This video will show you the right and proper safety gear for kayaking. Kayak safety gear is one of the most important aspect of kayaking. The most important kayak safety gear is the life jacket. It should be short torso so you can move freely and it does not rise up. Make sure that all the straps are tighten when you wear it. The next important kayak safety gear is a whistle. You will use it when you are in trouble or in emergency. Blow it once to catch attention and 3 times during emergency...

Whether you're shopping for deals, need help with a little math, or any number of other occasions, it's a valuable skill to know how to quickly figure out a percentage given two numbers.

Learning how to read a compass might just save your life one day! Know how to use a compass and you'll never get lost in the wild. Follow these simple steps & you'll learn this valuable skill.

Can you barely keep your eyes open at work? So bored you could sleep through the entire day? Seinfeld's George Costanza built a bed under his desk, but we'll tell you how to be a bit more subtle. Here's some tips on how to get a some quick shut-eye at work.

Frustration is something that comes along with learning to ride a bike. You mustn't give up as it's a valuable skill to have. This video shows you how to ride a bike and minimize frustration.

You've drafted a promising team, and the season's under way. Now increase your chances of making the playoffs.

Compulsive gambling is a recognized addiction, just like alcoholism or chemical dependency. Follow these steps to see if you might fit the profile. Recognize the signs of compulsive gambling with this guide from Howcast.

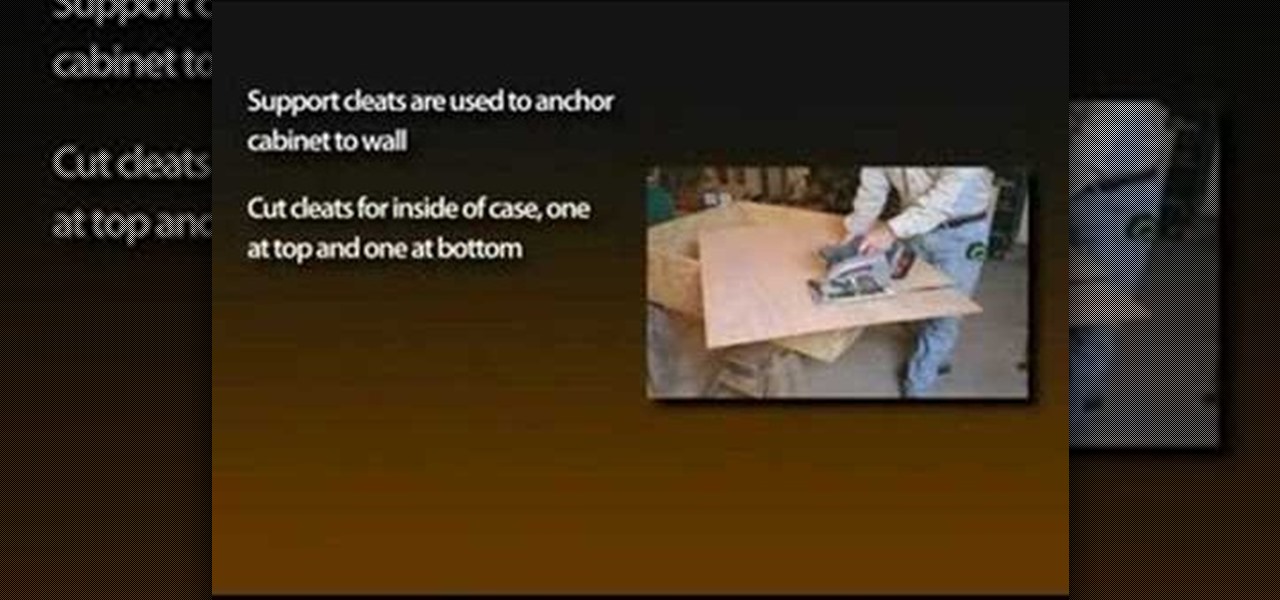
With the growing popularity of cordless power tools, it's extremely easy these days to accumulate a lot of portable tools, and when you add in quality corded tools, such as circular saws, routers, planers and air nailers, you can end up with a pretty hefty investment. These same tools are the first to “walk away” in a theft. Left lying around a shop or garage, they can also be somewhat dangerous for youngsters. A locking cabinet not only provides a secure place, but protects the tools as well...

Women's self defense strikes are extremely valuable in a world where women are attacked everyday. Learn self defense strikes, kicks and punches with tips from a martial arts expert in this free self defense video series.

