Hello Hackers/Viewers, It is a new day, and you might be thinking, It is so boring, why not try to be cool with computers in front of my friends? That is why, I have made this tutorial to make fake viruses using notepad to look cool!

Hello, ladies and gents! Today I will be discussing the fun and excitement of backdoor on an OSX system.

What's the point of having a 1080p screen if you're not using it to get in some quality gaming time? Google Play is great for downloading games, but you probably already have an extensive library of games for your consoles, so use those!

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

Welcome back, my eager hackers! In recent blogs, I've demonstrated how to grab password hashes remotely using Metasploit's meterpreter and pwdump. Once we have the Windows passwords from the SAM file, we can then crack these hashes using tools such as Cain and Abel.

Sense appears on over forty Android devices, but HTC's notorious GUI was actually designed with a completely different mobile OS in mind—Windows.

In today's world of social media, there's really only two powerhouses—Facebook and Twitter. And those of you with Twitter accounts know the power of a Tweet. Getting more followers means reaching more people, but the vast majority of Tweeters are following only a handful of Twitterers themselves. Do you ever wonder why them? What's so special about these selected followed users? Is it worth it to follow them, too? That's up to you, but if you're searching for more people to follow, then it's ...

Download .net framework and install it if you do not already have it. Download DevKitPro from here and install as instructed.

In iOS 13, Apple finally took the built in Files app from an extremely rudimentary file browser to a full featured app that can serve the needs of most any user. Among the new features is the ability to compress a file or series of files into a standard ZIP archive right from your iPhone.

Yes, I understand some people may consider this a repost. However, I have been searching for this answer for 3 weeks and after reading numerous reddit post, Kali Forums post and Null byte post I finally have gotten it to work for me. I would like to compile and share this information with you guys.

Hi guys. Hope you all had a good Christmas , today i have a tutorial for you.

What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may.

In previous tutorials we have encountered these things called pointers and addresses but we still don't know what they really are. Let's learn a bit more to clear things up.

Welcome back to another tutorial on functions. Last time, we looked inside memory to see what functions looked like in the flesh and all that Assembly was pretty nasty. At least you have some exposure to it. This time, we will be examining how functions work with the stack.

Hey there, reader! In this tutorial we are going to explain how values are stored in variables as either signed or unsigned. Try to not get lost!

Hello again, ***UPDATE: Adding links to the other Two articles****

After a few months, I get so fed up with hearing the same ringtone go off alongside each new notification that I'm forced to switch things up—only to end up repeating this whole process when the new one gets played out. And I'm sure people around me are equally sick of listening to that tired old tone towards the end as well. I mean, a decade later, I'm convinced that Nokia tone is permanently implanted in my brain.

