At a global security conference in Munich, philanthropist and businessman Bill Gates spoke about the next pandemic and a dire lack of global readiness. Here's how his statement could come true—and how to be ready when it does.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!
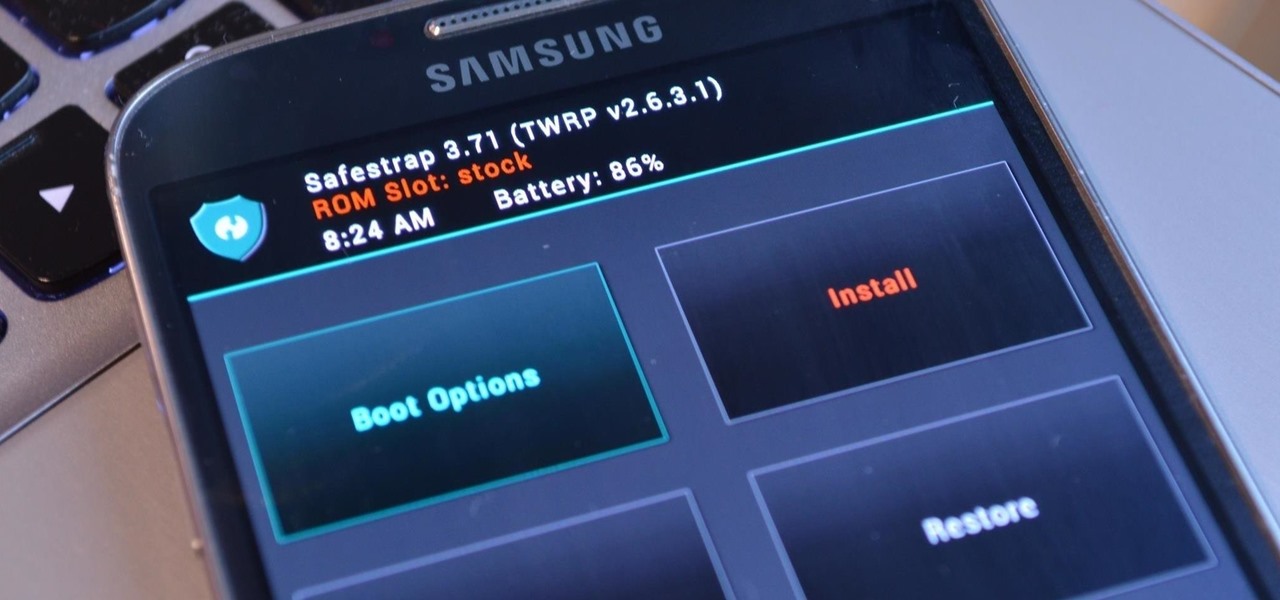
Third-party ROMs like CyanogenMod are the ultimate form of customization for softModders. Hard-working developers offer us alternate Android experiences to replace our often bloatware-riddled stock ROMs.

One of the best recent outings in the Marvel universe is the animated series What If...?, which explores alternate universe takes on various superhero storylines that deliver fascinating scenarios if one single factor had been different in the story.

The march of Amazon to insert itself into nearly every retail arena continues with the e-commerce giant's latest move to launch its own brick-and-mortar beauty salons.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

Mystery is a tricky thing. Used correctly, it can give onlookers the impression that wondrous and perhaps valuable things are afoot. However, once the veil of suspension of disbelief is removed in any significant way, that same mystery can quickly turn into not just skepticism, but outright anger at what may have seemed like an attempt to dupe trusting onlookers.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-depth article. In this article I'm going to walk you through one of the main networking protocols when it comes to communication across the Internet between programs, aka UDP(User Datagram Protocol).

A lot of digital ink has been spilled heaping scorn on Magic Leap. Much of that media schadenfreude was due to what some believed were unmet promises versus some of the early hype around the product. Others just seemed to be rubbed the wrong way by the startup's Apple-esque secrecy and penchant for attempting to coin new terms and frameworks for things that were, mostly, already in play.

