You can easily share and transport your photo and videos on the Canon EOS 7D by using the wireless file transmission option. See exactly how sharing and downloading your files to computers and other devices works in this video. When the digital SLR camera is combined with the WFT-E5A Wireless File Transmitter, transmitting is easy.

There's a new LCD viewfinder on the Canon EOS 7D, and in this video, you get to see all about it. See how you can change your viewfinder options on this digital SLR camera with ease. You can display almost any information you want.

The EOS 7D has an accurate level display, which you can activate on either the read LCD monitor or in the viewfinder. See how to work the electronic display on the Canon digital SLR camera. This is great for getting a steady shot wherever you need it.

The Canon EOS 7D can be fine-tuned to adjust its auto focus to suit nearly any subject. See how you can customize your AF functions to get the best focusing options needed for your desired result. This video breaks down everything.

See the workings of memorizing AF points on the Canon EOS 7D digital SLR camera. It's easy to memorize points and come back to them whenever you want, by just pressing a button. See how to use the memorization option in the video.

Let your Canon EOS 7D do all the hard work. With the AF Point Selection option, the digital SLR camera will do all the focusing for you. It's easy to compose and shoot in just one step.

Mailboxes don't have to look all lonesome, with only the curb to cheer them up. If you have one of those street boxes on a post instead of a house box, the best thing to do to make a happy mailbox is to give it some company. To improve your home's curbside appeal, take your landscaping efforts to the curb and enhance the area around the mailbox. It's a great way to accentuate your landscape.

With thousands of beauty companies out there, we can generally find at least one lipstick shade that makes us look more dazzling than New Year's Eve. But sometimes, whether you need to match your lipstick to your dress or just can't seem to find The One, you need a specific color that no brand carries.

Left handed writing style is not as common as right handed so many people are not sure how to do it neatly. Check out this tutorial for advice on how to improve your grip and posture to make your handwriting perfect. Left handers face many challenges. First of all, most teachers will teach children writing skills more suitable for their right handed classmates, also there are not many left hand specific products on the market, and left handers often have posture problems as they are pushing t...

Live View wit the EOS 7D camera from Canon, lets you compose and view your subjects with the LCD monitor as your viewfinder. This is great for a multiple of reasons. See how to use live view on this digital SLR camera.

You can use the Canon EOS 7D to shoot digital video at a variety of frame rates and resolutions up to full HD. In this video, see the basics of movie mode and how to use it. This is the best digital SLR camera to film video with.

In video shooting, it's always best to select manual focusing on the Canon OES 7D digital SLR camera. If you need to adjust focus during filming, then you can manually refocus when needed, but there are also powerful autofocus options available. Watch this to see how to change the movie mode settings for your needs.

The new Canon EOS 7D digital SLR camera uses a powerful lithium-ion battery called the Canon LP-E6. You can manage your battery's capabilities with the battery display in your camera. See how in this video.

If you're not one to trust you digital SLR camera's automatic focus options, then the only thing you have to do is go to manual mode. With the Canon EOS 7D, select the Manual AF Point Selection and take control. It allows you to pick the area you want to focus on.

Thrusting, thrusting, thrusting... No, we're not talking about sex here, we're talking about LARPing. To be specific, boffer sword fighting.

While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal.

Graham Potter of Kaizen Bonsai shows Bonsai beginners how to make interesting trees from relatively available materials. He first details the history of the specific tree he will be working on. He points out that this specific specimen has small, compact foliage, branches that support itself, craggy bark, and a nice taper in the trunk. He begins to shape the tree by cutting the small amounts of foliage that are dead or weak as well as the foliage grows beneath the branches. He then uses hand ...

Do you win the prize for messiest room in America? That's a difficult contest, but how about messiest room in your house? It’s time to clean your room, so do a good job in the shortest amount of time and get your parents off your back.

Horrible at saving money? Creating a savings account to put aside and accumulate money is easier with these strategies.

