The mystery surrounding Overture, an app that showed up in the Magic Leap World app store along with the latest Lumin software release, has been cleared up.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.
While iOS 12 is arguably the best iteration of Apple's mobile operating system yet, one major fault so far is security. On Sept. 26, Videosdebarraquito discovered a passcode bypass that gave access to contacts and photos from the lock screen. Apple has since patched that security flaw, but Videosdebarraquito has discovered a new one that affects all iPhones running iOS 12.1 and 12.1.1 beta.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.

Apple released the third developer beta for iOS 11.2.5 on Wednesday, Jan. 3, and public beta testers got in on the action the following day. The update comes two full weeks after the release of the second beta, marking an extended update period of Apple. The second beta mostly brought under the hood improvements to 11.2.5.

Five Phases of Hacking:- The five phases of Hacking are as follow:

The interwebs is a great source of information, but sometimes said information is not always legit. That can be frustrating when it comes to making fun food, costumes, and arts and crafts for Halloween, like this bowl of "bloody" gummy worms.

Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often offer an entire point to the internal network and resources.

We tend to assume that eating is mostly a physical act, but the mind has so much to do with the choices we make.

I've discovered something in minecraft! Invisible pressure plates!!! Pretty excited!!

Artists discovered the almighty vanishing point during the early Renaissance and haven't stopped using it since. The genius of the vanishing point is that it gives a three dimensional quality to a two dimensional space, meaning increased depth perception and more believability.

Swing dancing dates back to the 1920's, where the African American community, discovered the Charleston and the Lindy Hop, while dancing to contemporary Jazz music. The term "Swing dancing" is used to refer to one or all of the following swing era dances: Lindy Hop, Charleston, Shag, Balboa and Blues and extends to include West Coast Swing, East Coast Swing, Hand Dancing, Jive, Rock and Roll, Modern Jive, and other dances developing in the 1940s and later.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.

Apple just released the first developer beta for iOS 13.4.5 on Tuesday, March 31. The update follows the previous week's stable release of iOS 13.4.

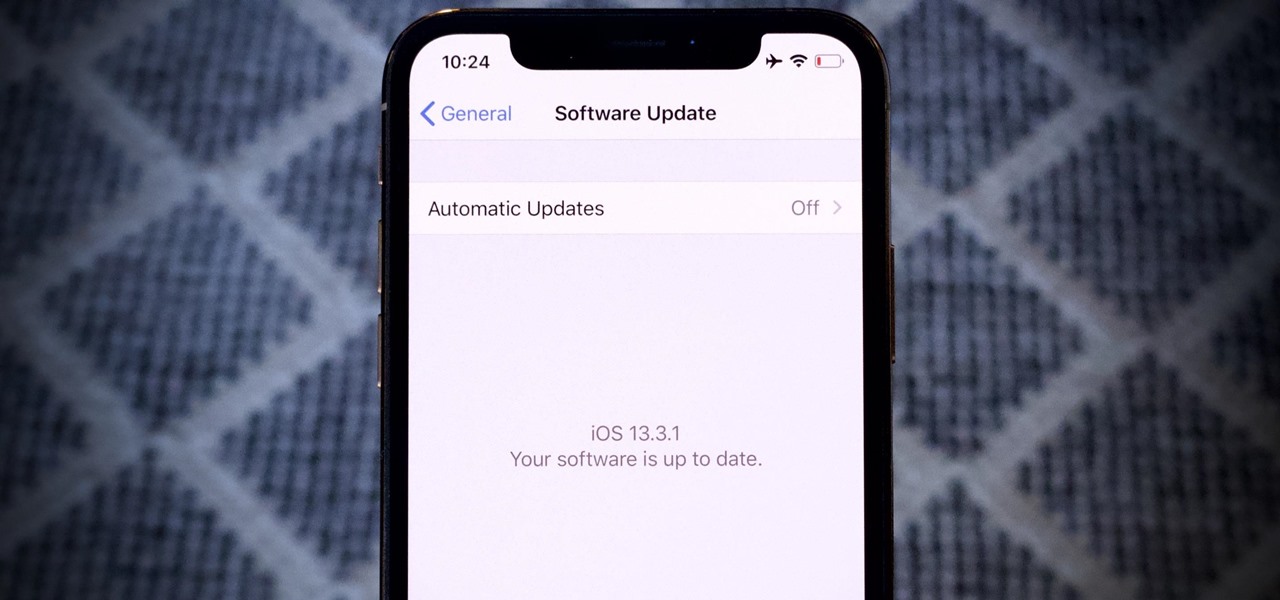
Beta testing on iOS is as Wild West as Apple gets. From feature-filled to featureless releases, there's a high level of unpredictability for what to expect. And not everything is found right away. For instance, last week's developer beta 2 added a new feature that was left undiscovered until three days later. So what has Apple hidden in today's iOS 13.3.1 dev beta 3 update?

