Everything you thought you knew about cooking pasta is wrong. When I took cooking classes in Italy, they taught me to bring a large volume of salted water to a rolling boil, add a drop of olive oil so that the noodles wouldn't stick together, and wait several minutes until it was al dente (which literally means "to the tooth," i.e., firm and not mushy when bitten).

It's easy to take the food we eat for granted, but the truth is, there are a lot of bizarre, wonderful, and just plain weird things about what we eat and drink, the effects it has on our bodies, and vice-versa. Read on to learn how bugs provide food dye, the Japanese grow square watermelons, and more.

Curve stitching is a form of string art where smooth curves are created through the use of straight lines. It is taught in many Junior High and High School art classes. I discovered it when my math students started showing me the geometric art they had created.

While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

The end of year surprises keep on flowing from the Plantation, Florida offices of Magic Leap. This time, it's yet another game from the company's old partner Insomniac Games, and it's called Strangelets.
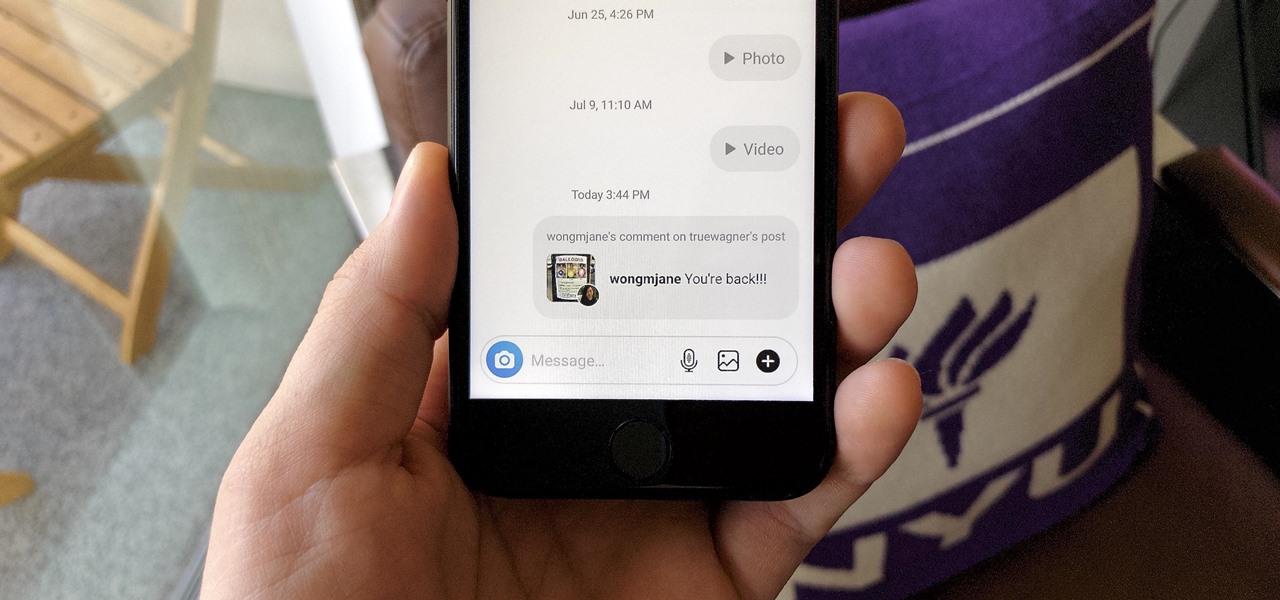
Sometimes, you'll see a comment on Instagram that you really need to share. Maybe it's something funny, possibly offensive. Whatever the case, the only thing to do is screenshot it and share that, right? Hopefully, not for long. Instagram is currently testing a feature that would allow you to share comments with others via a direct message and maybe even to stories and other apps.

Does your Activity page on Instagram feel cluttered? You're not alone. Instagram lumps all alerts into one long, chaotic timeline, so if you want to see comments or likes, you have to weed through everything else including shares from other users, memories, recommendations, and new follows. Instagram knows its a mess, and the company plans to add notification filters to sort things out.