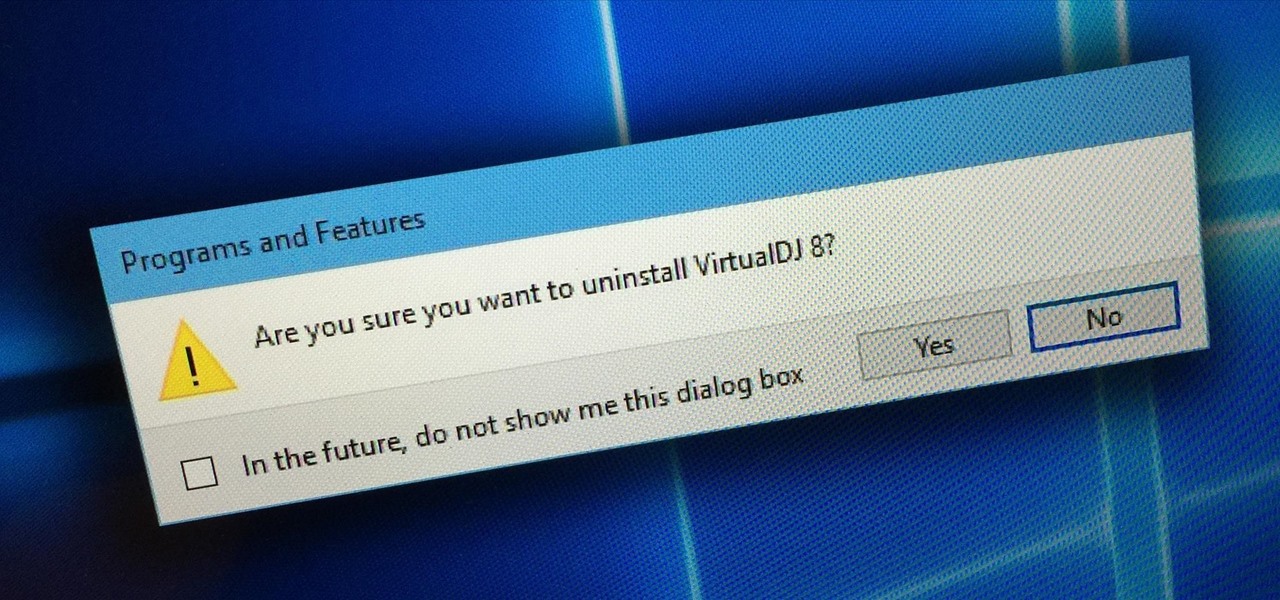
Uninstalling programs in Windows is not the nicest procedure. Some programs bundle a nice uninstaller with them which helps to ease the process. Other programs, mainly those that utilize the Windows Installer technology, begin the uninstall process right away. This can potentially be problematic for users who are trigger-happy with the mouse.

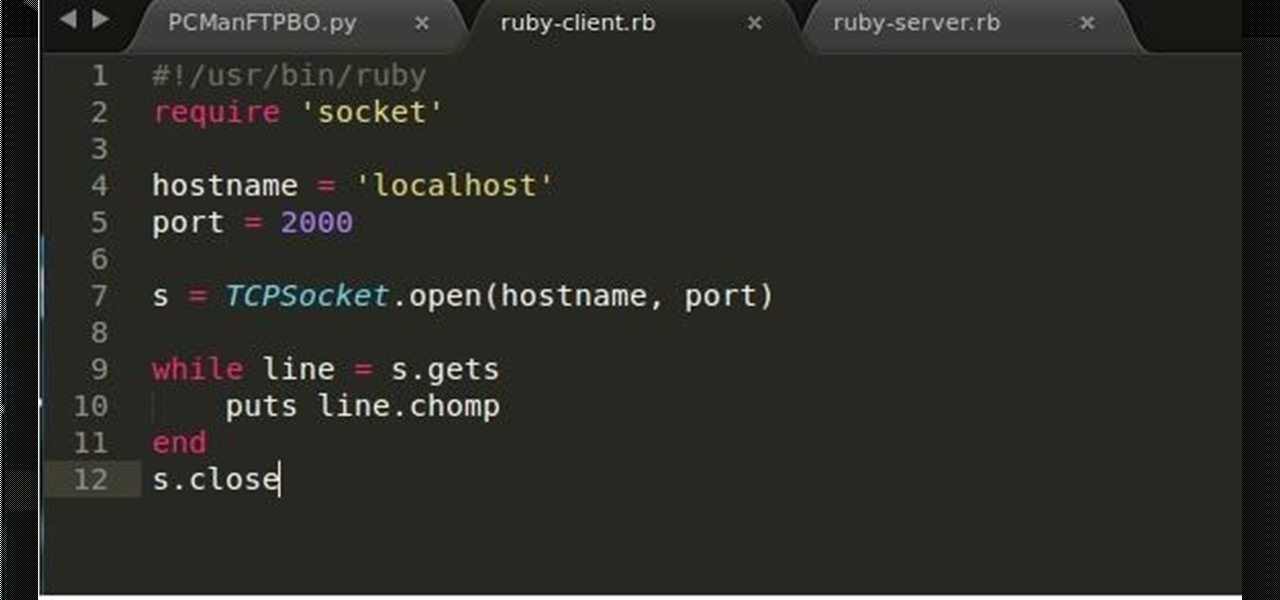
Recently, I've been learning Ruby as a second scripting language. But one topic I never covered with the many lessons online were sockets. So I did some research and came up with a very simple client/server connection that sends a string over the socket.

