Starcraft 2, like it's predecessor before it, has a very robust level editor that allows you, the DIY modder, to create nearly any scenario within the bounds of the Starcraft 2 engine that you could imagine. We have compiled videos on how to do all sorts of fun things with it, from making RPG's and Tower Defense games to just making you dream Starcraft 2 level. This video will teach you how to make a Starship Troopers (film, not book) style map where a group of Terrans have to defend a remote...

Starcraft 2, like it's predecessor before it, has a very robust level editor that allows you, the DIY modder, to create nearly any scenario within the bounds of the Starcraft 2 engine that you could imagine. We have compiled videos on how to do all sorts of fun things with it, from making RPG's and Tower Defense games to just making you dream Starcraft 2 level. This video will teach you how to create a basic Warcraft 3 style hero using the Starcraft 2 patch 13 beta editor. He won't be quite a...

Starcraft 2, like it's predecessor before it, has a very robust level editor that allows you, the DIY modder, to create nearly any scenario within the bounds of the Starcraft 2 engine that you could imagine. We have compiled videos on how to do all sorts of fun things with it, from making RPG's and Tower Defense games to just making you dream Starcraft 2 level. This video will teach you the basics of using the Starcraft 2 Editor (current as of patch 13). It will teach you how to use the terra...
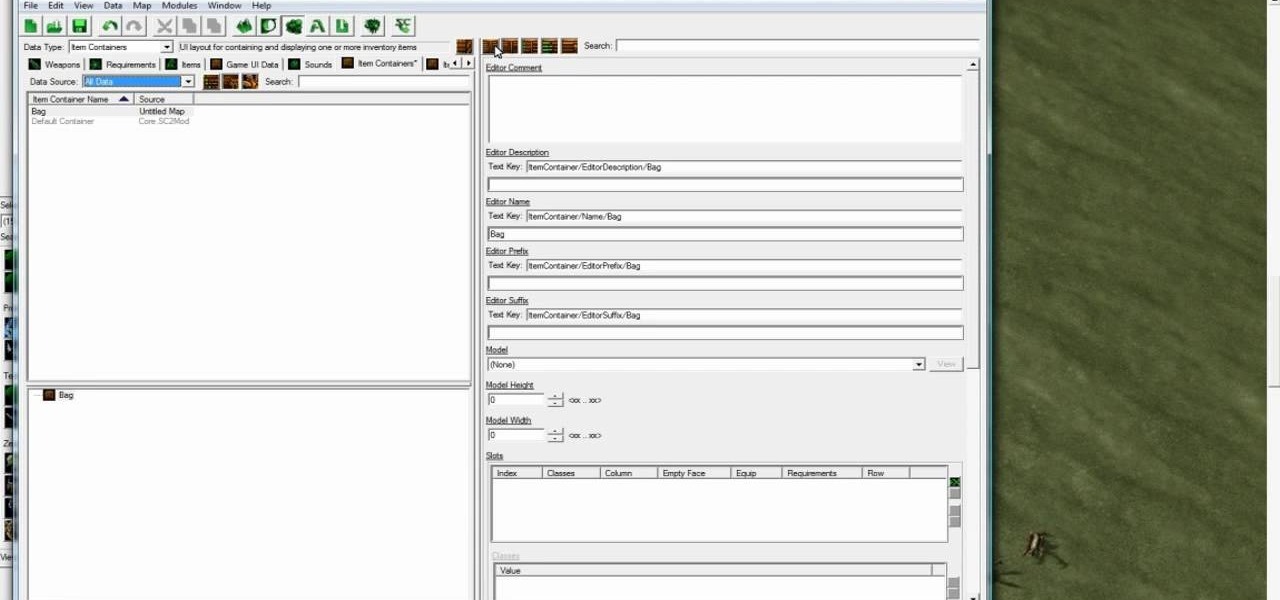
Starcraft 2, like it's predecessor before it, has a very robust level editor that allows you, the DIY modder, to create nearly any scenario within the bounds of the Starcraft 2 engine that you could imagine. We have compiled videos on how to do all sorts of fun things with it, from making RPG's and Tower Defense games to just making you dream Starcraft 2 level. This video will teach you how to work with items and loot in your custom levels. You'll learn how to create items, create ancillary i...

