So during your time creating mines and exploring various cave systems you probably have discovered a few hidden coves with strange flaming cages in them. Those are creature spawners, they create zombies, skeletons, creepers and more. If you destroy it they stop coming out, but, if you leave it alone, they continue to spawn, now wouldn't it be great if you could create a way of being able to harvest the loot drops from them with little to no effort? Check out this video, in it, you will learn ...

Spidey is after the next fragment in the distant future, 2099 to be exact. A new fragment has been discovered, and Scorpion is on the move to get it, and the only person qualified for the job to bring him down is your friendly neighborhood web head. In this video you'll get a full walkthrough of chapter 7 along with the final boss fight.
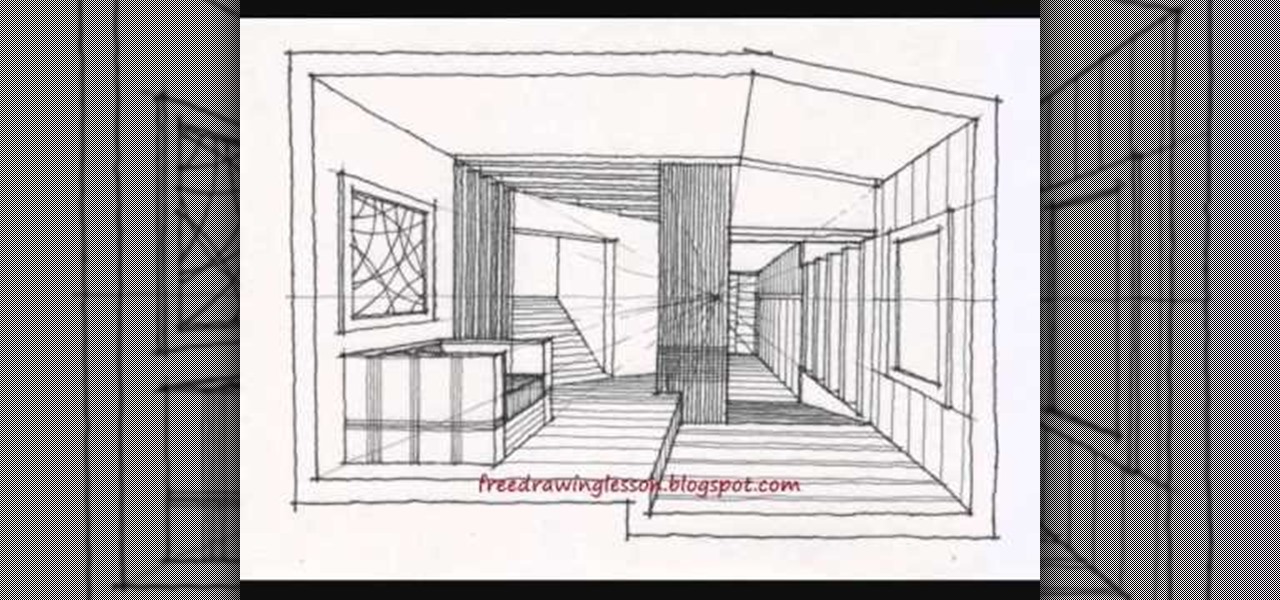
When vanishing point perspective was first discovered in the early Renaissance, artists were astounded by how the draftsman tool was able to transform a flat, 2D space (that until then always looked like a flat, 2D space without perspective) into a believable 3D image. We've been using vanishing point perspective ever since, and architects would die without it.
Attention all achievement hunters! It's time for, yet, another achivement tutorial. This time the game is Dragon Age: Origins. For this tutorial, you'll be finding out how to get the Perfectionist achievement in the game. This can only be obtained after you've played across all the playthroughs and discovered all the possible endings.

Facebook is a wonderful website where you can connect and keep up to date with your friends. Facebook has some useful features like chat. Facebook chat can be used to chat in live with your online friends. The chat also supports smileys. Using different character combination you can create different smileys. To create the happy smiley type :). To create sad smiley use :(. Use :P to show a funny smiley. These are the basic smileys. There are many more smileys present like the one showing teeth...

British record producer David Spoon explains how he uses the computer program Propellerhead Reason 4 to create rhythm and bass tracks in his home music studio. He explains that by just messing around with the controls within the program, you can create a lot of interesting sounds and effects. Sometimes the best sounds are discovered by accident. He uses Filter 2 to create interesting effects that he describes as "acid-y" or "nasty", having to do with the resonance of the bass sound. He also a...

Next time you don't want to make your bed, dry the dishes or clean the house there's no need to feel guilty. You may be doing yourself a favor. There are legitimate scientific reasons why some chores aren't always the best health choice.