It feels strange to be walking through an open field in a small village in the English countryside. There's no one else around — just the four of us: me, my husband, my 12-year-old son, and my adult niece. The day is spectacular, particularly for England. The sun is shining, and the temperature is in the low '70s.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

It is almost indisputable that smartglasses and head-worn displays are the future of augmented reality. However, at this precise moment, they are still a very niche market.

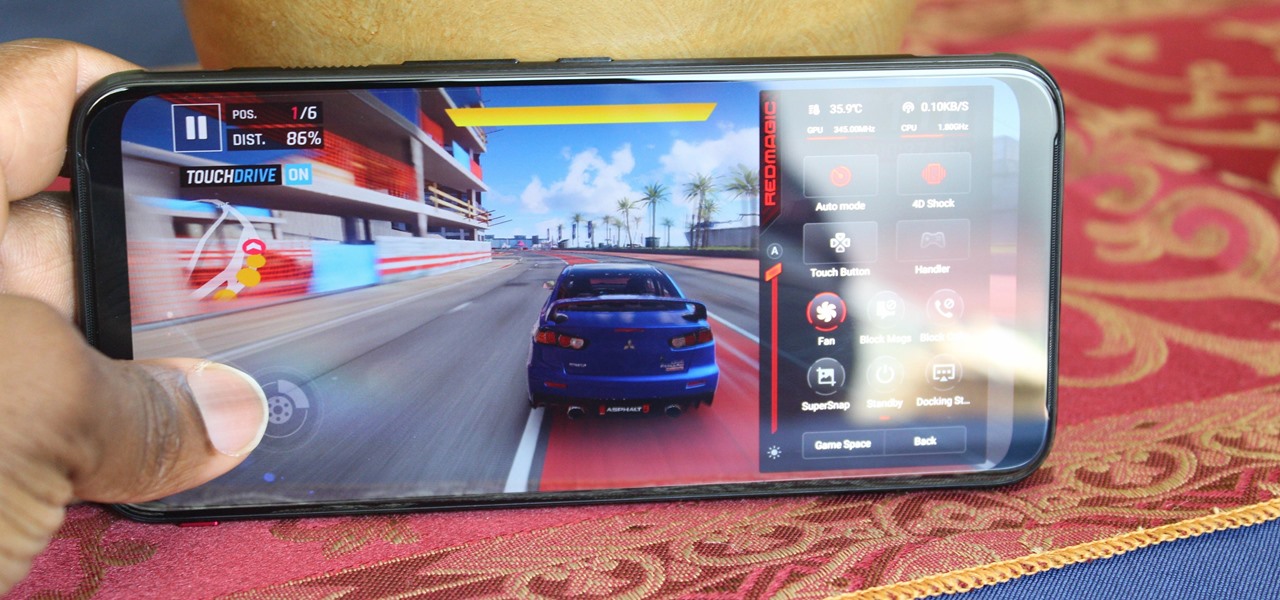
Mobile gaming has exploded in recent years, with experts predicting 2.4 billion global mobile players by the end of 2019. It already accounts for 47% of the worldwide gaming market, besting console and PC. No wonder we've seen the rise of gaming smartphones, a class of phones that specialize in mobile gaming.

With the list of available mobile apps for moviegoers constantly expanding and improving, seeing a film at your local theater has never been better. With the right apps for your iPhone or Android phone, you can research movies, find out if showings are sold out, reserve seats, save money on tickets and concessions, preorder popcorn and soda, and even find dull bathroom-worthy scenes.

For many, phones are starting to replace televisions as the primary device for watching videos. Thanks to their portability and easy to use apps, it's often simpler to watch Netflix, Hulu, YouTube, or Prime Instant Video on the smaller screen. But not every phone is suited to fit this need, so we did some testing to find the best of the best when it comes to streaming videos.