Do you know what an idiom is? If you don't, this English lesson is sure to make you an expert on idiom usage.
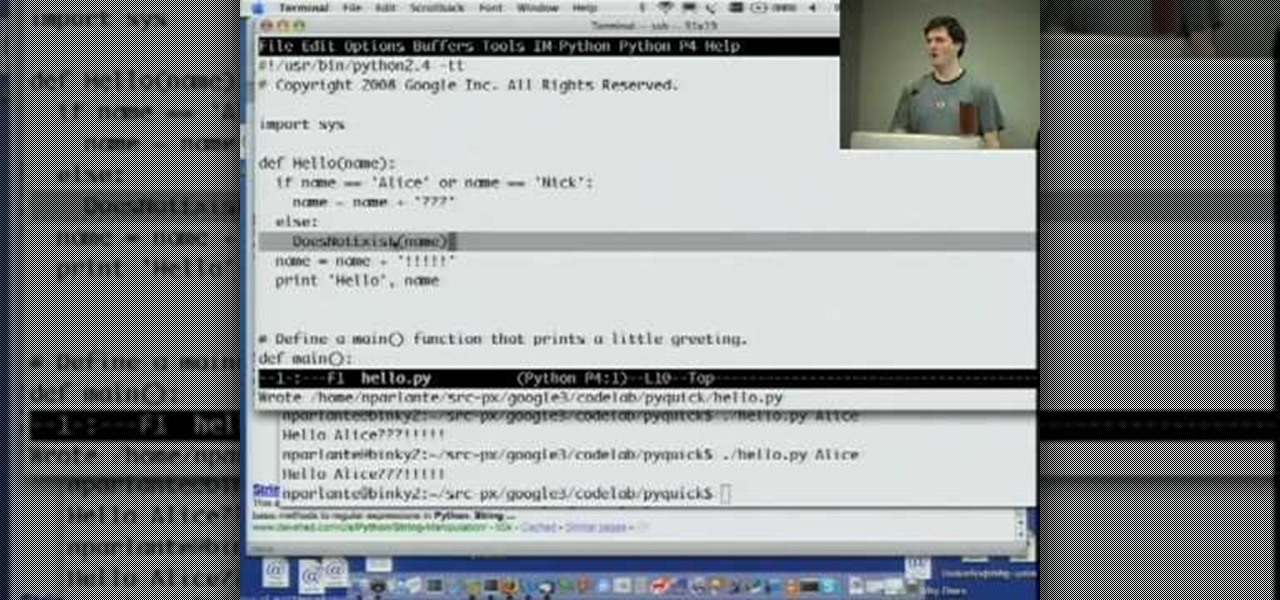
Welcome to Google's Python Class – a seven-segment, two-part free virtual class for people with a little bit of programming experience who want to learn Python. The class includes written materials, lecture videos, and lots of code exercises to practice Python coding. The first exercises work on basic Python concepts like strings and lists, building up to the later exercises which are full programs dealing with text files, processes, and http connections. The class is geared for people who ha...

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.

Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills.

The OnePlus 5 had been in the hands of the public for a meager twenty hours before developers on XDA released a custom recovery image for it, and the 5T had a similar trajectory. The installation process is simple enough, but it can be somewhat confusing if you're new to modding Android.

Welcome back to this series on making physical objects come to life on HoloLens with Vuforia. Now that we've set up Vuforia and readied our ImageTarget and camera system, we can see our work come to life. Because in the end, is that not one of the main driving forces when developing—that Frankenstein-like sensation of bringing something to life that was not there before?

As pentesters and hackers, we're going to be working with text frequently — wordlists, configuration files, etc. A lot of this we'll be doing on our machine, where we have access to whatever editor we prefer. The rest of it will be on remote machines, where the tools for editing will be limited. If nano is installed, we have an easy-to-use terminal text editor, but it isn't very powerful.

