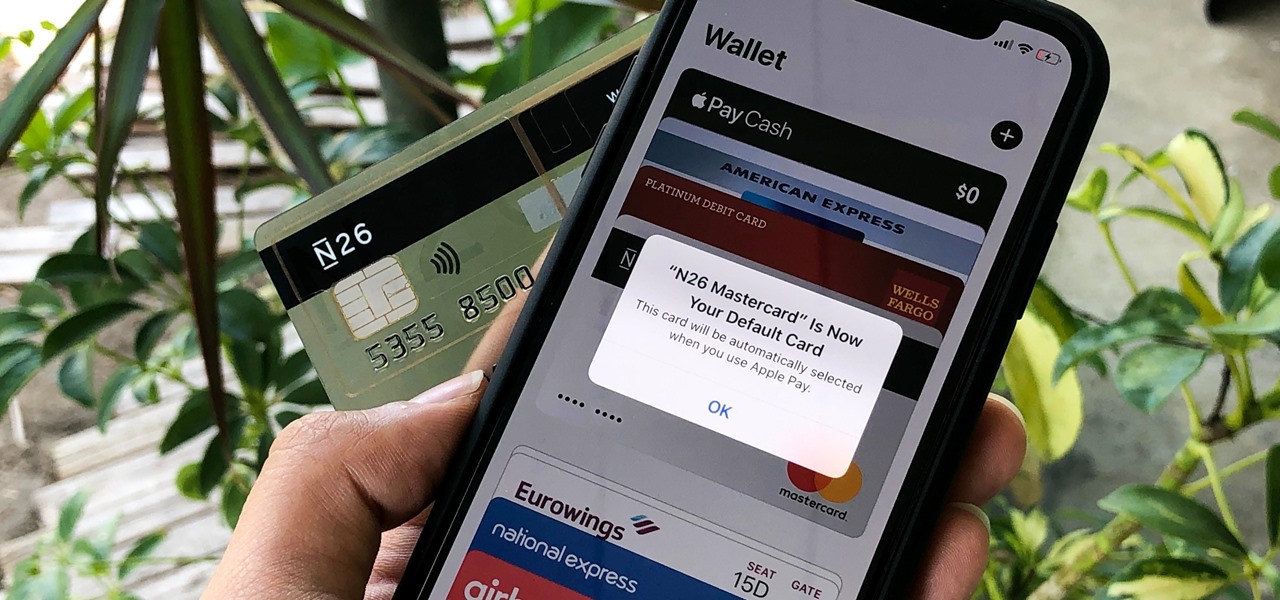
Using Apple Pay in stores to make purchases is as easy as holding your iPhone near the NFC reader and authenticating with Face ID or Touch ID. That method uses the primary payment card in Apple Wallet automatically, and your primary card may change from week to week based on your spending, so you'll probably need to change it periodically.

Estimates say that there are roughly 441 million Apple Pay users in the world, but with almost a billion active iPhones in the world, some of you have yet to jump on board the digital payment method. But once you're ready — or if you just need a refresher — adding your debit and credit cards to Apple Wallet is simple.

Sure, it's the giving season, but sometimes you've just got to treat yourself to some cosmetics. If you're shopping at Walmart, L'Oreal just made that a shade easier when shopping for Garnier hair color products with an assist from Google Lens and the Modiface AR platform.

Augmented reality already seemed like the ideal technology to advertise for a movie based on the premise of being sucked into a video game world the first time around. For the sequel, how about two times the immersion?

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

Augmented reality seems to come into its own in museums, where audiences are ready and willing to try out new immersive tech. Now, that tech-powered palette is about to get a little larger.

After you've spent your Thanksgiving afternoon working through that turkey, mashed potatoes, and three different kinds of pie, you might find yourself heading to the mall to claim some unbeatable Black Friday discounts on iPhone 11, 11 Pro, and 11 Pro Max. You don't have to go in blind, though. Check out our guide below to make sure you're saving as much as possible on the iPhone you really want.

I've just recently hopped on the AirPods bandwagon, and I can't see myself ever going back to the wired EarPods that Apple includes with every iPhone. The only issue is that I paid full price, but you don't have to with 2019's Black Friday deals, some of which are happening right now.

The week in AR business news started out with a bang with two bombshell reports that cast a shadow on the AR industry as a whole.

Following up on the initial tease over three months ago, Snap Inc. is finally letting the public get its hands on its new Spectacles 3 wearable device.

It takes confidence and guts to pull off attractive and yet adequately frightening Halloween makeup as an adult.

Big-box retailer Target has been on a bit of an augmented reality advertising shopping spree via Snapchat lately.

Google has started to release a Go line of Android apps. These apps offer a minimalistic version of their major app counterpart. So far, we have Go versions of Maps, Photos, Gmail, and more. Who are these apps for and why would you want to use them? Here's a quick overview of Google Photos and Gallery Go.

