How To: Discover the Origin of the Planetary Names?
Hello! I invite all the readers, interested in space, to discover the origin of the names of the planets in our galaxy. Just simply follow my words,... Step 1: Planets and Stars

Hello! I invite all the readers, interested in space, to discover the origin of the names of the planets in our galaxy. Just simply follow my words,... Step 1: Planets and Stars

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

When approaching a target, having a precise and detailed plan of attack is absolutely necessary. One of the main goals is to increase the attack surface since the more opportunities there are for exploitation, the greater the chances of success. Subdomain enumeration is one method used to increase the attack surface, and we'll be using a tool called Subfinder to discover hidden subdomains.

When setting up a Raspberry Pi, it's easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi's default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called rpi-hunter, hackers can discover, access, and drop custom payloads on any weak Pi connected to the same network.

Remember last month when we introduced you to Trover? Well, now this great little discovery app for iPhone has completed its beta mode and has officially launched in wide release.

When it comes to finding great new tunes for your music collection, the last place you would think to look is YouTube. But more and more artists are posting music videos on the popular video hosting site as a means to getting noticed and hopefully—building a fan base. And since YouTube is not just a music video site, there's quite a bit of junk to sift through, making it virtually impossible to find new songs to add to your iPod's repertoire... unless you use Cantio.
You're in a new city and you want to explore—what mobile app is best? If you want to know what club is hopping that night, use SceneTap. If you want to know if any friends are at a nearby get-together, use Foursquare. If you want to know what restaurant is best, try Yelp. But if you're looking to get a real feel for the city, skip the more touristy destinations and take to the streets—discover where some great graffiti is located or where the best view of the city is with the Trover iPhone ap...
Photoshop remains one of the coolest digital editing tools of all time, and if you're a user, you're likely discovering new tricks every day. One of the most helpful tricks is removing a shadow from an object, such as a face, a car, a cat, a dog or like this tutorial, a child. This excellent tutorial walks you through each and every step to show you how to use Adobe Photoshop to make those shadows vanish. Check it out and clean up your photos today!

When your kids start discovering technology, it can be a fantastic learning experience. Check out this tutorial, hosted by a third grader, to help your kiddies get used to handling a digital camera. This video is filled with a ton of tips and lots of advice, tailored just for children.

These videos will take you through the fifth episode in Alan Wake on the Xbox 360. You're almost to the point of discovering where Alan's missing wife is. Is she in Bright Falls or is she dead? Before you can find out, you have to defeat Episode 5 - The Clicker. Watch the gameplay on Nightmare Difficulty.

There are many different things that could contribute to a power or gas outage or accident in your home. To be properly prepared for an emergency or other situations that endanger you, take a look at this video from SDGE on simple tips to keep safe, including discovering gas leaks and using power generators to maintain eletricity in your home during an outage.
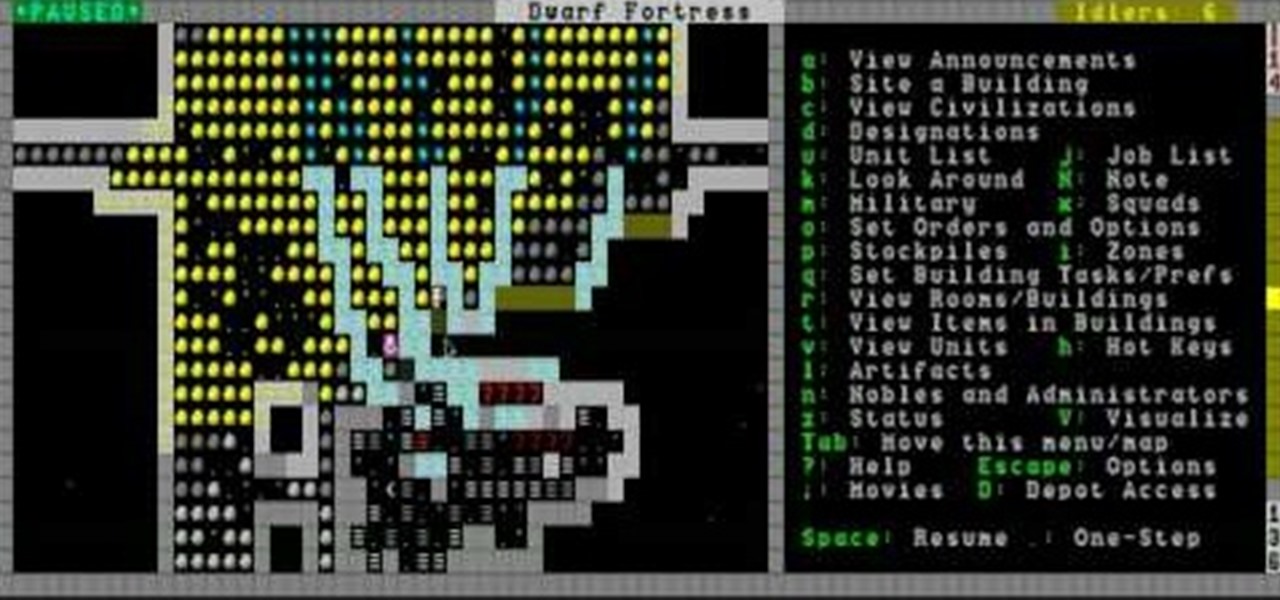
Adamantine is the best, most versatile metal in Dwarf Fortress, but discovering and using it bears great risk. This video will teach you all about adamantine and how you should react to ensure you survive what happens after you find it.