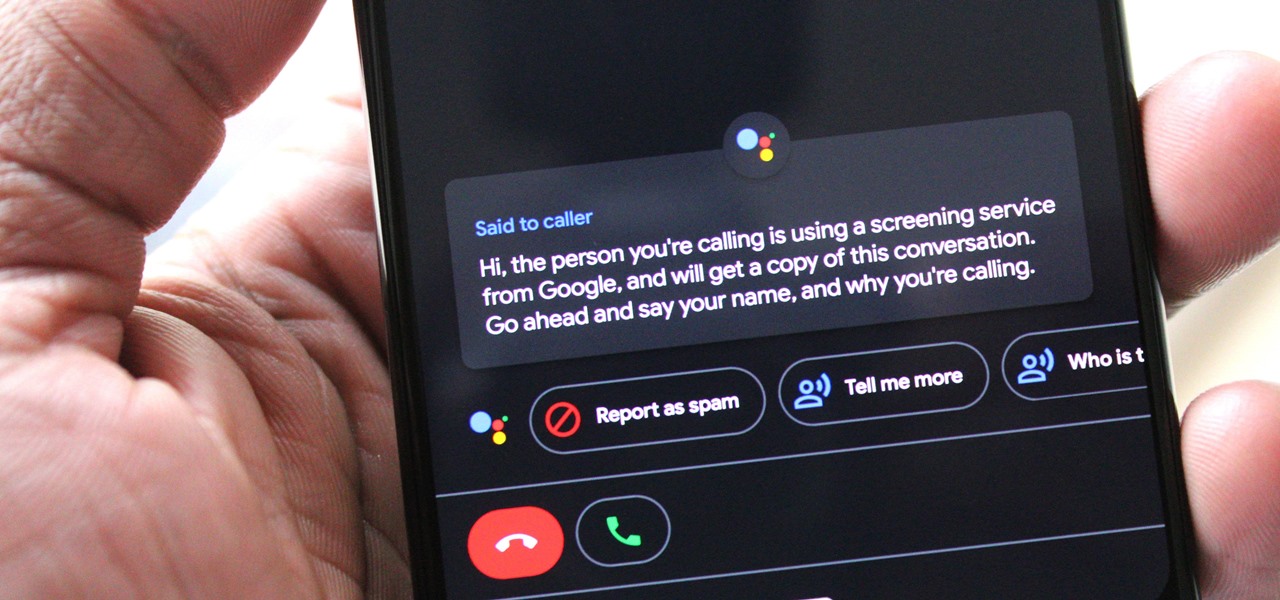
One of the best features on Pixel phones is the new call screening. Any call received on your Pixel device can now be answered by your Google Assistant, allowing you avoid spam calls, wrong numbers, or even exes. But what many don't know is that you can listen to the caller during the screening process.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

The Magic Leap One: Creator Edition has been teased for months now, and while we still don't know exactly when the sales will begin, it can't be long now because we've discovered a couple of new hints that the device's launch is imminent, hiding in plain sight on the company's website.

A peek inside the code of the Snapchat app has revealed that the company is expanding the search capabilities of its augmented reality camera to include visual search that may link to items within Amazon's massive online store.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

It hasn't been a great year for Facebook. Recently, Android users had to discover on their own that the company was logging their calls and texts in Messenger. However, according to Facebook, all users did approve of the data collection, and as such, all affected users can disable logging as well.

The Android world exploded when it was discovered that Facebook was logging the call and text histories of many of its users, although the company claims those users had explicitly given Facebook permission to log that data. The case remains that many users were unaware of this activity, which occurs on both Messenger and Facebook Lite. Luckily, it's very easy to disable.

When first released, the iPhone SE was nearly identical to its iPhone 6S counterparts in all but form factor. While the rumored SE 2 (if it even happens) is expected to follow suit with the iPhone 8 models, that hasn't stopped people from wondering what it would look like with an iPhone X-like bezel-less display.

Augmented reality developers are rapidly bringing science fiction tropes into the real world, with the latest example leveraging the TrueDepth camera on the iPhone X to emulate the cloaking technology made famous by movies like Predator and Marvel's The Avengers.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

One of the most highly-cited drawbacks to the HoloLens is its limited field of view (FOV), but now it appears that Microsoft has solved that problem.

As a long-distance runner off and on for the past, I absolutely detests hills. While there are many apps that can measure elevation and slope for certain routes, understanding spatial data on a line graph or even an elevation map can be difficult.

Android Oreo may not be the flashiest release, but it's got tons of under-the-hood changes. We recently discovered documentation in the AOSP source code that outlines one of these understated features, which has been dubbed "Rescue Party."

