
How To: Get great skin like a celebrity
Not everyone in Hollywood owes their nice complexion to a dermatologist. Here are some homespun beauty secrets you can steal.


Not everyone in Hollywood owes their nice complexion to a dermatologist. Here are some homespun beauty secrets you can steal.

Your kitchen is the heart of your home, and is as individual as you are. No matter what your ultimate goal, there are several initial steps you will take to begin remodeling your current kitchen, regardless of its size or shape.

Watch this quick RV tutorial video to find out how to maintain or repair your furnace. All of the items shown are simple steps you can do yourself. Some motor homes have two furnaces and some have one. They should be located on one of the sides of the unit. In the shape of a medium sized rectangle. This compartment will also have a grill and it does stay hot. In order to open it up, remove the screws, remove the first door, and then there will be another one that just comes down as well. Then...

Check out this demonstrational video to learn how to create lighting FX and fog behind the back of a tombstone that's a great prop for Halloween sets.

Watch as a seasoned professional demonstrates the steps necessary for cleaning a fireplace, including how to prepare the area, how to use various cleaning tools, and how to stay safe in the process -- in this free online video about home care.

Preparing before hitting a golf shot should help you stay out of trouble on the golf course. Learn how to prepare for a golf shot from a professional golf instructor in this free golf instruction video.

Get tips for training dogs to lay down, come, stay, and walk on a leash in this free video series on dog training.

This tutorial for Devil May Cry 3 covers the basics of jump canceling and the overall advantages it will provide the player once mastered. The whole concept of a Jump Cancel (JC/JCing for short) is the cancellation of an aerial technique with a jump.

"Buy low and sell high" is great advice, but how do you accomplish it? While the stock market can be unpredictable, it's not a complete enigma. There are patterns to watch for that can make you a successful trader.

When you press the Home button on your iPhone SE, you're not quitting your current app. Instead, it stays open in the background. If an app ever bugs out on you or you don't want it to run in the background, you'll need to force-close to quit it completely. Doing so is also helpful when your app switcher gets too cluttered, and you find it hard to switch between apps because of it.
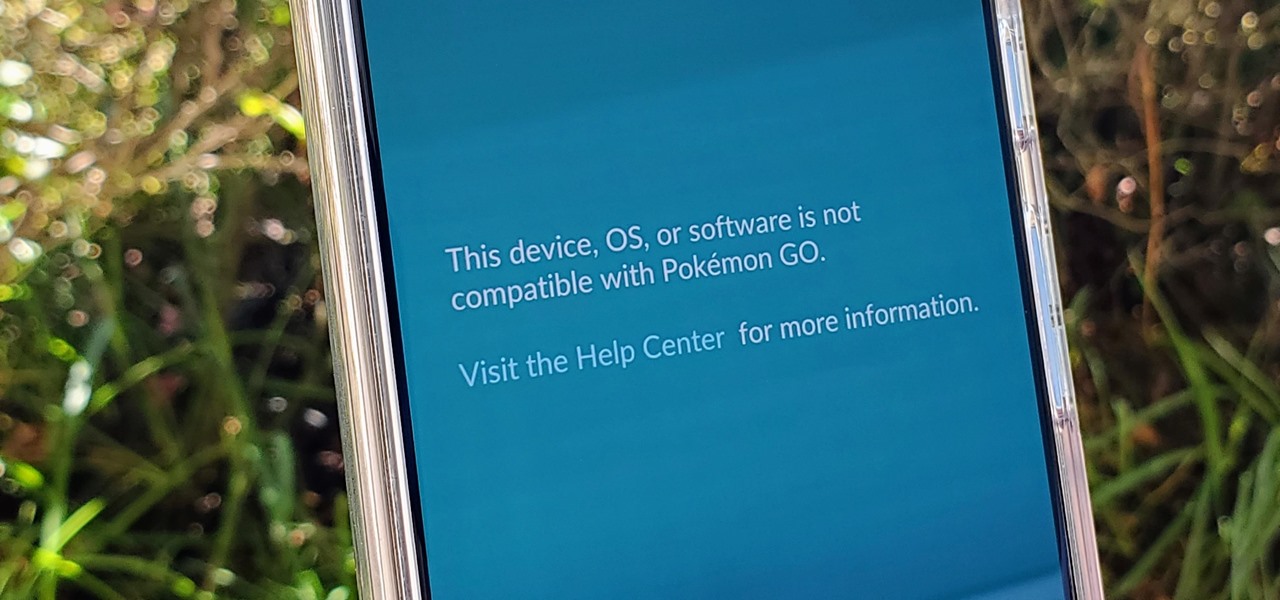
If you're a root user who has played Pokémon GO over the years, then you're probably familiar with the detection methods used to spoil your fun. The game's developer, Niantic, has publicly mentioned their ongoing battle with rooted Android phones and are unwilling to let up. They have a no-nonsense approach to try and keep you from playing, and they've stepped their game up once again.

