Having an SSH or Secure SHell to tunnel your traffic through is something we have talked about many times at Null Byte. As we know, it allows us to securely route and encrypt our traffic through a remote server, effectively anonymizing us and protecting our traffic from all forms of analysis—simultaneously. We have gone over how to make a home SSH tunnel. However, the question has come up, "How can I get an SSH tunnel to somewhere other than my computer?" This would be useful in a situation w...

Flash memory can be a tad unpredictable at times. I have had 4 flash drives die out on me over the last few years, and they usually die without warning. When a flash memory based device dies, the data is likely impossible to recover. Adversely on an HDD, or Hard Drive Disk, even if the disk dies out, someone will probably be able to fix it and get it back to working order—at least long enough for you to back up your data. Hard drives are a bit more forgiving. As you can guess, due to the unpr...

Skype is a great service. It allows a free solution for VoIP to VoIP calls, and cheap VoIP to landline calling. However, a very disturbing, little known fact that might push you away from Skype does exist. If you closely read the terms of service agreement, it clearly says that Skype is allowed to decrypt your messages whenever they please. Here at Null Byte, we tend to enjoy our anonymity, don't we?

More password cracking action from Null Byte! Today we aren't going to be cracking passwords per se, rather, we are going to learn the basics of generating rainbow tables and how to use them. First, let's go over how passwords are stored and recovered.

Gamers who have their Xbox 360's firmware flashed may have recently noticed an inability to play backups, or even make backups of newer games that have come out, such as Gears of War 3 and Dead Island, to name a few.

Last week's Community Byte we got off to a great start! We had a few people build our IRC bot, and all went well. We had some great contributers, ideas, and people willing to learn. So, needless to say, we will be having another. Let's try to get a few more people involved this time!

Lockpicking is a skill that takes years upon years to master. Locks come in all sorts of shapes and sizes, but have common ground in how they work. Most cylinder locks have "tumblers," which are metallic cylindrical objects that sit vertically to the actual locking mechanism. Tumblers have five or six holes with rounded key pins of various height in them, each needing to meet an exact height or the cylinder in the center (the lock itself) will not be allowed to turn. This is the reason why yo...

Welcome to the second Null Byte in a series educating you on Social Engineering awareness and techniques. Today, I'm going to show you how a saavy Social Engineer would trick a friend into unknowingly surrendering their Facebook password. My intent is to warn and demonstrate how easy it is to succumb to phishing via Social Engineering, and therefore expose yourself.

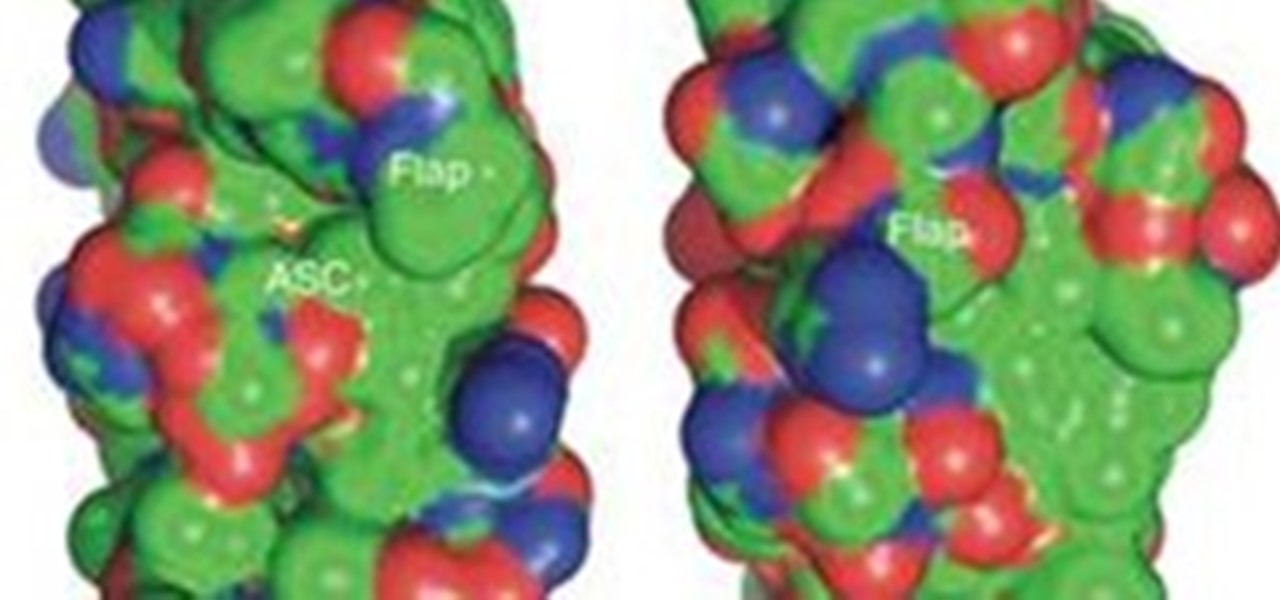
Foldit is definitely a niche game. The sole gameplay mechanic is attempting to fold complex proteins into smaller and more efficient shapes following the rules of molecular physics and biology. Points are awarded based on how small one can make the protein. Online leaderboards track players' relative progress and allows them to view and manipulate other players' completed designs. It's original, certainly, but no developer is going to ship a million units of a game about molecular-level prote...

