While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

Nova Launcher is one of the most popular apps on the Play Store thanks to its rich features and fluid navigation. But one downside that comes with this abundance of features is that much of Nova's functionality is lost on the masses. Fortunately, I've used Nova for several years and learned a few tricks along the way.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

Despite concerns with SafetyNet, Google actually cares about root. Every phone they sell has an unlockable bootloader, so you can toggle a setting and send a Fastboot command, then start flashing custom firmware right away. The Pixel 2 and Pixel 2 XL continue this tradition, and now they have an official root method.

Samsung has finally rolled out the Android Oreo update for the Galaxy S8 and S8+. If you're just now getting the update, you'll be happy to know that your Galaxy just got upgraded with plenty of cool new features. Like previous updates, Samsung has improved upon its software by including a new look and new functionality.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

If you have a HoloLens, you can now control the lighting throughout your home or office via holographic controls using the free Hue Lights app in the Windows Store. The app, made by California-based AfterNow, works with the Philips Hue colored lighting system and is much more polished than the prototype we saw in January.

After enabling disk encryption, creating encrypted disk images, installing KeePassX and iTerm2, and using Git with local repositories, the next step to getting your Mac computer ready for hacking is setting up a package manager that can install and update open-source hacking tools. There are multiple options to choose from, but Homebrew has a slight advantage.

The sheer variety of Android devices on the market is staggering—one report suggests there are well over 24,000 distinct phones and tablets floating around out there. When you consider that each manufacturer adds a few tweaks to the Android code base here and there, that makes for a lot of software variations, which in turn means there needs to be many different root methods to match this variety.

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.

So you finally decided to make the switch from iOS to Android, huh? Well first off: welcome to the world of tomorrow. And secondly: good call, mate.

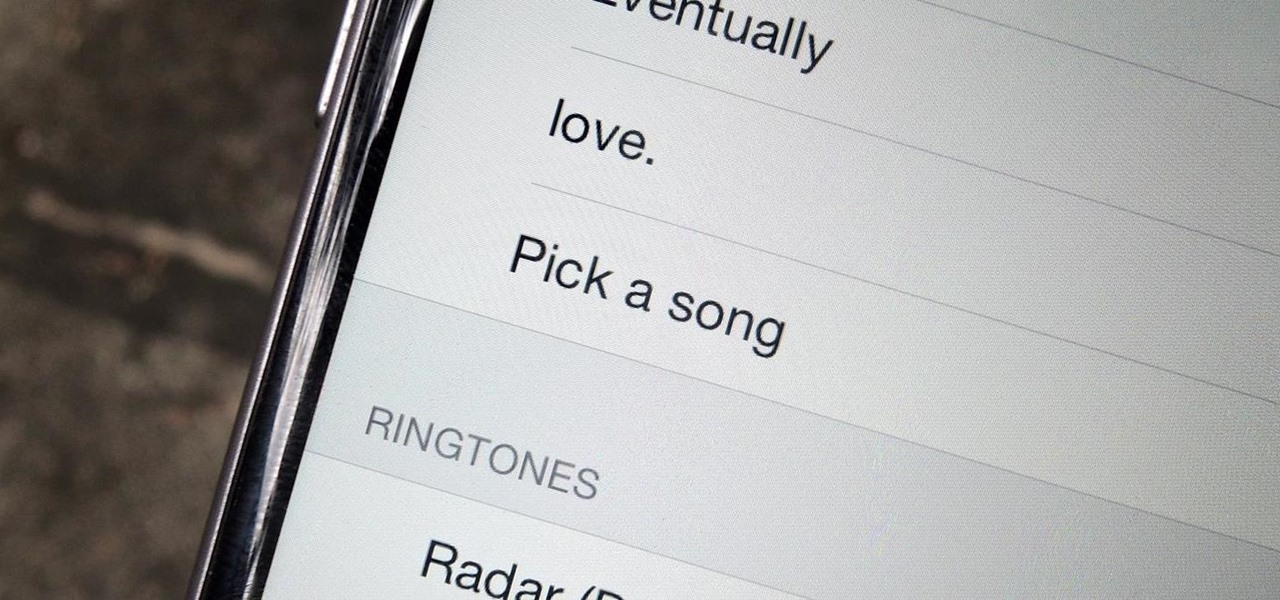
Don't like how Apple's default Radar ringtone — or any other tone — wakes you up in the morning? Then don't use them as your alarm sound. Instead, use your favorite song to get you out of bed. Whether you enjoy an acoustic tune or a heavy, energetic jam, you can choose any Apple Music song you want, or any track in your personal Music library, to get you going each day.

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

One of the main reasons to buy a Nexus device is the fact that they're always the first to get new Android updates. Another great selling point for the Nexus series is that the devices are amongst the easiest to root and mod. Unfortunately, though, these two features are somewhat mutually exclusive.