Every 5G model of the Galaxy S20 comes with 12 GB of memory. This amount of RAM is overkill, but Samsung's been putting similar amounts in its flagships for years. Since you have it, why not put it to use? With One UI 2, you can.
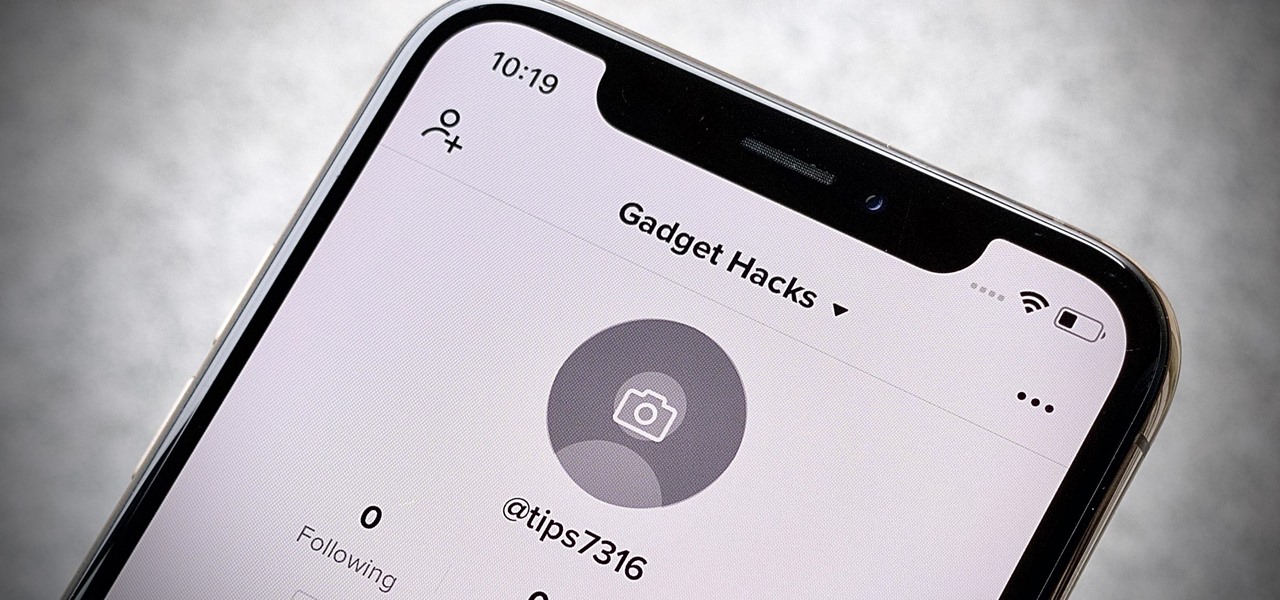
Many of us install TikTok just to see what it's like, but most of us stay for good. Inevitably, that involves creating an account. The problem is, TikTok assigns you a username, usually based on your email address — an odd choice for a platform made for self-promotion. If you're not happy with your random TikTok handle, you can change it.

While the rest of the world is scrambling to figure out how to adopt augmented reality and VR tools for remote meetings, one company is building its war chest to serve the growing space of corporate clients who need this kind of immersive computing training.

