Backdoors are convenient to leave behind once you've already found a way into a server, and they can come in handy for a variety of reasons. They're good for developers who want a quick way into machines they're working on, or for systems administrators who want similar access. Of course, backdoors are also a hacker's best friend, and can be added in a variety of ways. One good tool for doing this is Weevely, which uses a snippet of PHP code.

Halloween is this weekend, so if you're looking for a last-minute big batch cocktail that will keep your guests properly hydrated—and might turn them into mutants—look no further! (Note: This will not actually hydrate anyone, just so we're clear. Priorities, people!)
Blue light (like that from our smartphone) tricks the human brain into thinking it's still daytime, even if it's coming from something as small as a screen. So while you're playing around with your new Pixel or Pixel XL after dark, subconscious signals to be awake are preventing you from getting to sleep as early as you should.

Some of the best Android apps are not hosted on the Google Play Store, and that means you have to sideload them if you want to get their awesome functionality. But without the Play Store, these APKs are never automatically updated, so your only choice has been to scour the internet for a newer version when you need a bugfix.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

When it comes to hacking guides, most are written from the perspective of a Linux user. There are a few outliers, but it's mainly Linux, which leads to the idea that Linux is the only OS that's viable for hacking. This couldn't be further from the truth. A properly set up Apple machine can do quite a bit of heavy lifting.

Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.

Fall is here, and it's time for warm, filling meals... that don't involve a lot of effort, because it is getting cold outside and you spent a full day at work wishing you were on the couch with a blanket over your head, dammit.

When Facebook purchased WhatsApp for $19.3 billion back in 2014, we all knew this was coming—it just took longer than we thought. But starting today, the data mining became official, and now, information from your favorite messaging app is no longer out of reach for the world's biggest social media site.

The HTC Vive and Valve's SteamVR make for one of the more compelling virtual reality experiences, mixing in real-world motion tracking with the immersive headset. But third-party manufacturers couldn't tap into the Vive's full potential and make creative new peripherals—until now.

Keyboards and mice work fine for computers, but in a holographic environment you'll want to do more than just point, click, and type. While we can still benefit from these input devices, complex hand-tracking methods are necessary for the evolution of mixed reality user interfaces.

Nintendo rolls out its first smartphone-specific game in the U.S. on March 21st, and the main protagonist is... you. Well, your Mii, and it's not a game, but a social app.

Logan's Run is one of my favorite movies of all time. The dialog is cheesy, the set design and special effects are wonky, and the main villain looks like he was conceived and built by an eighth grader in shop class—oh, and his name is Box.

For years, users have been clamoring for a "dark mode" theme in Android, but it has always seemed like Google is so committed to the white motif from their web services that such an option would never become a reality. But in a stunning turn of events, Google is finally embracing the idea with a night theme that will work in any app, and I'll cover all of the specifics below.

A lot of things have been changing over at Microsoft recently. Not only did they acquire the ever-popular Android keyboard SwiftKey and give away Windows 10 for free, but they've started a Google X-like experimental division called Microsoft Garage, and they've actually released quite a few awesome Android apps.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

The dock in Mac OS X is intuitive, customizable, and aesthetically pleasing, which is a stark difference from its clunky Windows alternative. In fact, in Windows, it takes both the Start menu and taskbar to accomplish what Apple's dock does—but it doesn't have to be like that. Below, I'll show you how to add an OS X-inspired dock on any PC running Windows XP or higher. Step 1: Install Aqua Dock

Welcome back, my budding hackers! In this series, we are trying to understand how AV software works so that we can learn to evade it. To that end, we are working with the open-source AV software, ClamAV. I had previously introduced ClamAV in Part 2 of this series. If you have not installed it yet, go back to that and install it.

Nice people finish first—or is it last? Though you may have been told throughout your life that being kind pays off, there are some obvious advantages to getting mean. So whether you're driving towards a goal at work, or need to attack a task in your personal life, acting like a jerk just might help you get what you want.

In Minecraft 1.9 New Command Blocks can be used to make elevators. You types different commands to achieve controlling the elevator for movement you like. This tutorial tells in Minecraft 1.9 how to use command blocks to make elevator. Lets just have a look at it!

After a few months, I get so fed up with hearing the same ringtone go off alongside each new notification that I'm forced to switch things up—only to end up repeating this whole process when the new one gets played out. And I'm sure people around me are equally sick of listening to that tired old tone towards the end as well. I mean, a decade later, I'm convinced that Nokia tone is permanently implanted in my brain.

Your brain holds a lot of precious information and is capable of great feats. However, there's one quality that doesn't lie among its strengths—memory security. Yes, that's right, your brain can be hacked, and it doesn't take a psychologist to do it. Anyone with the right know-how can change your memories for their own personal benefit, and you can do so to others, too.

The new iPhone 6S and 6S Plus models have a really cool feature called 3D Touch that lets you perform app-specific Quick Actions from the home screen for apps that support it. The only downside is that this awesome new feature is not available on older iOS devices.

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

Greetings, hackers and friends! I know it has been a while since I posted a tutorial, and hopefully I can make up for that by posting a series.

If you have a specific app you want to lock so that others can't access it, the most secure way of doing so is with biometrics. While there are options to lock apps with either a PIN or pattern, these can easily be figured out with a simple glance over your shoulder. It's much more difficult for someone to crack your fingerprint ID, unless they chop off your finger, of course.

Windows has always been pretty customizable, and there are a ton of ways to change up the way your PC looks—though, it hasn't always been easy. In the past, changing anything other than wallpapers, titlebars, and fonts involved long hours of switching out system files with modified versions and changing icons to no end, but that's not the case with SkinPacks.

