Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

The legal drama surrounding Chinese startup Nreal and Magic Leap continues, and now we finally have an update.

I go back and forth between two home screen apps: Nova Launcher and Action Launcher. While I prefer the aesthetics of Nova, I like Action's Quickpage feature since it puts some of my favorite apps just a swipe away. But now, I've found a way to replicate this feature on Nova (or any other launcher), and it works even better.

As a root user, you have a lot of responsibilities to make sure your phone stays secure. Expectedly, some things may slip through the cracks. Remembering to check which apps have been granted root access is extremely important. All it takes is one bad app, so it's good to learn how to avoid that at all cost.

Augmented reality jigsaw puzzle game PuzzlAR: World Tour, formerly only available on mobile devices, has been given a major upgrade via a new version for the Magic Leap One.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

I'm here at the annual AWE event in Santa Clara, California, and the venue is just as packed, if not more so, than last year.

In case you thought the long and unfortunate story of ODG was over, hold on, there's one last chapter to tell.

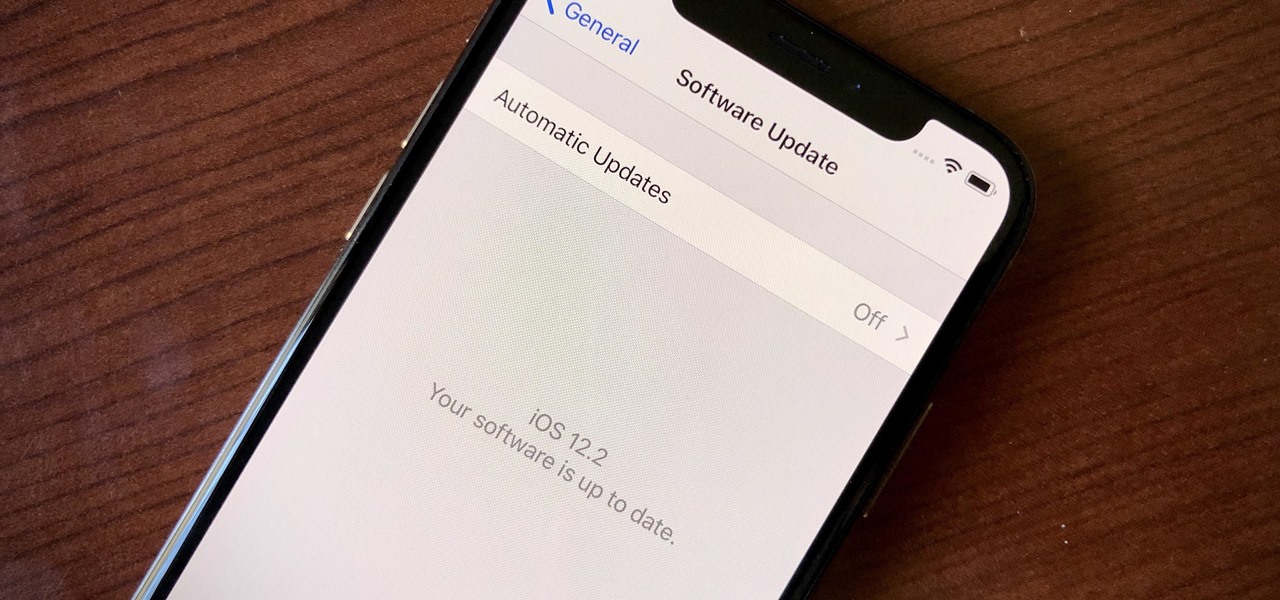
Apple just released the sixth beta release for iOS 12.2 today, Monday, March 18. Just as expected, the update to the developer version dropped just past 1 p.m. EDT (10 a.m. PDT), and comes with new changes and features from iOS 12.2 beta 5 and beyond, including a new warranty status in the "About" page in Settings.