After jumping to the head of the class of augmented reality journalism in 2019, USA Today is continuing to push the medium forward in 2020.
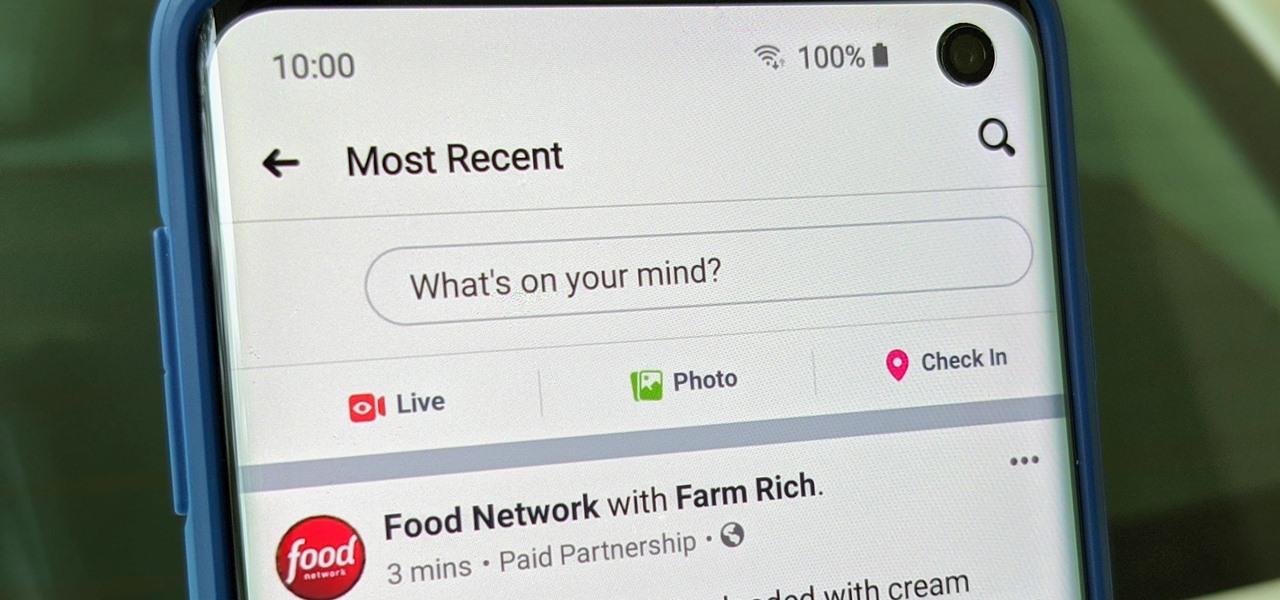
Facebook is where a lot of people get their news. The problem, though? Your Facebook feed gets jumbled with random post times, which isn't useful for keeping up with new stories in real-time.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

One of the coolest things about Android is the massive development community behind it. These developers keep on cooking up new things even after official support has stopped for an older device. It breathes new life into somewhat forgotten devices, which is always great news. With Android 10 out, it's time to see what phones will get the custom ROM treatment.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

