How to unblock a toilet EASILY & WITHOUT a PLUNGER! That's right, without a plunger! How to unclog a toilet has never been easier. A blocked toilet is without doubt a major inconvenience, but don't call the plumber just yet. Save yourself a truck load of cash and give this method a go.

How to build an outdoor, homemade fire pit out of an old washing machine drum! It looks great and works fantastic. Fire pits are conventionally made from stone or bricks and as the name suggests, are made into a pit in the ground. The fire pit that l have just built is a little different to that.

How to repair a stripped screw hole. Look, we've all bought a crappy chipboard piece of furniture in our time that has fallen to pieces because the screw holes are so worn they no longer hold the screw, or have had an old door that is about to fall off because the screws holding up the door have been stripped out of their hole.

Sound waves are a lot more versatile than you'd think. For starters, you can use them to project images onto a bubble and liquefy gummy bears. And now, YouTube scientist and optical illusionist extraordinaire Brusspup shows how sound waves can also be used to manipulate a stream of water into a zigzag shape.
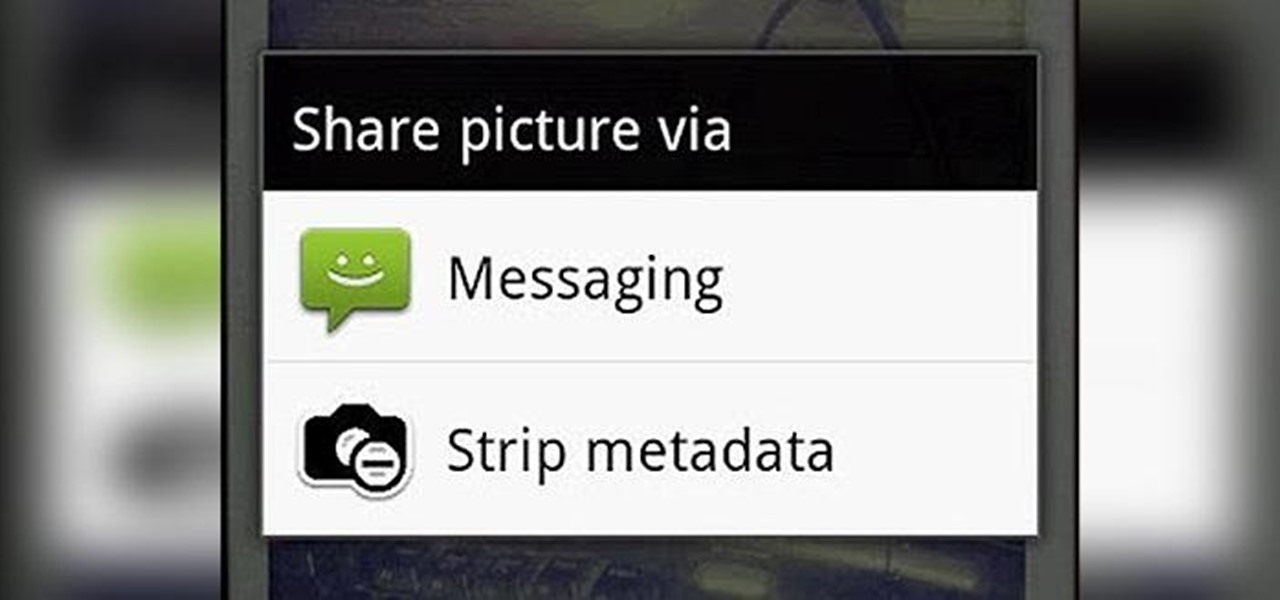
We've talked before about EXIF data—or metadata—attached to photos and how it can expose information about your location, what type of device you're using, and even the device or camera's unique identification number.

I recently stumbled upon this lovely design created by Nichole, from nail polish wars, and was instantly inspired to ask for her permission to use her pictures to make a slideshow presentation of her wonder work! I like to call them mystical nails!!

