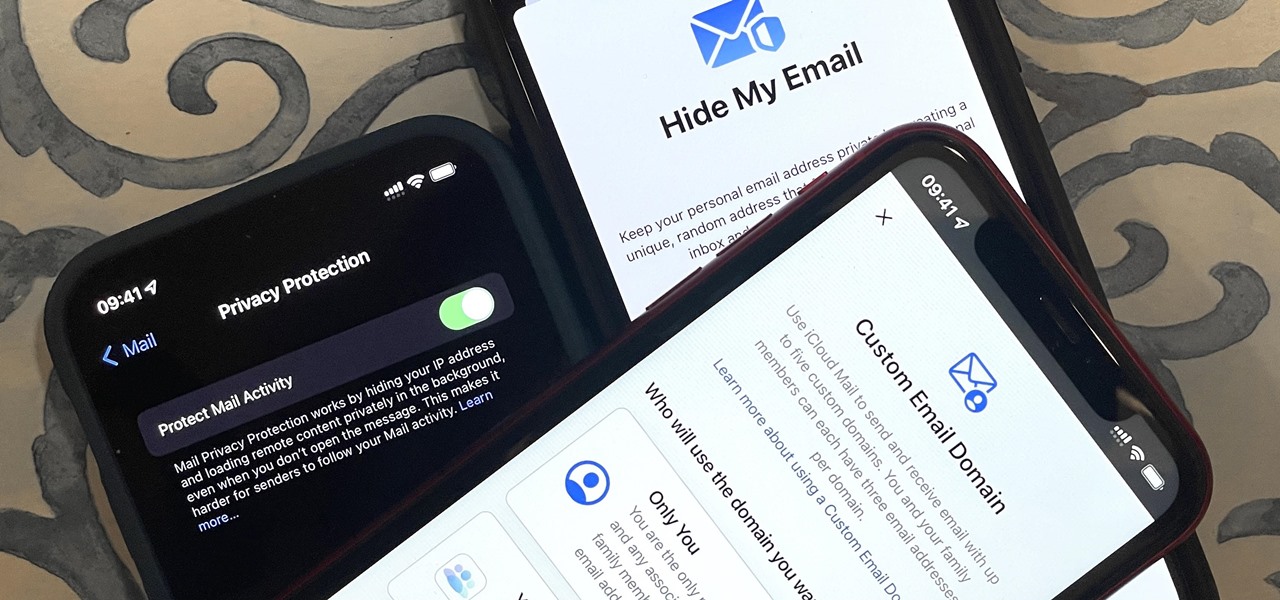
Privacy is a growing concern in the tech industry, but Apple has fallen behind many of its peers when it comes to email security. Fortunately, iOS 15 changes that. Your email address is the key to a vast amount of personal information, not to mention a stepping stone into your other online accounts, so it's great to see new features for iPhones that protect email accounts and their contents.

Although the enterprise use cases for the Microsoft HoloLens 2 continue to impress, the arts community just can't stay away from the best augmented reality headset on the market.

We usually focus on augmented reality here, but when something important in VR happens, we highlight it as part of the overall immersive computing story.

The fight to wrest control of apps from Apple's revenue-focused grip just took a major turn in favor of Epic Games.

The beauty industry has increasingly relied on the powers of augmented reality to drive sales in recent years, and now that virtual "everything" is on trend due to the pandemic, yet another big player is entering the fray.

The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

The modern remote workforce faces many challenges, but perhaps none is greater than organizing calls and syncing tasks. Many platforms are convoluted and difficult to manage. Team members get bogged down by administrative tasks instead of staying productive.