Check out this dance tutorial video that demonstrates how to do a chest circle in belly dance. The chest circle of belly dancing is an important move to study. Learn to belly dance for fitness or art in this belly dancing video.
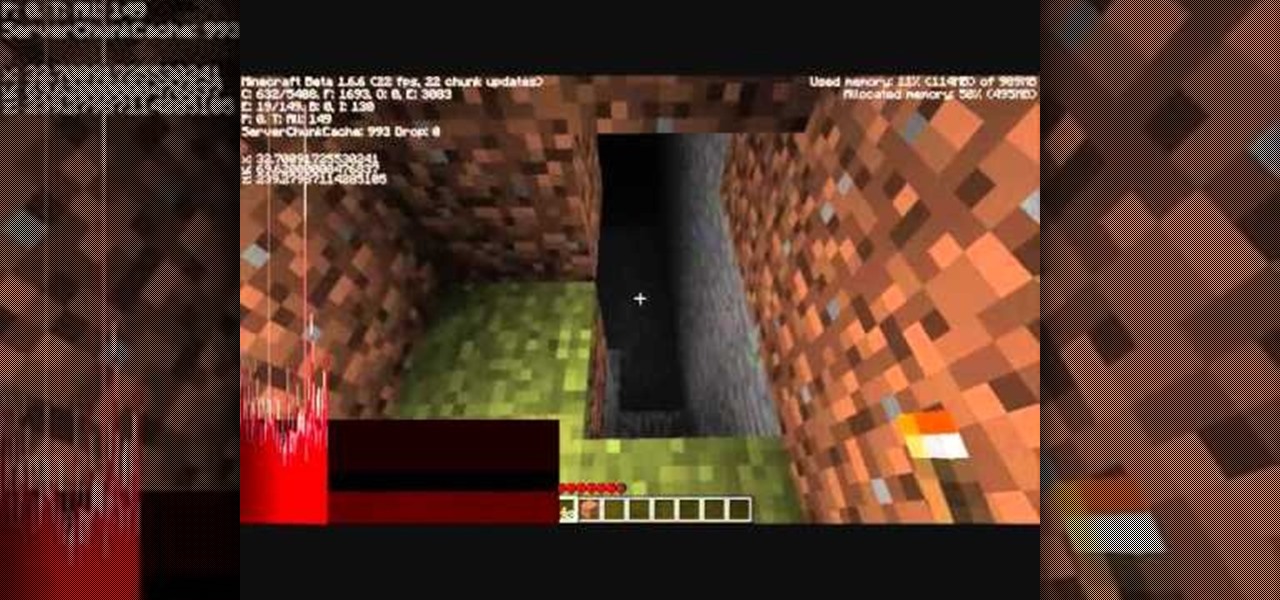
Where are all the caves? Let this video show you. Watch this Minecraft guide to learn how to find caves in Minecraft. Learn techniques for finding caves in your Minecraft world and start discovering new resources to use for crafting.
This clip demonstrates a pair of handy shortcuts for discovering the PIN and phone number of a BlackBerry phone. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this official video guide from the folks at Blackberry. For detailed information, including step-by-step instructions, take a look.

In this video you'll look at different methods of discovering a vacuum leak in your vehicle wherever it may be. Word of caution: FOLLOW THESE INSTRUCTIONS VERY CLOSELY, there is a chance that you CAN catch your engine on fire if you do it wrong.