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

Check out this video of corporate/industrial photographer David Tejada's small location lighting kit and what criteria he used to compile it. Get tips from this how-to video.

A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).

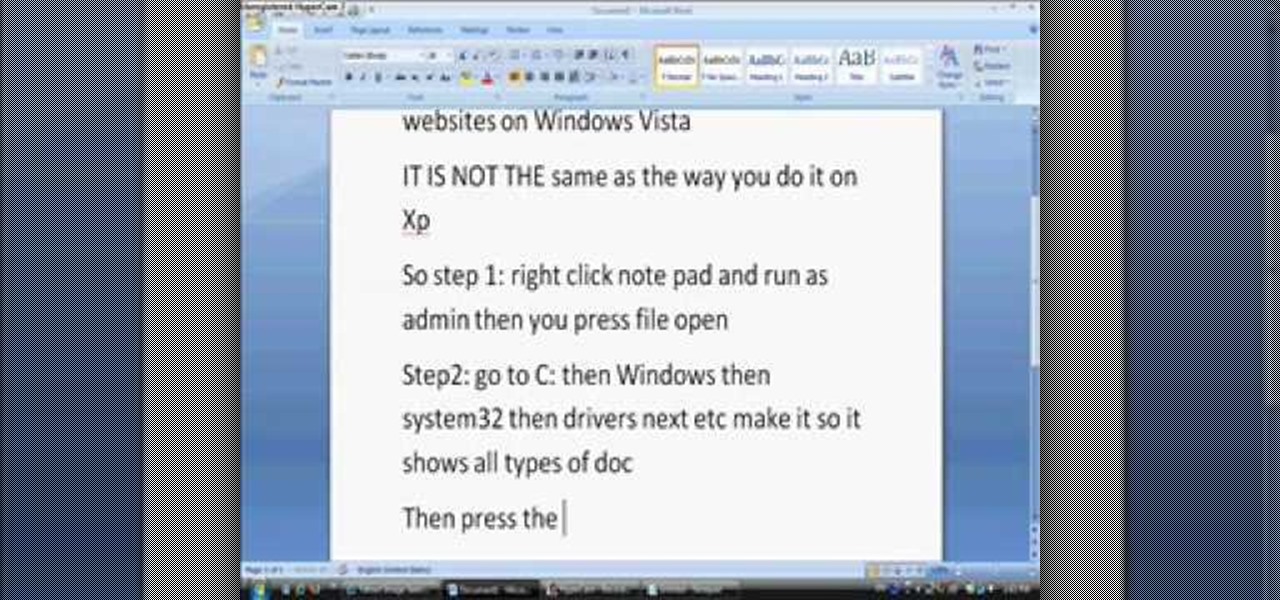
In this tutorial, we learn how to block websites on Windows Vista. First, you will right click on the notepad and then run as admin. From here, you will click "file open". Then, go to the C drive and open up windows. Then, you will go to the system and find the drivers, then click on the host file. From here, go to the second local host and press enter twice. Then, type in "127.0.0.1" and press tab. Then insert all the directories that you want to block. From here, you will be finished blocki...