The release of iOS version 8.1.1 brought some much needed bug fixes to Apple's mobile operating system, but with it came a patch for Pangu's jailbreak method, which worked on iOS 8.0 to iOS 8.1 using a Mac or Windows computer. Luckily, it didn't take very long for a new team of developers to come up with a method for jailbreaking iOS 8.1.1 devices, and much like its predecessor, the process is a cinch.

You saw our post on the 18 coolest new features of iOS 7, but now that you've had a chance to play around with your updated iPhone, it's time to lock it down.

If I were to lose access to the entire internet for the rest of my life, one of the websites I would miss the most would have to be Wikipedia. Wikipedia has ended countless arguments, informed me of how old and single some of my favorite actresses are, and helped me brush up on thousands of historical topics.

If you can’t find the man of your dreams or maybe you’re looking for a new buddy, you can always stop looking and just draw him. After completing the basics your can style him and create whatever mood and features you like.

Summer is almost here and you’re looking forward to that exotic vacation but you are going to need a passport and photos to go in it. There are a few simple ways to get a photo for your application. Find the method that is best for you and get traveling.

A computer’s safe mode is useful when fixing problems or saving work after, say, your hard drive malfunctions. Safe mode can easily be accessed as your computer starts up and is a useful tool to have in your belt.

This video is about how to lock the screen in Mac OS X. 1. Opening the Keychain Access utility: Open up the Utilities folder. You can get to this by either hitting Command+Shift+U with the desktop (Finder) selected, or by opening Finder, browsing to the Applications folder, then double clicking on the Utilities folder.

In this video clip series, our expert will demonstrate brake pad installation, including instructions on filling brake fluid, locating caliper bolts, removing the tires for disc brake changes, as well as rotor, caliper and brake pad cleaning techniques.

Richard Revis has been keeping and breeding poison dart frogs for over 10 years. He is co-owner of Black Jungle Terrarium Supply located in Greenfield, Massachusetts, where a collection of over 200 dart frogs. encompassing more than 60 different types is maintained and bred.

In this online video series learn from expert professional mechanic Nathan McCullough who graduated from Nashville Auto-Diesel College with a Grade Point Average of 3.5 and received their craftsmanship award and honor seal. Learn important automotive Serpentine belt topics including: what is a Serpentine belt, locating the Serpentine belt, replacing the Serpentine belt, when to check the Serpentine belt, types of wear to look for, Jacking Screw Tensioner, Serpentine belt removal, checking the...

In this online video series learn how to change the alternator on your car from certified mechanic Nathan McCullough. Watch these videos and learn alternator diagnosis as well as how to disconnect the battery on your car; and how to locate the alternator; how to remove the alternator by disassembling the intake, removing the throttle linkage and radiator hose; learn how to unplug the vehicle electrical connectors from the alternator; how to remove the serpentine belt; and how to install the n...

When you listen to music, you don't just want to listen to your favorite songs and artists — you want to hear them perfectly. The same goes for videos you're watching, games you're playing, calls you're in, and anything else in which audio plays a key role.

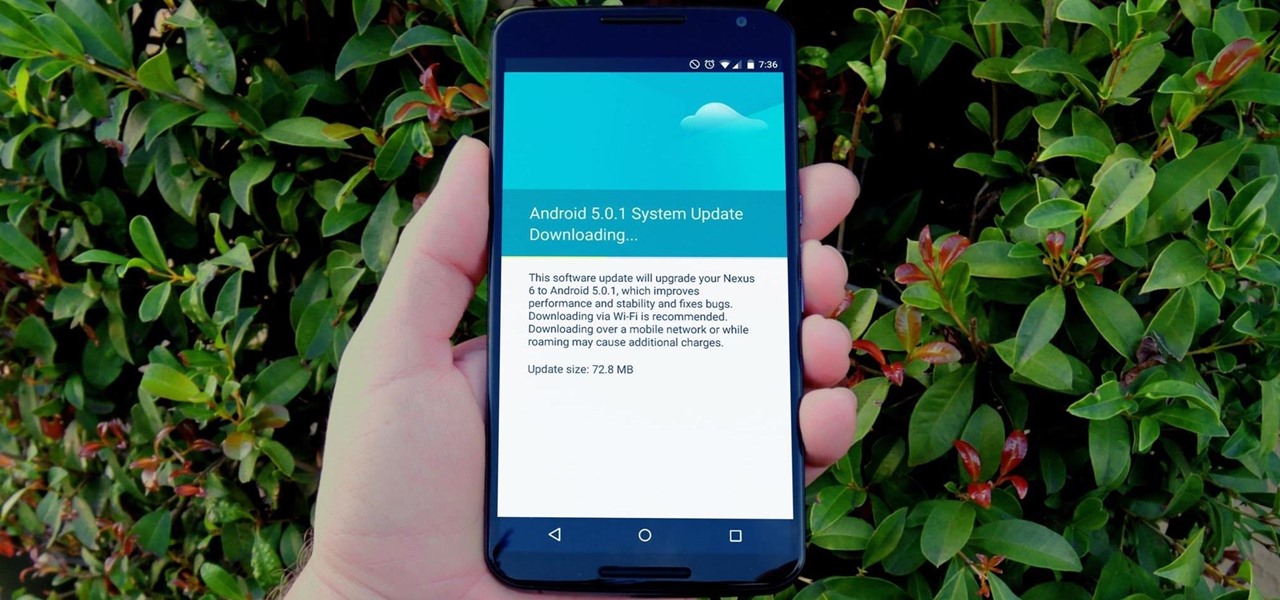
We all know Android updates have been iffy in the past. But Google has implemented several measures recently that have sped up the process substantially, and OnePlus is taking advantage of these. Still, a staged rollout update might keep you waiting for a few days or longer. So if you'd rather skip the wait, there's a better way to manually check for system updates.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

