After years of making do with a cheap knife, I finally bought a really good 8" chef's knife—a Henckels, although I was also eyeing a Global santoku. It quietly but literally changed my life.

Even though I often end the workday exhausted and just want to wrap rotisserie chicken parts in a store-bought tortilla and shove it in my eating hole, I generally try and take a couple of minutes to warm up said tortillas before I begin my meal. But if you're starving, do you really need to take the time? Do warm tortillas really make that much of a difference?

Welcome back, my hacker novitiates! Recently, I demonstrated a hack where you could redirect traffic intended for one site, such as bankofamerica.com, to your fake website. Of course, to really make this work, you would need to make a replica of the site you were spoofing, or better yet, you could simply simply make a copy of the original site and host it on your own server!

Nokia's recent foray into the world of Android brought a plethora of goodies along with it. The Finnish smartphone manufacturer offers a slightly different take on our favorite mobile operating system, with customizations ranging from ringtones to its very own app store.

When you come home from the grocery store, you probably put away every single fruit and vegetable in the bins and drawers in your refrigerator. Any fifth grader knows that fridges work to preserve food, thus everything should go in there, right? Nope!

The Samsung Galaxy S5 was just officially announced at Mobile World Congress. The new flagship device will be available worldwide beginning April 11, 2014, including all major U.S. and international carriers. With over 200 million Galaxy devices sold to date, the S5 doesn't stray too far from the trend, at least not aesthetically. We've still got a high-grade plastic shell with perforated back covers, and four color choices at launch. Our highlights of the release event are as follows.

Whether you have the original Nexus 7, or the 2013 Nexus 7 tablet, rooting it will give you access to tomorrow's features, today.

Currently, all Nexus tablets running Jelly Bean or higher can enjoy multiple user accounts. With tablets often migrating between various people in the same household, there’s no reason for Dad’s finances to mingle with little Tammy’s candy crushing. Multiple users, each with separate profiles, just makes sense on an Android tablet.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

The @DesignGears guys have been busy today, leaking an unofficial KitKat build (Android version 4.4.2) for the AT&T Samsung Galaxy Note 3. The latest is a peek into what the international variants are beginning to see, although this build is far from official. Still, if you want to give it a shot, I'll show you how to install it, but make sure to check out the details below the how-to to see what you can expect, good or bad.

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.

There are some ingredients I cook with so often I can never buy too many of them, and most of them are produce. Onions, garlic and fresh herbs are staples in a lot of dishes, and they may be inexpensive, but when you use them on a daily basis it can add up.

Sometimes... no, most of the time, I don't want to do anything, so I was excited to find a developer teaming up with Sir Isaac Newton to create an application that encouraged my slothfulness.

When it comes to the user interface, you're pretty much limited to the stock one that comes on your Samsung Galaxy Gear smartwatch—a carousel of large black and white icons representing the features and applications on the watch.

Like many other smartphones, the HTC One has a few capacitive keys on the bottom of the device, but that's the problem. It only has a few keys, meaning two, which are the Back and Home keys.

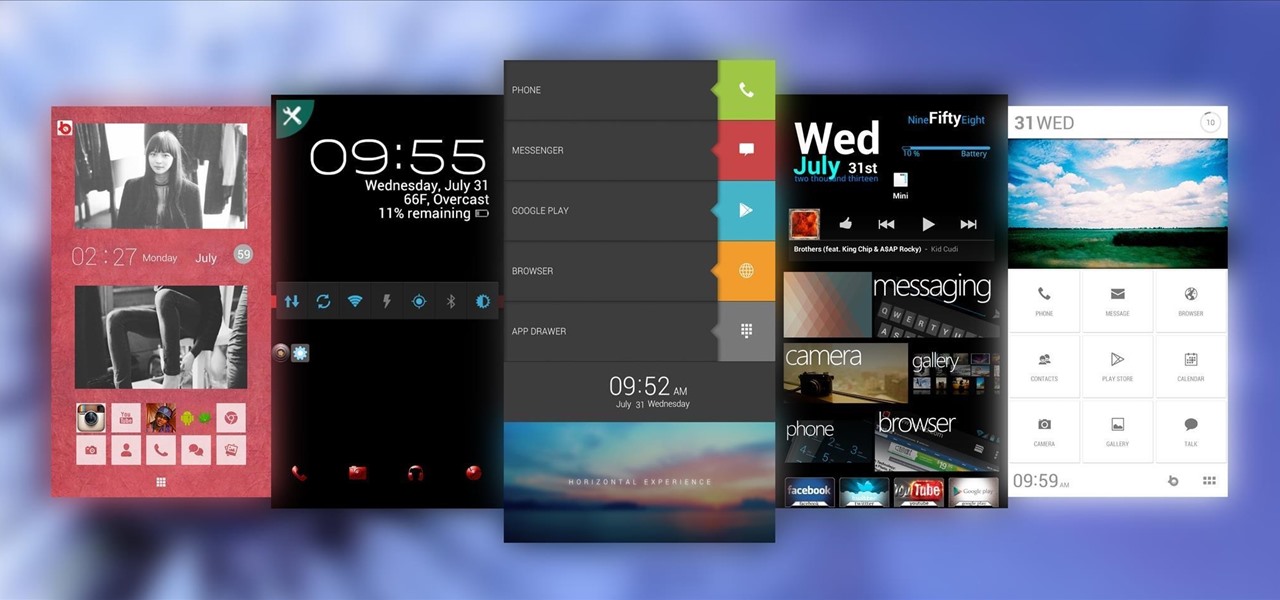
Customizing isn't all rooting and ROMs—there are plenty of ways to customize your Samsung Galaxy Note 2 or other Android device without gaining superuser access. One of the easiest ways is to install an Android launcher, sometimes called a home launcher, that matches your style.