Today's segment of Making Art on Your iOS Device takes us into the third dimension. The below apps are suitable for beginners looking to venture into the world of 3d modeling, as well as pros who simply want the basics of Maya in their pocket.

Tower defense games have taught us little. We already knew that defending castles from baddies was fun and that legions of weenies are the key to success in most real-time strategy situations. What other insights have they to offer?

One of the coolest things about Twitter is the fact that you can get direct access to some of your favorite celebrities, and have one-on-one conversations with them in less than 140 characters. With Google+, you can have the same advantage, but you don't need to feel constricted by the 140 character limit. Although Google+ has been weeding out fake accounts, they do not currently have a system for celebrities to verify whether their accounts are legitimate or not.

Speech recognition software made it easy to search Google on your smartphone, and Google Goggles made it easy to find answers from camera snapshots on your device. But now Google's bringing similar technology straight to your desktop, and with faster results—faster than Google Instant.

George Plimpton may be one of the most interesting Americans ever. Foremost a sports journalist, he was also a novelist, Fireworks Commissioner for New York City and host of Mouseterpiece Theater. Some of you may also recognize him as one of the men who tackled Robert F. Kennedy's assassin, Sirhan Sirhan. But most of you probably remember him as the pitchman for products like Pop Secret Popcorn and the Intellivision video game console. Actually, his most appreciated work would probably be a s...

There are a lot of important things to keep in mind when you’re recording a kick drum. It seems like it’d be as simple as putting a mic in front of the drum, but there is so much more! Here are some quick tips on recording and mixing a good kick drum.

When I heard that a man wearing a pink wig and matching PVC dress won the 2010 National Scrabble Championship yesterday, I wasn't that shocked. After all, it was Halloween. But it turns out that it wasn't just a Halloween costume. In fact, it's a way of life for this champion scrabbler.

Halloween just isn't Halloween without Jack O'Lanterns. Below, anything and everything you need to know on the art of pumpkin carving.

General Tips for Exercising in the Heat -Schedule workouts for the cooler times of the day.

Written by JD Coverly of WonderHowTo World, LoadSave:We've spent the last week with Sprint's new phone, the HTC Evo 4G. Specification wise, it's better than Verizon's Incredible and T-Mobile's HD2. Apple has unveiled the new version of their phone this week and thankfully it's debatable as to which phone is better. The iPhone has better battery life and a more robust App store, but it suffers from a smaller screen, smaller camera resolution, no HDMI out, face talk only on wi-fi networks, and ...

What Am I Doing???? Last night, I was reminded on the negative impacts of striving for perfection. It's not possible to be perfect. We describe many things as being perfect. IE, an afghan, a hat, a tablecloth and more over, there is always something better... a different colour, a slightly different pattern, and so on. As time progesses, the colours we choose this fall might be the OUT colours of next fall.

Levon Helm... The longtime drummer for The Band , Levon Helm wore many musical hats throughout his long career, including multi-instrumentalist, songwriter, singer, impressario, studio owner, studio engineer and producer. He grew up working on a farm in Arkansas; his first instrument was guitar, which he began playing at ag eight, but after seeing the F.S. Walcott Rabbits Foot Minstrels, he decided to ...