OnePlus phones are easy to root, but that also means they're easy to brick if you get trigger happy with your superuser privileges. If you find yourself in this situation, you'll quickly realize the OnePlus firmware download page doesn't provide files you can flash in Fastboot mode.

Data is king. Nearly every carrier and MVNO offers unlimited talk and text with their cellular plans. Where they differ is the amount of data available, so that's the part that can save or cost you the most money.

If you haven't used a Samsung device in a few years, the Galaxy S20 series will be your first taste of One UI 2, the skin running on top of Android 10. Although One UI is on the heavier side, it has loads of exciting features that go beyond what's offered in stock Android.

If you have an Android device that Netflix does not support, you can check the Play Store and it simply won't be there. But just because you're unable to download it through official means doesn't mean you have to live without Netflix since there's a way you can sideload it manually.

Despite Android's flexibility in regards to customization, the options available in stock Android are pretty barebones. It is only with the help of third-party apps that we can entirely transform sections of the UI to our liking. And thanks to a new app, we can modify another part of the OS, the status bar.

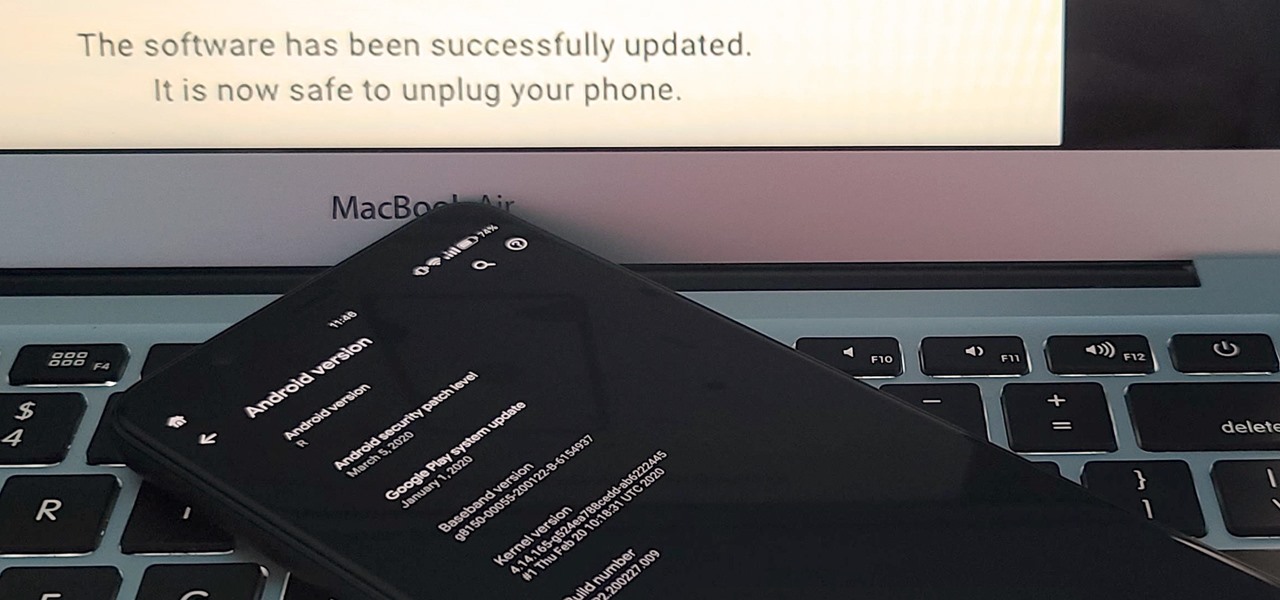
If you've ever tried to update your Android phone manually, you know the process can be unnecessarily hard. There are so many steps and parts, that if one thing goes wrong, the whole process doesn't work. Recognizing this, the Android team came up with an even easier way.

The impact of the COVID-19 pandemic caused by the novel coronavirus has practically guaranteed that the virus, along with the phrases "social distancing" and "flattening the curve," will rank among the top search terms of 2020. USA Today combined the phrases in its latest augmented reality experience, which quizzes your knowledge in the best practices of social distancing.

Downloading third-party screen recording apps can be dangerous. The primary function of these apps is being able to record everything on one's display, so it's easy to see how a malicious developer could exploit this for their own gain. That's why the addition of Android 10's built-in screen recording is so impactful.