The Samsung Galaxy S5 was just officially announced at Mobile World Congress. The new flagship device will be available worldwide beginning April 11, 2014, including all major U.S. and international carriers. With over 200 million Galaxy devices sold to date, the S5 doesn't stray too far from the trend, at least not aesthetically. We've still got a high-grade plastic shell with perforated back covers, and four color choices at launch. Our highlights of the release event are as follows.

Whether you have the original Nexus 7, or the 2013 Nexus 7 tablet, rooting it will give you access to tomorrow's features, today.

Currently, all Nexus tablets running Jelly Bean or higher can enjoy multiple user accounts. With tablets often migrating between various people in the same household, there’s no reason for Dad’s finances to mingle with little Tammy’s candy crushing. Multiple users, each with separate profiles, just makes sense on an Android tablet.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

The @DesignGears guys have been busy today, leaking an unofficial KitKat build (Android version 4.4.2) for the AT&T Samsung Galaxy Note 3. The latest is a peek into what the international variants are beginning to see, although this build is far from official. Still, if you want to give it a shot, I'll show you how to install it, but make sure to check out the details below the how-to to see what you can expect, good or bad.

There are some ingredients I cook with so often I can never buy too many of them, and most of them are produce. Onions, garlic and fresh herbs are staples in a lot of dishes, and they may be inexpensive, but when you use them on a daily basis it can add up.

Sometimes... no, most of the time, I don't want to do anything, so I was excited to find a developer teaming up with Sir Isaac Newton to create an application that encouraged my slothfulness.

When it comes to the user interface, you're pretty much limited to the stock one that comes on your Samsung Galaxy Gear smartwatch—a carousel of large black and white icons representing the features and applications on the watch.

Like many other smartphones, the HTC One has a few capacitive keys on the bottom of the device, but that's the problem. It only has a few keys, meaning two, which are the Back and Home keys.

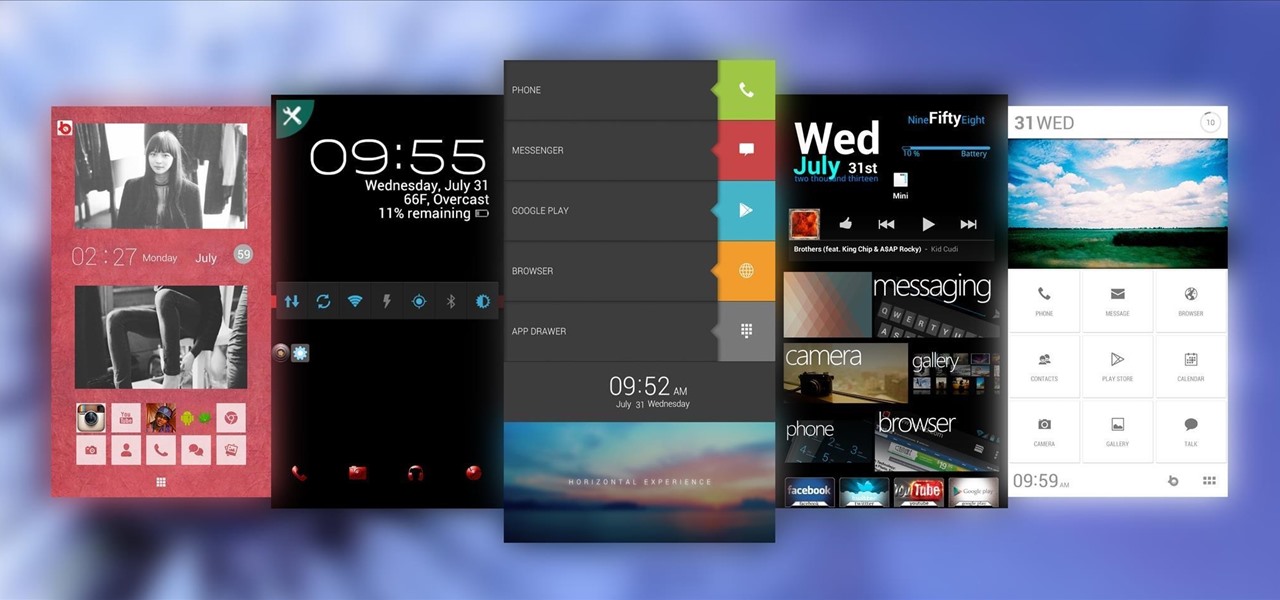
Customizing isn't all rooting and ROMs—there are plenty of ways to customize your Samsung Galaxy Note 2 or other Android device without gaining superuser access. One of the easiest ways is to install an Android launcher, sometimes called a home launcher, that matches your style.

