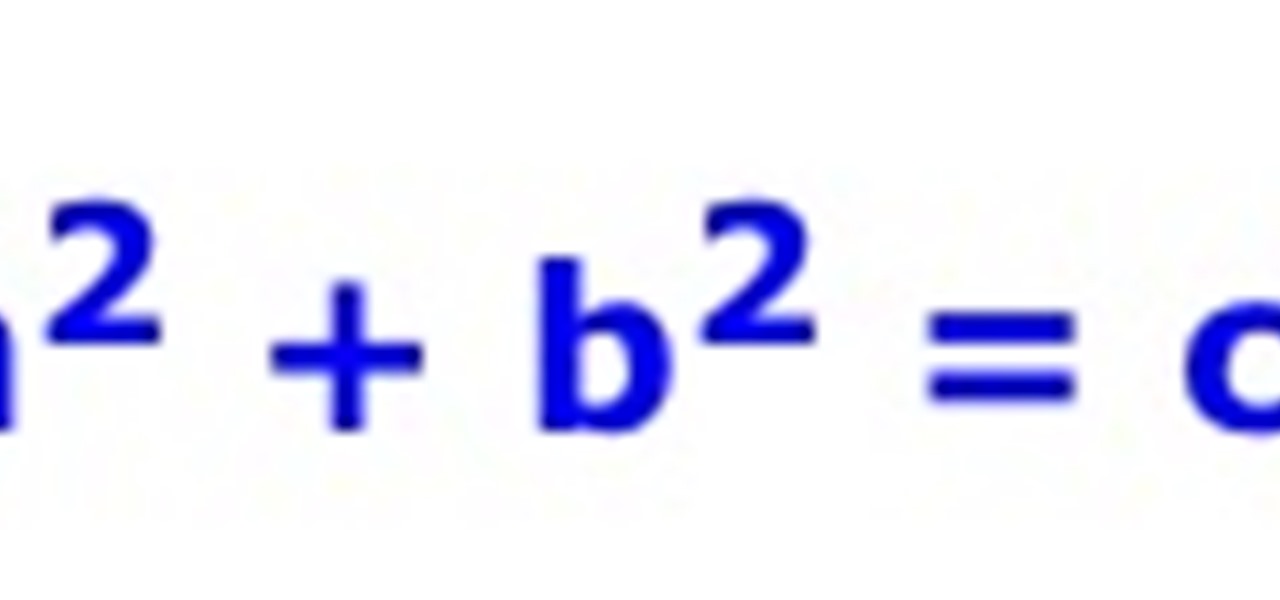My years in the restaurant business have taught me many things. Some of those things are best left unsaid and other things require a PhD in vulgarity, but the one thing I learned that I keep coming back to night after night is that you do not have to spend a lot of money to drink excellent wine. This is especially true of champagne...I'm sorry, sparkling wines.

Google has already started to roll out the over-the-air update of Android 5.0 Lollipop to older Nexus series phones and tablets, but chances are it will take a long time for the OTA to hit your device.

If you struggle with deciding which wine you should buy for an intimate dinner, or the type of beer with the highest alcohol content that doesn't taste like tree bark, then check out some of these great alcohol-friendly apps to make better booze decisions.

Admit it: you've been caught muttering to yourself under your breath in very public places. Maybe you've gotten stares while wandering the grocery store talking to yourself out loud. If you're like me, you might even talk yourself through various tasks, giving the atmosphere a little background noise.

Coffee! It's so amazing that J.S. Bach wrote a comic opera about caffeine addiction. Meanwhile, more than half of Americans 18 years or older start their day with a cup of the hot stuff. Most of us take coffee for granted, but it's a bean that can surprise you. Read on to understand more about coffee and how to take advantage of all that it offers.

You're in the middle of cooking and a car alarm, cute kitten, or neighborhood brawl made you step away from the stove for a few minutes longer that you should have. It happens to almost every home cook. Most of the time, nothing dramatic happens, but every now and then, you end up with something like this:

Depending on who you ask, internet connectivity should be a basic human right. With Google recently embarking on a project to provide internet capabilities to remote corners of the world using balloons and satellites while Facebook attempts to do the same with unmanned drones, the concept of free web access is steadily gaining steam.

Security is a priority for many when they first set up their mobile devices. Nobody wants to have a stranger or nosey friend go through their phone and discover risqué photos or embarrassing text messages. These days, the closet is gone—everyone keeps their skeletons in their phones.

Welcome back, my hacker apprentices! Last week, I started off my password cracking series with an introduction on the principles and technologies involved in the art of cracking passwords. In past guides, I showed some specific tools and techniques for cracking Windows, online, Wi-Fi, Linux, and even SNMP passwords. This series is intended to help you hone your skills in each of these areas and expand into some, as yet, untouched areas.

Contrary to popular belief, taking someone's mind off their sadness and telling them to "cheer up" doesn't do much good. Misery loves company, and while it may be a tiresome cliché, there's actually some science behind it.

If browsing speed is important to you—and it should be—you'll probably be interested to know that there are ten simple flag modifications you can make in Google Chrome in order to achieve the fastest browsing speed possible.

If you're anything like me, your day doesn't start until you've sloughed away your grogginess with a scalding hot shower. That perfectly-heated water can clear stuffed sinuses, relax the muscles, and make pretty much anyone feel squeaky clean. However, a cold shower can do even more for you if you can stand the low temperatures.

There are spontaneous times in everyday life that just scream to be recorded on video. The crazy guy yelling obscenities on the bus. Your favorite actor at the supermarket check-out register. Maybe even your kids just being super adorable.

Fasting—or the practice of regularly abstaining from ingesting anything except water—is a pretty drastic move. I tried to fast for two days and made it to the 12-hour mark, which is when I broke down and ate a quart of ice cream.