Rock, Paper, Scissors is a classic childhood pastime, but some people take it a little more seriously than that. There's the ultimate version, which has 25 gestures instead of the traditional three, and there are even tournaments and championships for those who consider themselves real pros.

Contrary to popular belief, IKEA can get pretty expensive. You find something that comes pretty cheap, but then, you decide that your GORF will look good with the BLERGH, and you really need the SPLOOF to tie it all together. Pretty soon, your living room looks like an IKEA magazine ad, and your bank account has seen better days. Instead of spending so much money at IKEA, why not build your own pieces of furniture?

While putting content and information online gets easier every day, it seems like getting it back is only getting harder. In a lot of cases (we're looking at you, Facebook), once you upload something, it's forever in the hands of someone else. That's where The Data Liberation Front comes in. Believe it or not, The Data Liberation Front is a team of Google engineers who work to make it easier for users to take their stuff back whenever they feel like it.

Anything free is cool, but getting a fully upgraded operating system for the great price of nothing is downright awesome. A recent exploit was uncovered that allows users to get a free copy of Windows 8 Pro directly from Microsoft's own website. Seriously.

Whether it's forgetting your driver's license or misplacing your cell phone, forgetting things at home can be a pain in the butt. Car keys, wallet, purse, papers, sunglasses—the list can go on. Sometimes I even surprise myself at the important things I forget... Oops.

You can do a lot with water guns. Have trouble waking up? Make a water gun alarm clock that (almost) no one could sleep through. Prefer real ammo? Turn your water gun into an airsoft BB gun. And if you don't have one, you can even make your own.

There are plenty of things you can use at home to make your own rocket, like sugar, matchsticks, or even trash. They may not be as impressive as a real rocket, but they can still be a lot of fun. In this video, How To Lou shows how he made a high-flying water rocket out of some basic materials like PVC and a soda bottle. As Lou points out, the bigger your soda bottle, the further it will go. He used 1/2" PVC pipe, valves, and connectors, as well as some brass adapters. He added an air compres...

How to roll up an extension cord. Rolling up an extension cord. Extension cord. It sounds like a basic skill but it's amazing just how many people just don't know how to roll up an extension cord. For the DIY'er and tradesman alike there are probably two main methods. There's my way of doing it (which l show in this video titled how to roll up an extension cord) and the other is similar to the method used by skydivers to roll up their parachute cords. They are both good and you could use eith...

Forgot the passwords to your email or your other favorite websites? If you typically store your passwords in Internet Explorer (IE9 or other versions) it can be tricky to get your passwords back -- but this tutorial makes it really easy!

As if the world needed one more reason to be obsessed with Shark Week, Volkswagen has teamed up with Discovery Channel to create this awesome "underwater car" that's actually a mobile shark cage.

I've never really liked to type on a flat or low keyboard. Even the small flip-up stands underneath most keyboards were not good enough for me, as those little legs aren't usually more than 2 or 3 centimeters high. I'd like a minimum of 5 cm, so I decided to make this keyboard base for myself. Aside from giving me the right height and angle, this DIY keyboard base also features LEDs that light up my monitor, the table, and gives a nice background to my desktop. It's even got a built-in stand ...

Alright guys sorry for the delay, lets just get to it: » Pelosi Says Holder Contempt Charge About Suppressing Vote.