It's easy to forget just how cool face filters are. Augmented reality has come a long way, and apps like Instagram now offer a suite of impressive effects to play with, but some of the best ones aren't easily found. There is a treasure trove of exclusive, custom face filters that are unavailable to the general public, but not at all inaccessible — you just need to know the trick to getting them.

Beloved toy maker Lego is returning to the realm of augmented reality, this time with an experience that explores supernatural fun.

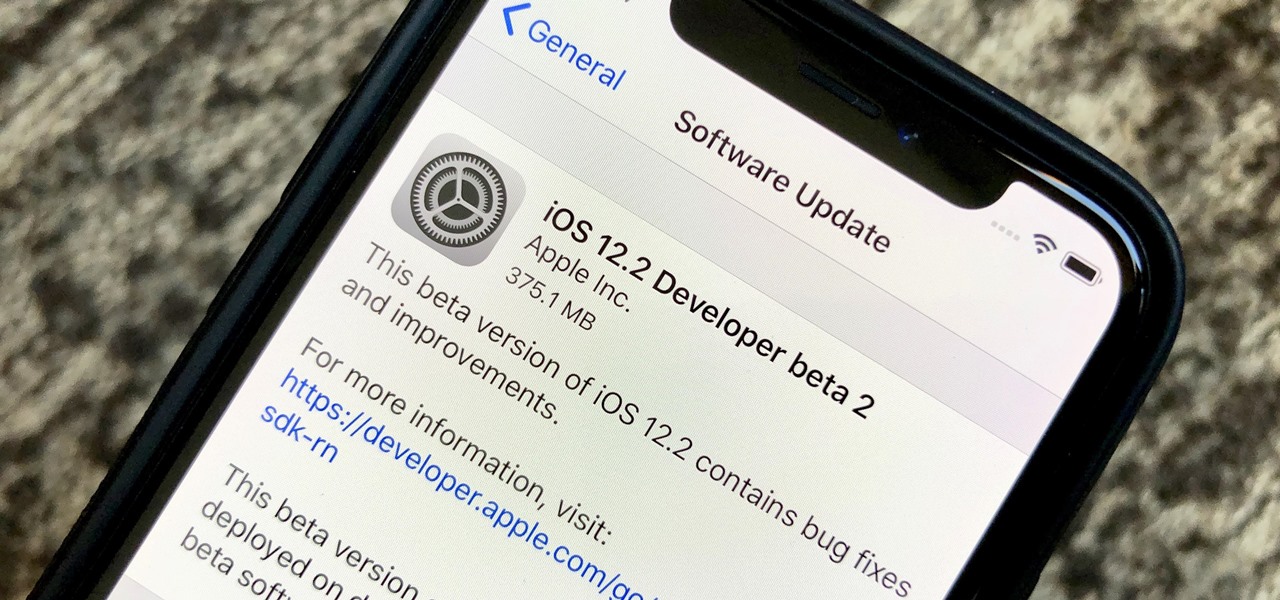
On Monday, Feb. 4, Apple released the second developer beta for iOS 12.2. The update features bug fixes to users running iOS 12.2 beta 1, as well as four new Animoji for Face ID devices. Developers are strongly encouraged to update their iPhones. It's unclear at this time whether the update includes a fix for the Group FaceTime bug discovered last week.

If you've blocked out your calendar to watch the NHL All-Star Game this weekend, then you might be excited to know that USA Today has given its readers the opportunity to meet Washington Capital's John Carlson in augmented reality.

One day after the official release of iOS 12.1.3, Apple released the first beta for iOS 12.2 to developers. The software appears to be the first in some time to be a major update. Apple's last beta cycles included 12.1.2 and 12.1.3, incremental updates to iOS 12.1. Now, we've entered a new version of iOS 12 entirely, hopeful for new features.

I love finding new artists on Spotify to listen to but hate when musicians I don't like keep popping up in recommended playlists and radio stations. For the longest time, there was nothing you could do about it, but now, Spotify lets you block specific bands and singers from ever playing again.