With each year that we anxiously await Apple's next big version of iOS, there comes the sad reality that the eldest iPhones will not continue to receive support. That's not the case with iOS 12, however, as the software is compatible with all iPhones currently running iOS 11, going back as far as the iPhone 5S.

A promising new antibiotic has been discovered in, of all things, another bacteria. Burkholderia bacteria live in diverse habitats, including soil, plants, and humans where they thrive by knocking out other microbes that compete with them for resources or threaten their existence. Scientists have discovered they accomplish this by producing a very effective antibiotic.

We were really rooting for you this time, BlackBerry! With the phone company having minimal success in the past with smartphones, the BlackBerry KEYone was extremely promising. That is until YouTube Reviewer JerryRigEverything discovered a fatal flaw, the phone's screen popped off with just a bit of pressure and then stopped working. So...there's that.

Wound infections don't usually enter the blood and become systemic, spreading the infection throughout our bodies, and there's a good reason for that: Our bodies actively work to prevent it, according to research that discovered a new use for a protein first discovered decades ago.

Tardigrades are some of the toughest but least well-known creatures on our planet. These tiny animals, also called moss piglets or water bears, are definitely of this earth, but some can boast that they've also traveled to space.

A 'superbug' fungus is currently running riot in the hospitals of New York and New Jersey. This outbreak of Candida auris has contributed to 17 deaths in NYC, according to recent reports.

It's safe to say most of us know the dangers of online security. We know there are people trying to steal our most sensitive information, and we try our best to prevent that theft. But new research is showing what we're doing might not be enough, as the sensors in our phones may be telling hackers everything they want to know.

A human rights activist from the United Arab Emirates recently stumbled upon three gaping security loopholes in iOS that work by enticing you to tap a link sent to your iPhone. Ahmed Mansoor received a text message from an unknown number roughly two weeks ago, but instead of following the link it included, he sent the message over to a security researcher at Citizen Lab.

If beauty is in the eye of the beholder, music lies in the ear. Even within a group of friends who share enough common interests to sit around and socialize over, music tastes can vary dramatically.

Yesterday, the Free Software Foundation published an article written by Paul Kocialkowski. A software developer for the the Android fork system Replicant, Paul stated that his organization discovered, and later patched, a "backdoor" vulnerability that existed in older Samsung Galaxy devices, including our beloved Galaxy S3s. Only problem is, it's kind of bullshit—but we'll get to that later.

Thanks to Yifan Lu, it's been discovered that the operating system running on the Kindle Touch is written mostly in HTML5 and JavaScript, unlike the previous models which used Java. This is exciting, because when a device is hacked or rooted, that means homebrew programs can be run on the device, maximizing its potential and getting the most for your money.

Aaron Betsky, director of the Cincinnati Art Museum and previous director of the Netherlands Institute of Architecture, reports on the world's first postage stamp to employ augmented reality. Dutch advertising agency Gummo, the NIA and the Dutch postal service teamed up to present five unbuilt models by different Dutch architecture studios in 3D form. When held in front of a webcam, the illusion of a 3D building is projected in your hand. By slowly moving the stamp, you can experience the vir...

It is important to maintain a diet rich in selenium. Selenium is an essential trace mineral and antioxidant that protects your cells, boosts the immune system and helps fight infection. Check out this helpful video, and discover how to add more of this great mineral into your diet.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.