Samsung devices may dominate the Android market, but that doesn't mean everybody loves TouchWiz, the user interface on all of their smartphones and tablets. It's difficult to modify, comes with lots of bloatware, and isn't much to look at, to say the least.

Who doesn't enjoy sitting down to a nice dinner with a cocktail in hand? After a long day, a drink is a great way to unwind. Yet your favorite spirits can do more than just help you relax after work. By utilizing alcohol in the kitchen, you can enhance everything from how food tastes to your health.

T-Mobile continues to make waves in the U.S. wireless market behind CEO John Legere's UnCarrier program. At the latest installment in a series of industry-challenging announcements, Uncarrier 5.0 unveiled Test Drive. The new program is set to allow would-be customers to try out the "latest generation" iPhone for seven days on T-Mobile's network without any financial commitments.

Apple has released the 2nd beta of iOS 8, exactly fifteen days after the first version was unveiled at WWDC and subsequently released to developers. I've already shown you some of the new features of iOS 8, like location-based app alerts, randomized MAC addresses, hidden Safari tricks, and a slew of new things in the Messages app. But if you've had the chance the explore iOS 8, let's go through some of the changes that Apple has made to the latest iteration of its mobile operating system.

Boozing it up at work might have been okay back in the days of Mad Men, but today, employers prefer that their workers stay sober. What you and your bosses probably don't know is that a little drinking on the job can actually increase your creative capacity and problem-solving skills. Alcohol Can Enhance Your Creativity at Work
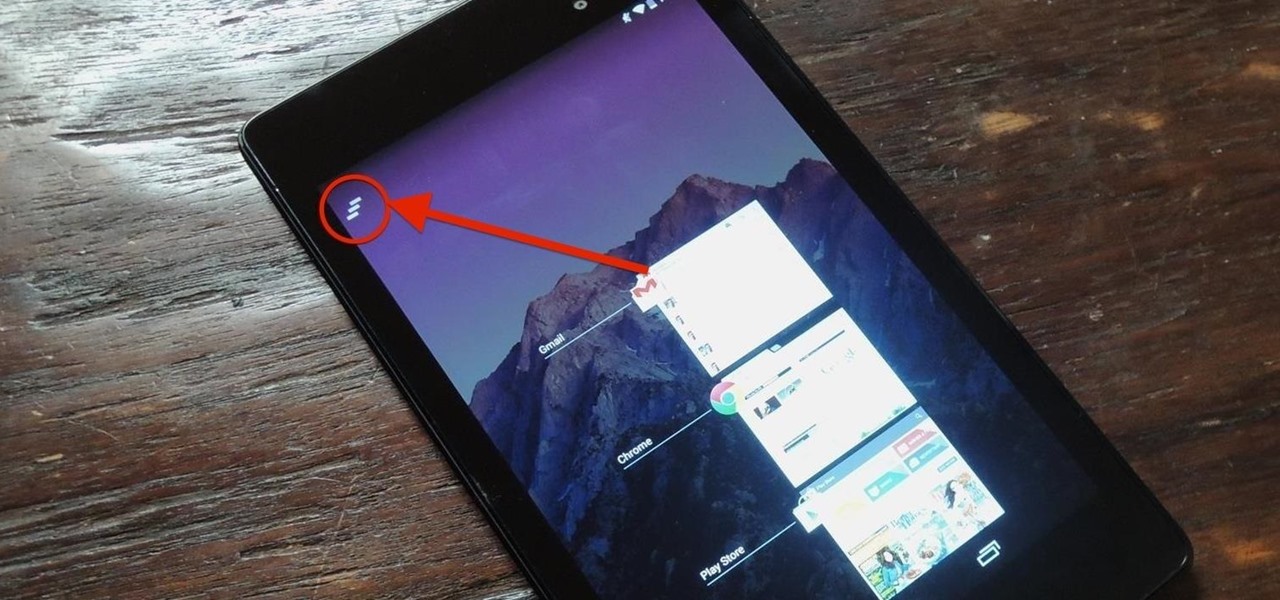
Unlike the Galaxy S4 and other Samsung devices, the Nexus 7 doesn't have a Clear All option in the recent apps menu. It's a highly requested feature, as it cuts down the time required to go one-by-one swiping each individual app (you can't swipe away multiple ones at the same time).

Ever since Android 3.0 Honeycomb, Google has been trying to push phone manufacturers to do away with physical menu buttons. Samsung has been one of the lone holdouts, retaining the menu key up until the Galaxy S5, where they finally replaced it with a "recent apps" multitasking button.

Unless you've been living under a rock with no internet connection, it's safe to say that you've heard of the Heartbleed flaw that allows practically anyone with the right knowledge to steal your personal information, such as passwords, credit card numbers, and e-mail addresses using OpenSSL.

When it comes to blocking unwanted calls, your Android device comes stocked with a native blocking feature that allows you to reject certain phone numbers. That being said, the native blocking feature on the Samsung Galaxy Note 3 isn't the prettiest or the smartest, with its non-obvious setup and lack of features.

Popcorn Time is an app that streams movies directly from torrents on to your computer, and it's seen its fair share of publicity, being lauded as a free Netflix alternative and chastised as an illegal file-sharing network.

I love my status bar. Not only does it tell what time it is and how much battery juice is left, but it gives me cellular connection info, text alerts, and app update notifications. However, one thing is does not give me is customization. Since you're looking at it all the damn time, why not personalize it?