It looks as though the novel coronavirus and social distancing guidelines are here to stay for a while. So companies of all sizes and industries are scrambling to adapt to a new reality in which everything from morning meetings to large-scale presentations are done entirely online. It looks like this is going to be the new normal for the foreseeable future.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

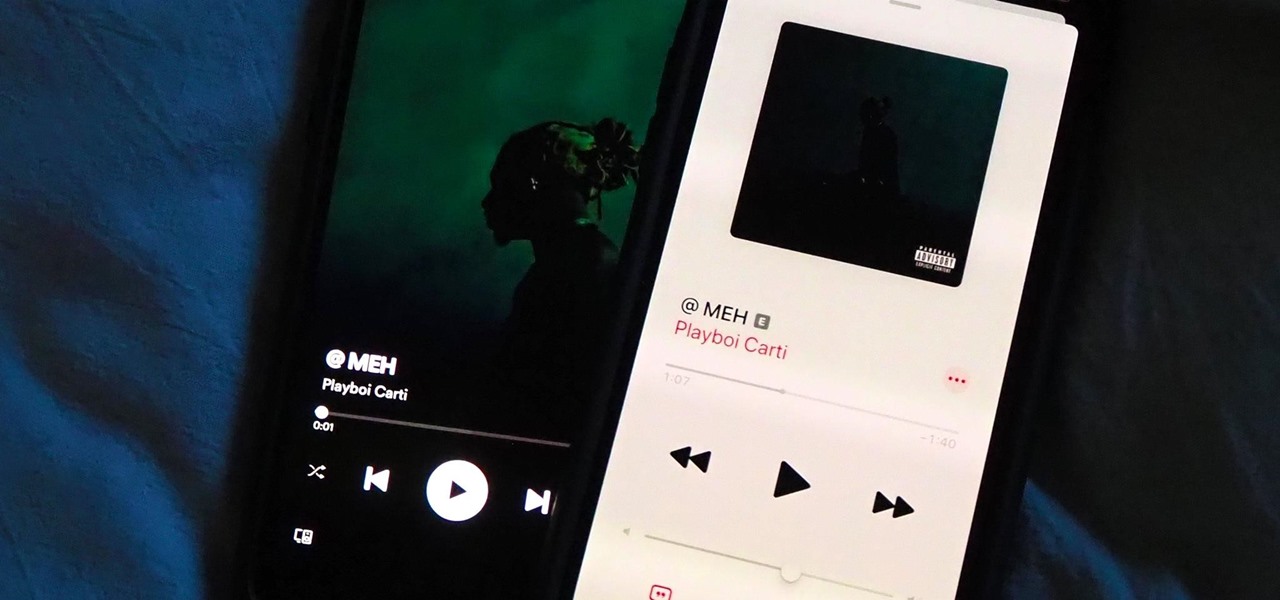
To share a song or album to family and friends, it's as easy as copying its link in the app and pasting that into a message. However, not everyone uses the same music streaming service, so a link to an Apple Music song won't do a Spotify, Tidal, Pandora, Deezer, or YouTube Music subscriber any good. If you're on an iPhone, though, there's an easy way to convert links from one service to another.

With more digital content than ever, the search feature on smart TVs is essential. But typing is such a terrible experience when you're forced to use voice dictation or peck around with the remote control. Thankfully, there's a better way.

A modern iPhone is capable of running sophisticated, exquisitely-rendered games that rival titles on current-generation consoles. However, there is some value in classic video game titles, whether you grew up playing games on the Atari 2600, Nintendo Entertainment System, and Sega Genesis or not.

Every Galaxy S20 sold in the US — even the S20+ and S20 Ultra — simply can't be rooted. With the bootloader permanently locked, you miss out on the world of rooting and the customization it opens up, but modifications are still possible.

Whether you're trying to become an influencer or just want to share better photos and videos, the best camera to start with is your smartphone. It is likely the only camera you always have on you and it's probably capable of excellent pictures and video capture. But with a little help, it could definitely be better.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

In our comparison of the best gaming phones in 2019, the winner actually surprised us. A phone that most people don't know about from a brand you probably haven't heard of ended up as the clear winner. But how? Well, it ticked so many flagship boxes despite its midrange price tag.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

Since the Razer Phone's announcement in 2017, we've seen a new subgroup of phones emerge. Gaming phones are now a thing, leading to companies like ASUS creating phones that are thoroughly optimized for the mobile gaming experience. And with their second iteration, they perfected it.

