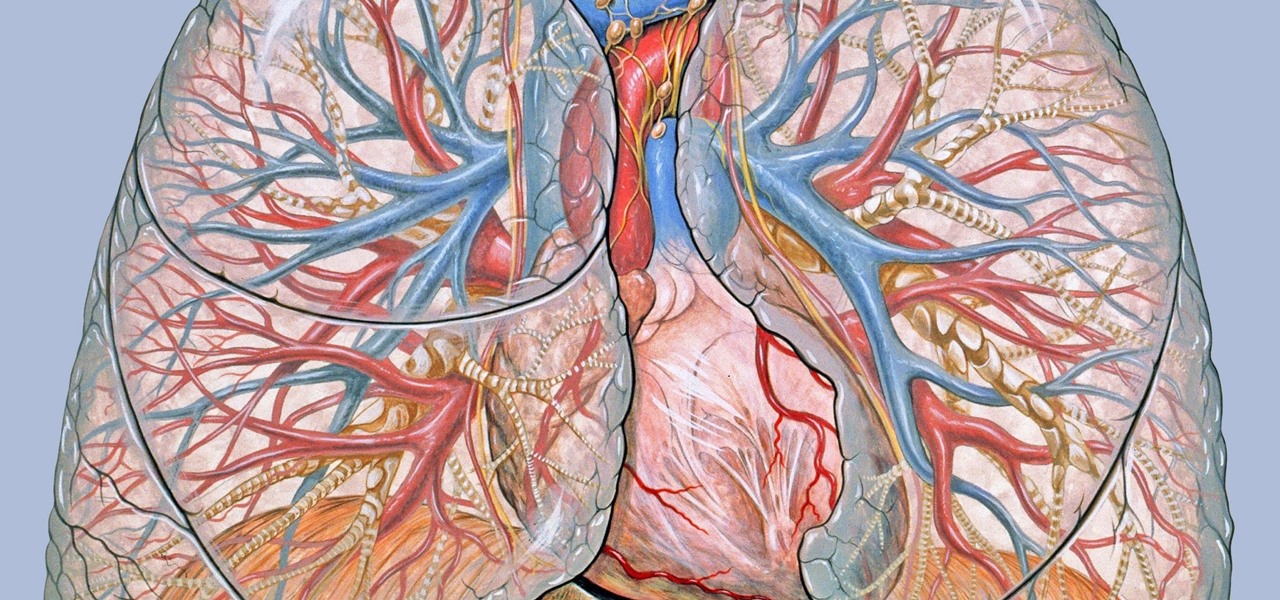
The body's usual response to a bacterial infection in the blood — called sepsis — takes time. It requires a carefully orchestrated sequence of events that gets the body's immune system ramped up to deal with the invading bacteria.

Final Fantasy XV, the latest release in the long-running Final Fantasy franchise, has been a massive success, shipping around 6 million copies worldwide in less than two months. Final Fantasy XV: A New Empire is a mobile game based off this popular console iteration, and has surfaced in New Zealand for download.

Fans of fighting game series such as Street Fighter and Mortal Kombat are in for a treat! Skullgirls has entered the crowded field of the mobile fighting genre and has touched down in the form of a soft launch for iOS devices, which is now available for download in Canada and the Philippines. But don't let this limited release stop you from trying Skullgirls out, as it's still possible to acquire this little gem with a little finagling.

Tom Clancy games, like Rainbow Six and Ghost Recon: Wildlands, are famous for their realistic and immersive gameplay that focuses on covert, low-intensity warfare. Ubisoft now appears to be testing the overcrowded waters of mobile gaming with the release of ShadowBreak, and has soft released the game for both iOS and Android in Canada for further development, which means that with a little tinkering, you can play ShadowBreak in any country.