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

The leaks and rumors surrounding the highly anticipated Galaxy Note 8 just keep coming. But none have suggested that the new Samsung phone might be powered by a different chipset than the Snapdragon 835, until now.

We all know we shouldn't be using our smartphones while driving. But we also know many people do it anyway. Soon, however, the addicts among us may not have a choice but to kick their habit. A new app announced today by Samsung will block all calls and texts while you drive, stopping those who text and drive right in their tracks.

While there are many good reasons to update to Apple's newest mobile software, a bug has made it to where you may want to double-check your iCloud settings after doing so.

Don't ignore the update sitting in your Settings app; you'd be leaving your iPhone's security vulnerable.

A bacterium which triggers respiratory disease has been detected in the water systems of two Pennsylvania nursing facilities.

Apple lets you save webpages as PDF files in iOS 10, but the only obvious way to do this is by using iBooks. The thing is, most people would probably rather save their PDFs to a service like Google Drive or Dropbox to make sharing a bit easier. Plus, iBooks isn't officially available for Windows or Android, so there are some cross-platform problems there, too.

Mobile gaming is a huge industry that raked in more than $91 billion in revenue in 2016, and of course, all of the major players get most of the glory. But smaller, independent game developers make some of the most fun and unique games out there — it's just harder to find their stuff because they don't have the promotional budget of studios like Rovio and Gameloft.

If you're tired of fumbling with the Control Center every time you need to turn off your iPhone's LED flashlight, you'll be happy to know there's a faster way. Using a simple trick that was discovered by Redditor 49599066, you can actually toggle your flashlight off in less than a second in iOS 10 and higher.

For some strange reason, Google Now is unavailable in several countries across the globe. Users from Albania, China, Cyprus, Malta, Nepal, Puerto Rico, Tunisia, and many more big countries have reported for years that the service doesn't work in their area, mostly likely because Location Reporting is not available in their region. This is really a shame, because Google Now has some great features.

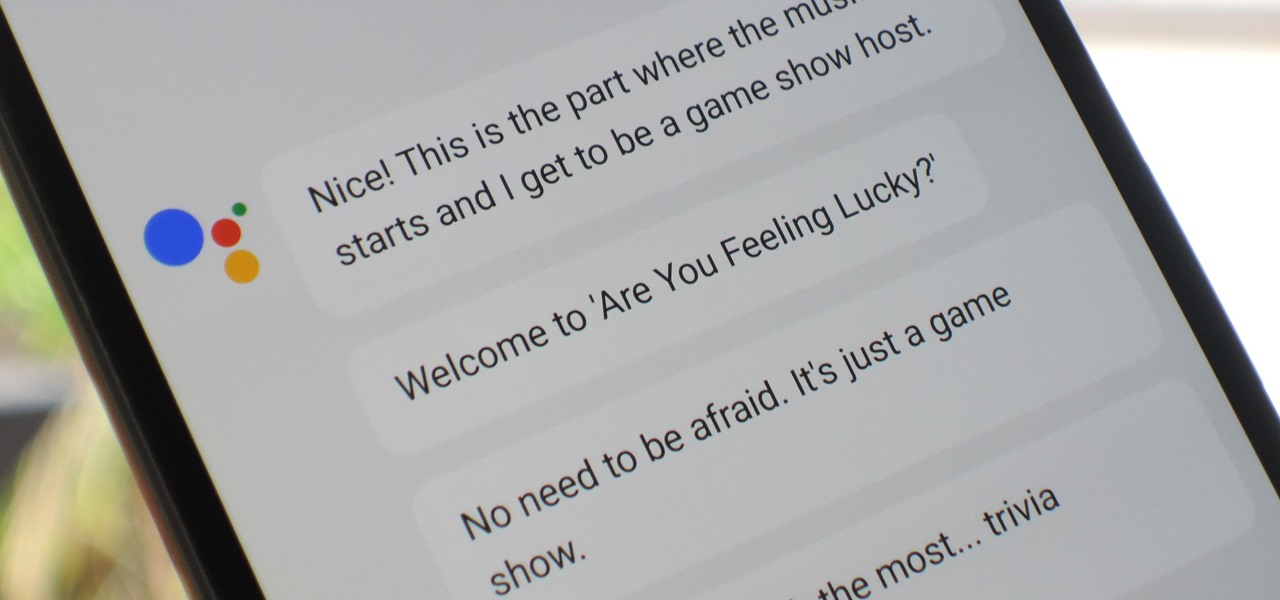
If you took your favorite search engine, gave it a witty personality, and bundled it together with a messenger-style interface, you'd have the new Google Assistant. It's great for getting fast answers—even on your follow-up questions—but its flair for fun might just be the standout feature.