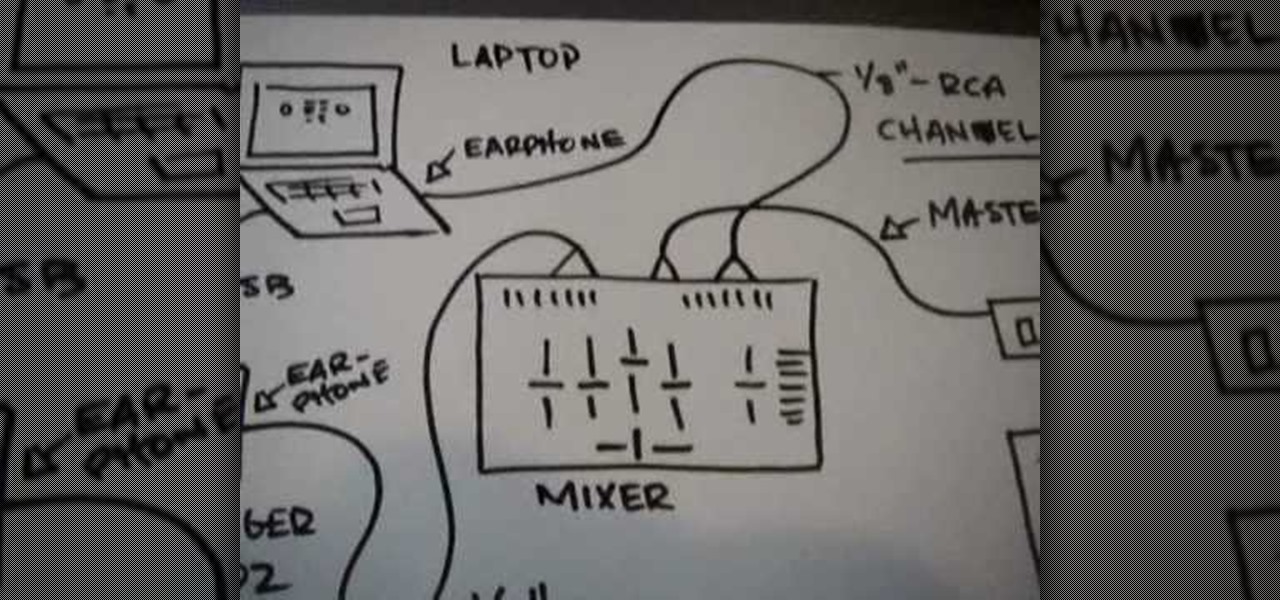
This video shows you how to connect your laptop to your mixer. First you will need two different sound sources from your laptop to your mixer. This is so that you can use all of your mixer functions on two different channels. The way to do this is to run a 1/8" RCA cable channel 7 from your normal earphone jack to the mixer. Also use a behringer uca202 audio interface to connect to the laptop via USB cord. This provides another earphone jack. Then use a master out cable to connect it to an am...

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to create a jellyfish environment in Photoshop.

Why pay for a movie when you can get it for free? Thanks to Movies Anywhere, you can claim and download a video for your digital film collection right now at no cost. And getting your freebie flick couldn't be any easier.

The breakdown - 5 cool new channels without too many new subscribers. What's the best way to expose them to more people?