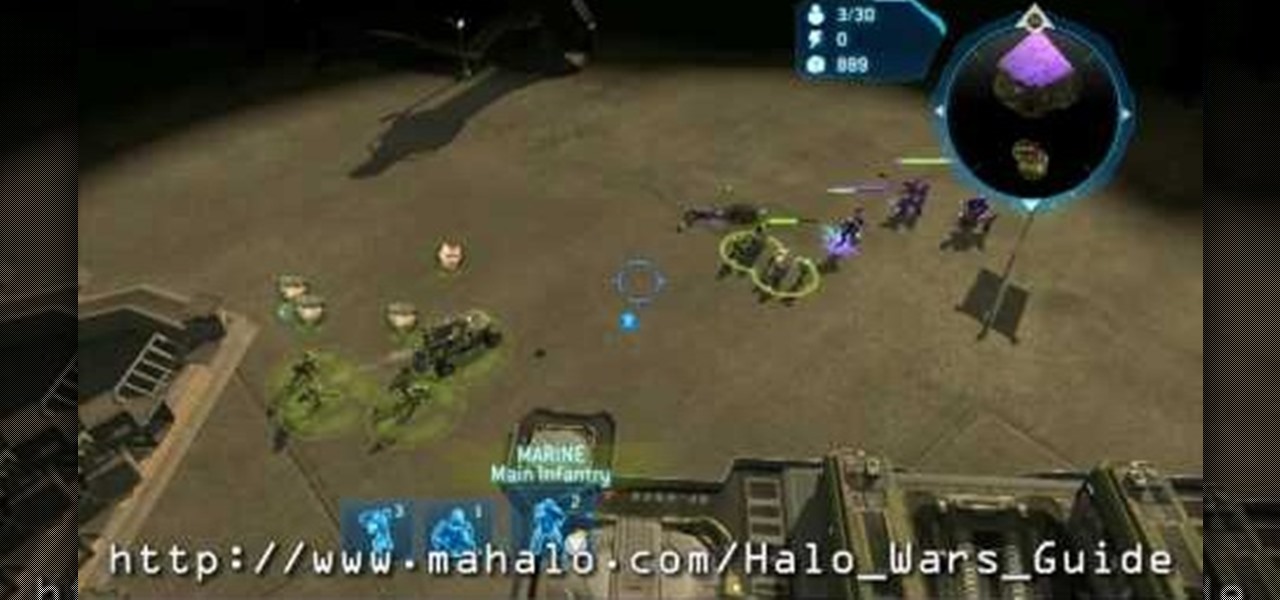
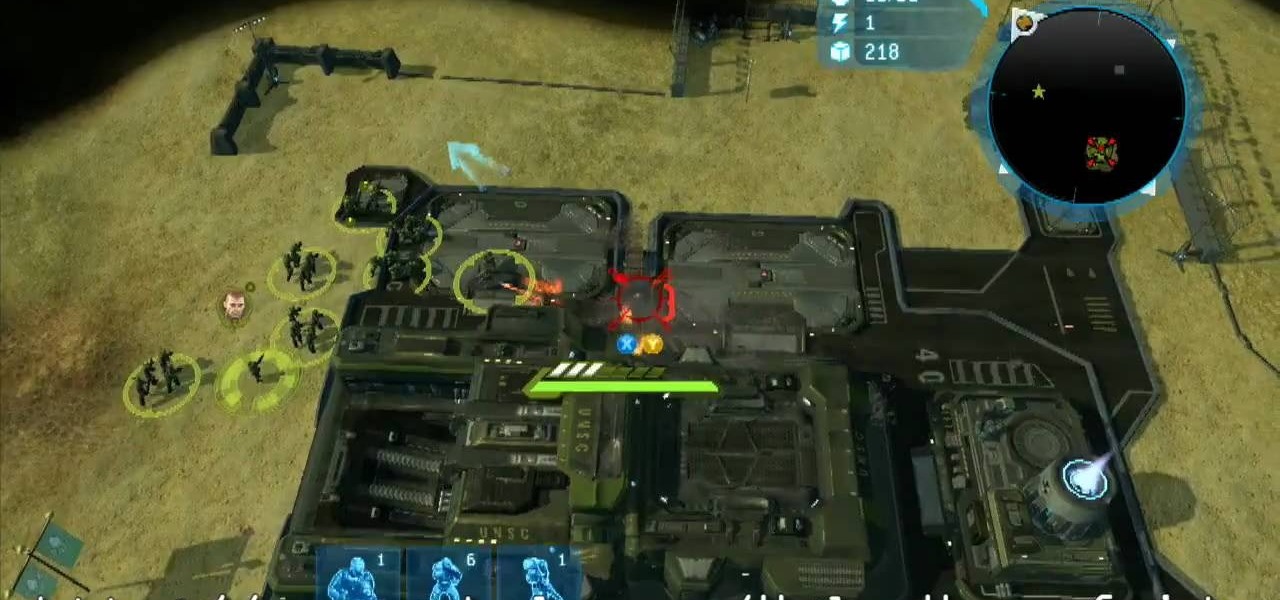
Halo wars is a real-time strategy (RTS) game that takes place in the Halo universe 20 years before the original game took place. Halo Wars is for the Xbox 360.