A new iPhone exploit has recently been discovered by YouTube user videosdebarraquito, who has found many other exploits and bugs in iOS over the years. This new exploit allows someone to bypass the lock screen and gain access to contacts and photos via Siri, Apple's digital voice assistant—but it only affects the iPhone 6s and the iPhone 6s Plus because it requires 3D Touch functionality.

If you want to make some money from catching bugs and are sick of pentesting Facebook, Google, and Microsoft's products, Uber may be your new favorite playground.

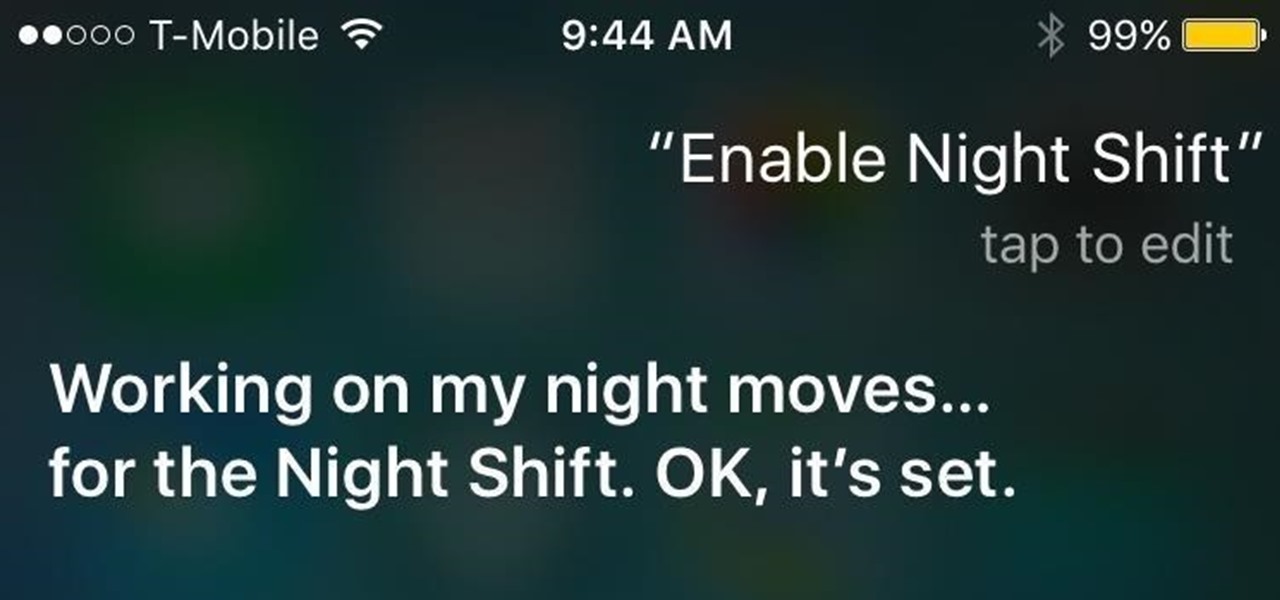
Night Shift is arguably the biggest feature found in iOS 9.3, but if your phone is in Low Power Mode, you can't use it. Some users have also reported that Night Shift causes battery drain, so using Low Power mode when you don't have access to a charger could be necessary when you're nearly out of juice. Turns out, however, that both can be enabled at the same time using a simple process discovered by 9to5Mac.

Anyone who paid attention to the Lavabit shutdown had a feeling it was connected to Edward Snowden, the high-profile NSA whistleblower. Ever since the government's case against Lavabit went public in late-2013, people have put two and two together.
According to security firm Kaspersky Lab, CoinVault and Bitcryptor ransomware are officially dead.

You would think that with each major iOS update, there'd be fewer ways to bypass the lock screen. Unfortunately, Apple's developers have consistently failed every year since 2013 in this department, leaving open lock screen exploits for iOS 7, iOS 8, and now the latest iOS version, iOS 9, with each exploit being discovered within days of the OS release.