Augmented reality can be more than simply a way to enhance navigation, or superimpose virtual sunglasses onto your face. It can also be a platform for shining a light on important social issues.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

Smartglasses maker Vuzix made a big splash at CES 2018 with the inclusion of Amazon's Alexa voice assistant among the AR superpowers of its consumer-centric Blade smartglasses.

Samsung just announced the Galaxy S10 lineup, but we already knew each device's every nook and cranny. Thanks to leaks and hands-on demos, we know the OEM kept the coveted headphone jack, but omitted one treasured feature in its place — the notification LED. Why did Samsung strip the S10 of this light, and can users expect something to replace it?

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

Reading the augmented reality news lately has felt a bit like reading a John Grisham novel, as the business side of things has dripped with legal drama.

If you're familiar with jailbreaking, you're well aware of the fragmented nature of downloading tweaks. Unlike the iOS App Store, which contains about two million apps of varying categories, installing jailbroken packages often requires you to first install a separate repo into either Cydia or its replacement Sileo, as many of these tweaks aren't available outright.

One of the most useful features of the Pixel Launcher is access to the Google Discover page. Initially, this feature was exclusive to Google's launchers, forcing users to give up the customization of apps like Action Launcher if they wanted the quick access to relevant news and updates it provided. Fortunately, this is no longer the case.

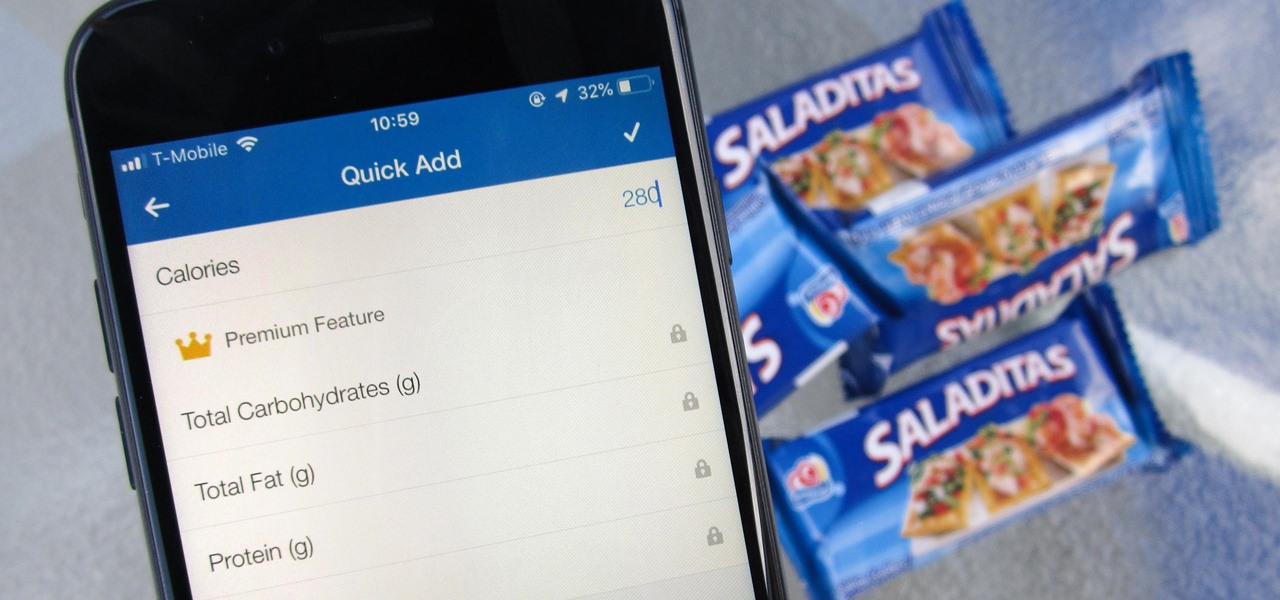
It's only normal to snack on a few french fries every once in a while when you're on a diet, but it's still important to hold yourself accountable, even when you cheat just a little bit. MyFitnessPal, for both Android and iOS devices, has a database of nutritional information to help keep track of the meals you eat, but it also has a way to add calories on the fly without digging for data.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

Last week, iOS 12 developer beta 7 was quickly pulled upon release, due to complaints of poor performance and instability issues. While Apple tackled these bugs with the release of developer beta 8 two days later, testers are seeing beta 7 again in their Software Update settings. Why is beta 7 back, and, more importantly, is it safe to download?

