
News: HTC-Built Nexus Tablet & Android TV Leaked in Latest Changelog
Veering from common practice, XDA commenter, "the_commenter", discovered a changelog for the upcoming version of Android 4.4.3 tucked away on Google's servers.


Veering from common practice, XDA commenter, "the_commenter", discovered a changelog for the upcoming version of Android 4.4.3 tucked away on Google's servers.

If you've haven't had your fill of Apple's security issues in recent weeks, Siri is now the latest to join the slew of problems with the most recent version of iOS (7.1.1).

Remember those horrible, soul-crushing studies from a few years back linking grilled meats with cancer? Unfortunately, they're still true, but scientists have recently found that an unexpected ingredient can curb some of the harmful effects of high-temperature cooking.

There is and always will be a staunch anti-microwave camp, but they're a fact of life. The whole point of a microwave is convenience, right? But it's not so convenient when you pull out reheated leftovers and discover that your food is only partially warm.
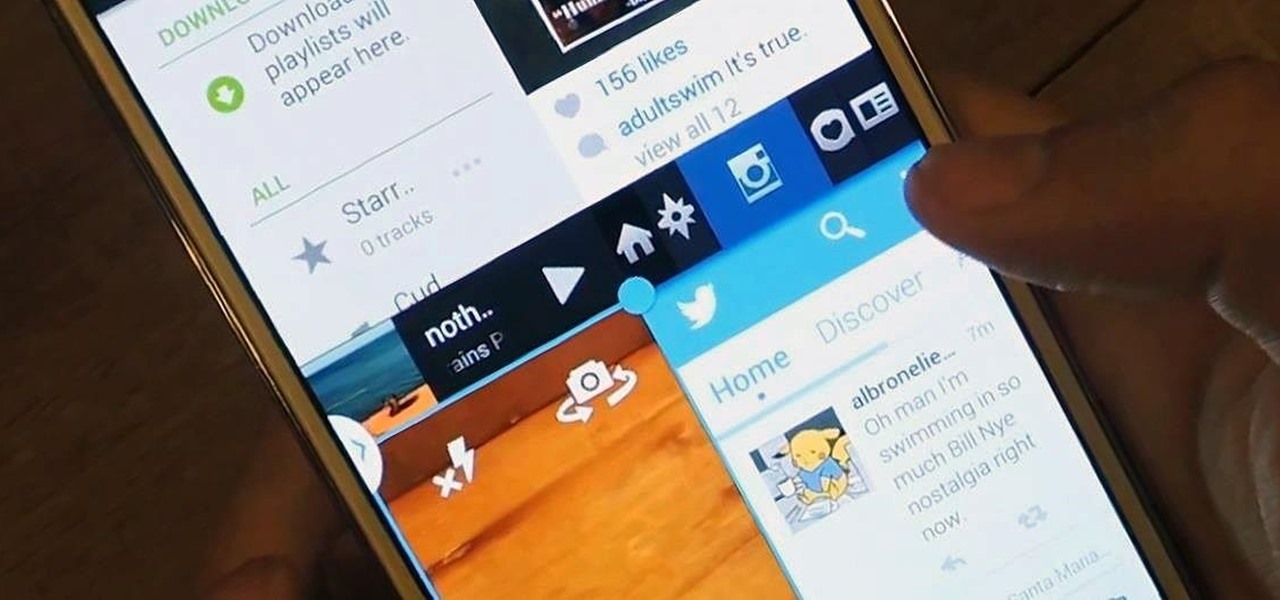
Restrictions are inconvenient, and for this reason I've sought out softmods that loosen the constraints for many of the features on my smartphone. Things like adding favorite apps to the Pen Window drawer or choosing any app for Multi Window mode are now must-haves on my Samsung Galaxy Note 3—and should be on yours as well.

Let's just say it's been a pretty bad year for spies and government agencies and an even worse one for the privacy of U.S. citizens. Edward Snowden blew the lid off the NSA's spy program, and the FBI was recently discovered to have the ability to access your webcam any time they want—without triggering the "camera on" light. Yeah, that means those Justin Bieber lip sync videos you recorded weren't just for your private collection.

For those of you who have (or had) and iPhone, one of the cooler photo apps for iOS was VSCO Cam, an extremely popular camera with pro-quality filters and effects. Now this app is available for Android on Google Play for your Nexus 7 tablet and any other devices running Android 4.0 and up.

Initially introduced as an Easter egg deep within Android's operating system, the Daydream screensaver feature turned official in the release of 4.2.2 Jelly Bean. Now, it's been out for a few months, which means developers have already figured out how to take advantage of it in their own ways.

Every time Apple releases a new product or software update, people quickly figure out exploits in order to bypass the lock screen without having to type in the passcode. It happened last year in iOS 6, so it's not surprising that it happened again in iOS 7.