The iPhone 11, 11 Pro, and 11 Pro Max are the most advanced flagships Apple has to offer, but that doesn't mean they're immune to occasional bugs. Anything from an app plagued with issues to a faulty software update still can cause your device to freeze up, so having the ability to force a restart can come in very handy.
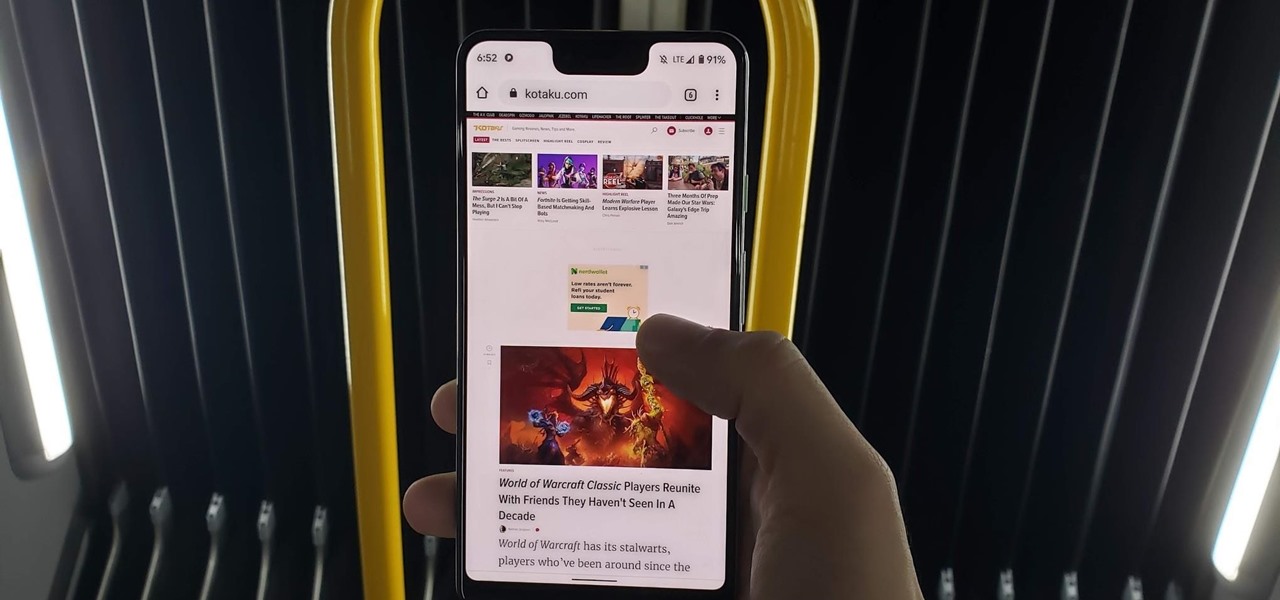
It's now standard for websites to have a mobile version. Conveniently, we can browse the web with a mostly mobile-optimized experience. But what if you want the desktop experience on mobile? If you want, you can browse the mobile web and see only the desktop version of websites on Android devices.
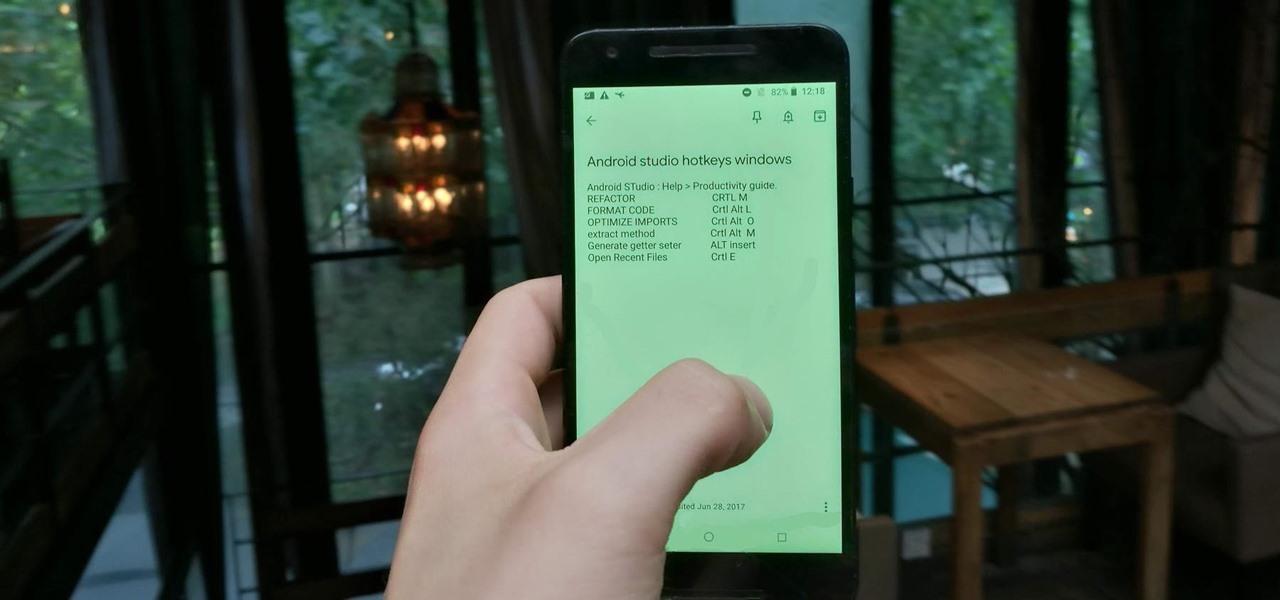