From day one, my favorite thing about the Magic Leap One has been its portability. It's so well designed that it just screams to be taken out for a walk through the city. Alas, Magic Leap says the device is (currently) designed to be used indoors, preferably in settings containing few windows or black surfaces.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

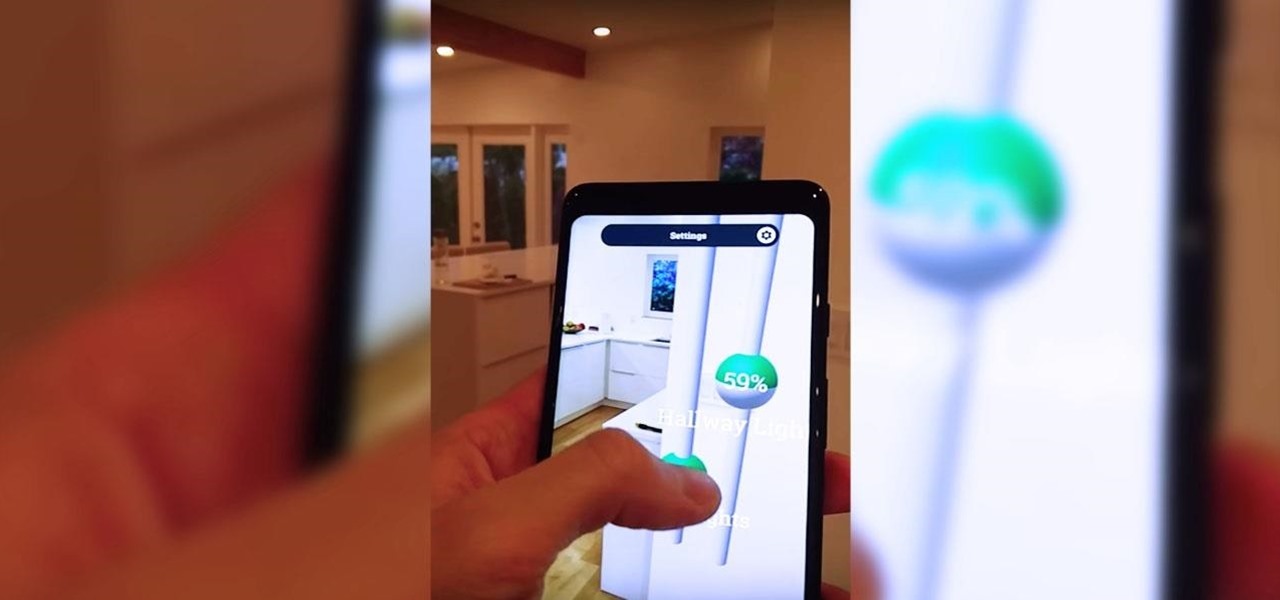
Voice-activated digital assistants from Amazon, Apple, and Google currently have the upper hand for home automation integrations, but a new augmented reality mobile app promises to give homeowners and renters visual control over their connected appliances.

US customers might soon get access to their first Xiaomi smartphone. The fourth largest OEM has been eyeing a US launch for years, with rumors indicating a debut by Q1 2019. Now, it looks like the Mi 8 Anniversary Edition will be the first device.