Among a crowded field of AR cloud companies aiming to power the future of augmented reality by creating a world of persistent holographic content that lives in a cloud, accessible across devices and accounts, Ubiquity6 is hoping it has found a way to differentiate its platform.

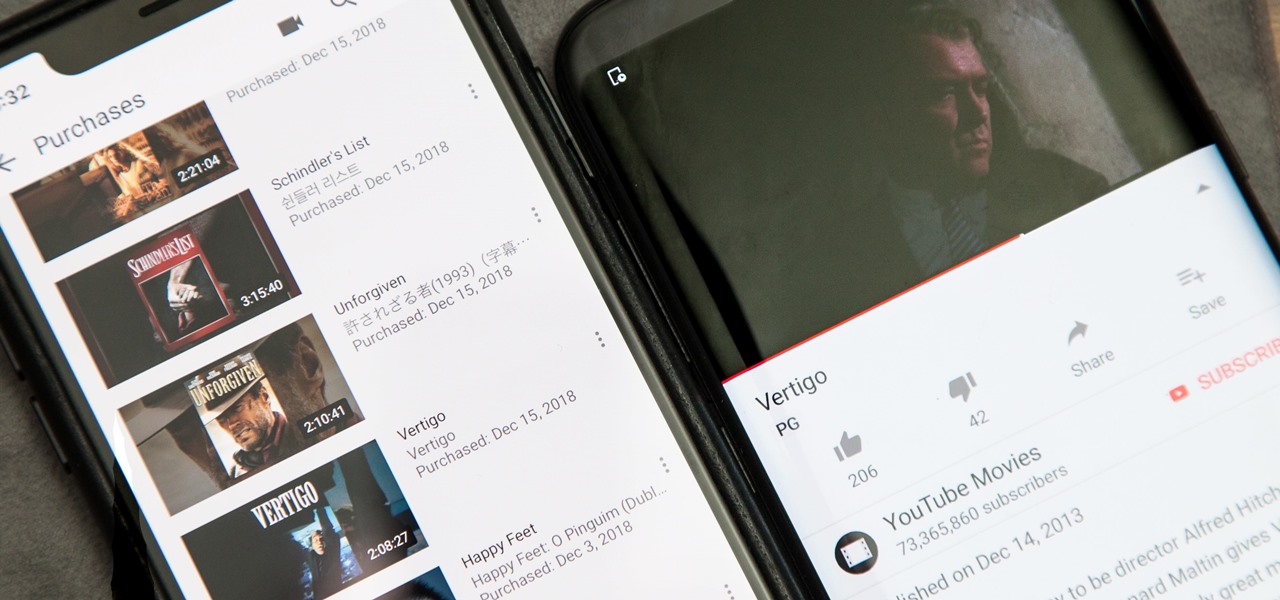
Owning digital movies has many advantages over physical discs, such as easy access and a variety of online stores you can turn to for good deals. There's Prime Video, iTunes, Vudu, and the list goes on. However, this leads to fragmented video libraries, unlike DVDs and Blu-rays which can be stored together. Surprisingly, YouTube is one app that can help consolidate your collection online.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

With CES in full swing, it seemed like Magic Leap would have little to announce at the major tech event, but it turns out that one of its partners has weighed in with a rather substantial update regarding the company.

Magic Leap continues to launch new AR apps on its fledging app store before the door closes on 2018, and this time the app is a sequel from a veteran VR developer and early Magic Leap development partner.