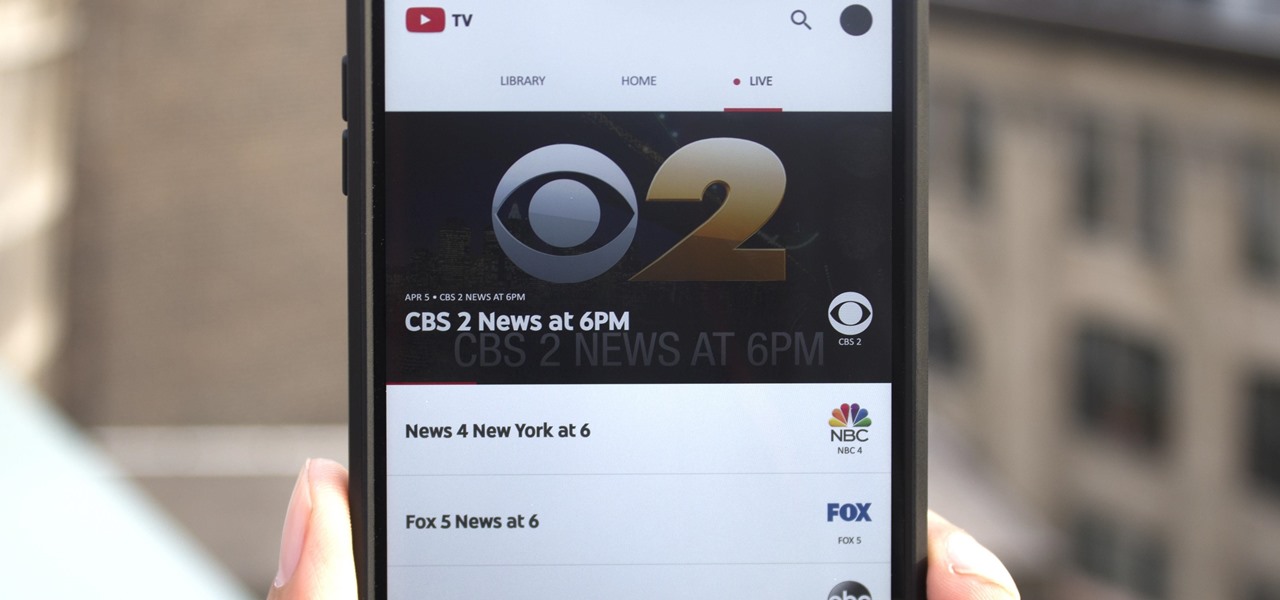
As you may have heard by now, YouTube has launched its own live streaming TV bundle available for users in the select markets of New York, Los Angeles, the Bay Area, Chicago, and Philadelphia. A subscription to the new streaming YouTube TV bundle costs $35 a month, but the service is drawing in users by offering a free 30-day trial.

Chrysaor, a zero-day spyware believed to have been created by the Israeli "cyber war" group NSO, is an even greater threat to Android phones than it ever was to iOS.

The first public beta of Android O, (most likely to be called "Android 8.0 Oreo") was released on May 17, bringing tons of new features and goodies for Android enthusiasts with supported devices. However, not all of Android O's features were available to try out right off the bat. Possibly the single biggest feature announced during the developer preview of Android O, Picture-in-Picture mode, is nowhere to be seen.

Google Maps beta version 9.49 now allows users to manually save their parking location, and includes weather forecasts in mass transit, according to Android Police. There's also a notification toggle for mass transit station notifications.

If you're one who likes to tinker with Android, TWRP is the first thing you should install. It replaces your phone's stock recovery mode interface and adds over a dozen advanced features to your device—most notably, the ability to flash ZIPs that can modify practically every aspect of your operating system. It's certainly one of the most powerful tools available for Android, and there's simply nothing capable of replacing it.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

Copying files from a computer to your Android device has always been pretty straightforward—just connect the two devices with a USB cable, open your desktop file explorer, then move the files over. But what if you didn't need any wires at all?

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

It's always a pain to make sure you have enough storage on your smartphone. Pictures and videos occupy a lot of space, so your music library has to take a back seat—otherwise, you might see that pesky "Storage Full" notification at any time.

We're on the verge of an amazing evolution of technology where we can work and play in virtual worlds that merge with our own—or let us escape into our imaginations entirely. But creating virtual, mixed, and augmented reality experiences requires resources and hardware that not everyone has access to. If you want to build something awesome with the Microsoft HoloLens (or one of the other awesome platforms), we want to help you do just that.