Learning American sign language is valuable for anyone who is deaf or has dead friends and family. Learn how to sign words for emotions in American sign language with tips from an audiology expert in this free sign language video series.

Orchid care isn't as difficult as you think, and to discover the orchid care secrets, Meghan Carter visited award-winning orchid breeder Dick Wells. There she discovered the best technique for growing orchids.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

A Russian augmented reality startup wants the next frontier in real estate to be augmented reality estate.

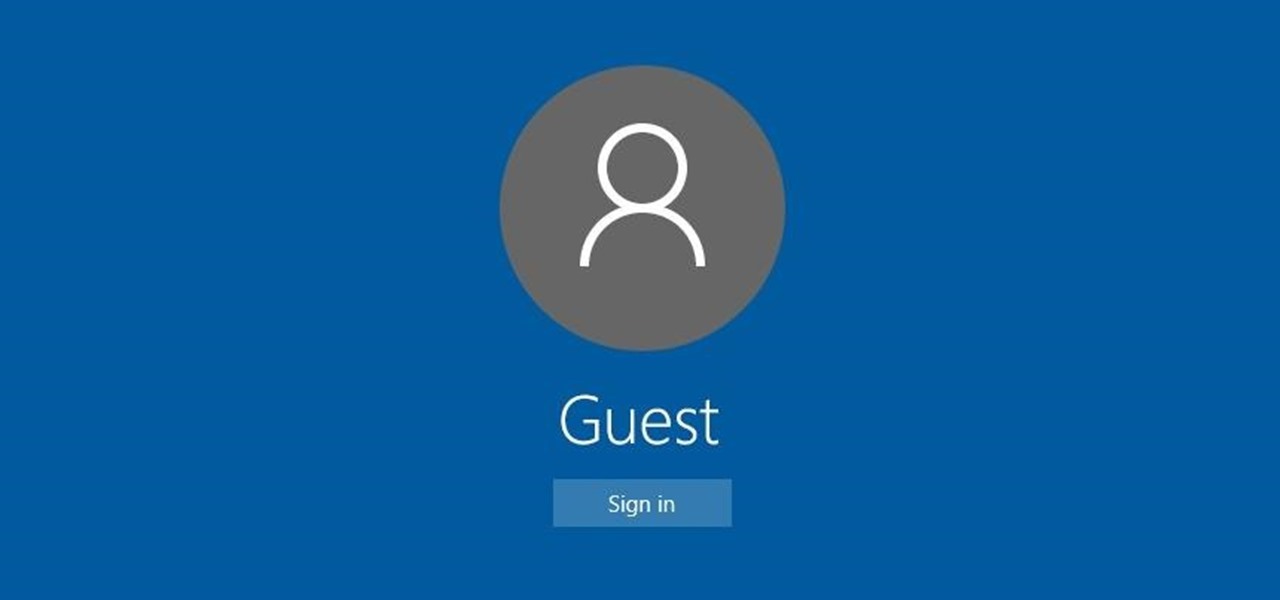
For reasons unknown, Microsoft decided to change the way the Guest account feature in the new Windows 10 operating system works. In previous versions, the Guest account feature allowed you to set up a limited account for other users so they don't have access to your important documents and settings. Now, the process requires assigning an email to a new account and configuring share settings.

There are countless ways in which you can turn your love of tech and coding into a full-fledged career — from developing apps and websites as a freelancer to working in the IT departments of small startups or major tech companies. But one of the best ways that you can put your programming skills to good use is to join the increasingly important world of cybersecurity.

Whether you live in foggy California or icy Massachusetts, you've more than likely struggled with a cloudy, vision-impairing window that makes even the shortest commute impossible.

