
SHOT ON 7D: 2010 SXSW Grand Jury Prize Winner
Tiny Furniture directed by, written and starring Lena Durham. Film shot on 7D wins SxSW juried “best film” prize


Tiny Furniture directed by, written and starring Lena Durham. Film shot on 7D wins SxSW juried “best film” prize

In this sports video tutorial, Adrian Heath, Head Coach of Austin Aztex explains how to defend a soccer corner kick. Corner is awarded to the opponent when the ball goes over the goal line after touching a defender. If the ball is close to the goal post, the goal keeper catches the ball. In case the ball is kicked wide of the goal post and lands in the penalty area, a defender kicks the ball out over the side line or passes to another member of the defending team. If the ball is directed slig...

Not sure when this might come in handy, but I'm a fan of these silly DIY edible googly eyes. Tutorial courtesy of Evil Mad Scientists:

Need some advice on fly fishing? Fly fishing is a distinct and ancient angling method of fishing, most notably as a method of catching trout or salmon. Fly fishing is also well employed today for a large variety of species other than trout and salmon, including pike, bass, panfish, grayling, carp, redfish, snook, tarpon, bonefish, and striped bass.
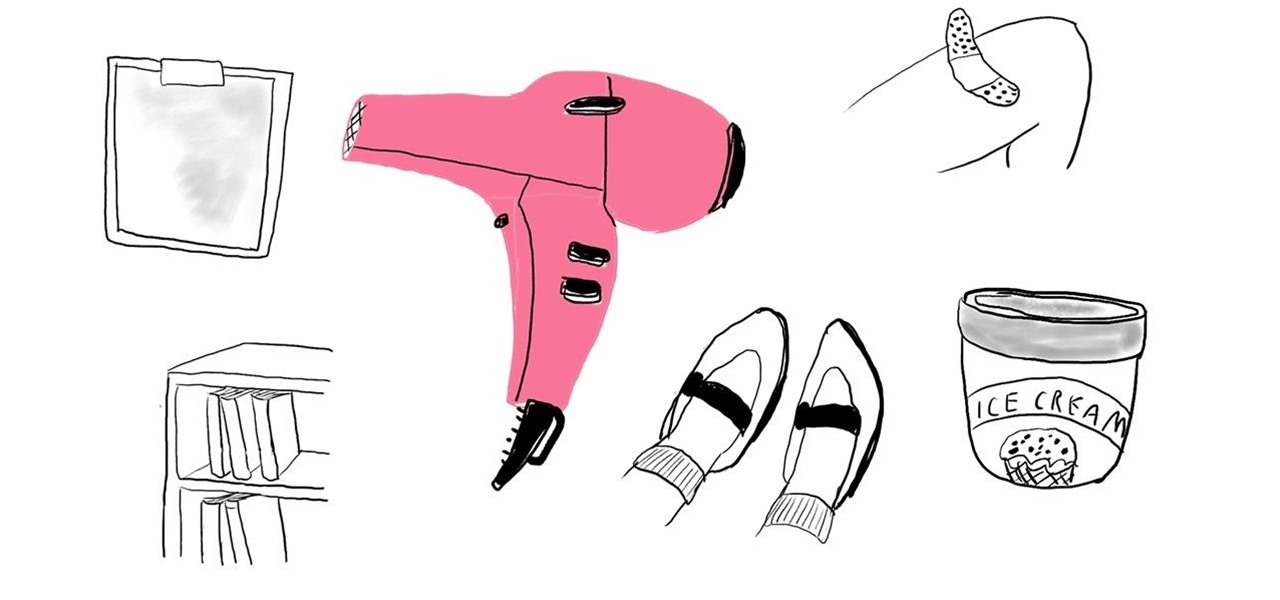
If your newly purchased shoes are feeling too tight, you can use a hair dryer to add more wiggle room for your feet. Simply wear your shoes with socks, and then direct the warm currents of a hair dryer at your feet, focusing on the areas that feel pinched.