The biggest problem with Netflix (which is hardly a real problem) is the overwhelming amount of content available for streaming. Browsing through profile-specific categories might help narrow down your search on something to watch, but some of those categories come and go without warning, and it's impossible to find them again—but not anymore.

Watch this winds tutorial video to learn how to play "The Dawning of the Day" on the tin whistle and review basic hand position. This video is directed toward beginning tin whistlers. You'll be playing "The Dawning of the Day" on your tin whistle in no time after you've watched this helpful how-to video.

There are many applications you can use to record and edit audio on your computer. This video discusses two others besides Audacity – QuickTime Pro for Mac and Windows, and GarageBand, which is only available for the Mac.

Teach your students about centripetal force with this science video tutorial. It will show you how to use some masking tape and a ball to demonstrate how centripetal force works.

There are a variety of ways to speed up your body’s ability to heal. Things like keeping the incision clean, resting, nutritious foods and physical therapy will get you feeling strong quickly. Avoid negativity, as it may actually slow down your recovery. No one likes to be laid up in bed after surgery. Follow the advice on your “get well soon” card and be back to your old self in no time.

Bennett's fracture takes place at the base of the thumb. It typically occurs when an individual falls on an outstretch hand. The force is directed this way; the fracture occurs here. Learn how to diagnose and treat a Bennett's fracture in this medical how-to video.

Reiki is a form of holistic healing that originated in Japan. It is a way of magnifying the healing "ki" energy of the hands. Reiki uses the same kind of non-physical "ki" energy martial artists use to nourish the body's health and vitality.

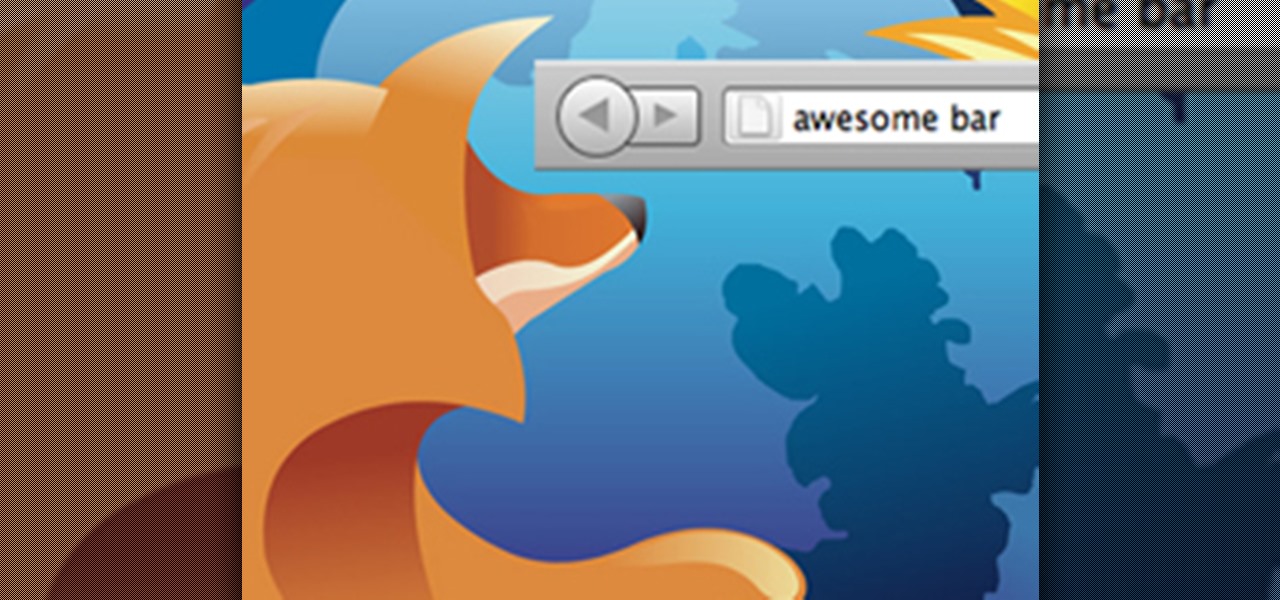
Getting used to your new Firefox 4 web browser? If so, you might have seen some improvements in the Location Bar. The updated features make browsing the web a cinch, so it's no wonder why more and more Internet junkies are calling it the Awesome Bar. It's faster and easier to use, and there's even some optional tweaks that you can employ to make your Internet experience smooth and effortless.

The last few months of WikiLeaks controversy has surely peaked your interest, but when viewing the WikiLeaks site, finding what you want is quite a hard task.

This Animal Welfare Foundation two-part video tutorial is from expert veterinary staff demonstrating the correct procedures for handling small mammals for clinical examination and medication. Its aim is to show that the primary consideration should be for the the welfare of the animal. This video guide will show you practical animal handling for a rat.

Knitted balls can be used for all sorts of projects. The obvious is a Christmas ornament, but knitted balls can also be the basis for knitting toys or snowmen. And of course, they can be used simply as balls which make a lovely gift for a baby. They can be all one color, striped or patterned. To get started, follow the directions below for a one-color knitted ball. You will need to know how to knit on double-pointed needles, so if you need help with that, check out my other article.

Square dancing, a fun American pastime! Learn square dance steps with this instructional animation. Fun fact about square dancing: 19 U.S. States deem it their official dance. Square dance is a folk dance with roots in Europe, eventually spreading to the states & becoming more of an iconic dance there. Square dancing consists of 4 couples arranged in a square formation. This square dance lesson is clear and to the point. Search "square dance instructional animation" on Wonderhowto for more sq...

Intro Everyone who has, or at one point in time owned an iPod or iPhone has used iTunes. And we all know the problems with iTunes. For example, sometimes it doesn't detect the device or thinks your iPod's just a camera, or there are bugs in the software.

Whenever we get together and hang, my friends are always talkin' me into doin' the famed truffle shuffle from the movie 'The Goonies', made famous by the character Chunk. Well, this is where I got the idea for this prank.

Square dancing, a fun American pastime! Learn square dance steps with this instructional animation. Fun fact about square dancing: 19 U.S. States deem it their official dance. Square dance is a folk dance with roots in Europe, eventually spreading to the states & becoming more of an iconic dance there. Square dancing consists of 4 couples arranged in a square formation. This square dance lesson is clear and to the point. Search "square dance instructional animation" on Wonderhowto for more sq...

Square dancing, a fun American pastime! Learn square dance steps with this instructional animation. Fun fact about square dancing: 19 U.S. States deem it their official dance. Square dance is a folk dance with roots in Europe, eventually spreading to the states & becoming more of an iconic dance there. Square dancing consists of 4 couples arranged in a square formation. This square dance lesson is clear and to the point. Search "square dance instructional animation" on Wonderhowto for more sq...

Todd Cole directed this beautifully shot (DP Matthew Lloyd) and art directed preview of the Rodarte Spring '11 line. The visual execution of this ostensibly simple concept is flawless; there are no extraneous colors whatsoever. Clarity of vision and preproduction certainly paid off.

In our media-enriched world, past and present, SCRABBLE has made a name for itself, whether deliberately, subconsciously, or influentially. You may have a read a book that had the popular word game within a chapter, watched a movie that showed your favorite characters bringing out the SCRABBLE board, or even listened to a rap about this word or that word. SCRABBLE is everywhere, even if you don't realize it.

Here is the trailer for the feature film "Leaves of Grass" starring Edward Norton, written and directed by Tim Blake Nelson

Ashes directed by David Dang Making of Ashes (Shot with a Canon 7D)

Check out the winner from Beyond the Still's Chapter Two: Job Security. "Job Security" written & directed by Josh Thacker.