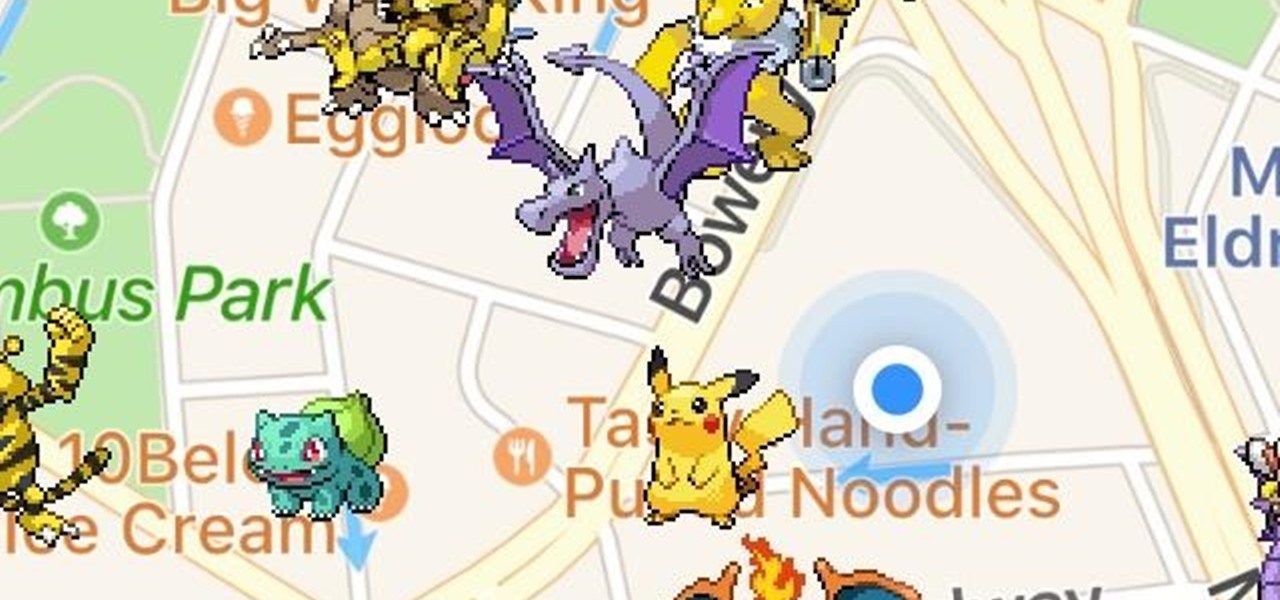
The only way to know which Pokémon are in your area in Pokémon GO is the cryptic "nearby" list, which sometimes doesn't work—and also doesn't tell you which direction to head off to hunt that Pokémon you're looking for.

This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

Nobody's supposed to know where the Batcave is, but as most everyone thought, Batman's underground lair lied below the estate of his secret identity, Bruce Wayne, in Gotham City.

In this series you will learn how to use PHP to perform attacks, gather information, and setup backdoors. Along with performing attacks you will learn how to protect yourself from them. In this part you will learn about PHP as well as install Apache and PHP. What you'll need for this series

Hello again, folks! I'm back with another (final) guide on runtime crypters which is an extension on my previous runtime crypter guide. If you have not read it yet, I highly recommend that you do since the fundamental theory of the PE format. Again, this will be a Windows-specific guide, so I'll repeat this: If you're a hater and cringe at the slightest sound of Microsoft's grotesque baby, feel free to close this tab, delete your history, exit your browser, pour some oil onto your machine and...

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

SentrySafe puts all sorts of measures in place to protect your valuables and important documents. This particular SentrySafe has an electronic lock, four 1-inch bolts to keep the door firmly in place, pry-resistant hinges, and it's able to withstand drops of up to 15 feet. That all sounds great, until you find out that you can open this safe—and pretty much every safe like it—in a matter of seconds using only a magnet. A rare earth magnet, to be precise.

Hello fellow Nullbytiens, I'm Washu, a long time commenter but first time poster. Today we'll be making an IRC bot, if you haven't seen OTW's post about the new IRC channel I would encourage you to go check it out. He does a good job at explaining what IRC is and how to get set up.

Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, this is an excellent way to learn how to hack Wordpress, Joomla, and Dupral plus many more!