A Steampunk's Guide to Sex was the subject of a recent successful Kickstarter campaign, and I now hold the finished book in my hands. As such, I can say (mostly) unreservedly that you should buy this book. Allow me to tell you why, before I get into the nitty-gritty about the book itself. Sex is something of an odd topic in America because it's perfectly legal, and yet taboo. Unlike things that are illegal and not taboo, like drug use, murder, theft, etc. What this means is that children can ...

Steampunk music is an oft-debated genre, full of bands playing all sorts of different sounds. While this can make it difficult to generalize about the genre as a whole, it means that the average person is bound to like at least some Steampunk bands. That's why it's a great idea to support some independent Steampunk bands this holiday season by buying their music for yourself, or sharing it with someone else.

In these lion dance video instruction clips, learn about the music of the Southern style Chinese New Year Lion Dance and how it influences and directs the ceremony. Listen to the cymbals and drums as the Buddha puts the lion through its paces, taunting him with his fan. Learn how the different instruments create emotional soundscapes related to the narrative of the lion dance. Get an in-depth look at Chinese lion dance drum music in this video series, a thousand years in the making.

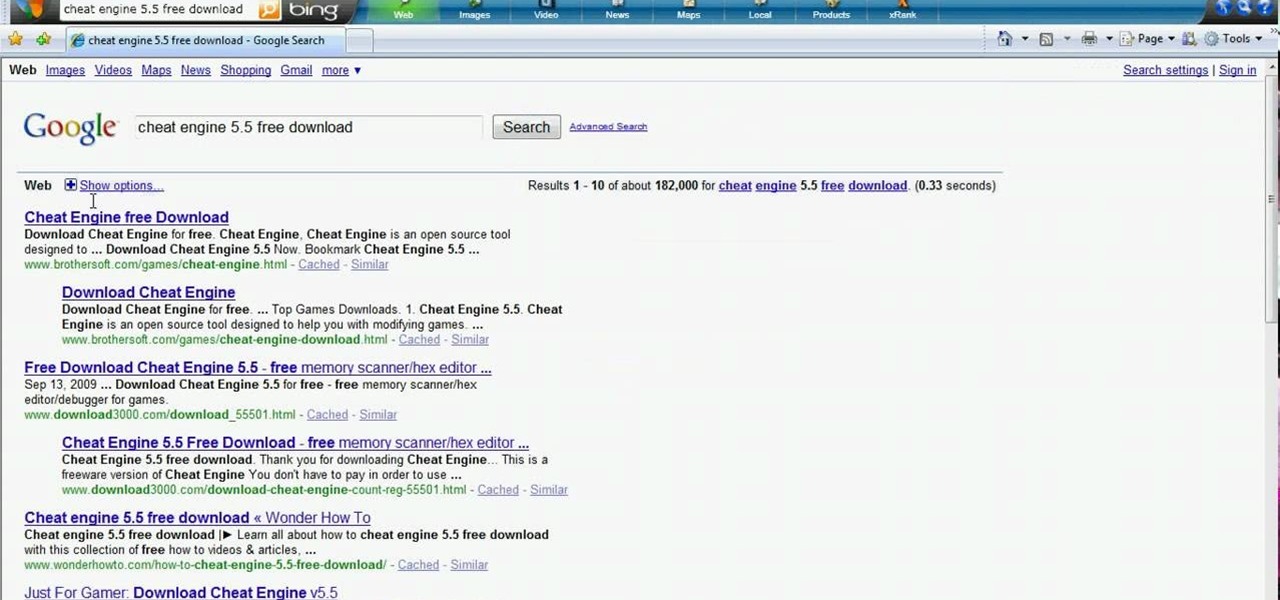
Need resources in Evony? Hack them… with a speed hack. You just need Cheat Engine and this video. Watch this video tutorial to learn how to hack speed in Evony with Cheat Engine (10/12/09). In order to perform this speed hack for Evony, you need to download Cheat Engine 5.5. Try it out for yourself.

Hacking flash games is the new coolest thing these days... now hackers can be anywhere, ever expanding, all thanks to a little cheating program called Cheat Engine. Check out this video tutorial to learn how to download and install Cheat Engine to hack flash games.