If you getting ready to place a load of wet clothes into your dyer and notice a faint smell, it may not be time to panic just yet. Even though discovering an odd odor is alarming, it isn't the end of the world.

There's nothing more maddening than opening the office fridge and discovering your lunch is gone. Put an end to the stealing with some of these strategies. This video will show you how to deter coworkers from stealing your lunch.
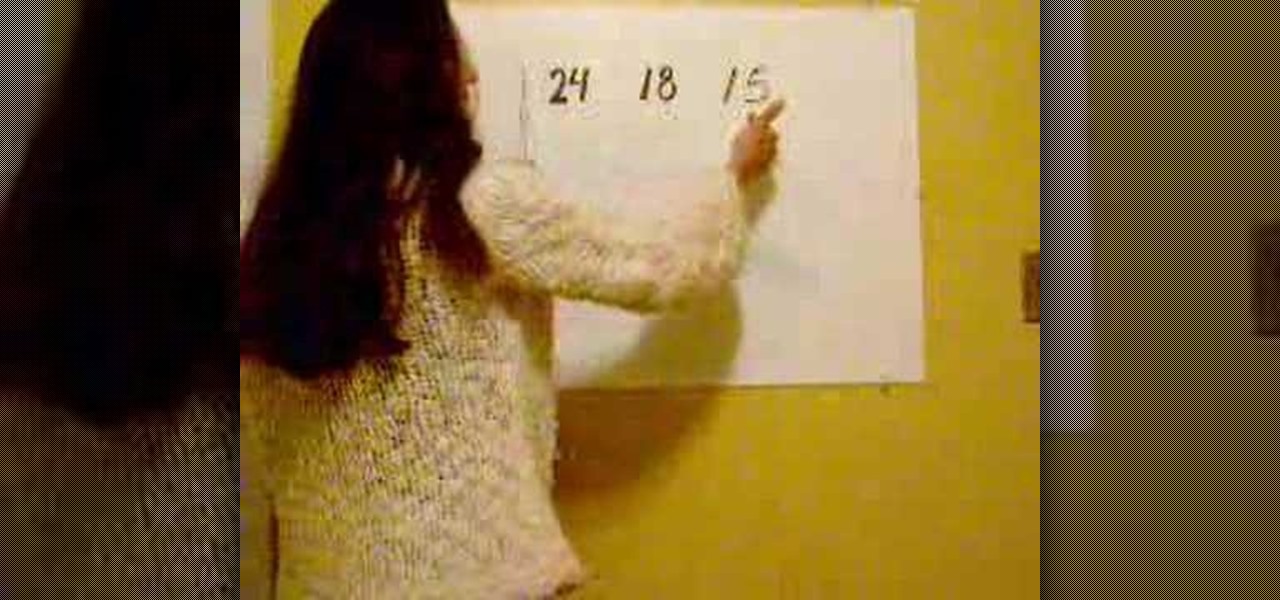
Looking for an easy method for discovering the lowest common multiple (LCM) and/or greatest common factor for a set of numbers? Try the Indian method! Learn how with this free video lesson. From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test).

Schoolteacher looks into choosing your career path. Helping students and people first looking for jobs, in discovering their best suited career path.

Personalize your drinking glasses by etching names and messages on them. Your guests will be so impressed!

Check out this dance tutorial video that demonstrates how to do the shimmy in belly dancing. The shimmy is a move fundamental to belly dancing that all dancers must master. Learn to belly dance for fitness or art in this belly dancing video.

Is the proper term nudists or naturalists? Doesn't seem to be too much of a difference, because when it all boils down, they're both still butt-naked on the beach. Nude beaches are fascinating places for the adventurous spirit, but unless you’re an old-time nudist, you probably have questions about the proper way to behave on a nude beach. Well, we’ve got the answers.