Need to heal your unsightly acne scars? For a quick and easy treatment, dab a little vitamin E gel onto affected area overnight daily until scars begin to fade. You can also use lemon juice, baking soda, aloe vera, and apple cider vinegar with honey.
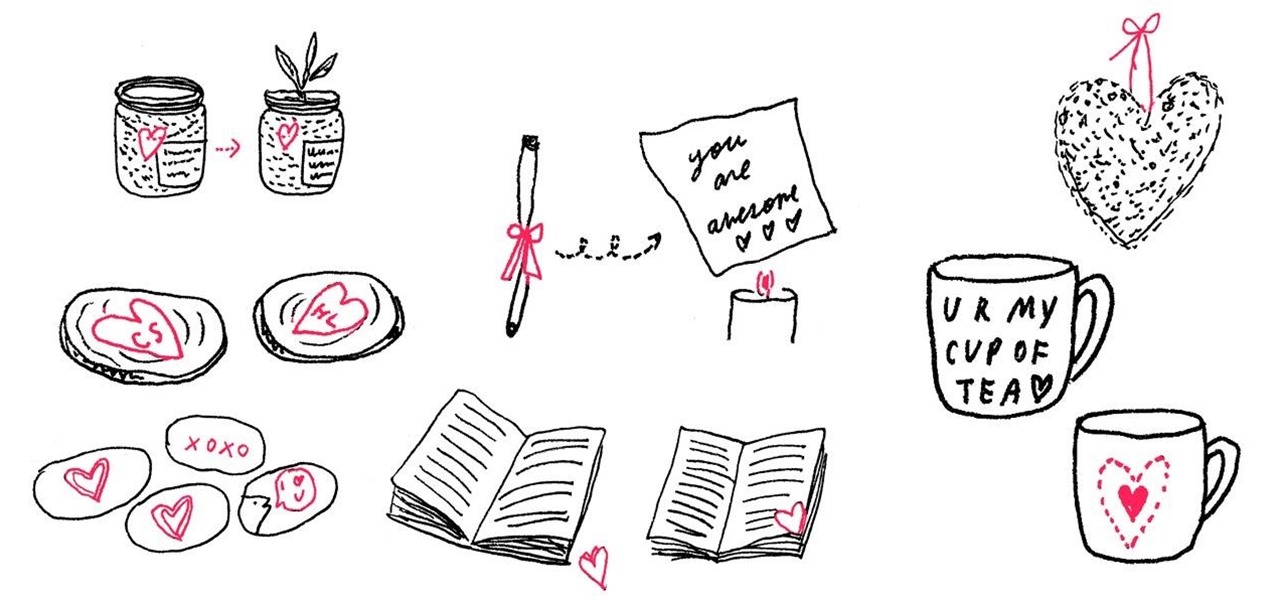
Tell the awesome person in your life how much you love him or her by writing a secret Valentine's Day message in invisible ink, which can then only be revealed by heating the paper over a flame or a hot light bulb.
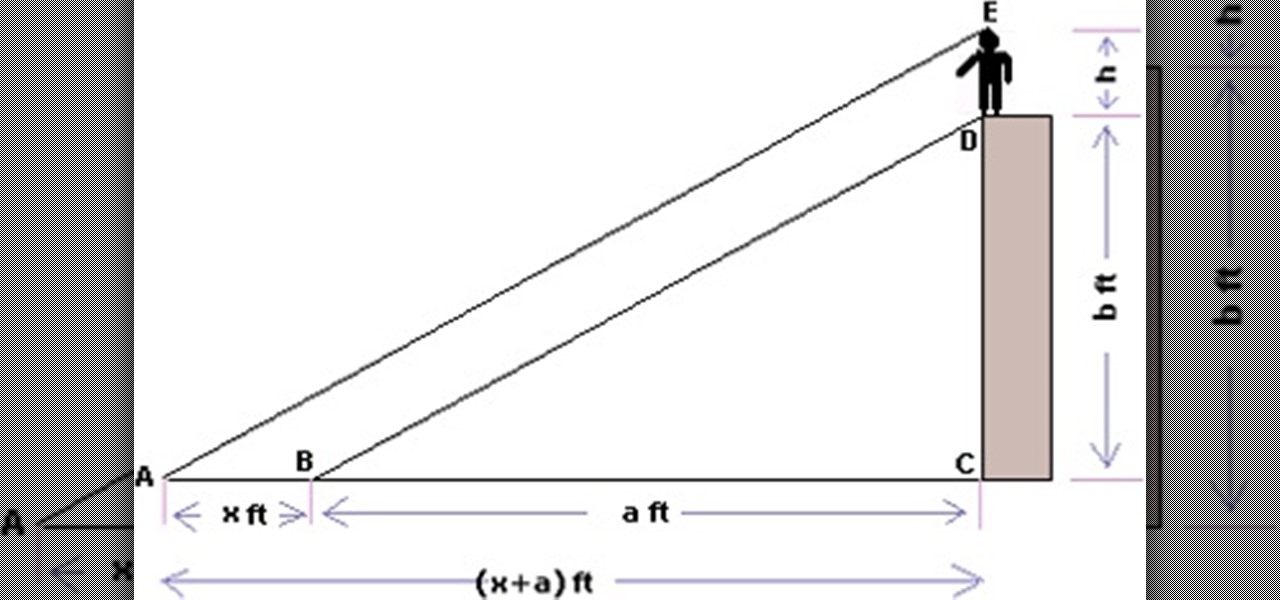
In this how to you will learn how to measure things indirectly. Indirect measurement is when you calculate something's measurement by measure the shadow. First, all of your measurement have to be taken around the same time. Next, measure your height. After, measure the object's shadow. After put the tip's of your toes on the edge of an object's shadow. Now you just use a proportion to solve what the height is. Here is a link to help you. Indirect Measurement - Math Dictionary.