As paper forms become a thing of the past, it's becoming commonplace to fill out contracts, rental agreements, waiver release forms, and non-disclosure agreements online. You can easily fill out forms on your laptop, but how can you best do this using your iPhone or Android device?

Following in the steps of Snapchat, Instagram, and YouCam, another popular photo app has gotten into the virtual try-on augmented reality game.

Apple added "Announce Messages with Siri" with the release of iOS 13.2, and it came as a welcome surprise for me; I missed the feature from its initial run during iOS 13 beta testing. However, while users online gleefully showed off their newfound Announce Messages with Siri capabilities, I was frustrated to see that I didn't have the setting, even though I just updated my iPhone to 13.2. So, what's the fix?

This time last year, Snap CEO Evan Spiegel and his company were faced with an erosion of its user base that cratered its stock price. This year, on the strength of Snapchat's AR camera effects, the company has reversed course. And that's why Spiegel tops the NR30, our annual list of the leaders in the AR industry.

The streaming content vision from Magic Leap recently underwent a quiet but major update, courtesy of AT&T.

When you think about it, isn't life just one big open-world RPG just begging to be conquered? We all have a set number of specific tasks or chores we must complete every single day like clockwork. Sometimes, these items on our to-do list can become tedious and cause us to lose motivation. What if you could take those tasks and turn them into something awesome instead? Now you can.

Imagine sitting on your patio, scrolling through your phone's photos, reminiscing about the past. Now imagine being able to see those photos floating in the air, at the exact vantage point from where they were taken a year ago.

Increasingly, cutting-edge platforms like blockchain technology and augmented reality are overlapping, forging new digital frontiers that promise to change the way we interact with the virtual and the real world.

Phone specs get better and better each year, and multiplayer mobile games are right there with them. Instead of playing solo, jump into some real-time gameplay with co-op and player vs. player modes, and battle friends, family, and strangers from around the world. But which multiplayer games are worth your time on Android or iOS?

Smartphone hardware surpassed the most popular portable game devices long ago in all but one category — control. Your iPhone is more than capable of running impressive, fully-realized games, but touch controls only go so far. That's why it's so exciting that Apple has added support for PS4 and Xbox controllers with iOS 13.

Now that we've had our hands on the Magic Leap One for almost a year and early adopter developers have had the opportunity to publish apps for the AR headset, it's time to see how it stands up against the rigors of a day at the office. We did just that, and we wrote about it!

One of the best ways to dig into a website and look for vulnerabilities is by using a proxy. By routing traffic through a proxy like Burp Suite, you can discover hidden flaws quickly, but sometimes it's a pain to turn it on and off manually. Luckily, there is a browser add-on called FoxyProxy that automates this process with a single click of a button.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

With the third season of Netflix's hit series Stranger Things set to debut July 4, it's time to crank up the hype machine, this time, in augmented reality.

Ever since iOS 7, you could ask Safari on iPhone to show you the desktop version of a website, and in iOS 9, it became even easier to do. However, it's always been a hidden feature, something you wouldn't know is there without reading articles or tips online telling you what to do. Apple's iOS 13 update shines a light on it so everyone will know it's there, ready to use.

The natural marriage between fashion and augmented reality is charging onward, but not just from the major brands we already know about.

Many of us know that you can make a few bucks from Amazon by helping the company sell its wide array of products, but now there's a very different way to make a buck with the company, and it involves 3D technology.

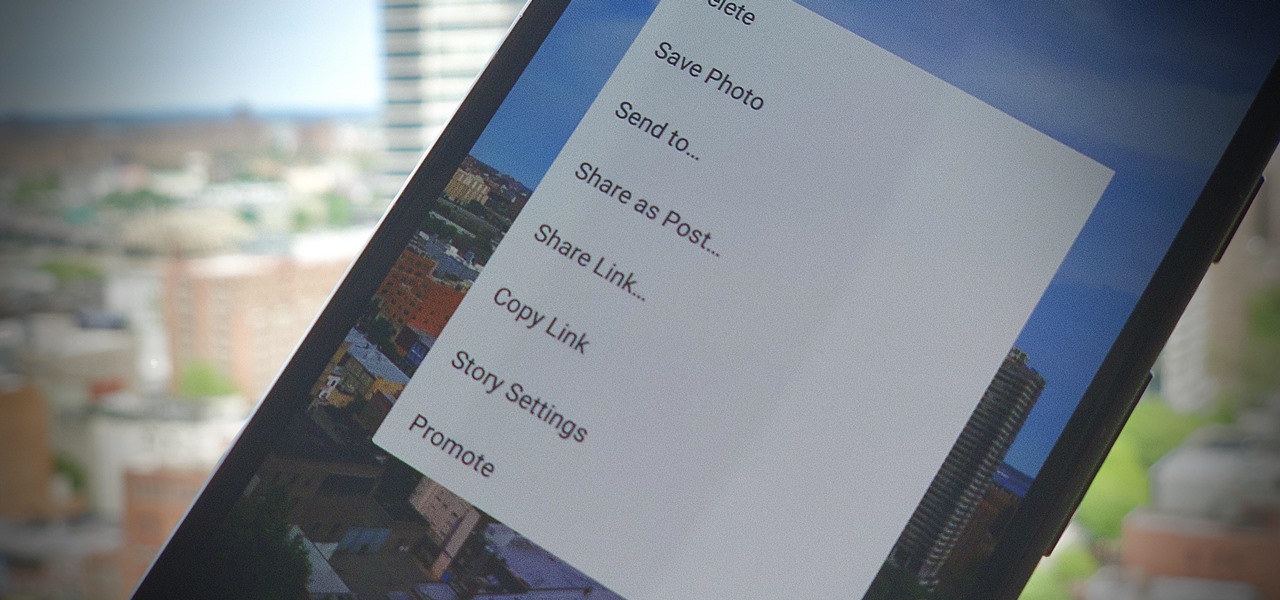
On Instagram, it's all about the sharing, but not all sharing is equal. Take stories, for example. Up until recently, stories couldn't be easily shared outside the Instagram bubble. Now, Instagram lets you share a convenient link to a part of your story or your entire story on any other platform — text, email, social app — pretty much anywhere.