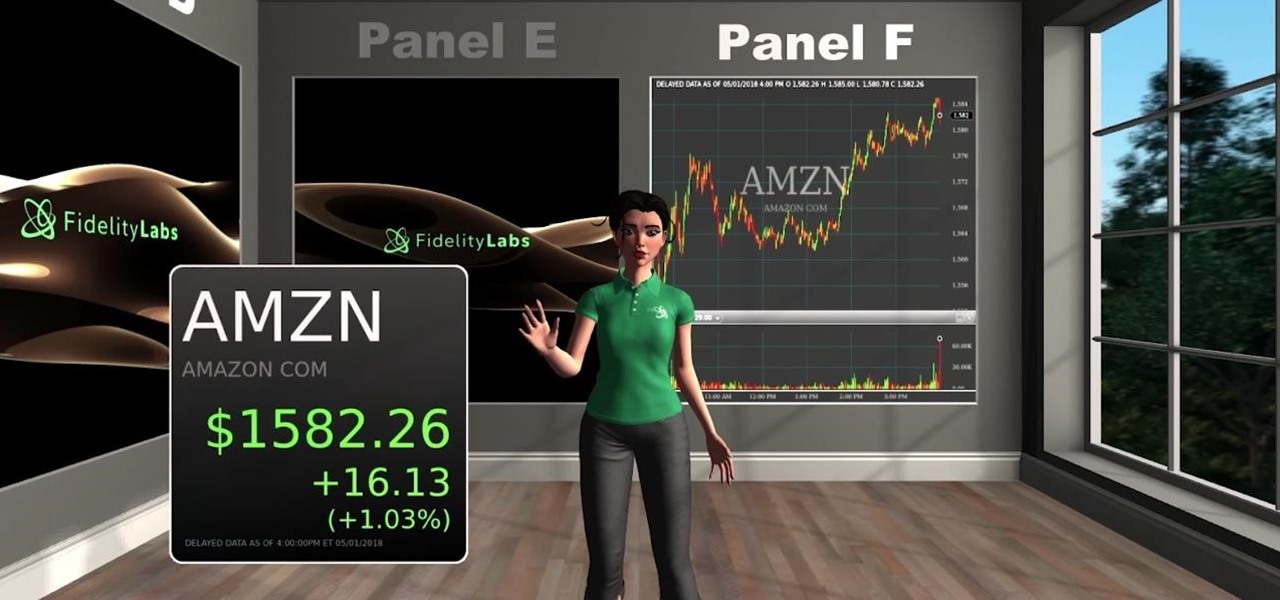
Amazon Web Service's do-it-yourself tool for building augmented reality experiences and VR has graduated from beta and is now available to all interested users.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

What's black and white, sounds like actress Kristen Bell, and is standing in your living room talking to your kids right now? Don't worry, that's just Genius the Panda, an augmented reality character from the Yakables app for iPhones and iPads.

The default Camera app got a few more tricks up its sleeves when iOS 11 was released, and the best addition by far was the inclusion of a built-in QR code reader since that meant no more third-party apps just for QR code scanning. However, Apple's built-in QR code scanner did have a vulnerability at one point that would let hackers direct you to a compromised website without you even noticing it.

The legal travails of Magic Leap appear to have no end in sight, as a lawsuit filed by an ex-employee further threatens to dampen the startup's 2018 launch.

It's human nature to wonder if the grass is greener on the other side. This is no more true than for people who use iPhones, and those who use Galaxy S phones. While iPhones were initially the gold standard for smartphones, Samsung's phones equal them in many ways and surpass them in others. If you use an iPhone and you're on the fence, here's the case for making the switch to a Galaxy S9 or S9+.

While Google has a water-resistant phone in the Pixel 2, its CES booth was anything but. According to Tech Crunch, Google had to shut down its two-level outdoor booth once it began to rain at the Las Vegas trade show. Even though Las Vegas is the driest city in the country, Mother Nature always has her idea of fun.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.

Many people think antivirus apps are useless — why pay a subscription fee when most malware can be avoided with common sense? But the thing is, there were an estimated 3.5 million malicious Android apps discovered last year, with many of them making their way onto the Play Store. As this number continues to rise, can you truly depend on common sense to protect you?

So much information exists online that it's easy to get lost in data while researching. Understanding the bigger picture can take a lot of time and energy, but narrowing the question to one that's easy to answer is the first step of any investigation. That's why analysts use open-source intelligence (OSINT) tools like Maltego — to help refine raw data into a complete understanding of a situation.

Did you want an iPhone X, but opted for the iPhone 8 instead? Or, maybe you aren't ready to upgrade from your 7, 6S, 5S, or what-have-you. Did you know iOS 11.1 lets you experience what it would be like if you had upgraded to the iPhone X? Well, in a way.