When the Nexus 5 debuted, one of its coolest features was the fact that you could say "OK Google" any time you were on the home screen to launch a Google Voice Search. This feature was ultimately made available for other devices by way of the Google Now Launcher.

Who doesn't enjoy sitting down to a nice dinner with a cocktail in hand? After a long day, a drink is a great way to unwind. Yet your favorite spirits can do more than just help you relax after work. By utilizing alcohol in the kitchen, you can enhance everything from how food tastes to your health.

Apple has released the 2nd beta of iOS 8, exactly fifteen days after the first version was unveiled at WWDC and subsequently released to developers. I've already shown you some of the new features of iOS 8, like location-based app alerts, randomized MAC addresses, hidden Safari tricks, and a slew of new things in the Messages app. But if you've had the chance the explore iOS 8, let's go through some of the changes that Apple has made to the latest iteration of its mobile operating system.

Boozing it up at work might have been okay back in the days of Mad Men, but today, employers prefer that their workers stay sober. What you and your bosses probably don't know is that a little drinking on the job can actually increase your creative capacity and problem-solving skills. Alcohol Can Enhance Your Creativity at Work

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

Let's get one thing straight: CyanogenMod is one hell of a ROM. They've got a great community, a great product, and getting it on your HTC One couldn't be easier with their CyanogenMod installer, which does all the hard rooting and bootloader unlocking for you.

Like many other smartphones these days, your Samsung Galaxy S4 is built to handle multitasking like a pro. With a 1.9 GHz processor and 2 GB of RAM (specs comparable to laptop computers just a few years ago), this powerhouse of a phone can switch between apps with supreme ease.

If you're a Twitter user, it's a safe bet to assume that you've used a hashtag. On all social networking sites that have the capability, such as Instagram, Facebook, and Google+, the pound (#) symbol is used to mark and designate specific keywords or topics in order to make it effortless for users to connect with one another.

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

In one of my previous articles, I showed off how to make water freeze into ice instantaneously. In this article, I'd like to elaborate on this, and show how a glass of water can turn to ice instantly on command. What exactly is this supernatural power? Discover the secrets to ice-bending—in real life.

What Is Pythagorean Theorem? Pythagorean Theorem is an equation discovered by a man named Pythagoras. It can be used to determine whether or not a triangle is a right triangle and find missing lengths of a triangle. The equation is: Parts of a Triangle

Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it.

Google Reader is soon to be no more. Yesterday, the company announced that the service will be shutting down as of July 1, 2013, as part of Google's second "Spring Cleaning."

Need to remove wrinkles from your shirt but don't want to bust out the iron and ironing board (or don't even have one)? Well, with a little bit of do-it-yourself ingenuity, you can "iron out" that wrinkly top in no time.

The creation of private browsing was brought upon by the backlash against ad tracking and other ways that sites and agencies take away users' privacy online. People were tired of getting spammed with ads for Vitamin C pills simply because they visited WebMD. Private browsing is now built into all of the major browsers and is used frequently. While private browsing is more infamously known as the "Porn Portal," and does prove to be a great way of keeping racy content out of the sight of others...

Mason jars are a DIYer's best friend, nearly on par with duct tape and paper clips. Why? Because you can use mason jars for so many things besides just canning and drinking, and I'm not talking about other obvious uses like basic storage containers or miniature terrariums. I'm talking about MacGyver-style ingenuity. With a little creativity, the uses for those jars are practically endless.

Curve stitching is a form of string art where smooth curves are created through the use of straight lines. It is taught in many Junior High and High School art classes. I discovered it when my math students started showing me the geometric art they had created.

If you don't work in construction or are a woodworking master, you probably aren't entirely sure what all those marks are on a tape measure. Sure, you likely know the basics, like there are 12 inches to a foot, but what are all those little tick marks for? Don't let all those little lines dissuade you from using a tape measure. Follow these guidelines to help you read all those little ruler marks.

Make sure your next apartment rental goes smoothly by properly checking the property before signing a contract. This way you will avoid unexpected disappointments or problems that you were not aware off. Moving is hard enough, give yourself all the advantage you can by going in prepared.

Wish things were free? Well, with this hack, you can make sure all the gold is zero and everything costs nothing. How? With Cheat Engine!

Discover the art of Telescopic Pole Setup in this informative video, where we guide you through the process of preparing your pole for speedfishing. Whether you're targeting Bluegill, Crappie, Trout, or Perch, pole fishing stands out as one of the most effective methods to reel in a catch.

In this video series, let Mei-chiao Chiu teach you the beginning forms of Wushu. She explains the history of Wushu, and its importance in the world of martial arts. She shows you how to warm up and stretch before being any Wushu exercise. With her instructions, you can discover the exciting martial art form of Wushu today

In these rock and mountain climbing instructional videos, learn how to set anchors for lead and top rope climbing. Having strong anchor points is crucial to a safe and successful climb. Get professional tips and techniques on using strong rope knots to secure your climb. Learn how to rock climb with natural anchors like trees and boulders. Discover how to join anchors together for a more stable climb in unstable conditions. Watch this series and use these tricks on your next rock climbing trip.

Google's "At A Glance" widget gives you the current weather conditions and upcoming events from your Google Calendar in a handy spot right at the top of your home screen. But on Pixel phones, this widget is permanently embedded into the launcher, so you can't just long-press it to remove it.

When approaching a target, having a precise and detailed plan of attack is absolutely necessary. One of the main goals is to increase the attack surface since the more opportunities there are for exploitation, the greater the chances of success. Subdomain enumeration is one method used to increase the attack surface, and we'll be using a tool called Subfinder to discover hidden subdomains.