Although the enterprise use cases for the Microsoft HoloLens 2 continue to impress, the arts community just can't stay away from the best augmented reality headset on the market.

We usually focus on augmented reality here, but when something important in VR happens, we highlight it as part of the overall immersive computing story.

The fight to wrest control of apps from Apple's revenue-focused grip just took a major turn in favor of Epic Games.

The beauty industry has increasingly relied on the powers of augmented reality to drive sales in recent years, and now that virtual "everything" is on trend due to the pandemic, yet another big player is entering the fray.

The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

The modern remote workforce faces many challenges, but perhaps none is greater than organizing calls and syncing tasks. Many platforms are convoluted and difficult to manage. Team members get bogged down by administrative tasks instead of staying productive.

It looks as though the novel coronavirus and social distancing guidelines are here to stay for a while. So companies of all sizes and industries are scrambling to adapt to a new reality in which everything from morning meetings to large-scale presentations are done entirely online. It looks like this is going to be the new normal for the foreseeable future.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

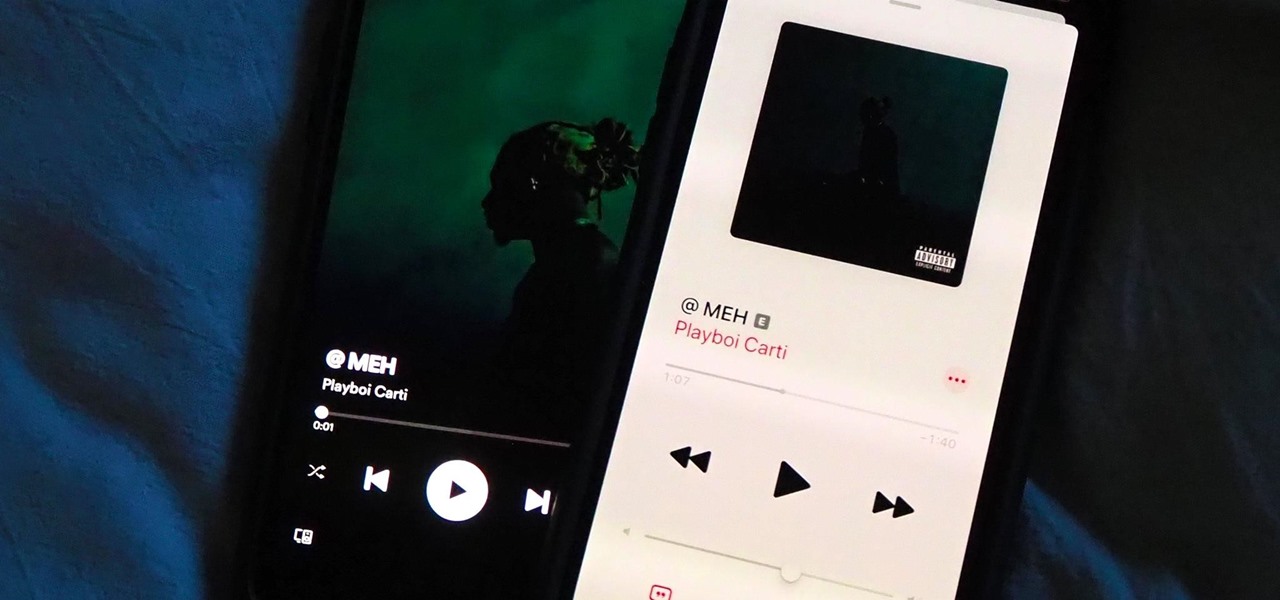
To share a song or album to family and friends, it's as easy as copying its link in the app and pasting that into a message. However, not everyone uses the same music streaming service, so a link to an Apple Music song won't do a Spotify, Tidal, Pandora, Deezer, or YouTube Music subscriber any good. If you're on an iPhone, though, there's an easy way to convert links from one service to another.

With more digital content than ever, the search feature on smart TVs is essential. But typing is such a terrible experience when you're forced to use voice dictation or peck around with the remote control. Thankfully, there's a better way.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

A modern iPhone is capable of running sophisticated, exquisitely-rendered games that rival titles on current-generation consoles. However, there is some value in classic video game titles, whether you grew up playing games on the Atari 2600, Nintendo Entertainment System, and Sega Genesis or not.