Everyone occasionally has tipsy fingers that lead to mistaken button taps. Even if you didn't accidentally delete your note, you may have found that it is in fact still relevant and not time for that note's demise. Thankfully, there's a simple way to undelete your Google Keep notes.
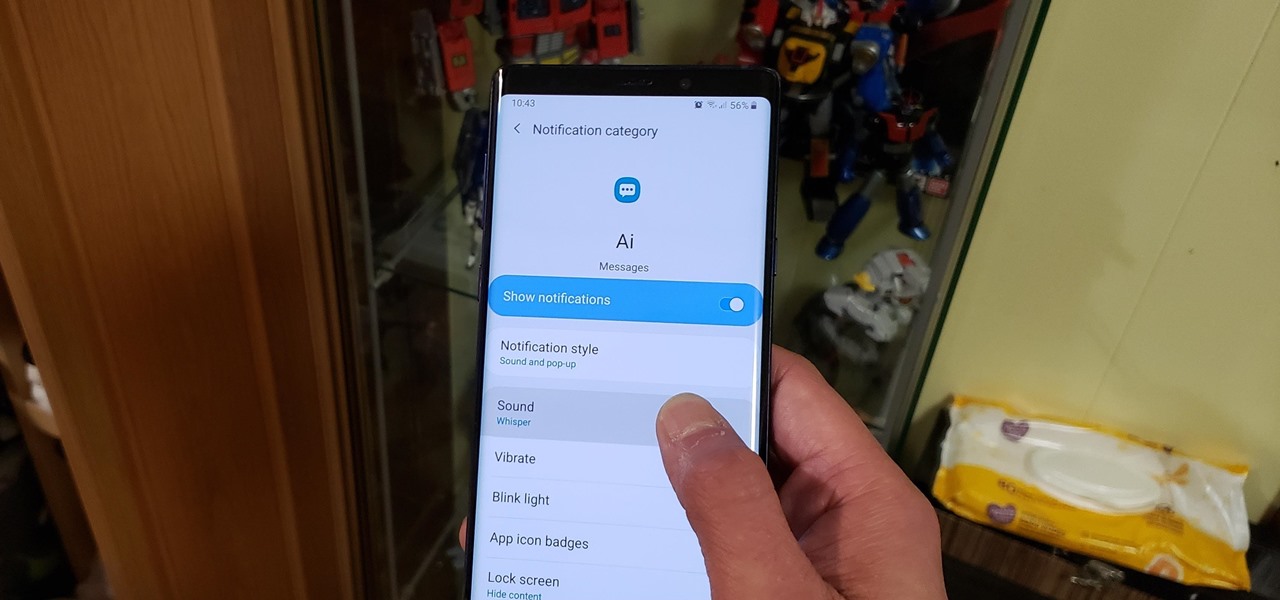
Some messages take precedence over others, so having the same notification tone for all your threads isn't always the best solution. Fortunately, Samsung Messages has a simple option you can tweak to set custom sounds for specific chats to help you stay on top of priority conversations and reply much faster.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