In old-school Konami fashion, there's an Easter egg lurking inside your Samsung Galaxy S3, and I'm not talking about gingerbread men, robots, or jelly beans. In fact, it's actually an achievement, like those you would unlock in Black Ops on your Xbox 360, and it's pretty easy to find.

A free Wi-Fi hotspot can be a lifesaver. Whether it's because you have shitty reception, need faster connectivity, or just don't want to go over your monthly data plan, free Wi-Fi in public areas is greatly appreciated. While connecting to these free hotspots is fairly easy, finding them can become a whole nother issue. I've been in plenty of situations where I wasted my data plan instead of taking a few steps to the right, where free Wi-Fi would have been waiting for me and my Samsung Galaxy...

Apps sure do run great on Android tablets! If you caught that little whiff of sarcasm, you probably already figured out I was lying. There is a definite lack of good, high-quality apps specifically made for Android tablets. If you've ever tried Facebook or Twitter on a tablet, you know exactly what I mean.

Matte and flat colors have became quite popular. I was surprised to see how many cars used these colors at SEMA 2011.

"Dude-man-bro, are you going to Coachella this year?" If I got a dollar for every time I was asked that question, I might just have enough money to actually buy the dang ticket. Concerts have been, for a very long time now, a great way to spend a night or a weekend having fun with friends and listening to some great tunes.

A lot of computers come with a ton of pre-installed software from the manufacturer, some of which you need and some of which you could most certainly live without. And over time, you may have downloaded and installed a bunch of programs and apps that you probably can't even remember. Now, you could go ahead and uninstall everything that you don't think you need, but then you run the risk of removing something that could really mess up the system. When I open up my Programs folder, I feel like...

Remember the 1960's American television series Batman, with Adam West as Bruce Wayne? It was waaaaay before my time. The caped crusader that I'm more familiar with is actually this one... When I first heard of Adam West, it was him doing the Batusi on The Simpsons. I had no idea what was going on, so I looked up Adam West and his sensual dance and found myself face to face with the 1960's Batman.

UPDATE: A patch to fix the exploit has been released. Download it here.

Earlier this week, Spiderlabs' vulnerability researcher Jonathan Claudius discovered a key in Windows 7 and 8 registries that makes it easy for anyone with physical or remote access to a computer get a hold of the user's password hints. When the "UserPasswordHint" key is read, the hints are displayed as a code that looks encrypted, but Claudius noticed a pattern of zeroes that could be easily translated back to plain text with a decoder he made in Ruby. He added this functionality to the Meta...

If you use Ubisoft's uPlay browser extension, you should probably get rid of it right now. An Information Security Engineer at Google discovered that the plugin has a hole in it that allows programs to be installed through uPlay, essentially letting anyone who feels so inclined to take over your computer. How the Exploit Works

Do you own an HP printer? If so, it may be vulnerable to malware attacks. Researchers at Columbia University discovered that 25% of Hewlett-Packard printers have significant vulnerabilities that put your printer in danger from hackers—even your home. With a budget of just $2,000, researchers Salvatore Stolfo and Ang Cui were able to hack into the printers using remote firmware to install malware, and in some cases even cause the printer to catch on fire. The main issue is with the printer's c...

Discover yet another of the delicious use for that cast-iron skillet you bought in this video from Jenny Jones, who teaches you how to make a Dutch Baby. No, you don't have to go to the Red Light District. Heck, you don't even have to leave your kitchen! A Dutch Baby in this case is a Dutch-style pancake covered with bananas and strawberries. In an Amsterdam pancake shop the fruit would be cooked into the pancake itself instead of spread over the top, but either way this recipe is tasty!

Trust is one of the most important aspects in a relationship. You can work on some trust building exercises and activities to strengthen your current relationships. Plus some of these activities are just fun.

Instead of just going for a walk through the outdoors, try adding in the rewarding hobby of bird watching. The song sparrow is a great bird to look for on perches and will vary in appearance across the US.

It is important to have healthy teeth not only for your appearance but for your overall health as well. You can keep your teeth white by avoiding foods that stain your teeth and having a good cleaning routine including fluoride

Bodyguard jobs can lead to an extremely rewarding and exciting career path. Learn to become a bodyguard with tips on training and salary from a professional bodyguard and former Secret Service agent in this free career video series.

Swing dancing dates back to the 1920's, where the African American community, discovered the Charleston and the Lindy Hop, while dancing to contemporary Jazz music. The term "Swing dancing" is used to refer to one or all of the following swing era dances: Lindy Hop, Charleston, Shag, Balboa and Blues and extends to include West Coast Swing, East Coast Swing, Hand Dancing, Jive, Rock and Roll, Modern Jive, and other dances developing in the 1940s and later.