Check out this 5 part walkthrough of Halo Wars - Mission 4: Arcadia City. This is the fourth chapter in XBOX 360's Halo Wars. This walkthrough helps you beat the game and is brought to you by Mahalo Gaming.

Beat Halo Wars now! Check out this walkthrough of Halo Wars - Mission 6: Dome of Light. This is a quicker way to make it through the game and beat Halo Wars. This is a production from Mahalo Gaming.

Check out this 4 part series on Halo Wars. This is a walkthrough of the Halo Wars, game for XBOX 360. This is a great way to cheat a little and beat Halo Wars before your friends. This walkthrough is brought to you by Mahalo Gaming.

Check out this 5 part series walkthrough for Halo Wars - Mission 9: The Flood. Beat Halo Wars with a little help from Mahalo Gaming's walkthrough. This is a brand new game for XBOX 360.

Check out this walkthrough of Halo Wars - Mission 10: Shield World for XBOX 360. This walkthrough is a wonderful creation from Mahalo Gaming. This is a 5 part series on how to beat the entire Mission: Shield World.

This walkthrough of Mission 15: Escape is the last chapter of Halo Wars. Complete Mission 15 and you'll have beat the game. This is a 6 part series walkthrough from Mahalo Gaming.

Artists discovered the almighty vanishing point during the early Renaissance and haven't stopped using it since. The genius of the vanishing point is that it gives a three dimensional quality to a two dimensional space, meaning increased depth perception and more believability.

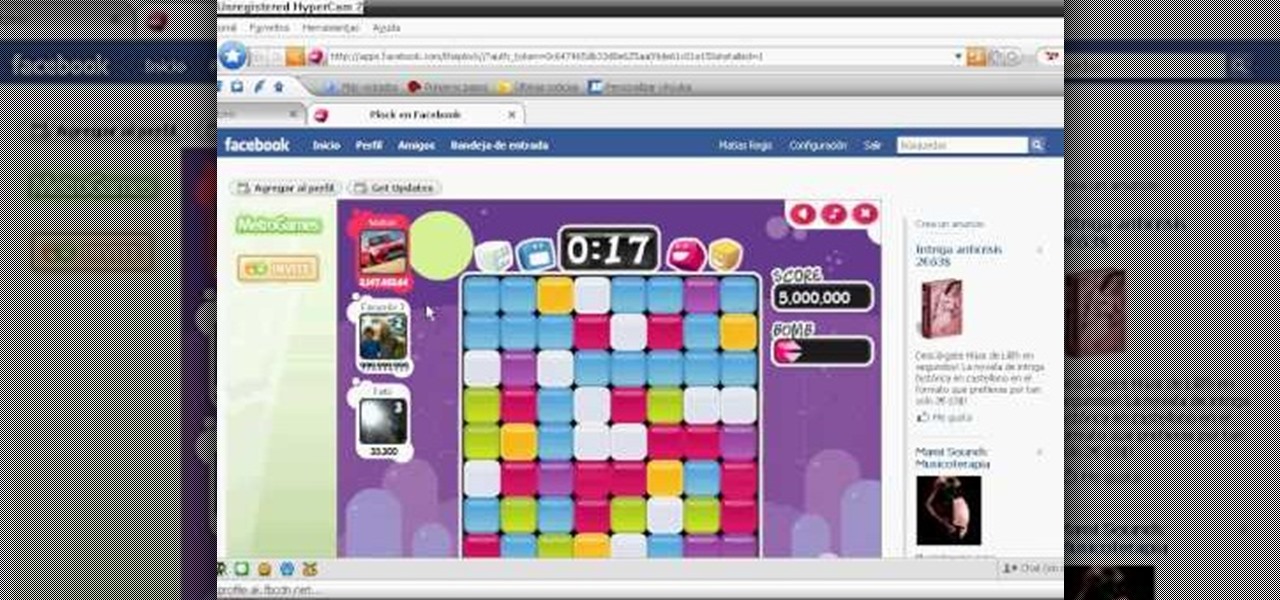
Want to learn about hacking Plock? You've come to the right video. Using Cheat Engine to hack Plock, you can do just about anything.