Some of the best images I've seen were shared via Snapchat, but once they're expired, they're gone forever, with no way to view them again unless I want to take a screenshot. But that will, of course, alert the sender.

If your smartphone is ever lost or stolen, it's a terrible experience. If you file a police report, chances are the responding officer will need your device's IMEI or MEID number if you want to stand a chance of getting it back. Same goes for making an insurance claim on a lost or broken phone, so it's definitely important to have this unique identifier handy.

Hello! This is my first post on this awesome website! I know that Windows exploits are less common than the more advanced hacks, but I found something I deem pretty cool and figured why not share it with you all. Alright, enough about me, lets begin.

Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.

I have been on Null Byte for a long time, a very long time and. I havent always had an account here, ive like many of you also have, been looking and decided to make a profile to contribute.

BlackBerry has yet to find a home amongst the iPhone and popular Android phones, with sales plummeting over the last couple years, but this might be a thing of the past thanks to their latest device, the BlackBerry Priv. It has decent numbers so far and was even sold out on Amazon shortly after its initial release.

It might be difficult to admit, but a lot of us are probably guilty of lurking on Instagram profiles, whether it be an ex you've been keeping tabs on or someone cute you literally just met.

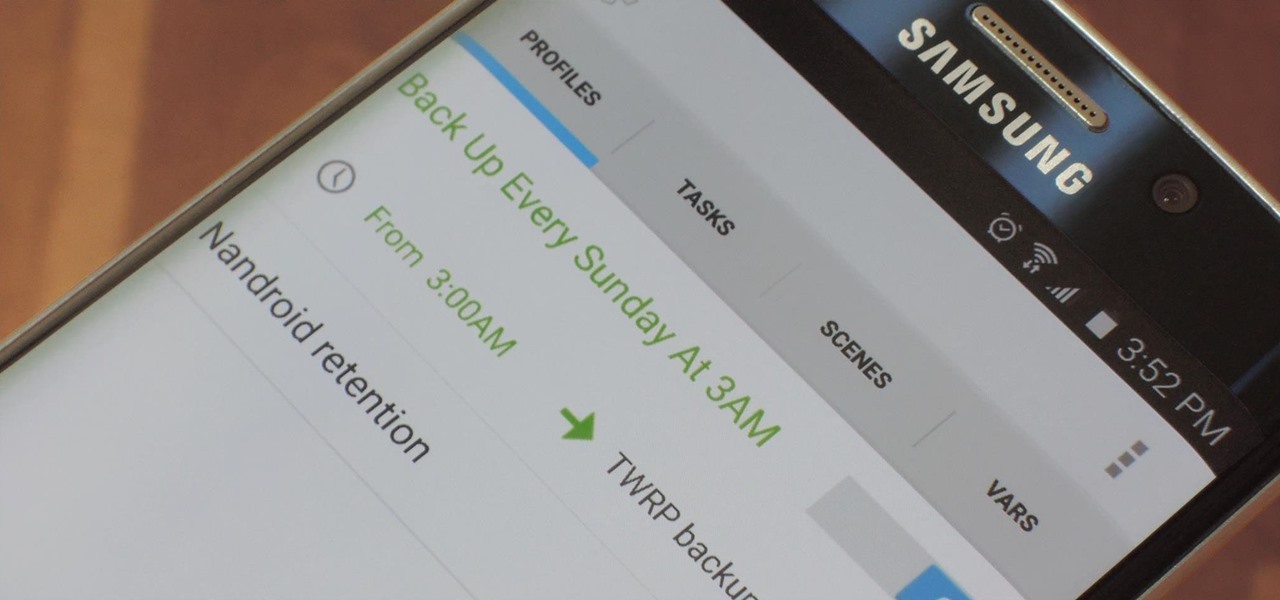
NANDroid backups are one of the best reasons to root your Android device and install a custom recovery. They're essentially a snapshot of your phone's entire operating system and all installed apps, so if you ever screw something up when installing a flashable ZIP or custom ROM, you can restore your NANDroid backup to get everything back to normal.