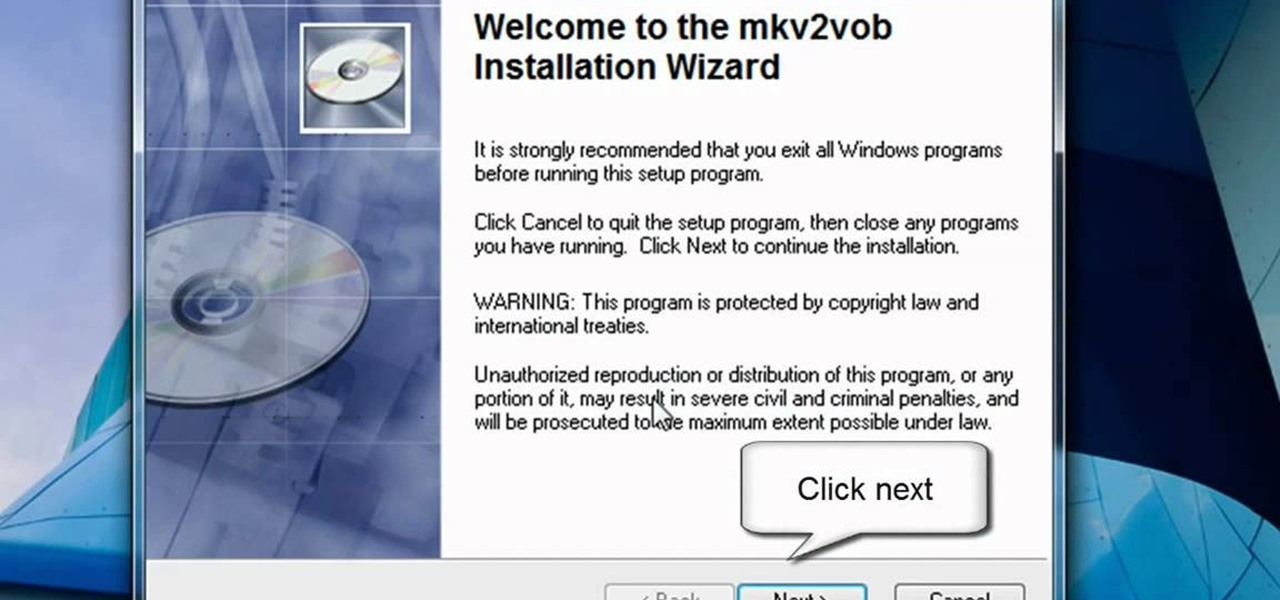
In this video tutorial, viewers learn how to play MKV videos on the PS3 using the MKV2VOB software. Begin by downloading the MKV2VOB programs from the link in the video description. Once downloaded, install it on your computer. Now open the program. Go the Configuration tab and change the setting to the same as the video. Then click on the Add File tab and select Browse under Source File. Find your MKV file and select Open. Then under Destination Directory, select where you want your file to ...

In this video the instructor shows how to hide any kind of file in a .Jpeg image file. To do this take the image in a new folder. Go to start button and then to run. Type cmd in the run and hit enter to open the command prompt. Now browse to the directory that contains the picture and also the file that you want to store using the CD command. Type the command to create our required file as shown in the video. Now a new file will be created that contains your image as well as the file that you...

Brizdo shows you how to download free music from MySpace using the Real player in this walk through video. This video shows how to first select download and install the real player that is most suitable for free use. Next by doing a MySpace search for the artist and visiting the MySpace page of that artist the music track that are on the artist's page can be downloaded by a few clicks. The downloaded tracks can be found in the Real players download directory usually in 'My Documents'.