Despite the recent gut punch of staff layoffs, Canada-based smartglasses startup North and its Focals are likely to be in the game for a while longer.

While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. In this guide, we'll build an Arduino program from scratch and explain the code structure in a way anyone can understand.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

Recently, Google's Messages app has become an important cog in the Android ecosystem. That's because, for the time being, it's one of the only texting apps which supports RCS Universal Profile for iMessage-style conversations. Even better, Google just gave it a highly sought-after feature: dark mode.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

For the curious, here are a number of close-up shots of the Magic Leap One's optics and the magnetic attachment that can be swapped out for a version with lenses matching your glasses prescription in the near future.

If you're a part of Generation X or a Millennial, there's a good chance that the first mobile game you played was Snake on an old school Nokia phone. Now, you can relive that nostalgia of monochrome and push buttons in augmented reality with the Facebook Camera.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

Whichever web browser you use, each comes with a way to surf the net "secretly." While nothing on the internet is truly anonymous, private browsing modes can help keep your movements hidden from those who might have access to your data. The "secret mode" for the Samsung Internet app goes a step further on Android, by locking your private browsing behind a unique password.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.
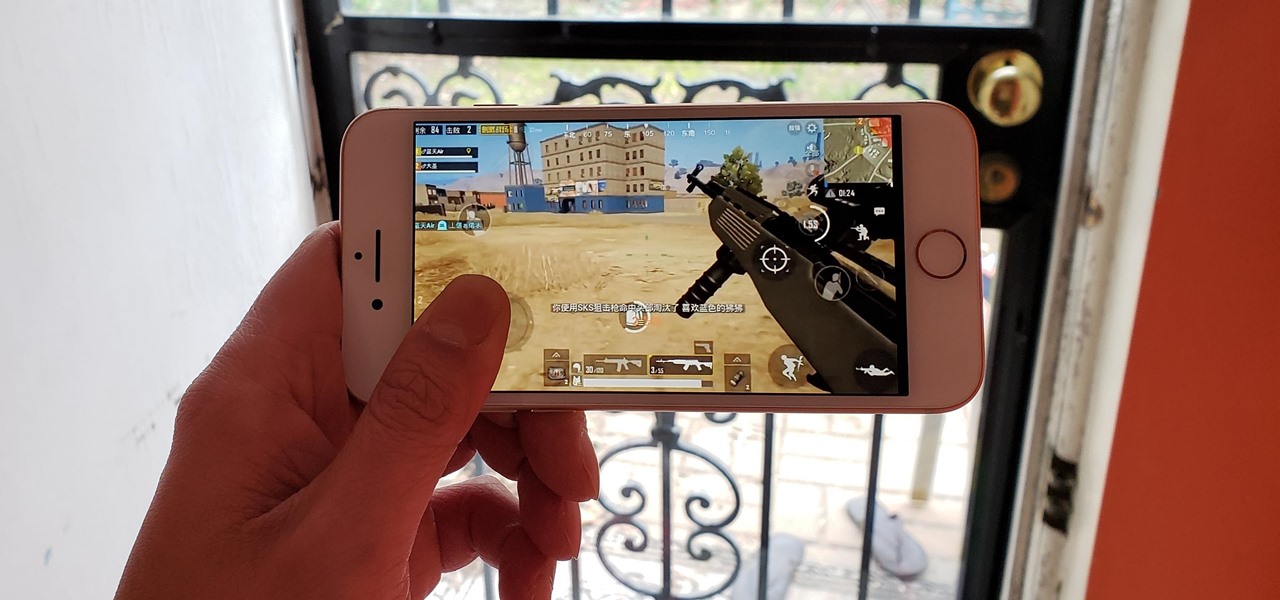
The recent 0.4.0 update for PUBG Mobile brought us a host of welcome features like the training ground and arcade mode. Sadly, one highly sought-after feature remained out of our reach: The ability to play in first person perspective, or FPP mode. Our wait may soon be over, as this gameplay mode could be out as soon as the next update hits for both Android and iOS.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Two weeks ago, Samsung took the wraps off their much-anticipated Galaxy S9 flagship. Preorders opened on March 2 with official retail availability scheduled for March 16. As usual, several of the US carriers have begun shipping the devices ahead of schedule. Last week, Sprint began shipping out devices to a few lucky customers. Today, T-Mobile appears to be joining the party.

Multitasking on a smartphone has never been better, but it still has some ways to go to compete with a desktop experience. Samsung hopes to change that with a new multitasking view on the Galaxy S9, which allows the user to open notifications in a new, smaller window on top of the app they are currently using.

On Monday, German newspaper and digital publisher Axel Springer announced its role as the latest company to invest in Magic Leap. This is just the latest in a series of investments the augmented reality company has garnered from the likes of Google, Qualcomm, Alibaba, Legendary Entertainment, Warner Bros., and others amounting to almost $2 billion in overall funding.