For those with small hands, smartphones have gotten out of control as of late. Nearly every flagship phone is over six inches in length, so many are forced to use phones that are too big for them and hope they don't fall. Well, thanks to one developer, using these phones can be a lot easier.

When I first found out about Nreal, back in the spring of 2018, the most interesting thing about the company's story was the founder's background. Chi Xu, the CEO and founder of Nreal, previously worked at Magic Leap as a software engineer.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

Next to Apple, Snap is currently one of the most important companies on the planet in terms of delivering products that are moving augmented reality into the mainstream. That's why it's no surprise that Facebook, which is also focused on AR and tried to acquire the company for $3 billion several years ago, duplicates many of the smaller company's features.

If you record yourself for a vlog or story post using your selfie camera, it can be challenging to stay on message. You might worry too much about the way you look or sound to focus on what you want to say. Using a script can help, but looking away from the camera to read is unprofessional, even on social platforms like Instagram. What you need is a teleprompter, and there are apps for that.

Nowadays, our phones are capable of just more than 30 fps video. Phones like the Galaxy S10 can shoot 4K at 60 fps, even on the front camera. Slow motion functionality has recently started to appear on more and more devices — but as you may have noticed, the quality of the feature differs from phone to phone.

On Monday, Apple unveiled its Apple Card, the company's boldest move yet toward becoming a truly mainstream mobile payments company. And the product has vast implications for our augmented reality future, some of which may not be immediately obvious to many.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

As I've mentioned in recent days, it was refreshing to discover that Microsoft's HoloLens 2 stage production was every bit as accurate as presented (check out my hands-on test of the device for more on that).

While Microsoft dominated the augmented reality news at this year's Mobile World Congress, a small AR startup we've covered in the past arrived in Barcelona, Spain, to unveil the next phase of its mission.

Switching phones has never been easier. Google backs up most of your app data on the cloud, which can then be restored onto your new phone. Sadly, Signal doesn't use this feature since it could compromise your security. Instead, Signal stores encrypted backups locally, requiring a bit of work to restore these messages.

Traditionally, if you were looking for end-to-end encrypted messaging, you'd stick with something like iMessage, WhatsApp, or Signal. However, if you already use Facebook Messenger, you have all you need for truly private chats with its built-in E2E encryption. It's available to all users, on Android and iOS — you just need to know where to look.

Stumbling upon a specifically tailored advertisement on your iPhone can be a bit disconcerting. But that's what happens when you let advertisers track your data. Some of you may appreciate more relevant ads in apps, but the rest of you might consider it a straight-up privacy invasion.

Every photo you take is brimming with metadata such as iPhone model, date and time, shooting modes, focal length, shutter speed, flash use, and geolocation information. Share these pictures with friends, family, or acquaintances via texts, emails, or another direct share method, and you unwittingly share your location data. Even sharing via apps and social media sites can compromise your privacy.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

Mystery is a tricky thing. Used correctly, it can give onlookers the impression that wondrous and perhaps valuable things are afoot. However, once the veil of suspension of disbelief is removed in any significant way, that same mystery can quickly turn into not just skepticism, but outright anger at what may have seemed like an attempt to dupe trusting onlookers.

By now, you've probably already seen Andy Serkis and his performance capture demo for Magic Leap. And sure, marrying motion capture acting and augmented reality sounds compelling, but how does it really work as an experience?

These days, it seems new phones get announced every other week. We've grown accustomed to glossing over the specs, looking at some press renders, then moving on to check out the next phone. If you had done this in September 2008, you might have overlooked what would become one of the most important phones of all time.

One of the primary marketing tactics used by Magic Leap in promoting the Magic Leap One was selling early adopters on the "magic" contained within the device. On Thursday, some of that magic was uncovered as the Magic Leap One was completely disassembled by repair engineers, revealing the delicate innards of the device and detailing how it delivers its augmented reality experiences.

I've had a few days to live with the Magic Leap One, and it's time to finally weigh in with some thoughts as someone who has been tracking this company from the beginning, for almost five years now.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing man-in-the-middle attacks.