Nobody likes having to stand at the crosswalk waiting for the light to change so you can cross. This seems to happen more times then not these days. A way has been discovered to eliminate this problem with ease. The first thing you are going to want to do is go to the pole that has the button to push for the crosswalk. Once you get there you are going to want to enter a combination of long and short clicks to get the light to change so you can cross. The first combination is going to be three...

Chutney is a term for a class of spicy preparations used as an accompaniment for a main dish such as chicken or fish. Serve this delicious mango chutney with your prepared fish or chicken dish tonight.

If you've been playing Fallout 3, you may have discovered that picking the locks in Fort Constantine is fairly difficult. Thankfully, this video clarifies how you can pick these locks without going through a bunch of bobby pins.

Sick of that burning, persistent, acid sensation? With a couple of easy steps, you can put your stomach at ease and boost digestive health.

Keep your fish healthy and your fish tank clean with these simple steps. You Will Need

With a torque wrench, you can set a bolt to the proper tightness and cut down on wear and tear. You Will Need

Microwaves are quick and easy to use, but unfortunately they don't yet clean themselves. Learn how to clean a microwave oven properly.

If you use your inkjet printer regularly, you’ve probably discovered that the cost of replacing the cartridges can quickly exceed that the printer itself. Refill the cartridges yourself to save some money.

Although most of us can't grow Mangoes or Avocados or some of the other plants we're looked at, most everyone can grow or enjoy Orchids. Today they're readily available and there are thousands of species and it's believed there are thousands that have yet to be been discovered. Considering the way they're propagated today and the many places they're sold there is no reason we all shouldn't be growing Orchids. Karen had a fear of growing Orchids, thinking they were difficult to grow. She recei...

Learn how to start seeds for planting. Start your own seeds to save money, grow different plant varieties, and extend your growing season.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

One downside to iOS 11's awesome built-in QR code scanner in the Camera app is its only been live for a short while. In its short life, there has already been a security vulnerability discovered that was an issue for at least the last 4.5 months, but Apple has finally patched this weakness with its iOS 11.3.1 update.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

Apple found itself in serious trouble last week when a teenager discovered a critical FaceTime bug that threatened the security of nearly every iPhone user. The bug enabled a user using Group FaceTime to access either the microphone or the camera of a recipient before they answered the call. According to Apple, the issues have been fixed in an iOS 12.1.4 update released Thursday, Feb. 7.

We've already taught you how to clench your fist to make healthier food choices, and how to make sure you eat healthily at a restaurant, but it turns out there are even more mind hacks we can use in our never-ending quest to control our appetites.

Do it yourself closet organization can be quite a journey, even with the best advice. Meghan Carter discovered first-hand the trials and tribulations of closet organization as she put herself under the scrutiny of professional organizer Cynthia Ivie. But in the end, Meghan not only organized her closet, but found a great excuse to go shopping.

Researchers have discovered a "severe vulnerability" that allows attackers to use eBay to distribute malware, and the online auction company has no plans to fix the problem.

A security analyst has discovered a flaw in Chromecast's initial setup process that allows would-be hackers to assume full control over the online streaming device.

Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highlight all of the features and changes.

Using Hydra, Ncrack, and other brute-forcing tools to crack passwords for the first time can be frustrating and confusing. To ease into the process, let's discuss automating and optimizing brute-force attacks for potentially vulnerable services such as SMTP, SSH, IMAP, and FTP discovered by Nmap, a popular network scanning utility.

After recently being in the news for collecting PII (personally identifiable information) for analytics and after-sales support, OnePlus has another security problem. An individual going by the name Elliot Alderson discovered an app in OnePlus devices that can enable root access with one command.

The Deepwater Horizon oil spill that began on April 20, 2010, was the largest maritime oil spill in history. Killing 11 people and discharging 4.1 million barrels of oil and natural gas into the Gulf of Mexico, the event was an unparalleled personal, environmental, and business disaster. It was also the first major oil spill to take place in the deep ocean.

Long admired for their active and cooperative community behavior, some types of ants also wear a gardening hat. Nurturing underground fungus gardens, these ants have a win-win relationship that provides food for both ants and fungi. If we humans understand it better, it may just help us out, too.

A disease called "citrus greening" has devastated and permanently altered citrus production in the United States, but a vaccine that could protect orange trees may be part of a winning strategy to beat the bacteria that is killing the trees.

A continuation of my earlier science testing in Minecraft, I worked on a few things requested and retouched on TNT as there was suggestion of possible (and confirmed) altered circumstances.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.