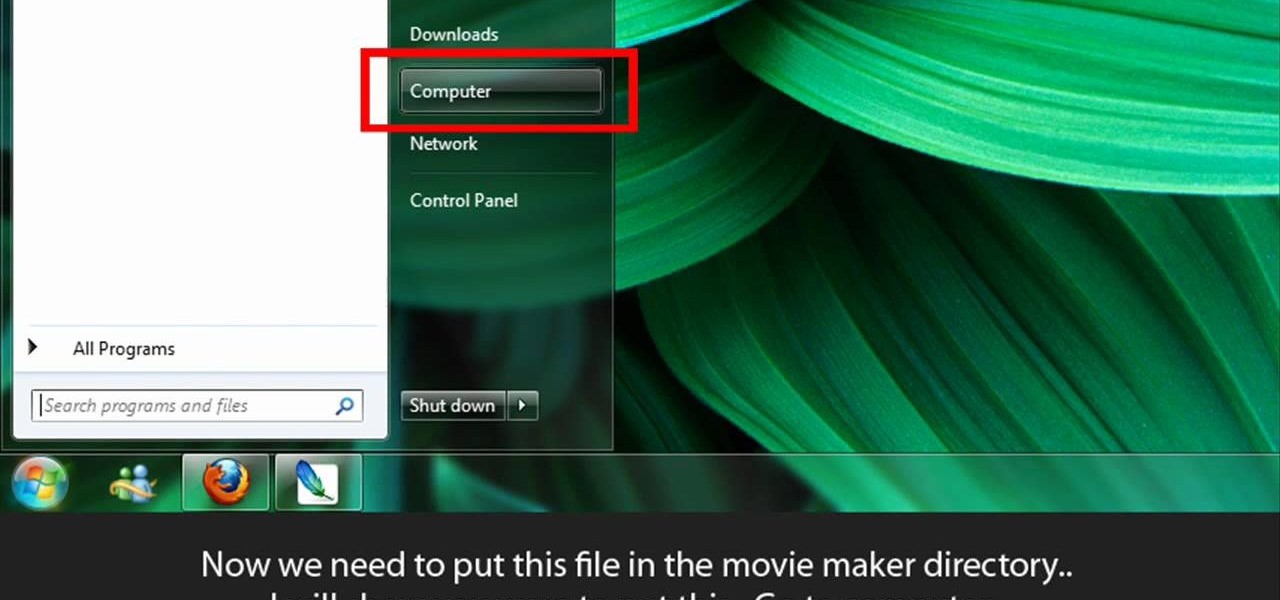
Learn to make HD Video With Windows XP's Movie Maker with this video tutorial. First, go to PapaJohn, there is WMV-HD at the left hand side of the screen. Expand that and click on the Introduction, then 1280*720 link. Download begins, save file on you hard drive. It has to be in the movie maker directory. It is in Program Files - Movie Maker - Shared Link. File must be added in the folder Profiles. Put it there, and if you don`t have such folder, create it. OK, we can start movie maker and ma...

In this tutorial video, we show you how to jailbreak Apple's latest device the iPhone 3G to start the process you need to do the following:

Apple's iOS 15.4 and iPadOS 15.4 updates have a pleasant surprise for iCloud Mail users and everybody that use the Mail app as their primary email client for AOL, Gmail, Outlook, Yahoo, and other third-party email services.

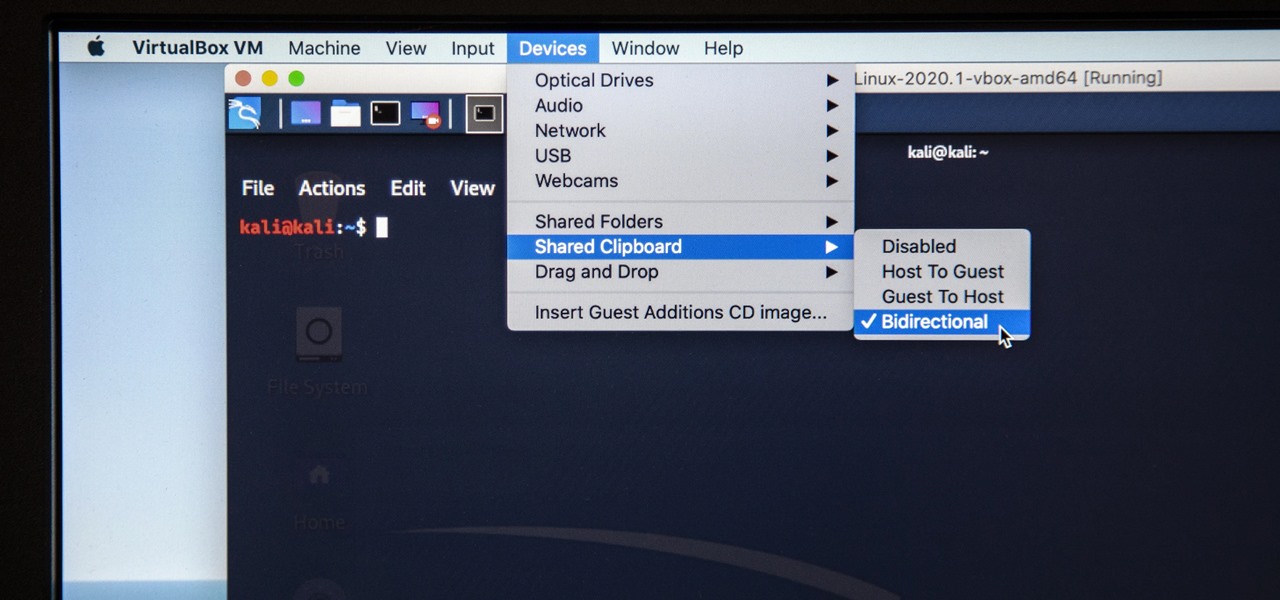
Last week, I updated VirtualBox on my computer since I had skipped a few versions, then I could no longer copy text or paste text from my Kali virtual machine to my host OS and vice versa. Installing the Guest Additions didn't seem to do anything, and the bidirectional shared clipboard was enabled, but there was one thing that did work for me that may help you out too if you experience the issue.