Swing dancing dates back to the 1920's, where the African American community, discovered the Charleston and the Lindy Hop, while dancing to contemporary Jazz music. The term "Swing dancing" is used to refer to one or all of the following swing era dances: Lindy Hop, Charleston, Shag, Balboa and Blues and extends to include West Coast Swing, East Coast Swing, Hand Dancing, Jive, Rock and Roll, Modern Jive, and other dances developing in the 1940s and later.

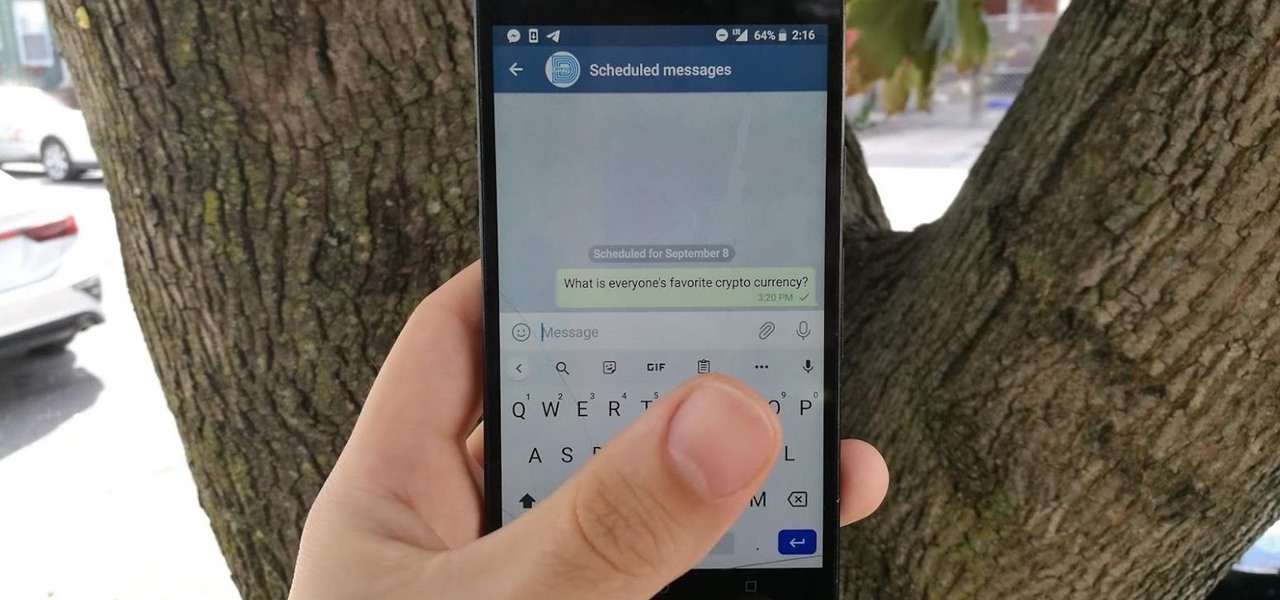
Sometimes you may need to send a message out at a specific time. Say a thought strikes you late at night, but you don't want to wake anyone up. You could do this by waiting to sending it at your desired time — or, you could schedule your message at a precise time.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

Learning Chinese is hard, but it can be a lot easier with the help of a few great apps. As a native English speaker who's currently living in China, this is a process I've recently gone through. After playing the field, here are the three apps I personally think will help you the most with your Chinese learning adventure.

Apple found itself in serious trouble last week when a teenager discovered a critical FaceTime bug that threatened the security of nearly every iPhone user. The bug enabled a user using Group FaceTime to access either the microphone or the camera of a recipient before they answered the call. According to Apple, the issues have been fixed in an iOS 12.1.4 update released Thursday, Feb. 7.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.