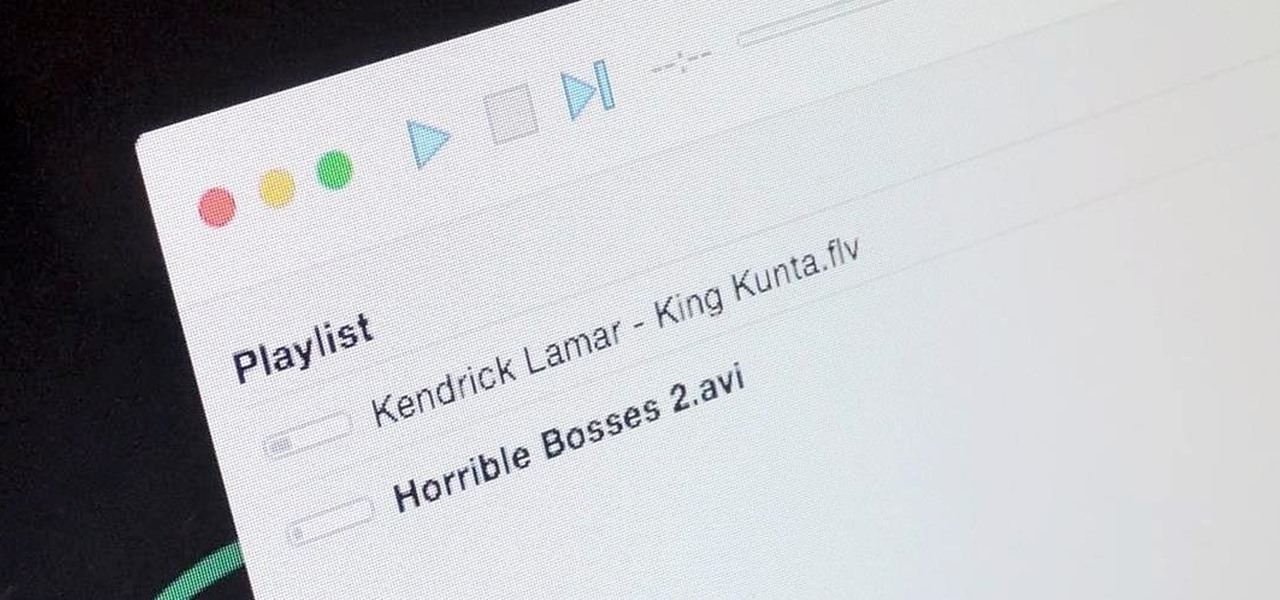
It's a breeze to send videos and music from your phone straight to your TV with an Apple TV or Chromecast, but these devices don't support all file types. While MP4 videos and MP3 music files are the norm these days, I still have a ton of AVI and FLV files that I'd like to watch on a big screen.

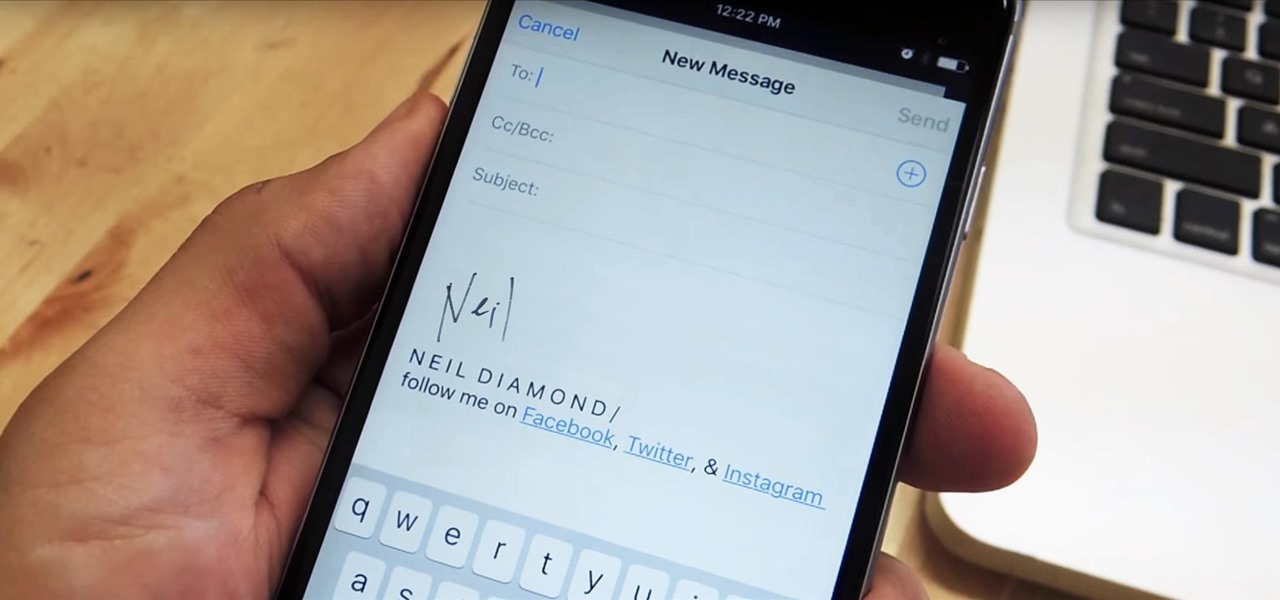
Emails sent from an iPhone, by default, are signed "Sent from my iPhone," which almost seems like a disclaimer in case the email has spelling or formatting errors. If your goal is to look professional while corresponding with coworkers or potential employers, then you're better off removing the signature completely and just typing your name out.