Direct current (DC) by definition flows in one direction. Alternating current (AC), on the other hand, periodically changes direction, or reverses polarity. It is indeed possible for a portion of a circuit that is normally DC to periodically change direction, or reverse polarity like an AC circuit.

Anonymous U.S. officials are quoted by the NY Times stating explicitly that a Hezbollah suicide bomber attacked the Israeli tourist bus yesterday. While this is entirely possible, I think we should remember the bizarre bombing plot of a few months ago in which a small-time Iranian drug dealer was alleged by the Justice Department to have direct links to the Revolutionary Guards, and to have plotted the assassination of the Saudi ambassador. By the way, this is the same person, Bandar ibn Sult...

Gun shots, dog mauling, compound fractures, partially severed limbs... Sometimes direct pressure isn't enough to cut the blood loss. This U.S. Army field instructional is a fascinating and thorough medic's walkthrough. Learn exactly how to apply a lifesaving tourniquet to an injured limb. No first aid poster can compete with the unmistakable deadpan of a military issue instructional. Only the American Army could deliver such eyewitness first aid advice. Bookmark this. If you're ever stuck bet...

With an impressive series of viral music videos to their name, it is no surprise that the latest video from indie rockers OK Go is another hit. The video is directed by James Frost, in collaboration with Syyn Labs, a collective of engineers that work on elaborate art projects. A huge Rube Goldberg machine was built in a warehouse, for a one-take video for the song This Too Shall Pass.

Kirsten Dunst is turning Japanese in short skirts and thigh highs. The art world crashes Hollywood in this video piece starring Dunst, directed by McG and produced by world renown Japanese artist Takashi Murakami.

As a web developer, I often read articles about hackers (from the lowly to the knowledgeable) infiltrating websites via the dreaded 'SQL Injection' method and completely taking control, changing, gaining access, or destroying the owner's data. As a fellow web developer, I'm sure you want to know how to protect against it. Well, here it is! In this article, you will find out what SQL Injection is, what you can do to protect against it, and additional recommendations that are easy to do and onl...

Is there a certain someone whose pictures and status updates you would rather not see? Like, ever? Wish you could hide a person on Facebook without publicly defriending him or her? Your new best friend is a Michel Gondry-inspired Google Chrome extension named Eternal Sunshine.

Business owners and marketeers are diverting from traditional marketing techniques, including billboards, radio and TV advertising, brochures, and any other outdoor promotions, to cheaper but effective Internet marketing strategies. Under the new arrangement, business owners reach out to the final consumers through advertising on the World Wide Web.

This Animal Welfare Foundation two-part video tutorial is from expert veterinary staff demonstrating the correct procedures for handling small mammals for clinical examination and medication. Its aim is to show that the primary consideration should be for the the welfare of the animal. This video guide will show you practical animal handling for a rat.

This article is all about creating content. This is a very important concept to grasp because the content that you will learn how to create is going to be the basis for how you will advertise and promote your website. Content, meaning articles, videos, and even podcasts. Content is now really the new advertising. Instead of traditional types of advertising and instead of the traditional separation between editorial content and advertising, that has gone the way of the dinosaur.