Hi guys. I'm here to go for level 7 now lets get it start but i apologize u all that i posted this very late but now lets rock:

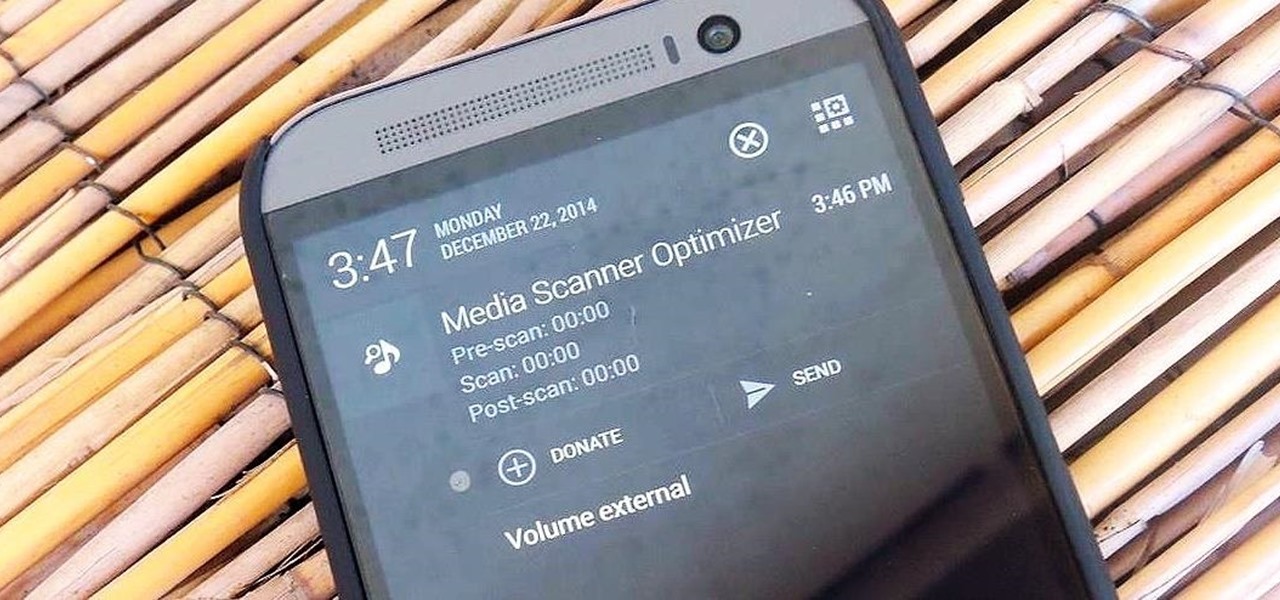
Battery life is extremely unpredictable on an Android. Finding the right ROM and kernel combo can make or break having the kind of battery that will last you all day long. Even if you do find the perfect pair, you then have to worry about apps, widgets, and other processes constantly waking your phone and draining your juice. While your media scanner isn't the biggest battery hog out there, it can definitely take a chunk out of it.