Android 10's new dark mode is a pleasure to behold for longtime users. Ever since OLED panels became widespread, we've been clamoring for the feature. But now that we have it, there's a new problem: it doesn't turn on automatically based on time of day. Thankfully, a simple app can turn dark mode into a true night mode.

If you ever want to root your OnePlus 6, install TWRP, get Magisk and Xposed, or flash a custom ROM, the first thing you'll need to do is unlock your bootloader.

Using Hydra, Ncrack, and other brute-forcing tools to crack passwords for the first time can be frustrating and confusing. To ease into the process, let's discuss automating and optimizing brute-force attacks for potentially vulnerable services such as SMTP, SSH, IMAP, and FTP discovered by Nmap, a popular network scanning utility.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

Essential just dropped the Oreo Beta Program for their flagship PH-1 phone. Users have been eagerly awaiting this update as the early Nougat builds of the PH-1 software have suffered from numerous performance issues and lag. The good news is that you can grab the Oreo update today with a few simple steps.

To really personalize your HTC 10, you'll need to be rooted — but that can't happen unless you unlock your bootloader. Thankfully, HTC has made it relatively easy to unlock the bootloader on their 2016 flagship.

Preorders for the LG G6 have all been fulfilled, and the phone has been up for grabs at local cell phone providers for three weeks now. However, not every LG G6 was created and released equally. The T-Mobile variant of the LG G6 features an unlockable bootloader, while most other North American variants come with a tightly locked down bootloader, which effectively limits the full potential of your brand new fairly expensive phone.

SSH local forwarding is a must for covering your tracks and getting out there to do your work. Also called SSH tunneling, this process will put one or more steps between your machine and the machine you're working on, for security and other purposes. It can be a bit daunting for newbies to get down, and that's where Punchabunch comes in.

It's been little over a month since the official release of LG's latest flagship phone, the LG V20. Despite a few minor hiccups, the V20 has been attracting attention from all over for being an amazing phone. But like with most Android phones, there's no better feeling than rooting and taking complete ownership of it.

Android's flexible operating system allows for lots of customization, and one of the most common ways to add personal flair to your smartphone is to set your own ringtones and notification sounds.

Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

OS X is built upon a UNIX foundation, which grants you access to the benefits that UNIX offers, including the standard toolkit (make, gcc, clang, git, perl, svn, size, strings, id, and a lot more) via the command line developer tools, which are an essential if you're a developer. Aside from developers, the command line tools can offer benefits to normal users as well, like the ability to purge RAM for better performance.

So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - bypassing antivirus.

Greetings null-bytians. Firstly, I would like to apologize for the no images thing. I guess I can't upload them.

In this article, we will explore the basics of radare2, a powerful package that comes with Kali. We are going to write a simple program, and then disassemble it, to see what is really doing in the processor.

Welcome back, my novice hackers! As most of you know by now, a notorious commercial, legal hacking group named "Hacking Team" was recently hacked. As part of the hack, thousands of emails and other material on their servers was divulged. Among the material released were three zero-day exploits. In this tutorial, we will walk through the steps to load one of them, which has become known as the CVE-2015-5119 exploit.