With $100 million in grant funding already available to developers via its MegaGrants program, Epic Games is sweetening the pot with some gear for Magic Leap developers.

There are only three more episodes of Game of Thrones left before the saga is over, but Magic Leap is capitalizing on the series' popularity while it still can.

Magic Leap's business strategy for bringing augmented reality to the mainstream has become even clearer via its latest funding round.

While Magic Leap turned heads at the Game Developers Conference with AR experiences at the Unity and Unreal Engine booths, news broke that the company was the winning bidder for ODG's patents.

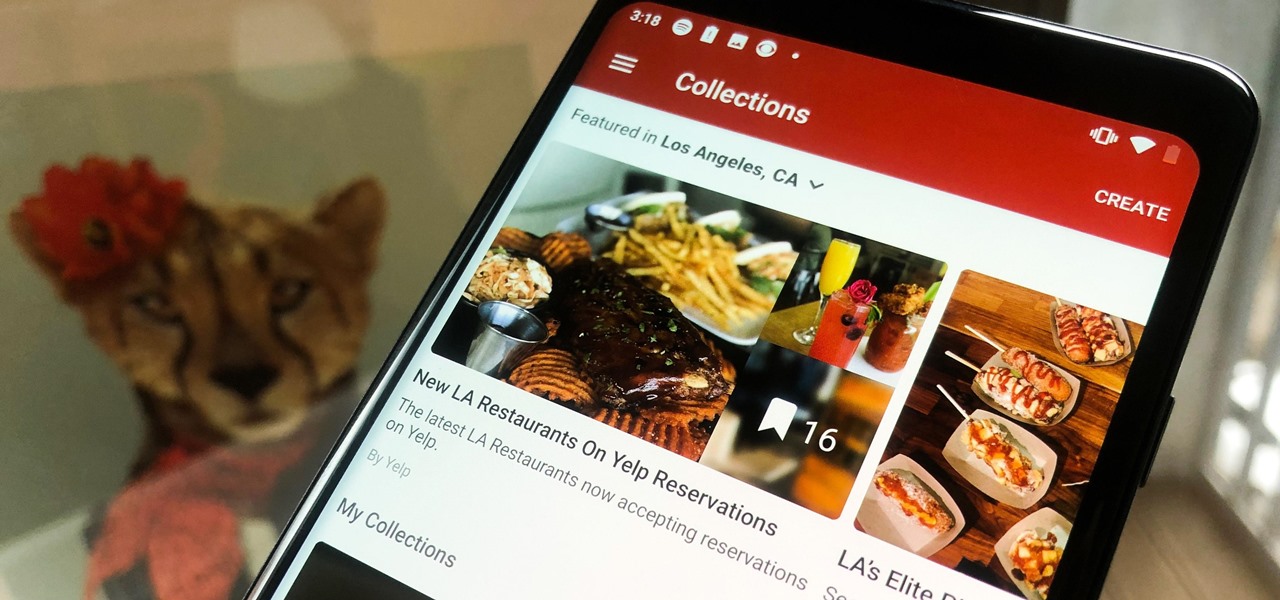
In the past, if you stumbled upon a Yelp listing you liked, you could bookmark it and check it out later on your profile. You can still take advantage of this feature in the mobile apps, but it's more refined now than it ever was thanks to Collections, a feature Yelp first added back in May 2018. You get more power over organizing, accessing, sharing, and discovering favorite businesses.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

As Magic Leap continues to spread its influence in the US with the help of wireless carrier AT&T, the augmented reality startup is also working its way into East Asia.

News junkies who own the Magic Leap One received some good news on Thursday, as CNN has published an app for the headset to display the network's news coverage in augmented reality.