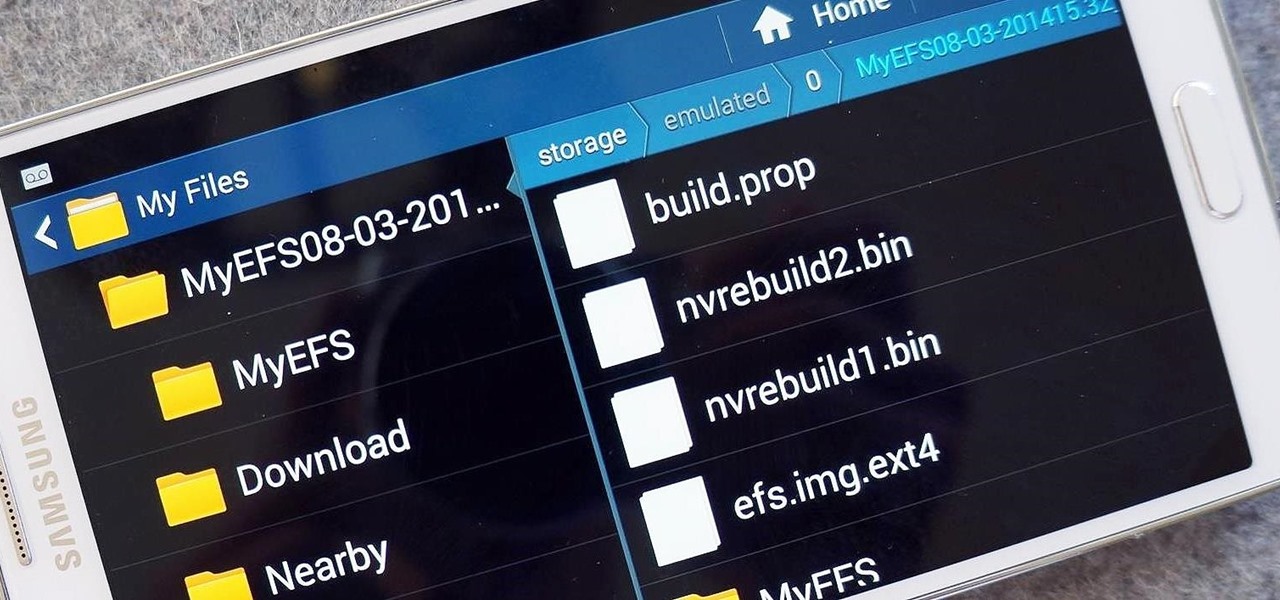
The options for customization are virtually endless when you're rooted and have an unlocked bootloader and custom recovery. However, there is always risk involved when flashing new mods or installing new ROMs. I always make backups in case something happens, but when I'm testing certain mods out, I sometimes get a damaged EFS partition.

For most of us regular folk, the only opportunity to relish in the conveniences of a maid is during hotel stays. Personally, I would love to have a maid around to help fold my clothes and sweep up those crumbs that accumulate in the corners of my kitchen, but sadly, I currently live in reality and can't afford that luxury just yet. In real life, I'm on my own.

Apple is widely known for keeping a tight grip on iOS, disallowing open-source and third-party downloads. While there are many reasons for this, the three most frequently referenced are quality control, malware prevention, and of course—money.

In this article, I'll be continuing my series on microcontrollers. If you haven't read part one, I'd recommend heading over there and reading it!

AppleScript is quite an easy scripting language to use. In this guide, I will be showing you several commands. Near the end, I will show how these can be used to create a fake virus that actually does no harm.

Starcraft 2, like it's predecessor before it, has a very robust level editor that allows you, the DIY modder, to create nearly any scenario within the bounds of the Starcraft 2 engine that you could imagine. We have compiled videos on how to do all sorts of fun things with it, from making RPG's and Tower Defense games to just making you dream Starcraft 2 level. This video will teach you how to create some cool effects for your custom map in Starcraft 2, including a voting system and a creep t...

First of all launch the program "Nero 7". Now click on "cd" and then click on "cd-rom boot'. From the new screen choose ' image file' and then click on 'browse'.Now go to the 'drive d' and select 'windowsxp-boot image' folder and then select 'boot.ima' file. Now click on 'open'. Now click on 'advanced' and then click on 'no emulation'. Select the ‘number of loaded sectors' and increase it to '4'. Now click on 'ISO' and then make sure that all the data is same as that on the tutorial.