As highlighted in our article on how to enable Google Now in Action Launcher, doing so takes away the Quickdrawer. This effectively ruins one of the more beneficial features of Action Launcher, making it a tough choice between the two options. So I looked for a solution and found one that works.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

In 2017, Google introduced a new feature called Fast Pair. This made discovering and pairing Bluetooth devices completely stress-free, as it eliminated the need to fumble through settings. Google has now made it even easier, so Fast Pair is a must-have feature for your next headphones.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

Apple's latest mobile operating system for iPhones, iOS 12, was released to everyone Monday, Sept. 17, and it's the same exact build that developers and public beta testers received as the "golden master" on Sept. 12, the day of Apple's 2018 special event. Install it to start taking advantage of the 100+ features iOS 12 has to offer right now.

While we've seen Snapchat apply sky segmentation to AR content, the makers of the Blue Sky Paint app have applied similar capabilities to create and share airborne art.

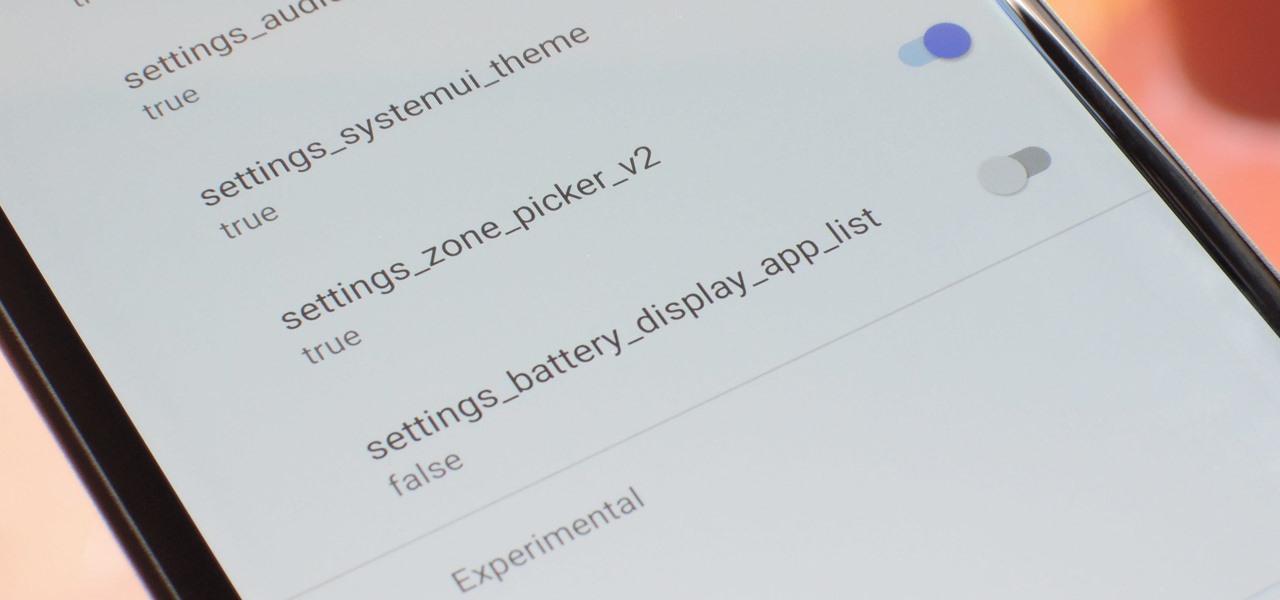
With every new Android update, hidden features are lurking under the surface. Google hides these options to prevent unnecessary tinkering by average users, leaving them in place for power users to discover. These secrets range from silly to really useful, with the latter opening up new ways to manage your phone.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

Attention all Redditors: Between June 14 and June 18, Reddit experienced a data breach. The popular website claims it discovered the breach on June 19 and has since made the necessary moves to contain and eliminate the threat. Unfortunately, there isn't much they can do about the data was that accessed and stolen — your user data.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