Discovering your partner's affair can be devastating, but it doesn't have to mean the end of the relationship.
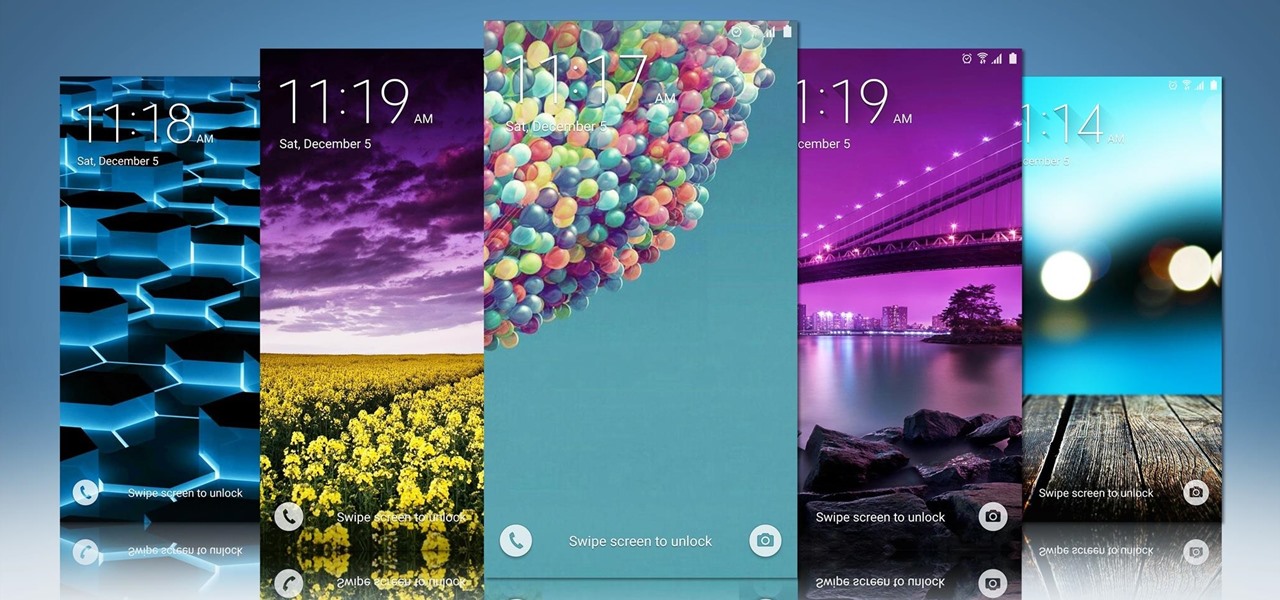
Say what you want about Samsung's TouchWiz UI being cluttered or overbearing, but one thing you can never complain about is a lack of features. In fact, it's been almost 8 months since I first took my Galaxy S6 Edge out of its box, but I'm still discovering features to this day.

If you are anything like me, you have a knack for taking silly selfies of yourself, i.e., taking scotch tape and wrapping it around your face to make yourself look like the blob, or perhaps you like taking selfies of yourself in weird or unusual situations doing weird and unusual things.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

Following in the augmented reality footsteps of Pokémon GO, Universal Studios has decided to give us an AR version of Jurassic World.