Confirming a lot of what we already knew, now we have a physical walkthrough video on HTC's new flagship, the M8. Or, maybe the "New HTC One", but let's hope that's not the name of the final product. Before we get to the video, here's what we already know:

With the the general computer users understanding of Information security rising (at least to the point of not clicking on unknown links), and operating system security getting better by default. We need to look for new and creative ways to gain a foothold in a system.

If you're spending hours on your phone playing games like Angry Birds and Candy Crush Saga, or posting online to Google+ and Pinterest, you're probably being spied on. The latest releases from NSA whistle blower Edward Snowden reveal that the National Security Agency, and its UK counterpart, GCHQ, are mining the ad networks utilized in these apps to collect a trove of information on you.

So, you find an interesting article online, but there’s something you don’t quite understand about it and instinct kicks in. Open new tab. Go to Google. Enter keywords. Search. Find information. Understand.

Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.

This year's NFL playoffs have been nothing short of spectacular. With Super Bowl XLVIII coming up on Sunday, February 2nd, people are already gearing up for another classic showdown between the NFC and AFC, and this time it's the Seattle Seahawks versus the Denver Broncos.

I know that after seeing 8 Mile for the first time, you and your friends tried a few freestyles yourself. Nothing to be embarrassed about. As one person dropped the beat, you started your stuttering flow, and everyone else nodded their head. And for a second you probably thought you sounded pretty good, until the beat maker started coughing and threw you off.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

Let's get one thing straight: CyanogenMod is one hell of a ROM. They've got a great community, a great product, and getting it on your HTC One couldn't be easier with their CyanogenMod installer, which does all the hard rooting and bootloader unlocking for you.

Regular wallpapers are like so 2012. That's where live wallpapers come in, bringing your background to life like a static wallpaper never could, with colorful animations, customization, and even interactivity. I've already shown off some of my favorite interactive wallpapers, but these type of apps are released at a rapid pace, making it difficult to choose just one that best fits your needs.

For a photo- and video-sharing app based around privacy, Snapchat sure has a lot of security holes floating around. At one time, you were able to take screenshots of Snapchats in iOS 7 without the sender knowing, which is something that you can still do on rooted Android devices.

Like many other smartphones these days, your Samsung Galaxy S4 is built to handle multitasking like a pro. With a 1.9 GHz processor and 2 GB of RAM (specs comparable to laptop computers just a few years ago), this powerhouse of a phone can switch between apps with supreme ease.

Automation applications bring the future a little closer. If you've seen Minority Report or other futuristic sci-fi movies, the intrigue of having your electronics work independently is something we can all appreciate.

I could write about a new launcher everyday, because there are so many options out there for Android users, but one of my favorites it Everything Home. You probably have your own favorite, but what if you could actually use two launchers together, taking advantage of each one's awesome features?

Welcome back My sleepless army of young hackers, Everyone uses internet, right? So for this tutorial, i'll start with the basics and slowly we'll get to the UPD Protocol.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

Thousands of history files, cookies, other unwanted files stored in your system as logs and other formats. To manually check each one is difficult. New computers are too fast by processor behavior, after some times of working it comes to slow performance.

Have you ever heard the expression "Dress for Success" or "Clothes Make the Man"? When you're wearing a perfectly fitted designer shirt, something inside just shouts, "I look good" and when you genuinely think that, those feeling are radiated outward to all your come in contact with. That said, what kind of designer shirt are you interested in, a bargain basement discount, or one tailored made, outlining your best features?

There are definitely some very cool things about the new iOS 7, but it's also got plenty of downsides, one being the updated look of stock app icons. Apple drastically changed their glossy skeuomorphic icons for a flat, modern squircle look using their golden ratio grid.

If you're a Twitter user, it's a safe bet to assume that you've used a hashtag. On all social networking sites that have the capability, such as Instagram, Facebook, and Google+, the pound (#) symbol is used to mark and designate specific keywords or topics in order to make it effortless for users to connect with one another.

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

How much privacy are you getting as an AT&T customer? With the recent leaks confirming the National Security Agency's surveillance on AT&T users, and the ongoing trial of Jewel v. NSA, it seems not much at all.

With so many cloud storage services out there, many people are starting to keep their important documents online, especially when they know they'll need to view them when they're away from their computer.

Have a load of games you want to play, but don't want to be seen in public playing on your old school Nintendo DS system? Play them on your Samsung Galaxy Note 2!

Since The Guardian published leaked documents exposing the depth of the NSA's spying powers, many people who've never put much effort into protecting their privacy are finally starting to pay attention. Evidence of public opinion concerning PRISM can be seen from the rise in traffic for pro-privacy sites like DuckDuckGo to the petitions demanding that the program be scaled back or done away with altogether. Some would argue that you waive your right to privacy by signing the terms of agreemen...

I'm still amazed by all the things some people just don't know. Script-kiddies often refer to Metasploit if someone asks them how to hack a computer because they think there's simply no other way. Well here I am today trying to increase your set of tools and -of course- skills.

How can you tell if the pair of Ray-Ban Wayfarer sunglasses that you are about to buy online are not a fake? Follow these 9 simple steps to verify the authenticity of your purchase. Always ask the seller to use the youVerify app prior to purchase. It's Smarter Selling & Safer Shopping.