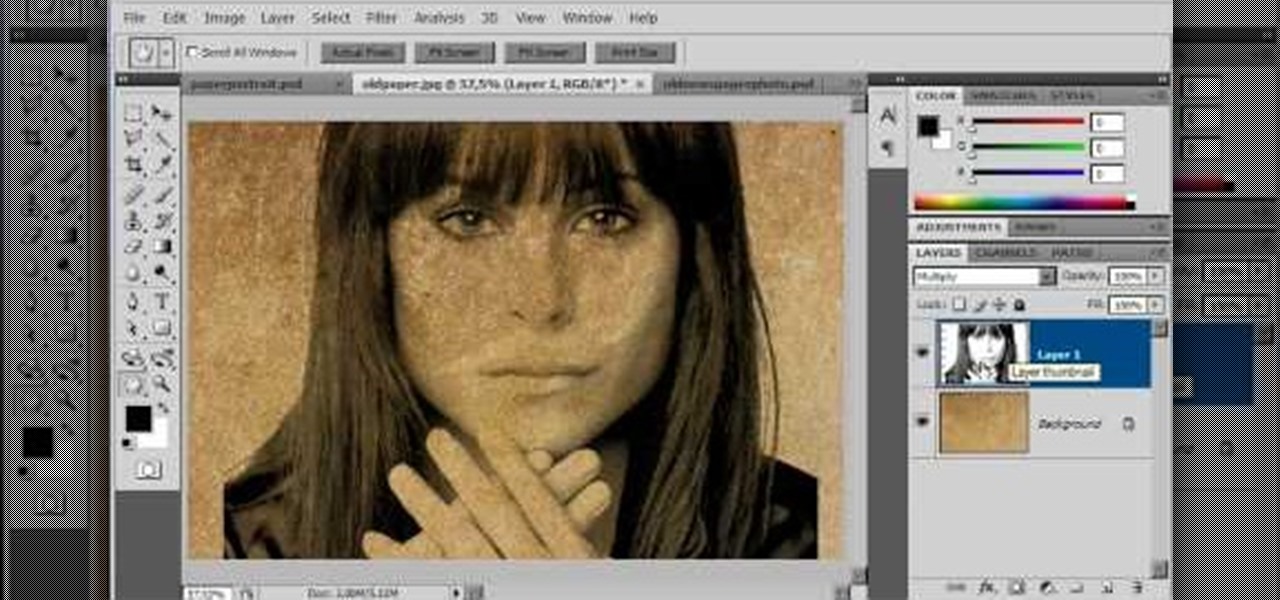
The video is about how an old stalled photographic image with faded backgrounds to a normal image. A nice clean digital image is taken and is mixed with a texture of a paper and produces a final composite image of all effects combined. The procedure is not that difficult but it needs to be followed in a proper order. First the paper texture is taken as a base and then the clean digital image is dragged onto this texture. The blending mode is adjusted from normal to multiplied blending mode, w...

Learn how to do break dance push ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

Pigs are not just pork chops, people raise, train, and put these Vietnamese pot-bellied pigs on stage. Watch this how to video to understand how pigs think and learn amazing tricks. Maybe you can train your pet pig to do amazing tricks.

Meghan Carter visits Chef Jason Hill to discover the secret to creating beautiful and delicious edible centerpieces. Jason, host of the YouTube Channel Chef Tips, shared the essential elements for an attractive green and purple grape centerpiece as well as how to make something your guests will want to eat. You can also try creating the olive tower.

Tips on modifying your fusion freeride saddle to keep the "channel" open.

Channel Pullip teaches how to make a round doll dress. To accomplish this, you'll need fabric. In the example she used sailor color themed material. You'll need lace and trimming, an elastic band, and velcro for closure. To start, cut the fabric to 17cm x 3cm, fold in half and sew to a tube shape. Then you'll turn it inside out and fold both ends in. Cut a 10cm piece of the elastic band. Then, sew the band to the material. You've just made the dolls headband. To make the top of the dress, you...

Each & Every One of You (EEOOY) is a mock TV show pilot that teaches ordinary people how to make contemporary installation art. If these words strike fear into your heart or make you cringe with memories of seeing contemporary art and wondering what the hell it was all about, this show is for you!

When learning Wi-Fi hacking, picking a compatible Wi-Fi network adapter is the first step to learning to crack Wi-Fi passwords.

While Magic Leap doesn't yet have a consumer edition of the Magic Leap One, that hasn't stopped AT&T from building apps for mainstream audiences for the headset.

Imagine being able to play a video instantly on hundreds of thousands of devices across the globe. It's totally possible, as long as all of those devices have a Chromecast plugged in. When Chromecasts are left exposed to the internet, hackers can use add them to a botnet that can play YouTube videos at will. The "attack" is made even easier thanks to a simple Python program called CrashCast.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

It's March once again, and while that might signify the beginning of spring for some, basketball fans have this month marked on their calendars for one good reason: NCAA March Madness. Though the tournament is already underway, the Sweet Sixteen leg begins Thursday, March 23, 2017. If you fear you may miss the upcoming games, worry not, as free apps for smartphones and tablets are available to help you watch all the action.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

If you've been following NextReality, you've surely seen me around, or at least have seen my articles. My name is Jason Odom, aka Subere23, and it's about time for a formal introduction.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.