You must have read news about hackers dumping the data online, recent one was Ashely Madison. It's only the big companies' data, which gets noticed once it is out. There are many other small leaks which don't even get a mention. So this article is the first one of my series which will help you to find hacked accounts. Some of you must already know about this, but this post is intended for the new learners. This also serves as an example of my learning how a good service can be used in other w...

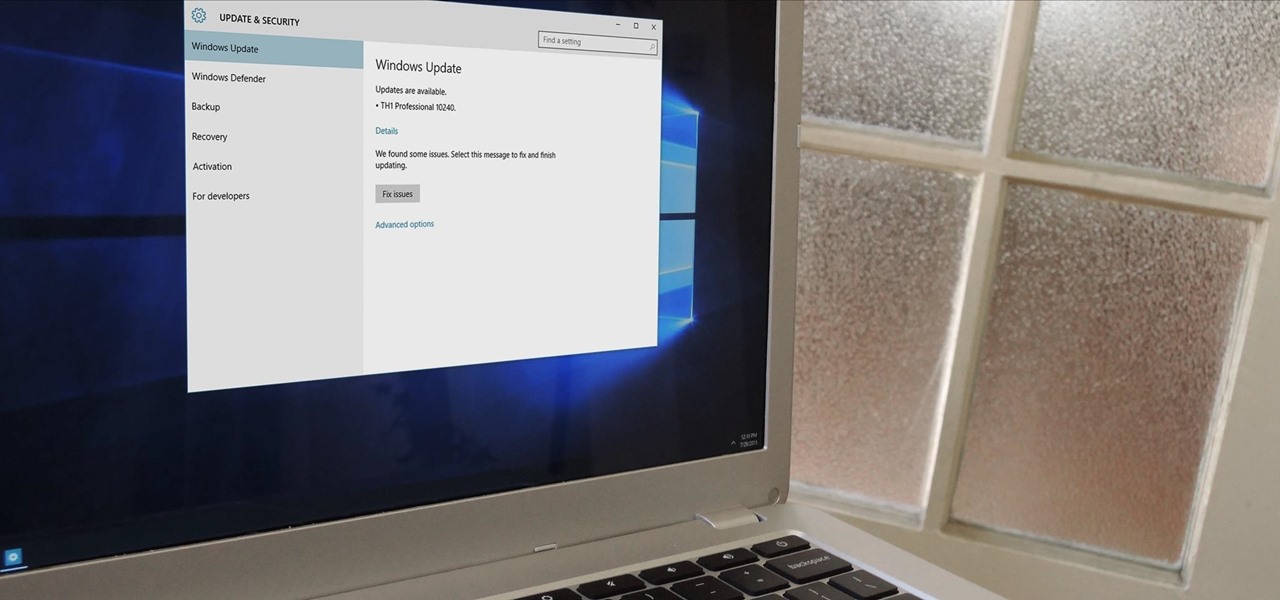
In a bit of a strange decision, Microsoft has made it to where some users don't have a choice in the matter of applying failed automatic updates. When a Windows or driver update comes your way and fails to apply for any reason, your computer will continue to attempt applying the broken update at seemingly random intervals. The Pro and Enterprise editions of Windows 10 will allow you to delay or stop updates altogether when something like this happens, but the Home edition has no such setting.

With the amount of time we spend glued to our smartphones, they could be considered a second job (if only we got paid). I spend a large part of my day scrolling through Reddit, Facebook, Instagram, and countless other apps, and burn through hours and hours without even noticing.

Long time reader, first time 'How To' poster. This tutorial has been highly requested. Here are the steps to perform a Pixie Dust attack to crack a WiFi password that has WPS enabled.

Saying that I was obsessed with Pokémon as a child would be a serious understatement, and even though I'm not the Pokémon fanatic I once was doesn't mean I don't love playing still. However, I do often find myself dumbfounded by all of the new features and characters in each generation.

The Samsung Galaxy S6 includes a pretty nifty feature known as "Gesture wake up," which lets users wave their hand over their locked display to wake it, making those periodic notification checks from the lock screen a lot more simple than having to press the power or home key every time.

We've all been there: slipping on a pair of perfect yet slightly uncomfortable shoes, hoping they'll stretch to fit perfectly. After about 30 minutes of wear, suddenly those fantastic shoes aren't feeling very great. By the end of the day, your poor feet are covered in throbbing blisters.

These days, there is no shortage of ways to exchange files to and from friends and family: text messages, email, Bluetooth transfer, and cloud services are just a tiny sliver of what you can use to share music, photos, videos, and more.

Your Apple Watch only looks as good as the band that it's bound to, but if you're looking to purchase one directly from Apple, expect to spend anywhere from $149 (for the Milanese Loop) to $449 (for the Link Bracelet).

Customization helps your device stand out from the rest, and that sentiment is no different when it comes to the Apple Watch. Unlike every other Apple device before it, the Watch allows you to customize the information that appears on the UI—without the need for any jailbreaking.

As you're probably well aware by now, the Apple Watch isn't just for sending text messages and checking Instagram—you can also use it as your wallet. With Apple Pay compatibility, you can use your Watch to make purchases at any retailer that accepts the payment service.

As someone who loves to run around my neighborhood, the Apple Watch feature that excited me the most was the ability to go out and exercise while listening to music, all without having to lug my iPhone around.

Widgets exist to offer quick access to certain features in the apps we use most. On the Samsung Galaxy Note 4, home screen widgets let me do pretty much anything, from checking the forecast to browsing my emails.