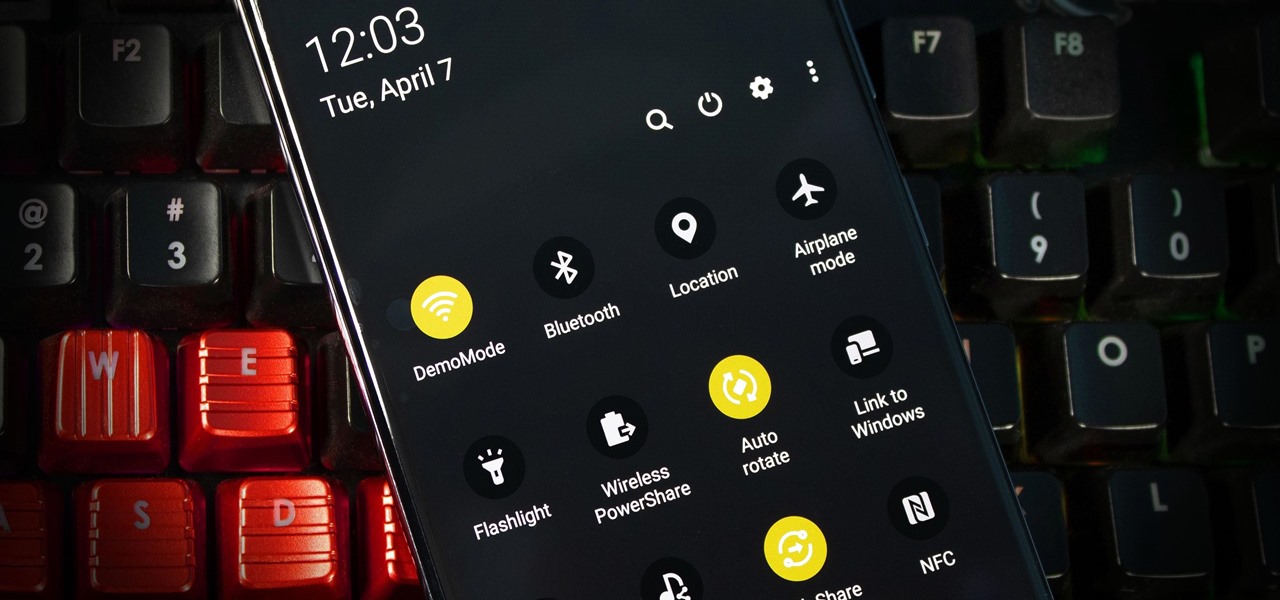
Every Galaxy S20 sold in the US — even the S20+ and S20 Ultra — simply can't be rooted. With the bootloader permanently locked, you miss out on the world of rooting and the customization it opens up, but modifications are still possible.

Whether you're trying to become an influencer or just want to share better photos and videos, the best camera to start with is your smartphone. It is likely the only camera you always have on you and it's probably capable of excellent pictures and video capture. But with a little help, it could definitely be better.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

Surprising? No. Exciting? Absolutely. After a grand introduction by at the Apple event on September 10, 2019, the iPhone 11 is finally here. We may have known nearly everything about this new iOS device ahead of time, thanks to the usual surge of reliable leaks and rumors.

In our comparison of the best gaming phones in 2019, the winner actually surprised us. A phone that most people don't know about from a brand you probably haven't heard of ended up as the clear winner. But how? Well, it ticked so many flagship boxes despite its midrange price tag.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

Why do you need augmented reality? Because enterprise, they say. And while that's certainly true for several disciplines, there's still that mainstream use case hanging out there waiting for users to discover beyond the realm of enterprise and gaming.

Since the Razer Phone's announcement in 2017, we've seen a new subgroup of phones emerge. Gaming phones are now a thing, leading to companies like ASUS creating phones that are thoroughly optimized for the mobile gaming experience. And with their second iteration, they perfected it.

For those with small hands, smartphones have gotten out of control as of late. Nearly every flagship phone is over six inches in length, so many are forced to use phones that are too big for them and hope they don't fall. Well, thanks to one developer, using these phones can be a lot easier.

When I first found out about Nreal, back in the spring of 2018, the most interesting thing about the company's story was the founder's background. Chi Xu, the CEO and founder of Nreal, previously worked at Magic Leap as a software engineer.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

Next to Apple, Snap is currently one of the most important companies on the planet in terms of delivering products that are moving augmented reality into the mainstream. That's why it's no surprise that Facebook, which is also focused on AR and tried to acquire the company for $3 billion several years ago, duplicates many of the smaller company's features.