From expert golf site, Golf Link, another free lesson for beginning golf players! In this video, learn how to hit a golf ball the proper way. The best ways to learn how to hit a golf ball are by taking lessons, making sure to achieve a good grip and making sure that the arms hang straight down. Discover why hitting a golf ball is harder than it looks in this video.

If a perm is too curly, get rid of the perm by shampooing the hair, applying a heavy conditioner and using a chemical straightener. Discover how hair salons can get rid of perms with this free video from an experienced hairdresser.

2020 has been a rollercoaster of a year for all of us, the type of year that makes you feel like you're not sure if you're upside down or right side up. But as the holidays arrive, it's time to get your bearings back and find the good in the world — the type of good that we could use more of right about now.

The COVID-19 pandemic has practically shut down all sports except for World Wrestling Entertainment, which has continued staging matches without an audience, leaving us sports fans with nothing much to cheer for. While they can't replace live games, smartphone games provide an alternate reality to live out our competitive entertainment in the absence of the real thing.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.
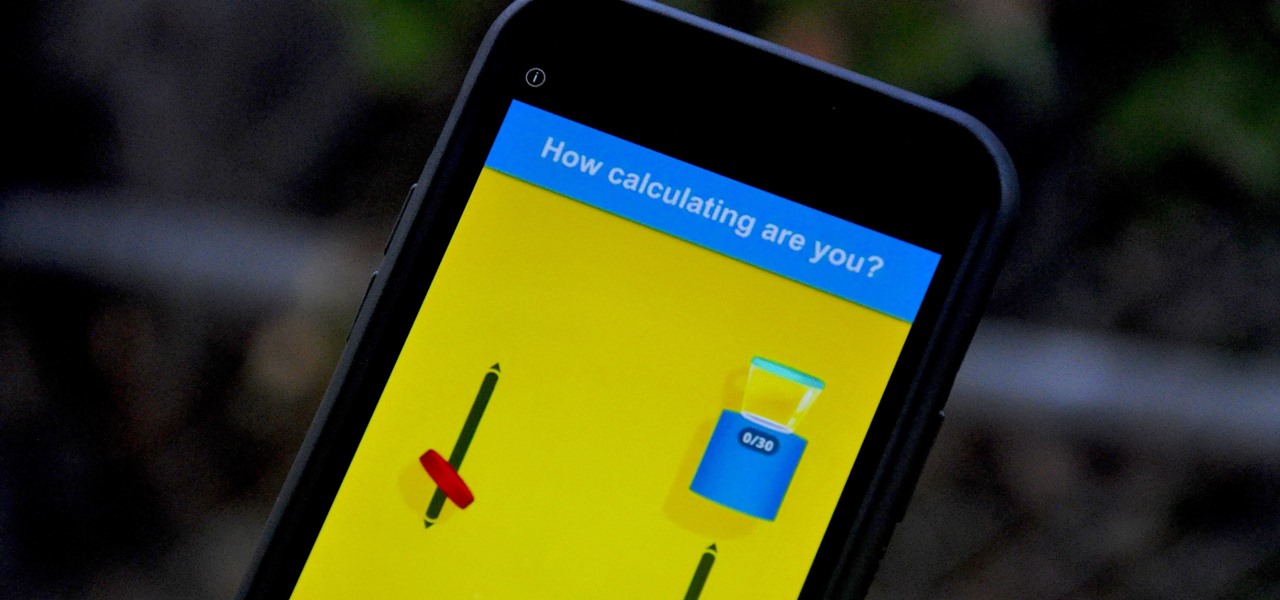
No one likes in-app advertisements, especially in mobile gaming, but they're necessary because they offer developers a way to make revenue without having to charge you to play. In some games, in-app purchases give you the chance to remove ads, but what can you do about apps that don't offer the option to kill ads?

In years past, the Consumer Electronics Show (CES) mostly dabbled in the future as far as the long-term vision for augmented reality was concerned. This year, however, objects in the future are much closer than they appear.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

Whenever the name Magic Leap comes up, the talk inevitably seems to turn to the company's big-name backers and "unicorn-level" amounts of cash poured into the venture. And if it's not that, observers tend to focus on the company's market strategy and overall prospects.

We've already shown you our favorite new action games that have come out this year, but now it's time to share our all-time top ten list. These games are available for both Android and iPhone, they don't have intrusive ads or freemium schemes, and most importantly, they're all completely free to play.

While a viable version of consumer-grade smartglasses has yet to find mainstream success, two more contenders emerged this week, as Vuzix confirmed that a leak of a fashion-forward design is legitmate and Vivo introduced tethered smartglasses designed to pair with its new 5G smartphone.

Over the past two years, the tech industry has formed a series of symbiotic relationships that are now converging in the augmented reality space. This week, we took a look at these interrelated technologies and how they are shaping the future of AR.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.