When explaining augmented reality to the uninitiated, Pokémon Go is often cited as an example. For all its popularity, though, many players would recommend disabling the AR capabilities in catching Pokémon.

Using the Mail app to log in and sync to email services such as Gmail and Outlook is incredibly easy to accomplish on the iPhone thanks to the intuitive nature of its operating system. This is still evident with iOS 11, and though the process differs slightly from its predecessors, it can still be accomplished with relative ease.

Newly appointed Ford Motor CEO Jim Hackett admitted yesterday that demand for driverless transportation could take many different forms and that Ford was rethinking how it would tailor its cars and mobility services for self-drive modes of transportation in the future.

Scientists know that bacteria create their own energy, get nutrients to run their cellular processes, and multiply. But, bacteria haven't been shown to respond to external mechanical stimulation or signals in a way that's similar to how our bodies respond to touch, until now.

Once we recover from the respiratory infection pneumonia, our lungs are better equipped to deal with the next infection — thanks to some special cells that take up residence there.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

Despite mounting scientific evidence that viruses can cause changes in learning and memory, the reasons have remained elusive.

Technology and nature, typically thought of as opposites, are coming together in a new London exhibit.

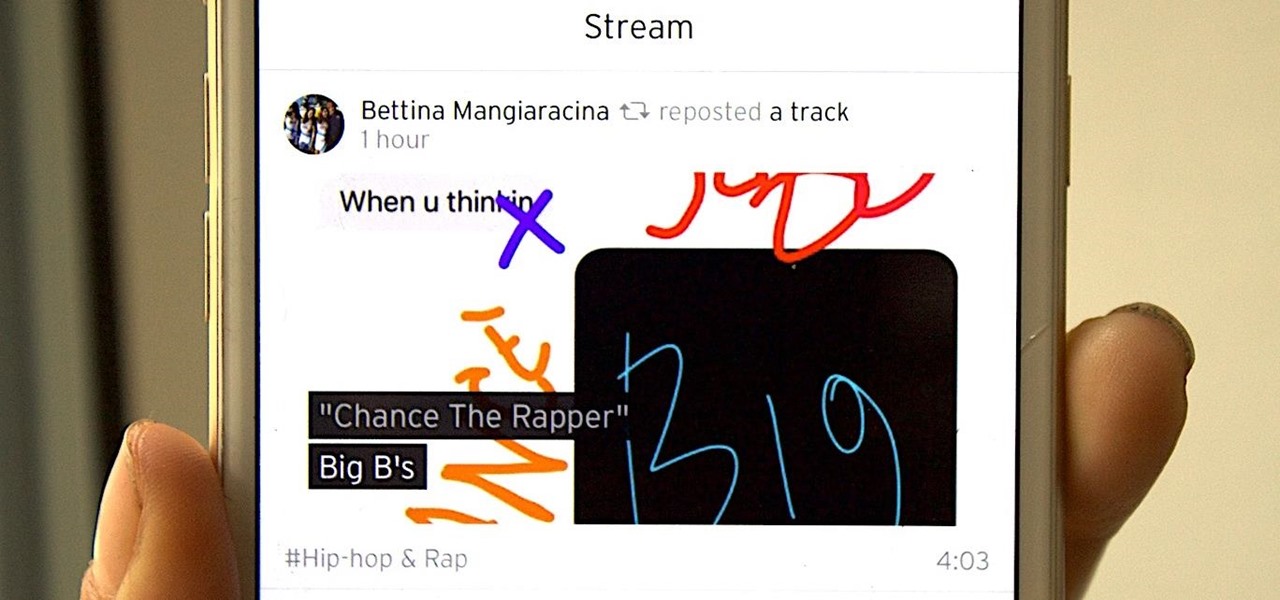
SoundCloud is a great place to gather all your different tastes in music and display them as representations of who you are. You can display things like your own tracks, albums, manually-curated playlists, liked tracks and playlists, and reposted content all from within your profile page.

With a death rate of one in five, sepsis is a fast-moving medical nightmare. New testing methods might improve your odds of survival if this infection ever hits you.

More bad news for patients who have undergone heart surgery in the past five years. A new study suggests about one-third of heater-cooler units used in cardiac procedures remain contaminated with a slow-growing, potentially fatal bacteria.