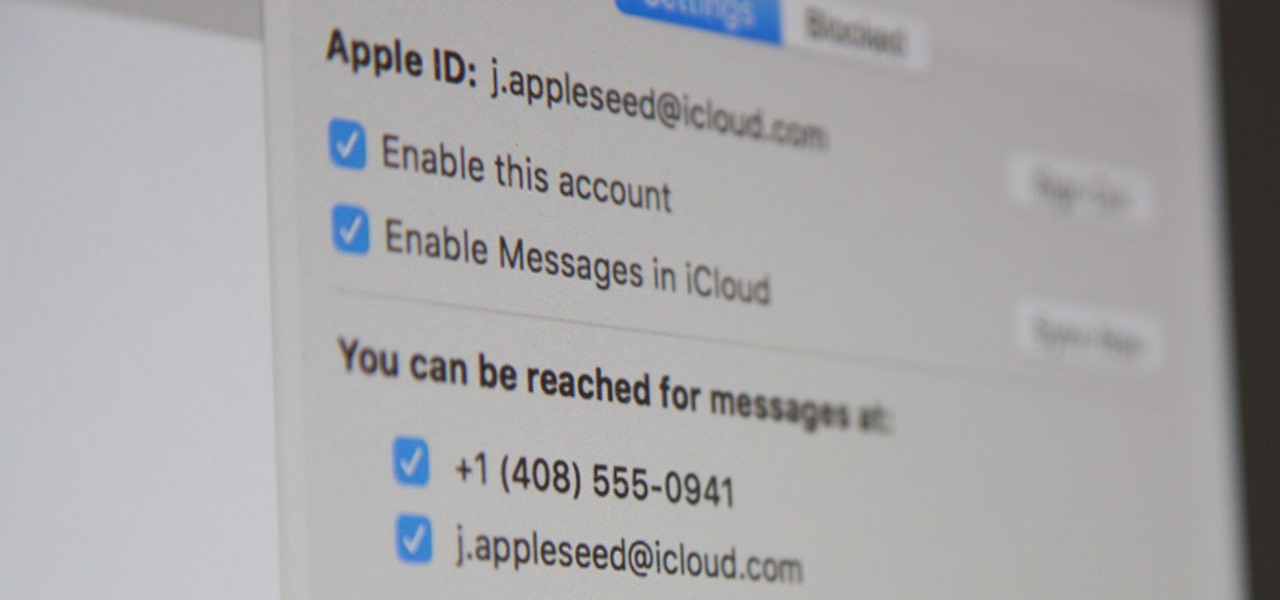
Apple pushed out iOS 11.4 on May 29 to iPads and iPhones, which included the long-awaited Messages in iCloud feature. The company did not release macOS High Sierra 10.13.5 at the same time, limiting the usefulness of being able to sync messages in the cloud since 10.13.4 is not compatible with Messages in iCloud. But three days later, Apple finally released macOS 10.13.5.