Welcome back, my neophyte hackers! As part of my series on Wi-Fi hacking, I want to next look at denial-of-service (DoS) attacks, and DoSing a wireless access point (AP). There are a variety of ways to do this, but in this tutorial we'll be sending repeated deauthentication frames to the AP with aircrack-ng's aireplay. Remember, hacking wireless networks isn't all just cracking Wi-Fi passwords! Our Problem Scenario

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

Many social networks have become a part of our daily routine. Checking Facebook or sending out a Tweet are things millions of people do every single day. So, one would think that having a great app offering for Windows 8 would be a no-brainer. But, and this is a huge but, there are still no official Twitter or Facebook apps for Windows 8.

A Steampunk's Guide to Sex was the subject of a recent successful Kickstarter campaign, and I now hold the finished book in my hands. As such, I can say (mostly) unreservedly that you should buy this book. Allow me to tell you why, before I get into the nitty-gritty about the book itself. Sex is something of an odd topic in America because it's perfectly legal, and yet taboo. Unlike things that are illegal and not taboo, like drug use, murder, theft, etc. What this means is that children can ...

Steampunk music is an oft-debated genre, full of bands playing all sorts of different sounds. While this can make it difficult to generalize about the genre as a whole, it means that the average person is bound to like at least some Steampunk bands. That's why it's a great idea to support some independent Steampunk bands this holiday season by buying their music for yourself, or sharing it with someone else.

When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new user has been added and will begin to take preventative action.

In this video clip series our fashion and cosmetology expert Casey Christensen will show you not only how to get some cool styles for men when cutting their hair but also how to use a razor for a messier, more party style look. She walks you through each step, cross checking again and again remembering that she's not done until the client is happy. Don't let today's fashions pass you by or one day you might be wearing the mullet of tomorrow. Ouch!

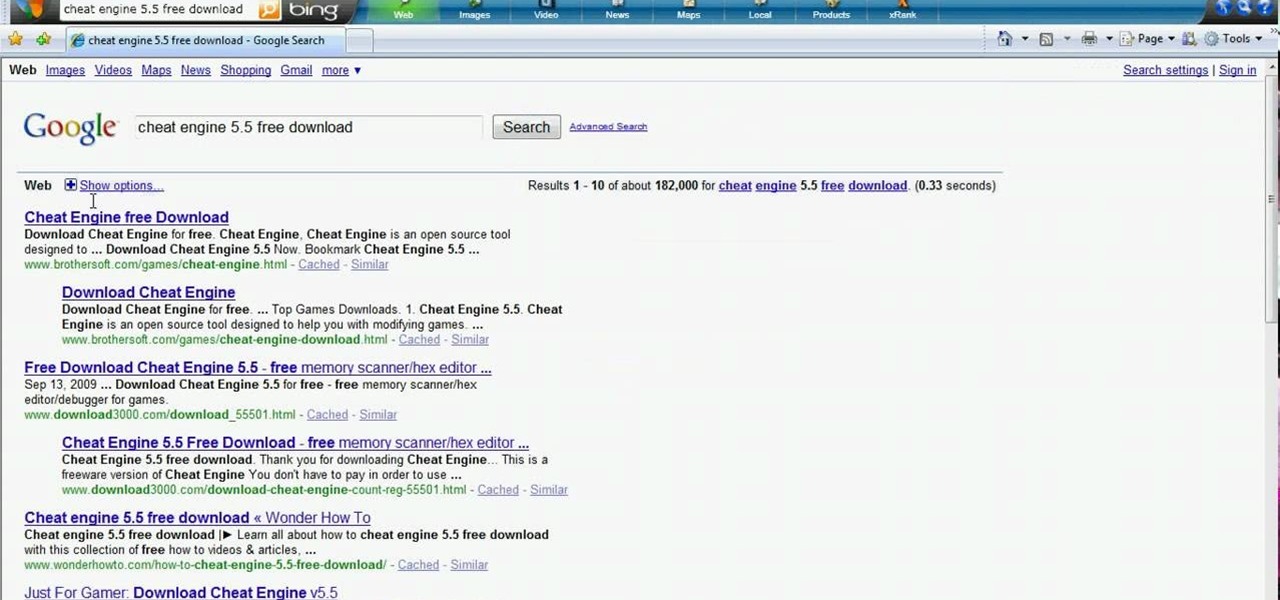
Need resources in Evony? Hack them… with a speed hack. You just need Cheat Engine and this video. Watch this video tutorial to learn how to hack speed in Evony with Cheat Engine (10/12/09). In order to perform this speed hack for Evony, you need to download Cheat Engine 5.5. Try it out for yourself.