We've all relied on the internet more than ever during this pandemic. But while you're staying safe at home, are you being safe and productive while surfing the web? That's where a trusty VPN comes in handy!

The 68th Annual Golden Globe Awards take place this Sunday, January 16th, 2011 between the hours of 5 and 8 PM PST — that's 8 & 11 PM for those of you on the East Coast (and Somewhere in the Middle for those of you Somewhere in the Middle).

It's mid-January and some of you happy tax-paying citizens have already started receiving your W-4s and 1099s in the mail. But before you start filling out your 2010 Federal Tax Return, make sure you're hip to all the tax tricks in 2011. You could end up saving some money!

In my recent article, How to Make a Mini Cannon with a Lighter, I demonstrated how to make a powerful combustion cannon out of parts salvaged from a standard BBQ lighter. The mini cannon was originally made to fire airsoft pellets, but I felt it was time to revive the project with something new.

Working in cahoots with the producers of E! channel's 'Chelsea Lately'; the entire Jackass gang & myself secretly come to a taping of Chelsea Handler's show. Whiles she is doing the show with her round table guests, the producers kick in the 'Party Boy' song over the sound system & we all suddenly run onstage live NUDE and we surround her and start doing a Rockette-style line dance or whatever musical moves we choose. Mayhem ensues. After several moments of shear debauchery, at the conclusion...

Self-storage may not be a new industry, but it is one that is rapidly reshaping its operations to suit a progressively more modernized customer base. In order to stay competitive with your self-storage facility, you'll need to keep an open mind, embrace current marketing trends, and most importantly, have a well-defined set of marketing goals. Your main focus should revolve around the following points:

Ever wanted to display text in Minecraft? It's actually not overly difficult. In this tutorial, I will endeavor to guide you through the process between storing and displaying text from memory. To do this, we will examine two different methods of displaying and storing text in memory.

Smartphones are crazy awesome. You can do your banking, track your children, find directions, and even pretend to have a mustache. The only thing that these personal supercomputers are missing is physical interaction with the environment.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

With the mass arrests of 25 anons in Europe and South America, and the rumors of an FBI sweep on the east coast of America floating around, times look dicey for hackers. Over the past few days, a lot of questions have been posed to me about removing sensitive data from hard drives. Ideas seem to range from magnets to microwaves and a lot of things in-between. So, I'd like to explain a little bit about data forensics, how it works, and the steps you can take to be safe.

For a moment, picture a situation where you want to host some files or images, but you do not want it traced back to you. Perhaps you're working on a project with others and need secure data storage. Anonymity is the new shield of the 21st century—and you best protect yourself. As always here at Null Byte, we are trying to make that happen. Before someone can learn how to root a box, they need to learn how not to be found. I can not stress that point enough.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. This past weekend, our Weekly Workshop focused on building a suffocation trap. But today, we're going to be covering a different type of redstone trap in Minecraft—one with a 100% success rate (perfect for PvP servers).

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Overclocking is quite an awesome thing. When computer components are designed, they are made to run at a certain speed, otherwise known as their clock and bus speeds. These limits are not actually limits. You can overclock components, which essentially makes them go faster than their set limitations. This can save you a lot of cash when newer components come out and you don't have enough money to upgrade. However, when you overclock components, you must be careful and make sure that the machi...

When your computer first connects to a nework, it sends out a request on the network to lease an IP from the router. The router then leases your computer an unused IP address, which is used as a unique routing address for sending traffic that is meant for you, to you. As everything tends to, this method has its flaws.

One of the primary goals of a social network is for you to share what you find interesting with your followers and friends, but on Google+, sharing has so many layers that it can be confusing for most people to really take advantage of it properly. Some of the tools in place that enable you do deal with spam and manage your privacy aren't very clear, so this week's round up is all about how you can share what you want with who you want on Google+.

SSL stands for Secure Socket Layer. It's an encryption standard used on most sites' login pages to avoid their users' passwords being packet sniffed in simple plain-text format. This keeps the users safe by having all of that traffic encrypted over an "https" connection. So, whenever you see "https://" in front of the URL in your browser, you know you're safe... or are you?

+Randall Munroe, the man behind the web's most popular web comic, XKCD, has always had a knack for getting to the heart of the larger social issues on the web. During the 1st 48 hours after Google+ started letting non-Googlers in, one of the most shared posts within its private walls was his latest comic about Google+: