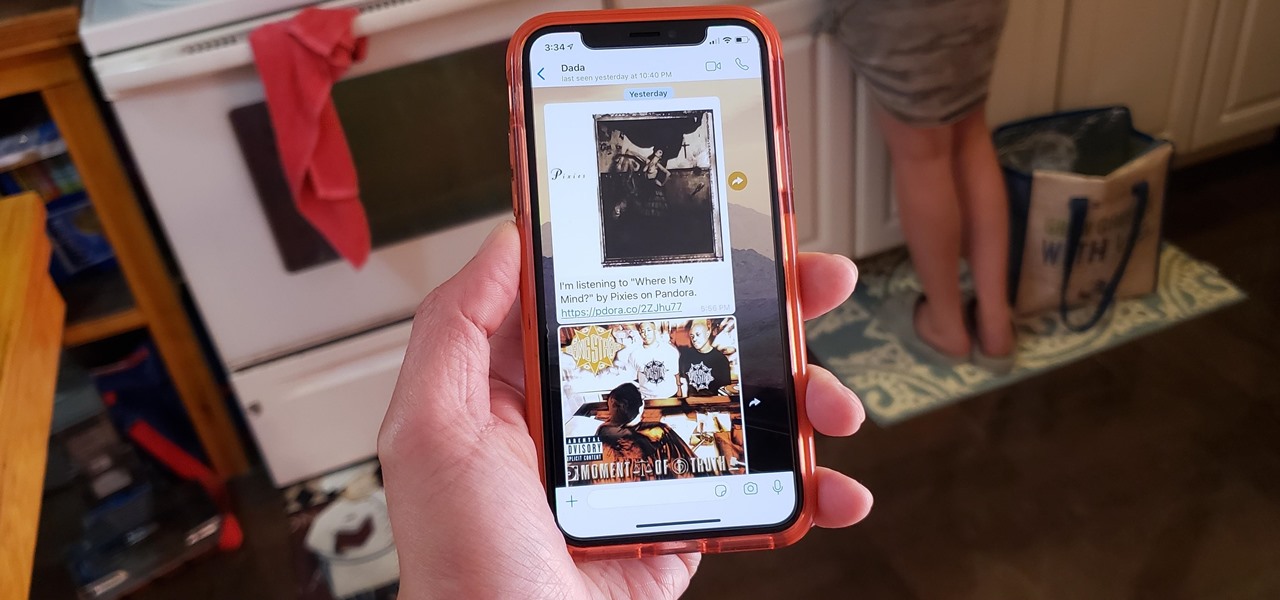
One of the best parts of Pandora is its personalized stations that auto-generate songs within the specific style or genre you've chosen. Not only does this play your favorite tracks with regularity, but it also opens your ears to previously unknown songs or artists — ones you may fall in love with and want to share with others.
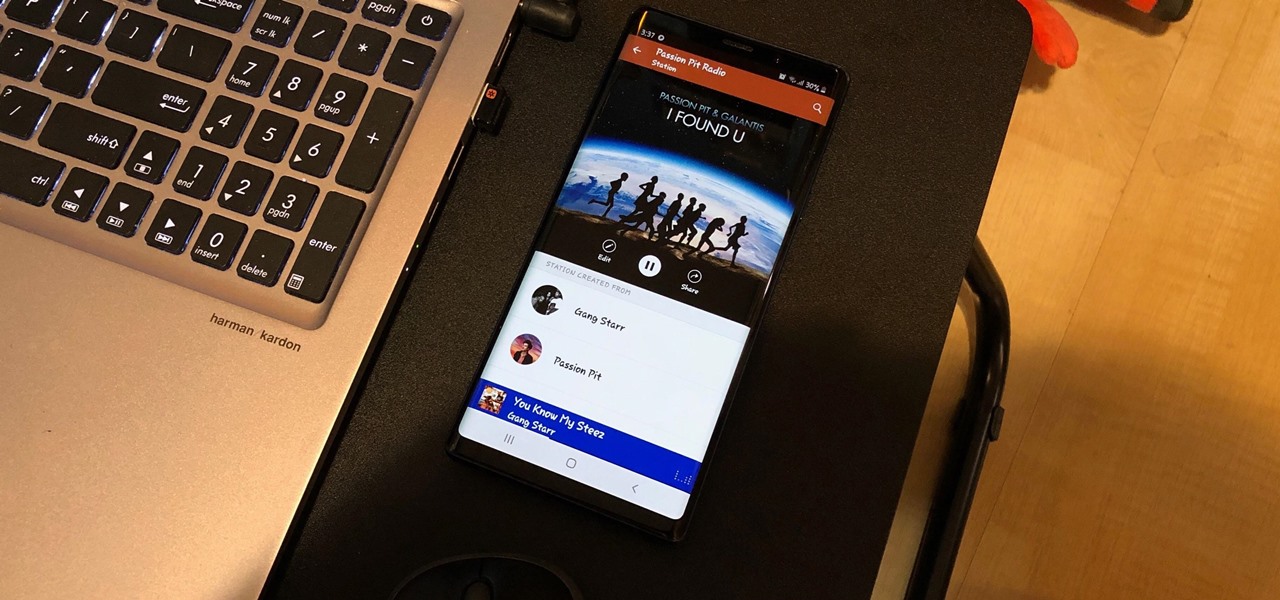
Whether you're out for a drive, commuting to work, or just taking a stroll, listening to your favorite tracks on Pandora takes the legwork out of choosing which songs to play next. After a while, however, you go-to playlist can get repetitive, as the same songs from the same artists seem to play over and over. Luckily, Pandora makes it easy to add variety to your stations in just a few taps.
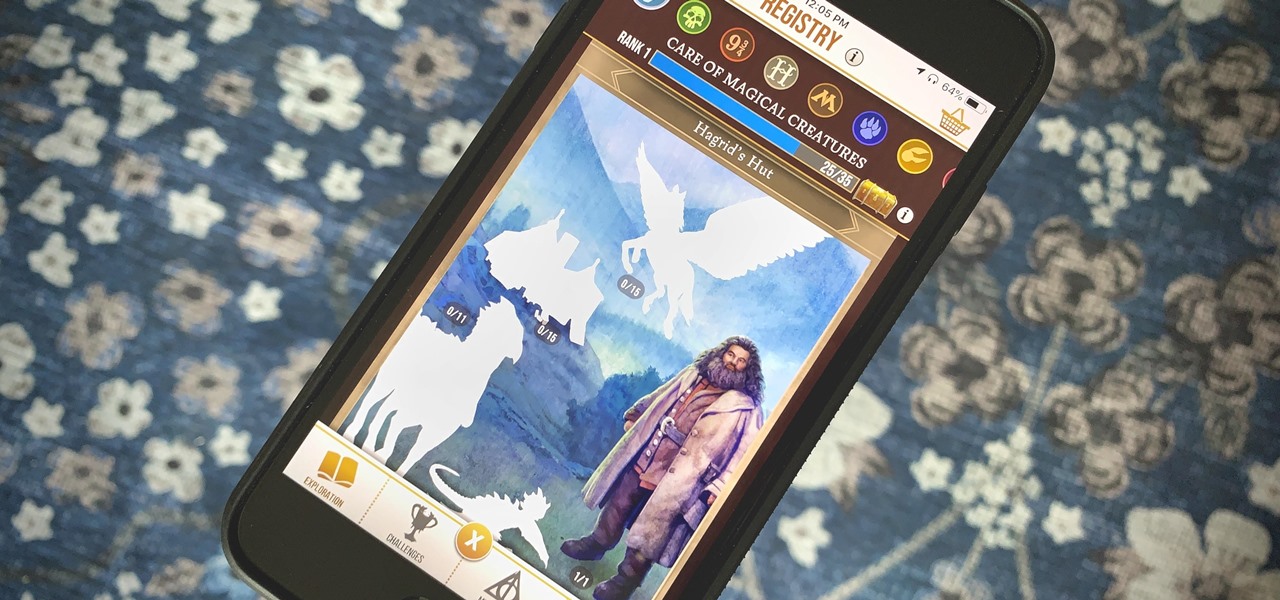
From the first moments of booting up Harry Potter: Wizards Unite to the hours of walking you're bound to experience, one thing is clear — encountering Foundables and defeating their Confoundables is a significant plot point of the AR game. While you receive rewards each time you retrieve a Foundable, the real treasure comes from completing parts of the Registry, called "Families."

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

After testing the waters with a few pop-up stores along the West Coast earlier this year, North is bringing its smartglasses to more cities across the US and Canada.
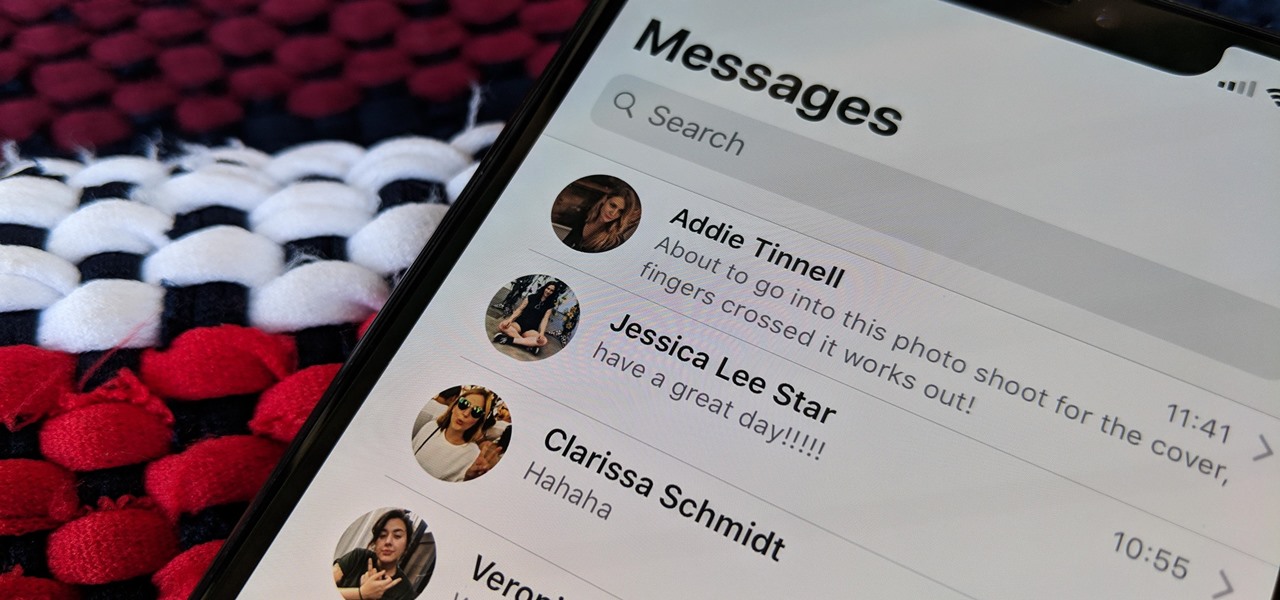
The Messages app on iOS features contact photos for every one of your conversations — including group chats. Even if you don't have a picture for a specific contact, their initials will appear instead. For non-contacts, a generic profile avatar appears. These give threads a bit of flare, but if you're looking for extra privacy or don't enjoy the look, you can easily hide those images and icons.

Your Skype contact list might contain a sea of names that make it tough to find a specific person you're trying to reach. The same goes for your loved ones and colleagues, especially if you have a common name like Jennifer or John. Knowing that, you might want to change your Skype display name to set yourself apart.

With the upcoming Memorial Day weekend serving as the unofficial start of summer, Pepsi is turning to Instagram to help sell its soft drinks to quench the thirst of beachgoers and BBQers.

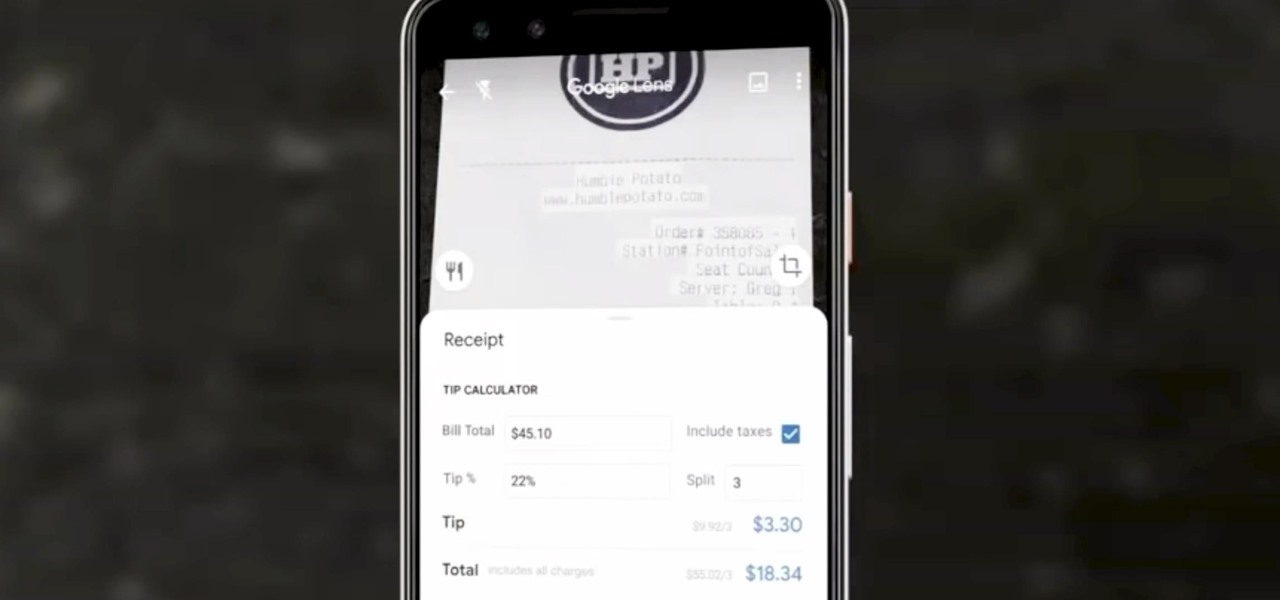
Google Lens can perform many different tasks with your smartphone's camera thanks to advanced machine learning, such as foreign text translations, landmark identification, and business cards to contacts conversion, to name a few. With this year's Google I/O conference, we have another cool Lens feature to look forward to — receipt calculations.

When setting up a Raspberry Pi, it's easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi's default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called rpi-hunter, hackers can discover, access, and drop custom payloads on any weak Pi connected to the same network.

On Monday, the world watched in horror as the historic Notre Dame Cathedral went up in flames in Paris.

One of the biggest advantages of the front-mounted ultrasonic fingerprint sensor found on the Galaxy S10 and S10+ is that you no longer have to physically pick up your device and reach around the back to unlock it. Instead, you simply place your finger on the screen for easier access and added convenience — at least on paper.

The first annual Snap Partner Summit kicked off on Thursday in Los Angeles, and with it came some new products announcements, several of which enhance Snapchat's already robust augmented reality powers.

Samsung's popular Good Lock app has been updated to work on One UI and now lets you take full advantage of its awesome add-ons to customize your S10 in a few simple taps. One add-on in particular lets you get rid of mostly redundant indicators like the NFC "N" for a cleaner status bar.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

It's easy to forget just how cool face filters are. Augmented reality has come a long way, and apps like Instagram now offer a suite of impressive effects to play with, but some of the best ones aren't easily found. There is a treasure trove of exclusive, custom face filters that are unavailable to the general public, but not at all inaccessible — you just need to know the trick to getting them.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

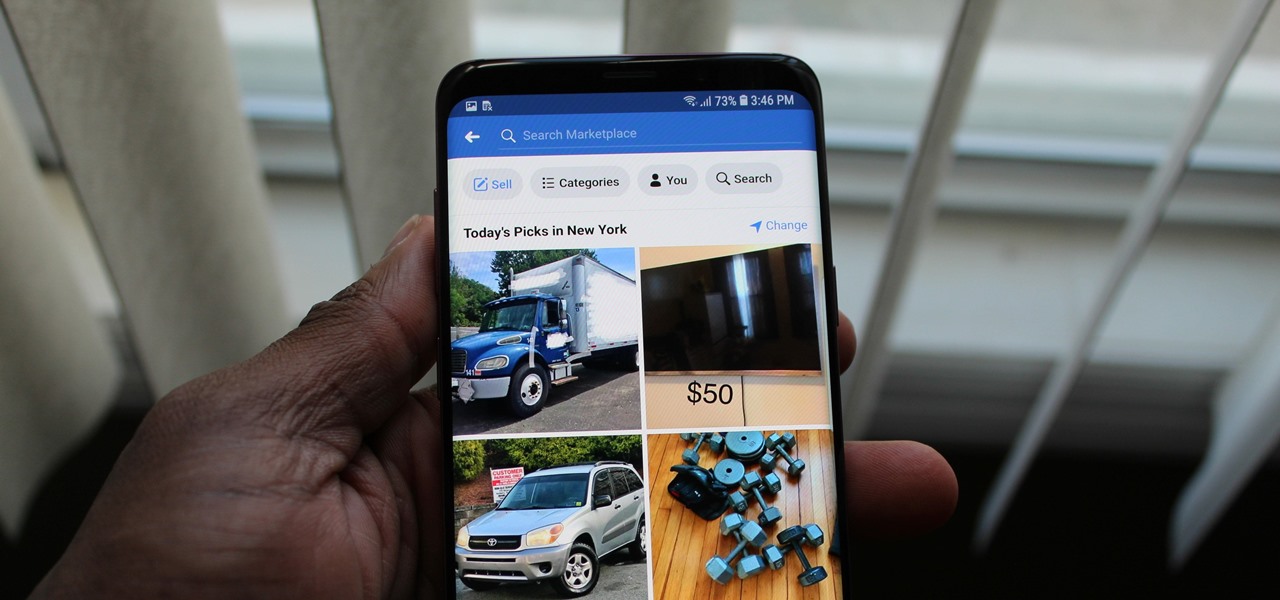
While many of Facebook's tools are well received as they enhance the experience, one which is often complained about is the Marketplace. The Craigslist-like feature which offers a way to facilitate transactions between users can be a little overbearing with its alerts. However, you can change that.

Designing and manufacturing waveguides for smartglasses is a complex process, but DigiLens wants us to know that they have a software solution that partially solves that problem.

The city of London is getting a holiday gift this season, but it's not the kind you unwrap, since it's completely delivered in augmented reality.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

If you're looking into buying shoes from DSW on Black Friday, then you can save an extra 20% — but only if you smile more.

In recent years, Apple has assembled its augmented reality team and supply chain through a series of acquisitions, high-profile hires, and strategic investments, but at least one potentially major deal was recently ditched.

You just brought a brand new Pixel 3 from the Google Store, and you insert your SIM card only to find the phone won't recognize it at all. No matter what you do, the SIM card won't register and your Pixel won't connect to your carrier network. That's what happened to me and several other Pixel 3 owners. The good news is a fix is coming, the bad news is Google doesn't have a date for that fix.

One developer has taken the formal name of the Magic Leap One: Creator Edition quite literally with an app that enables users to create a custom universe in their own living room.

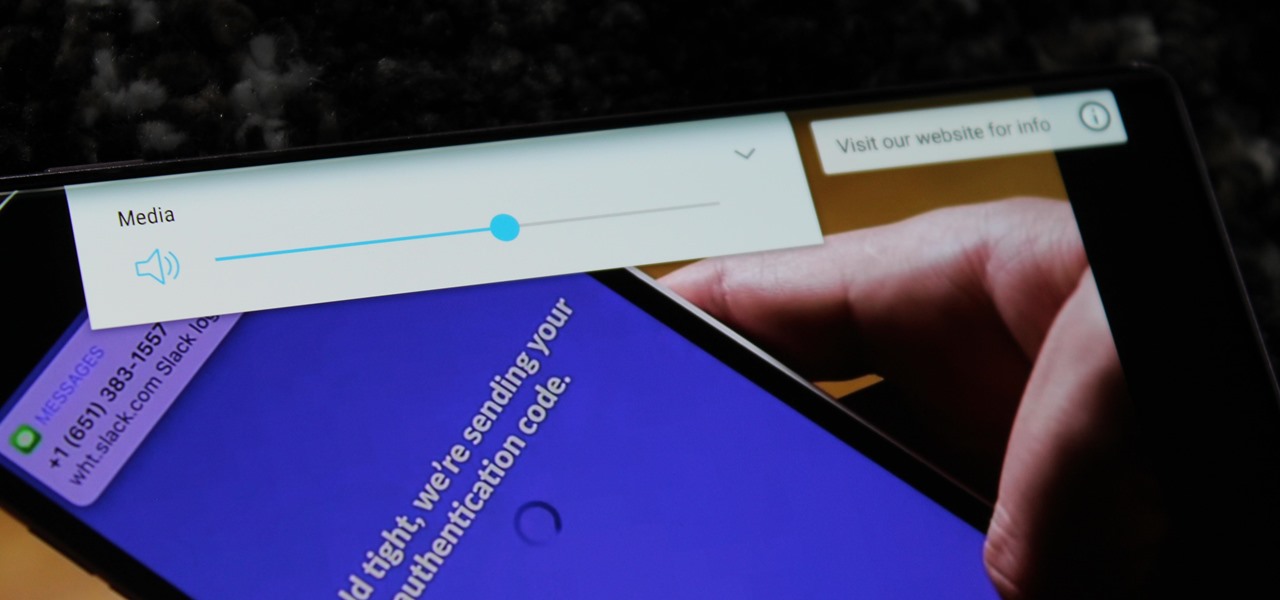
For some, the Galaxy Note 9's volume rocker doesn't have enough steps between silent and max volume. We all have different preferences for volume, and a higher number of steps would equal to more precise volume control. Good thing we can at least adjust this for the media volume.

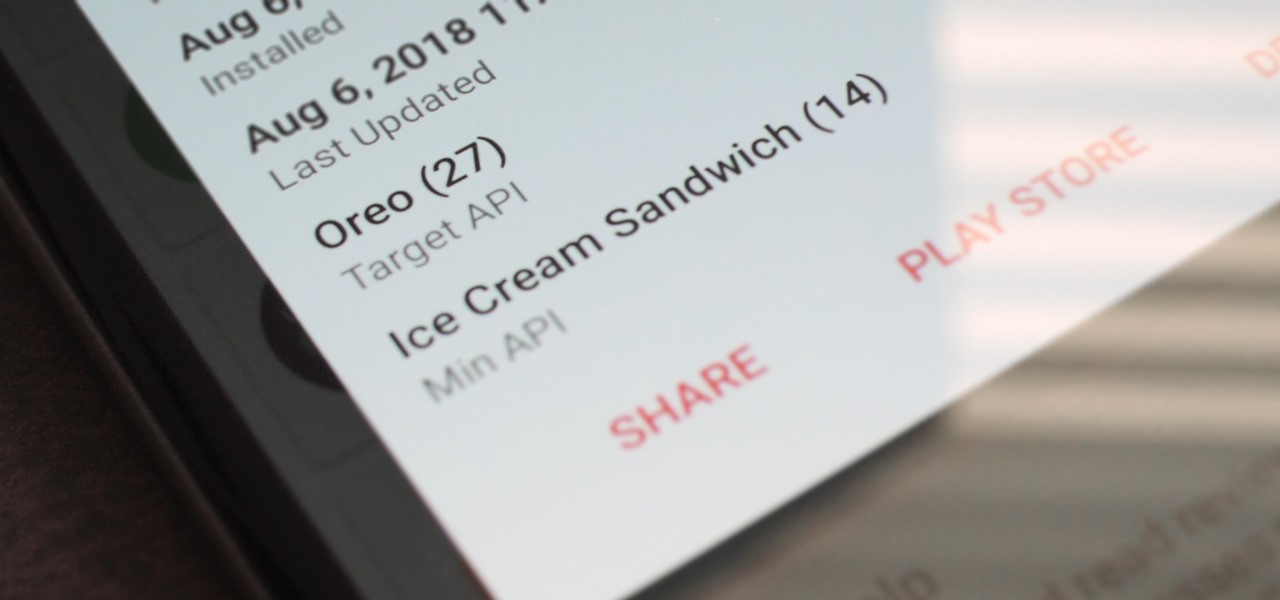
Starting November 1, 2018, Google will require that all new apps and updates to existing apps target Android 8.0 Oreo or higher. This move means the developers behind many of your favorite apps are now scrambling to get their software modernized, while others are considering abandoning outdated apps altogether.

If you're on the hunt for a profitable side-gig, or even a completely new way to to make money, you'll want to take a look at Upwork, a leading freelancing platform that connects skilled freelancers with clients from all over the world.

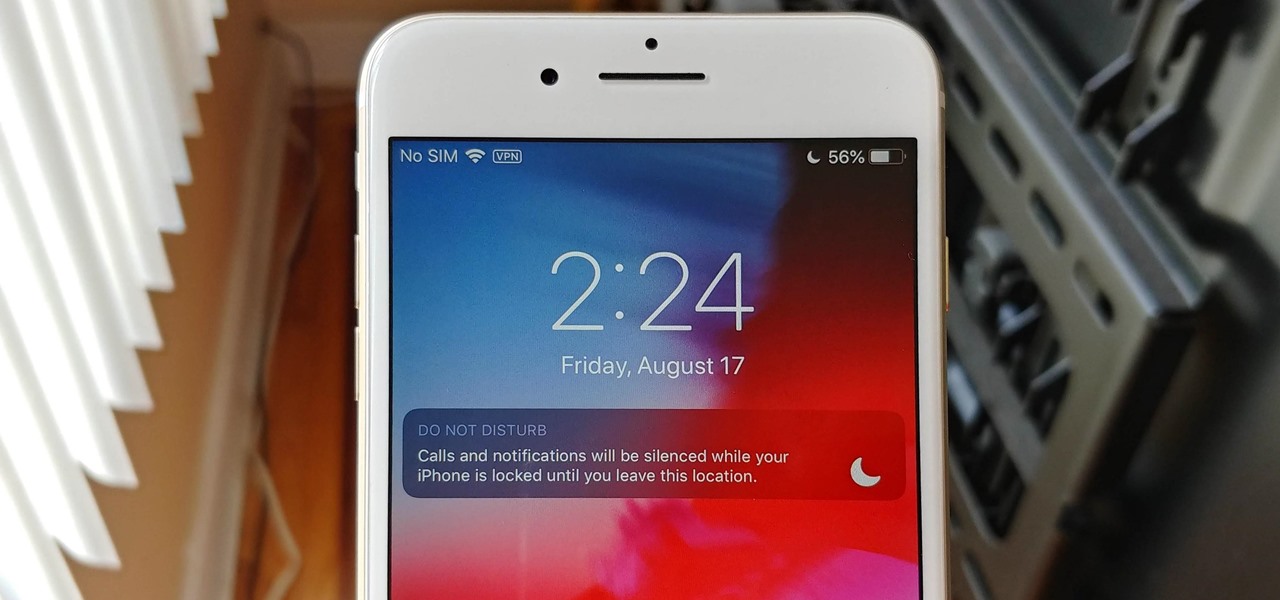
One of the new iOS 12 features for iPhones is an enhanced version of Do Not Disturb mode. Instead of being limited to times you manually input, Apple added new ways to manage the feature, including activating it based on location. For those on the go, this can be done pretty quickly.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

Mozilla has created yet another browser for Android. Similar to Firefox Focus, Firefox Rocket was designed to address specific problems: limited internal storage and low data caps. However, in the process of solving these problems, they created one of the fastest browsers on the market.

There's actually more to the dialer screen on your OnePlus than meets the eye. Besides its obvious purpose of calling people, there's a vast array of secret codes that you can input to troubleshoot your device, in addition to revealing important information, making anonymous phone calls, and so much more.

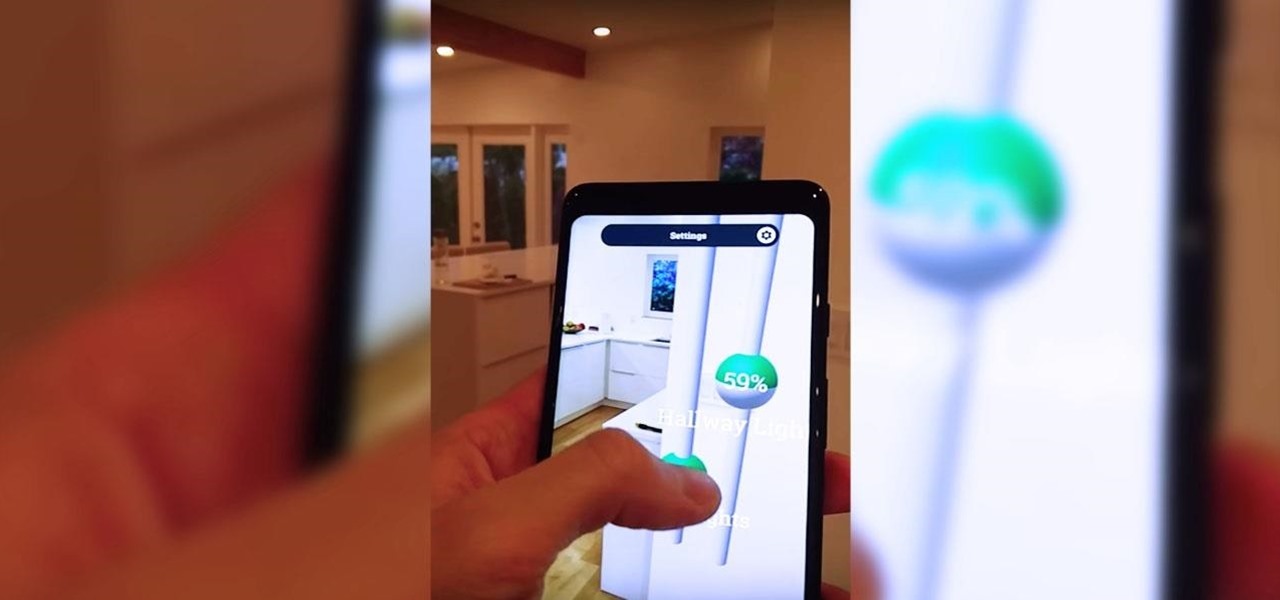
Voice-activated digital assistants from Amazon, Apple, and Google currently have the upper hand for home automation integrations, but a new augmented reality mobile app promises to give homeowners and renters visual control over their connected appliances.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

With all the talk about the impending release of the Magic Leap One, some have forgotten a very important, competing release on the near horizon: the HoloLens 2.0. Well, now we have new information that tells us when (roughly) the device will be released, as well as a few other exciting tidbits.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

Snap Inc. added stickers back in 2016 to its Snapchat app, and it has been building on that functionality ever since. Now, you can add Bitmojis and even GIFs from Giphy to your photos and videos. Even better, you can pin any of these stickers to background items or moving subjects when sharing videos. That means stickers aren't pinned to the screen itself but to a real-world location.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.