Hacking flash games is the new coolest thing these days... now hackers can be anywhere, ever expanding, all thanks to a little cheating program called Cheat Engine. Check out this video tutorial to learn how to download and install Cheat Engine to hack flash games.

Important emails can slip through the cracks in any email client, especially sent emails you were expecting responses to but never received — and ultimately forgot about. Apple has an easy solution for this problem, helping you get answers in Mail for all your pending questions.

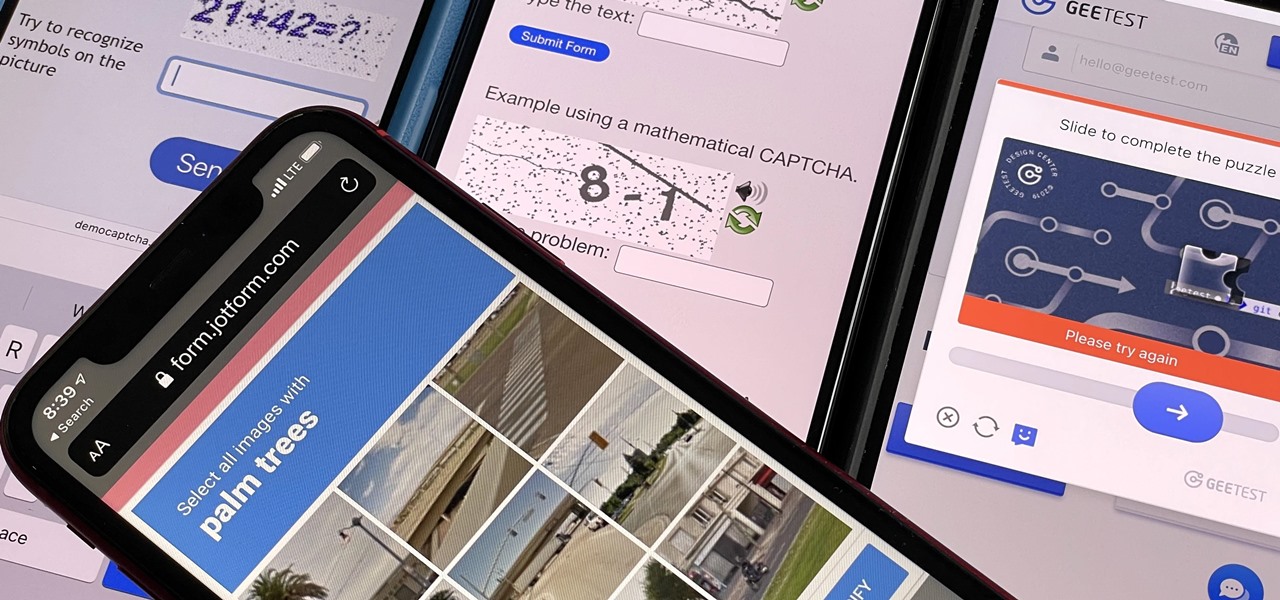
If you hate matching images, typing letters and numbers, solving math problems, and sliding puzzle pieces for CAPTCHA human verification, you'll love Apple's newest privacy feature for apps and websites.

You no longer have to resort to a third-party email client on your iPhone to schedule messages to send whenever you want. Apple built the scheduling functionality into its Mail app, and it works with any email service you use in Mail, whether that's iCloud, Gmail, Yahoo, Outlook, or another service.