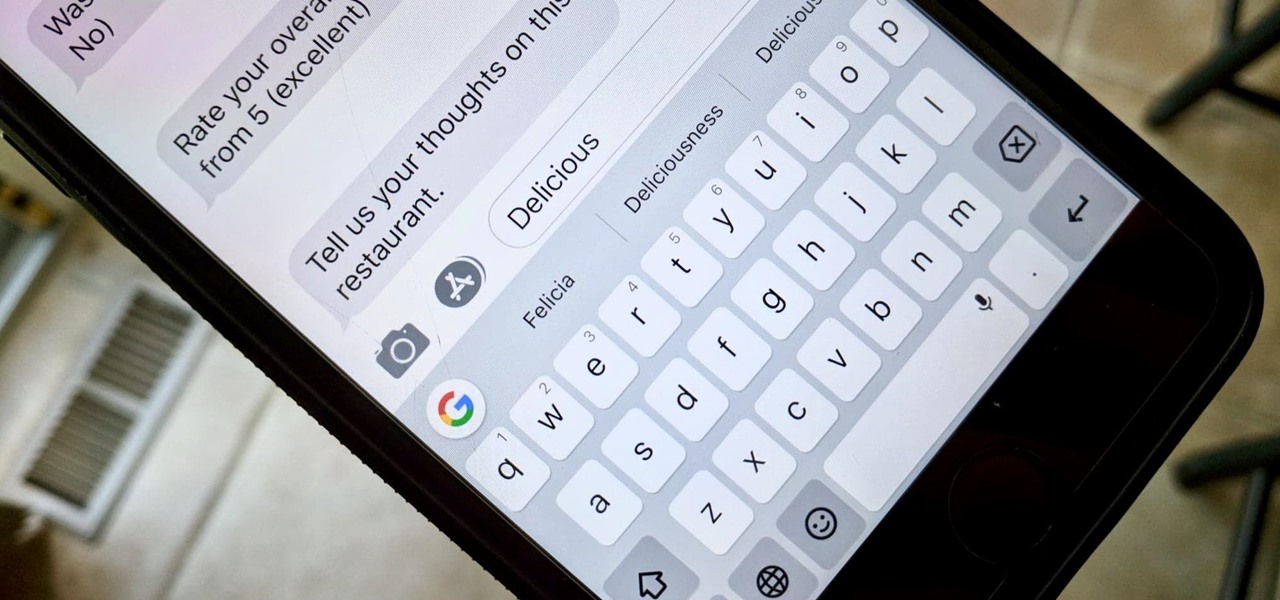
Predictive text is a common feature in most mobile keyboards these days. However, many times, its guesses are way off, sometimes hilariously so. As absurd as it can be, predictive text can also continuously suggest the same wrong word over and over. Thankfully, Gboard offers users a way to quickly remove these suggestions for good on both iOS and Android.

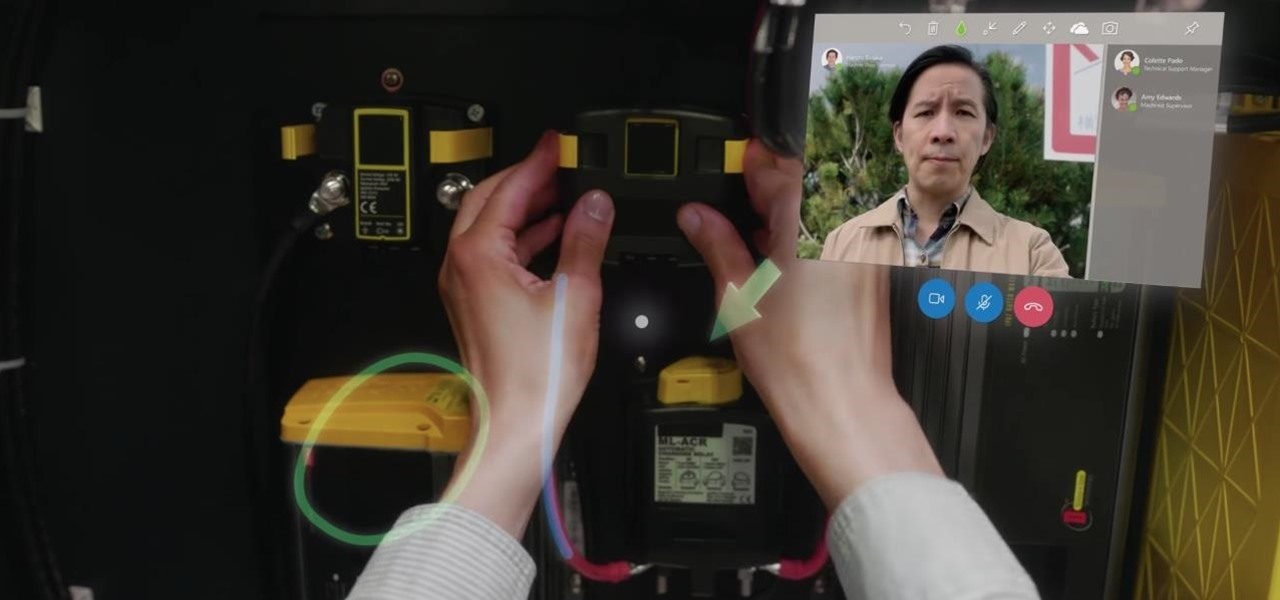
On Monday, at its annual Build developer conference, Microsoft revealed two new apps for the HoloLens apps.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