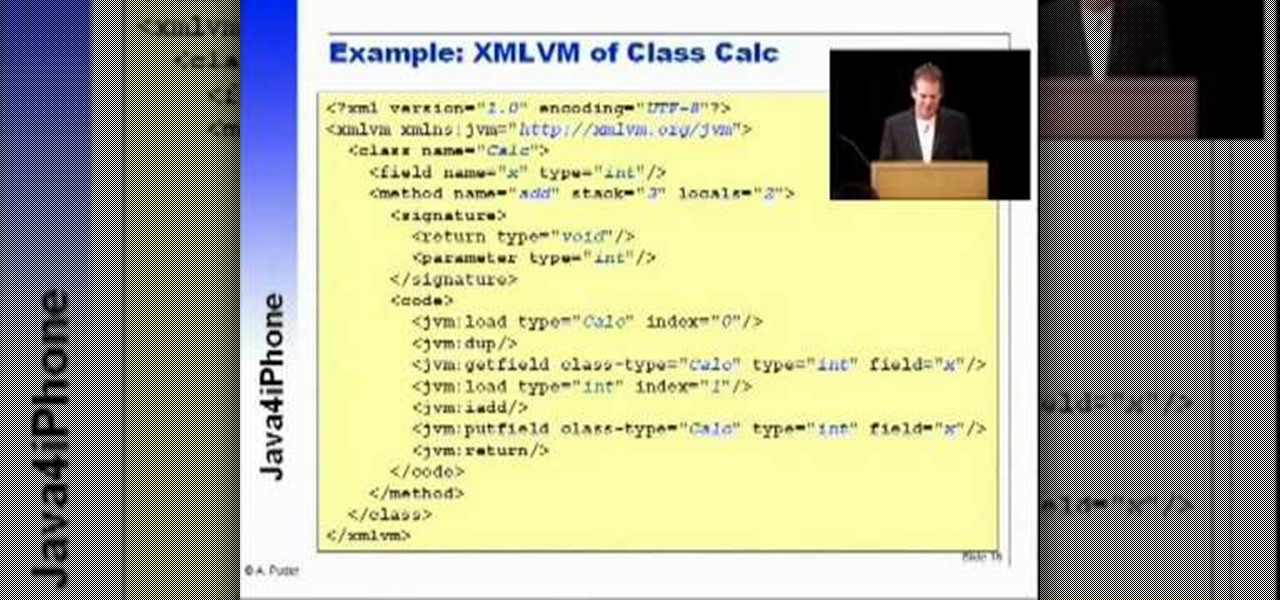
Arno Puder, a master of the XML coding field, gives a great rundown of Apple's new proprietary Java coding. This is especially helpful for Cocoa implementation

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

MouseJack vulnerabilities were disclosed over three years ago. Some wireless keyboard manufacturers have since issued firmware updates, but millions (if not billions) of keyboards remain unpatched worldwide, either because they can't be updated or because the manufacturer never bothered to issue one.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

Although the Galaxy Note 9 is an amazing phone, many members of the Android community won't even look at it. This isn't just because of the Samsung Experience skin, but the large amount of bloatware that comes with this device. However, with a little work, you can remove all of it.

As we aim for a wireless world, technology's reliance on cloud computing services is becoming more apparent every day. As 5G begins rolling out later this year and network communications become even faster and more reliable, so grows our dependency on the services offered in the cloud.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

Here are a couple of quick bits, and also a little bit of a teaser. If you know of my old YouTube channel and are a developer, you may be aware of the "Scale and Rotation System" tutorial series I did. I then started working for Next Reality and never finished it.

The OnePlus 3 and 3T are two of the most modder-friendly devices to be released in 2016. Not only that, but they're both extremely solid phones which happen to sport a very reasonable price tag. Among the things that make these devices such a joy for tinkerers is the fact that they have an unlockable bootloader, receive timely kernel source releases, and are actually quite easy to root.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.