One of Apple's most prominent iOS 16 features lets you unsend iMessages, but those aren't the only things you can take back. Your iPhone's Mail app also has the Undo Send feature, and unlike the Messages app, you can even customize the amount of time you have to stop an email before it's too late.

Throughout the COVID-19 pandemic, Facebook enjoyed a boost in sales of Portal, its smart video cameras with AR effects, as social distancing became the norm.

With its emphasis on well-rounded audible entertainment, Deezer gives all music and podcast fans the best of both worlds. As great as the app is, it's inconvenient to constantly tell Siri to play your music and podcasts through Deezer so that it doesn't default to Apple Music or Apple Podcasts instead. But as of iOS 14.5, you can set Deezer as your iPhone's "default" music player for Siri.

If there is one constant in currently available AR headsets, it's that, for a quality experience, they'll carry a high price tag. Price is one of the reasons these devices are mostly marketed towards enterprise customers for now.

Ever since the US Army awarded Microsoft's HoloLens a $480 million contract, the battle for enterprise augmented reality has heated up in earnest.

Dreaming up the next big business is easy. Running day-to-day administrative tasks is not. The tedious nature of entrepreneurship is the barrier that holds many people back from realizing their full potential.

We all know how hard it can be to stay productive, especially when working from home. There are many distractions throughout our day. Organizing your workflow is necessary for getting anything done.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

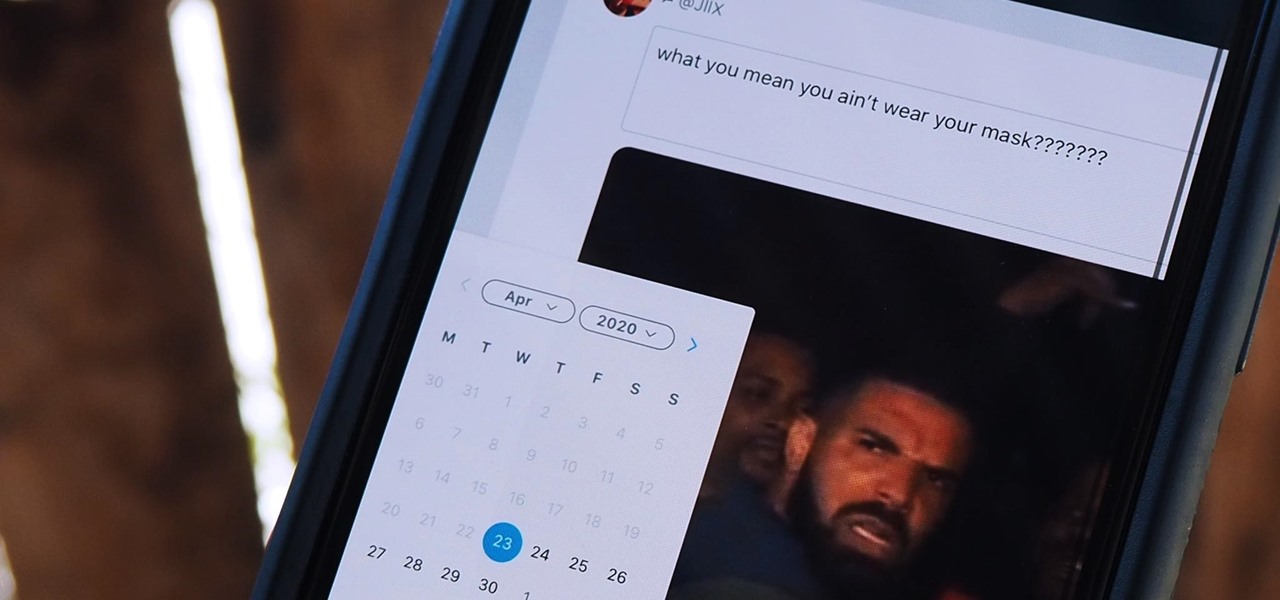
Twitter is a science. The smarter you post and engage with others, the better chance you have at building a bigger audience. Scheduling your tweets is one way to get there. Most engagement occurs at specific hours, but you may not be around then to post your tweet manually. While the official Twitter app on iOS and Android doesn't allow you to schedule, there is another way.

The response to the COVID-19 pandemic means that social distancing has become the new normal. It also means that more Americans are using video conferencing to connect with colleagues working from home or friends and family in quarantine because of the new coronavirus.

When you're stuck working or learning from home, video meetings can help you stay connected to employers, coworkers, schools, students, and more. And Zoom is the hottest video conferencing service at the moment. While Zoom is easy to use, it does have a fair share of sketchy features you should know about, such as attendee attention tracking.