Like the majestic mountain structure it's named after, Apple's latest version of OS X, El Capitan, goes a little deeper to expand on the foundation laid by Yosemite. While the update may not be as monumental as some have hoped, it is an improvement and includes tons of useful new features you don't want to miss.

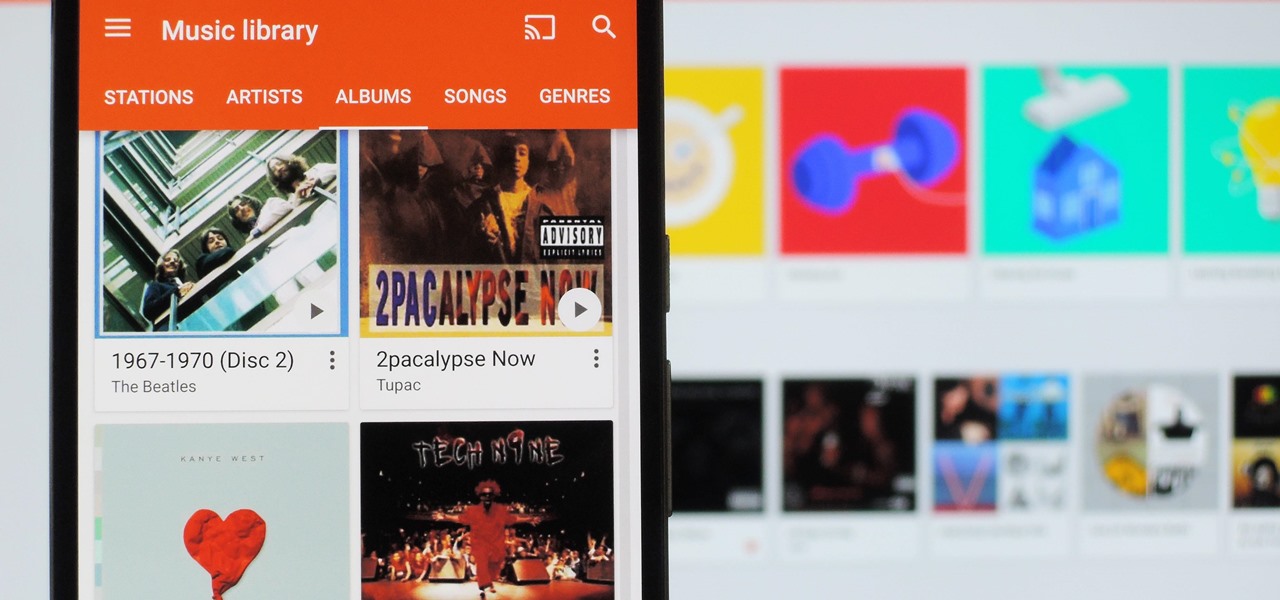
Piracy, it can be argued, is the scourge of the internet. But when it comes to music, sometimes it's best to give a listen to a track or album before deciding to spend your hard-earned money on fully supporting it.