While flying can be a frustrating and sometimes nerve-racking experience, Airbus is banking on augmented reality features in its new iflyA380 app for iPhones and iPads to help passengers learn to love the ordeal.
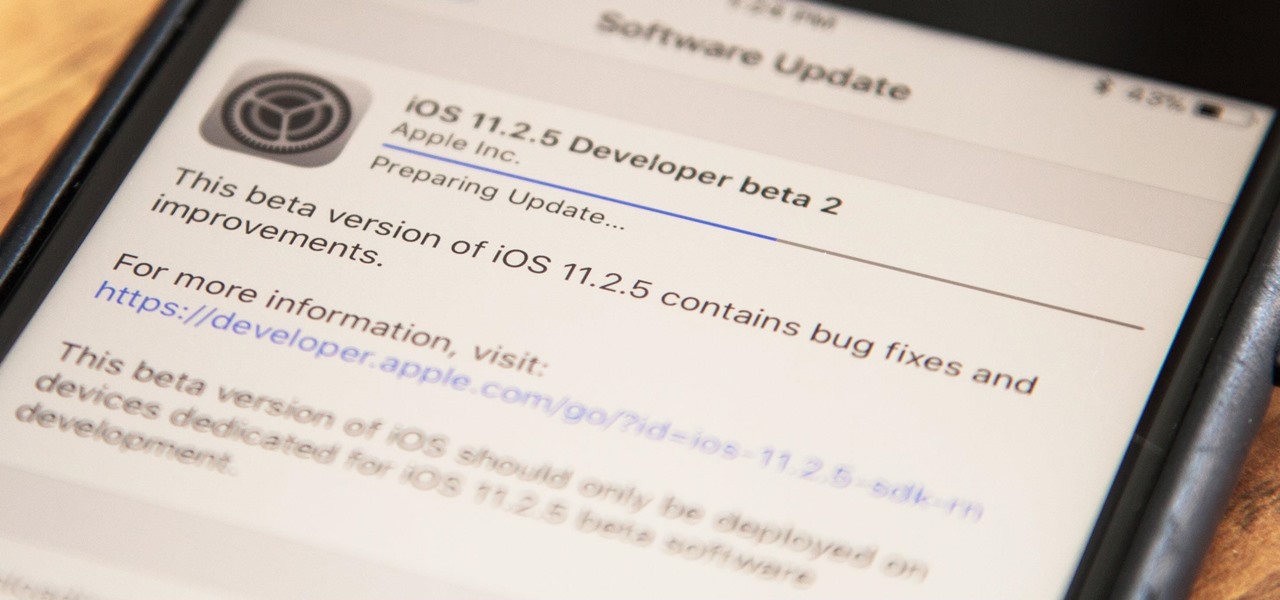
Apple has released the second beta for iOS version 11.2.5 for developers on Dec. 19. The update comes six days after the release of the first 11.2.5 beta which updated the Music app to include a persistent "play bar" at the bottom of the window, along with some bug fixes. Public beta testers received the update on Dec. 20.
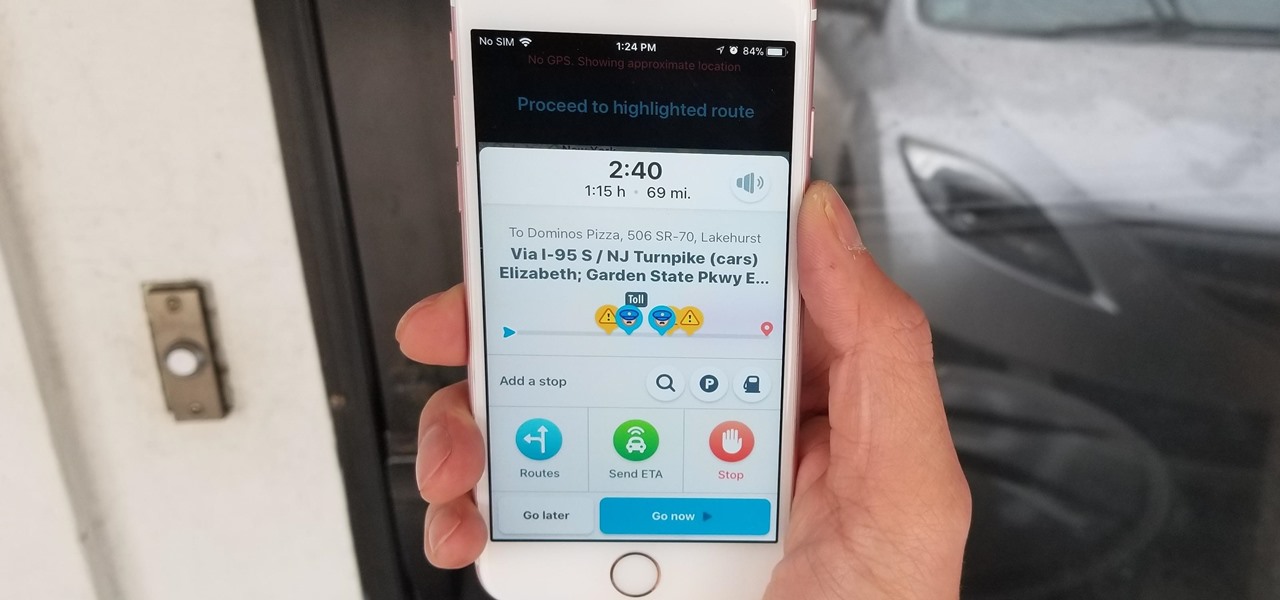
Discovering you're on a route filled with tolls while you're already on the road, with no cash on hand, is never a pleasant surprise. Fortunately, Waze has an incredibly simple solution to nip this potential headache in the bud and save you money while navigating.

Las Vegas is known as the city of sin, a place for gambling, fine dining, and decadence. Now, you can add another notable characteristic to that list: West Nile. You may want to hold off on scheduling your trip to the Sin City — or at least stock up on bug spray — because health officials have reported that mosquitoes in Southern Nevada have tested positive for the virus.

We just keep discovering hidden features and settings scattered throughout the Galaxy S8's system like little digital Easter eggs that were largely left unadvertised. One such setting is an option that lets you change the placement of your S8's display brightness slider.