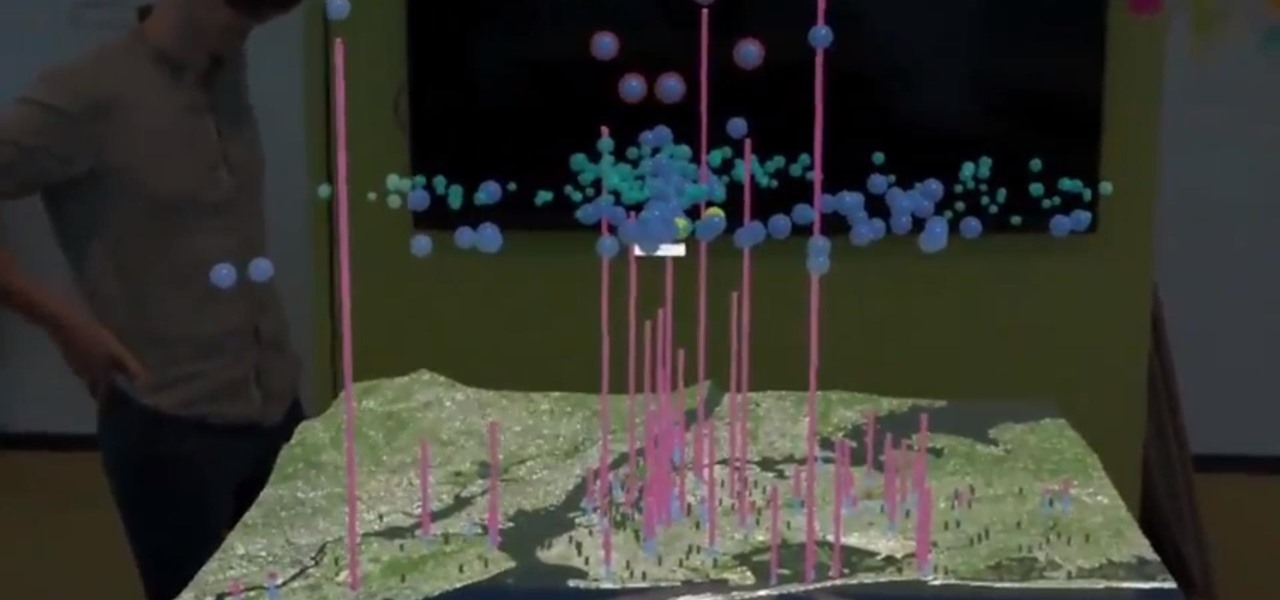
As the week of the Game Developer's Conference hits the mid-point, we've already had some major announcements hit the AR space. The specific timing of these announcements are thanks in part to a conference within a conference called VRDC, aimed at VR, AR, and MR developers. And while the week is hardly over, the announcement that is still having a big effect on the developer population is the reveal of the Creator Portal for the long-awaited Magic Leap One device.

The cosmetics industry faced a rude awakening on Friday as beauty behemoth L'Oréal gobbled up ModiFace, one of the leading providers of augmented reality technology to the cosmetics industry (price details for the acquisition were not disclosed).

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

This month, the power of artificial intelligence will be coming to more augmented reality developers as a leader in the game and 3D software development space and a major force behind the current school of cloud-based AI have officially announced a new partnership.

Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the user.

With the Super Bowl just days away, it seems appropriate to draw parallels between football and the professional sport of technology business, or, more specifically, the augmented reality segment.