For a moment, picture a situation where you want to host some files or images, but you do not want it traced back to you. Perhaps you're working on a project with others and need secure data storage. Anonymity is the new shield of the 21st century—and you best protect yourself. As always here at Null Byte, we are trying to make that happen. Before someone can learn how to root a box, they need to learn how not to be found. I can not stress that point enough.

Installing the Software Download the PC/Mac client from Dropbox for your computer. When installing the software you will also be prompted to create an account. Please do so at this point. This account gives you free access to 2 gigabytes (gb) of cloud storage that can be accessed from any PC/Mac or Dropbox Enabled Device.

For a professional photographer in the market for good business management software, Canon offers the Studio solutions package. This tutorial series outlines all the various functions and features of Studio Solutions, such as order processing, client files and managing your various photos for each product. Manage your professional photography business using Canon Studio Solutions - Part 1 of 8.

Follow these few step by step instructions to learn how to activate the junk mail filter in Entourage for Mac.

If you know anything about search engine optimization and online marketing then you know that having as many links going into your site from good sources is very important. And if you’re not really experienced at building links or SEO in general then you might not know the best way to get good links for your site. So please read on and I’ll present to you what I feel is the best way to get good quality links for your site.

VNC is a great protocol that you can use on Windows and Linux machines to remotely control computers. This is useful if you need to control your computer when away from home, help your grandma check her email, or help a client with a disk cleanup. VNC is secure in the sense that it requires authentication in order to make the connection, but after that, the data is sent over the internet unencrypted. This means that an attacker could sniff your traffic and snoop everything that's going on. Th...

Having an SSH or Secure SHell to tunnel your traffic through is something we have talked about many times at Null Byte. As we know, it allows us to securely route and encrypt our traffic through a remote server, effectively anonymizing us and protecting our traffic from all forms of analysis—simultaneously. We have gone over how to make a home SSH tunnel. However, the question has come up, "How can I get an SSH tunnel to somewhere other than my computer?" This would be useful in a situation w...

Big name individual hackers and hacker groups everywhere in the news are getting caught and thrown in jail. Everytime I see something like this happen, I won't lie, I get a little sad. Then I wonder, how are these guys getting caught? If a group like LulzSec, with all the fame and "1337-ness" can get caught, I think my hacker comrades are doing something wrong.

With so many wireless iOS networking apps for the iPhone, iPad, and iPod touch available, there’s very little reason to connect any of these devices to iTunes, except to update the software. Besides, importing and exporting photos using iTunes has never been one of the best features of Apple‘s mobile device process. Let me introduce you to 5 useful apps for importing and exporting photos to and from your iOS device(s).

Whenever we get together and hang, my friends are always talkin' me into doin' the famed truffle shuffle from the movie 'The Goonies', made famous by the character Chunk. Well, this is where I got the idea for this prank.

Because soccer players strike the ball into the goal with quick speed, the goalkeepers have to be even faster in order to prevent a score. With such agile goalkeepers, however, how do soccer stars manage to get a goal in at all?

Square dancing, a fun American pastime! Learn square dance steps with this instructional animation. Fun fact about square dancing: 19 U.S. States deem it their official dance. Square dance is a folk dance with roots in Europe, eventually spreading to the states & becoming more of an iconic dance there. Square dancing consists of 4 couples arranged in a square formation. This square dance lesson is clear and to the point. Search "square dance instructional animation" on Wonderhowto for more sq...

Square dancing, a fun American pastime! Learn square dance steps with this instructional animation. Fun fact about square dancing: 19 U.S. States deem it their official dance. Square dance is a folk dance with roots in Europe, eventually spreading to the states & becoming more of an iconic dance there. Square dancing consists of 4 couples arranged in a square formation. This square dance lesson is clear and to the point. Search "square dance instructional animation" on Wonderhowto for more sq...

Square dancing, a fun American pastime! Learn square dance steps with this instructional animation. Fun fact about square dancing: 19 U.S. States deem it their official dance. Square dance is a folk dance with roots in Europe, eventually spreading to the states & becoming more of an iconic dance there. Square dancing consists of 4 couples arranged in a square formation. This square dance lesson is clear and to the point. Search "square dance instructional animation" on Wonderhowto for more sq...