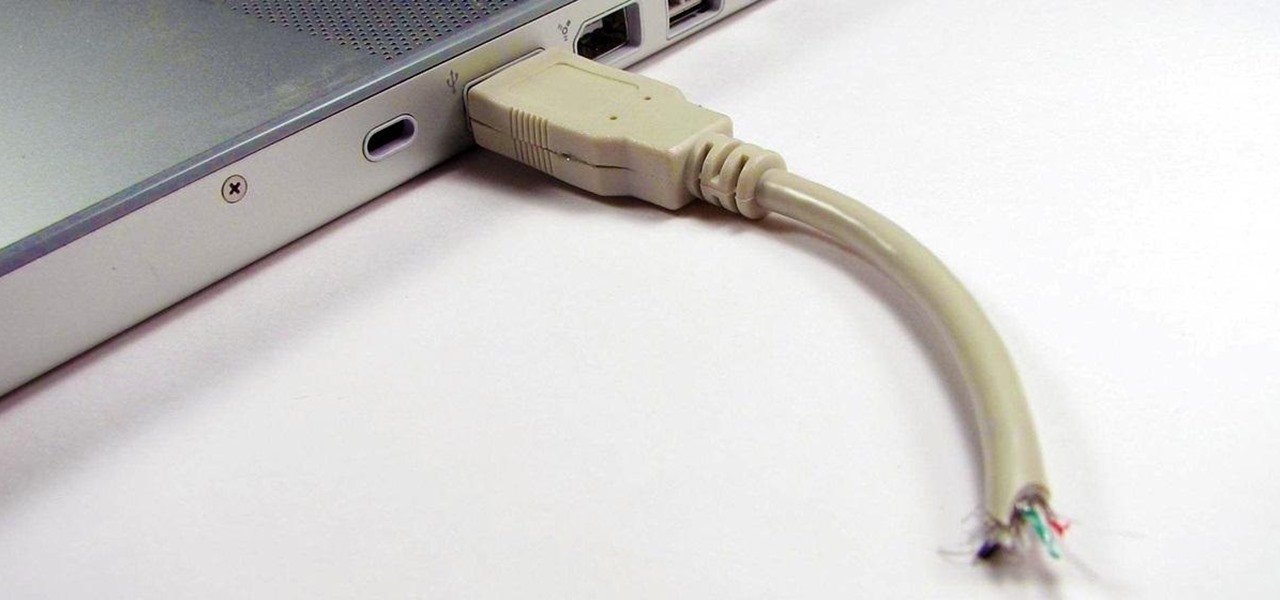
Having a flash drive is more or less a must, but the biggest downside is that they often get stolen, and it's not hard to figure out why. They're small, so they easily fit into pockets, and a lot of people store valuable information on them. Want to pretty much guarantee no one takes yours? Disguise it as a broken USB cable like Windell Oskay of Evil Mad Science Labs so it just looks like a piece of junk to would-be thieves. The materials are pretty simple: a flash drive (the smaller the bett...

If you saw my last tutorial on retiring early and wealthy, you now know how anyone can invest a small amount of money over the course of their life, and by exploiting compound interest, achieve an extremely comfortable and easy going retirement. In Part 2, we are going to dive into something a little more risky: Tax liens.

If you work in the film industry, are currently in film school, or have aspirations of being involved in the movie making process in some way, shape or form, you're probably very familiar with a certain set of books published by 411 Publishing that are commonly referred to as the "production bibles". If you live in the Los Angeles area, LA 411 is a valuable source of information when it comes to fulfilling your production needs. And if you're in New York, the NY 411 book is just as crucial fo...

In the dojo, what ISN’T said is often as important as what IS said. To most of us who’ve been raised in the USA, the reticence we encounter in the dojo can be off-putting. American society is very “content” oriented. Our legal contracts, for instance, run for pages and pages. Everything needs to be spelled out. In “context-oriented” societies there is far less reliance on such a literal approach. Much more importance is placed on the relationship between the two parties entering into an agree...

A wise old man once said, "Random best comes in threes". True story, somewhat. The elusive Flicker-Wiper:

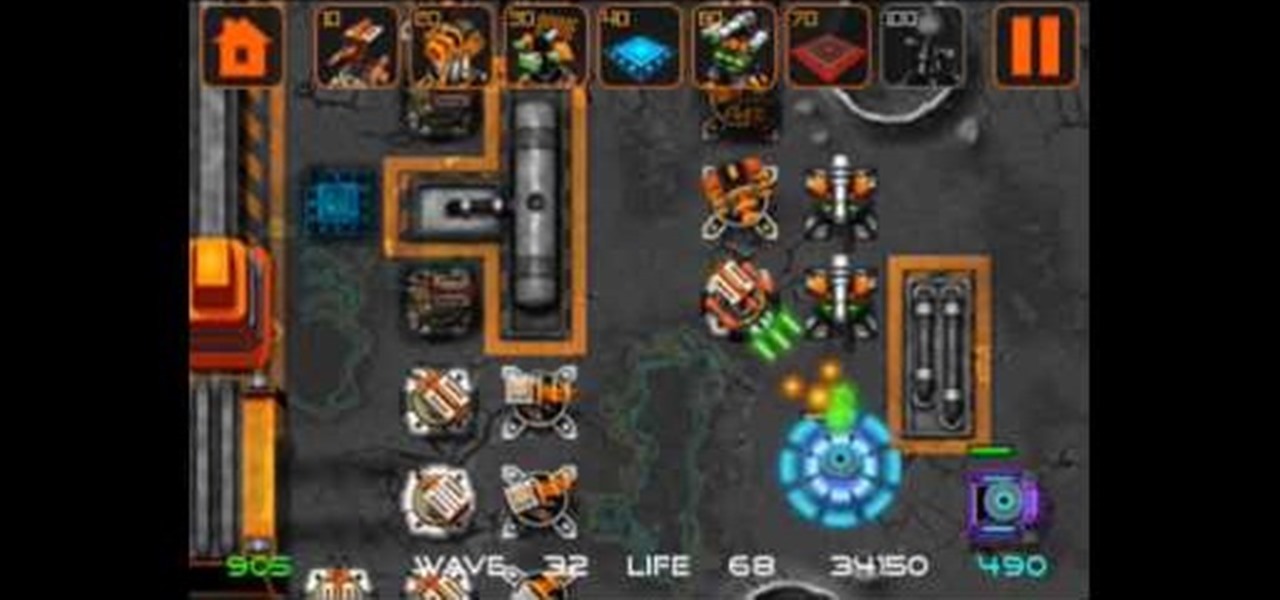
Need a new iPhone app? Check out Comets and Craters, a new iPhone tower defense strategy game. These ten video tutorials cover all of the gameplay troubles you may have. Steve explains the features and gameplay to help you get the most out of playing Comets and Craters on your Apple iPhone. For those more seasoned Tower Defense players, the video's also provide some insight regarding scoring, upgrades, plus Tower and Enemy capabilities.

Need a pinata for Cinco De Mayo or special occasion? This week Meg of Decor It Yourself shows you how with some simple house hold materials. Piñatas are a fun Mexican tradition, and are as easy to make as any paper mache project. Check out this how-to video to get ready for your next fiesta!

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

Want to learn a valuable skill? Well, just watch this video tutorial to see how to cross one eye or speak with an echo.

At a very early age, I would go on summer camping trips. I remember every night being handed a pack of sparklers that were my own, to swing around wildly, which gave me many valuable life lessons on cause and effect.

Do you think you are tone deaf? If you have trouble staying in key, or feel like you just can't get the rhythm, check out this video for advice on how to harness your inner songbird.

Cars are expensive to buy, replace or repair. Check out this video and learn how to avoid the most statistically dangerous parking areas. There is no guarantee that no one will touch your vehicle, but by take precautions you are much less likely to be targeted.

You've boxed up and shipped all your other possessions for the big move and all you're left with is the little issue of how your getting your car there. There are companies out there that will ship your car to you, just make sure your car is prepped for the journey.

Internal linking is a valuable way to improve search engine optimization on your website or blog. This component of organic search engine optimization we going to focus on web copy threading.

There're plenty of great ways to get traffic, especially this off-site optimization technique using classified ads to point website traffic back into your site itself.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

In today's data-driven world, being well-versed in Big Data and analytics can help land an exciting and high-paying career. Whether you're interested in working for a major tech company or pursuing freelance work in development, you need to have a thorough understanding of the latest and greatest platforms in analytics if you want to succeed.

The COVID-19 pandemic has hit everyone hard. With over 36 million American workers filing unemployment claims, finances are at the front of everyone's mind. Understanding your accounts has never been as important.

If you're trying to learn a new skill, you wouldn't want to waste your time learning from someone with sub-par experience. No, you'd want to learn from the very best of the best to ensure you're getting a quality education.

There is so much information in the world that trying to make sense of it all can be daunting. That's where data analytics comes in. By learning how to inspect and model data, you can take large data sets and transform them into highly valuable information that can take any business further.

To promote Battle of Azeroth, the latest expansion for the World of Warcraft franchise, Blizzard Entertainment has conjured a Shoppable AR Lens that is now available in Snapchat's app carousel.

If you have a substantial collection of POGs, the disc-collecting game from the 1990s, squirreled away in your basement, then a new augmented reality app may give you a reason to dig them up.

Back in November, Essential opened the Android Oreo Beta Program for all users of their PH-1 flagship. We even wrote up a full guide on how to install the beta, if you're interested. They followed the Oreo beta with a Reddit AMA, where they mentioned the second beta software would arrive very soon. That update has just gone live, so you can grab it right now in a few easy steps.