This creamy sauce goes best with a pan-seared rainbow trout, but you could also find other uses for this elegant seafood sauce, it doesn't have to stop at trout. This video recipe will show you just how to make the versatile sauce with rendered bacon and shallots, deglazed with aged sherry and veal stock, and thickened with butter. Keith Pooler of Bergamot Restaurant shows you the trick.
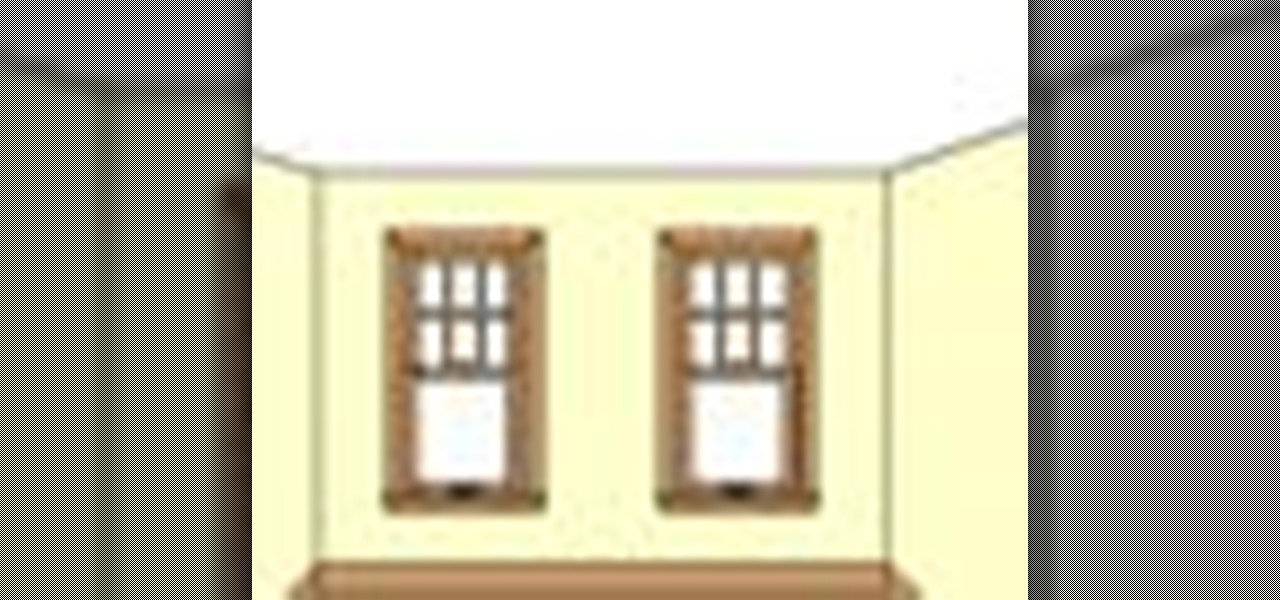
Installing recessed lighting into your kitchen or living room creates an immediate update to the look of your home! Recessed lighting is very low-key, makes a subtle statement, and yet is elegantly modern. If you are looking for an update to your home's lighting, think "recessed."

Single-cell electroporation (SCE) is a specialized technique allowing the delivery of DNA or other macromolecules into individual cells within intact tissue, including in vivo preparations. The distinct advantage of this technique is that experimental manipulations may be performed on individual cells while leaving the surrounding tissue unaltered, thereby distinguishing cell-autonomous effects from those resulting from global treatments. When combined with advanced in vivo imaging techniques...

Watch this video from This Old House to learn how to create zones in a hot water system. Steps:

Watch this video from This Old House to learn how to clear a clogged drain. Steps:

SSH is amazing, and we praise its existence on Null Byte for many reasons. Notably, it allows us to reroute our traffic through encrypted ports on our local host to be sent to its destination when on the go. You can even control your home computers remotely over a secure and encrypted connection. This is handy for a multitude of reasons.

A proxy is a server that lets a client to connect to it and forward its traffic. This enables a certain "layer" of protection by masking your IP. An IP address can be used to learn your location and track you on the Internet, thus eliminating any form of anonymity that you may have.

Warning Don't torrent things that you do not have the rights to torrent. Everything I torrent, I have a physical copy of, and just want a copy on my computer without causing wear-and-tear on my DVD drive's laser. Piracy is naughty.