Gmail has been the email standard for quite some time now, and for good reason: it's a free service provided by one of the largest tech companies in the world that offers users an amazing feature set to manage, send, and keep track of all their important emails.

Widgets are great ... if you actually use them. A quick swipe right on the lock screen will reveal the Today view and its widgets, and it's very easy to accidentally open. Plus, others can see your widgets without any authentication. You could manually remove every widget, but that wouldn't prevent the right-swipe from opening the Today view. There is a way, however, to disable the page entirely.

You probably don't give much thought to buying yogurt in the store. You have your favorite brand, or maybe you like trying new varieties each week; either way, you just grab it and go.

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.

Hash browns are a breakfast staple and for good reason: they're simple, salty, and crispy, and so delicious that you can easily down several servings of them in one sitting. Basically, they're the French fries of breakfast.

Scrambled, sunny side up, hard-boiled, soft-boiled, over easy, and poached: there are only so many ways to cook an egg before you get bored and look for inspiration somewhere else.

We're maniacs for mustard: we put it on our sausages, our salmon, our turkey club sandwiches... you name the dish, we find an excuse to spread mustard on it. So it's not surprising that it's a common item on our grocery list.

Mashed potatoes are a reliably tasty side dish, but they can definitely get a little boring sometimes. So if you're looking for that extra 'oomph' that goes beyond the classic butter and salt seasoning, try infusing your next batch with the flavor of baked potato skins.

When given the choice between canned and dried beans, many of us are guilty of reaching for cans. They're much more convenient than investing 5-6 hours of your time to make dried beans edible.

Pickling isn't rocket science. In fact, anyone can make their own speciality pickles using just about any fruit or vegetable. For example, I've pickled everything from lemons, watermelon rinds, and apples to red onions, carrots, radishes, and cucumbers.

Dried spices and herbs seem to be immortal; a peek in your parents or grandparents' cupboards will likely unveil cinnamon, basil, and oregano older than you.

A sphere of clear gelatinous goo may not sound all that appetizing. But to food fad fans on social media, the raindrop cake—a soft and lightly flavored edible blob—has gone insanely viral.

The Google Play Store hosts the largest collection of mobile apps on the planet, and it's the default app store for almost all Android devices. Ironically, though, while Google made its name with a powerful search engine, it can sometimes be difficult to find what you're looking for on the Google Play Store.

The Google Now on Tap feature puts the power of Google Search inside each and every application on your Marshmallow-powered device, allowing you to retrieve contextual results based on the content on your screen.

Welcome to a tutorial on XOR encryption. We'll be looking at what XOR is and how we can use it to encrypt or decrypt data.

Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

Nowadays, it feels like you can't talk about eating healthy without bringing up quinoa. Quinoa (KEEN-wah) has been the "superstar" of the health movement for a while; 2013 was declared the International Year of Quinoa by the United Nations, and has only continued to grow in popularity with both health nuts and culinary experts alike through the past few years. The true testament to quinoa's success has been its eventual integration into our everyday lives. Quinoa is now very accessible to fol...

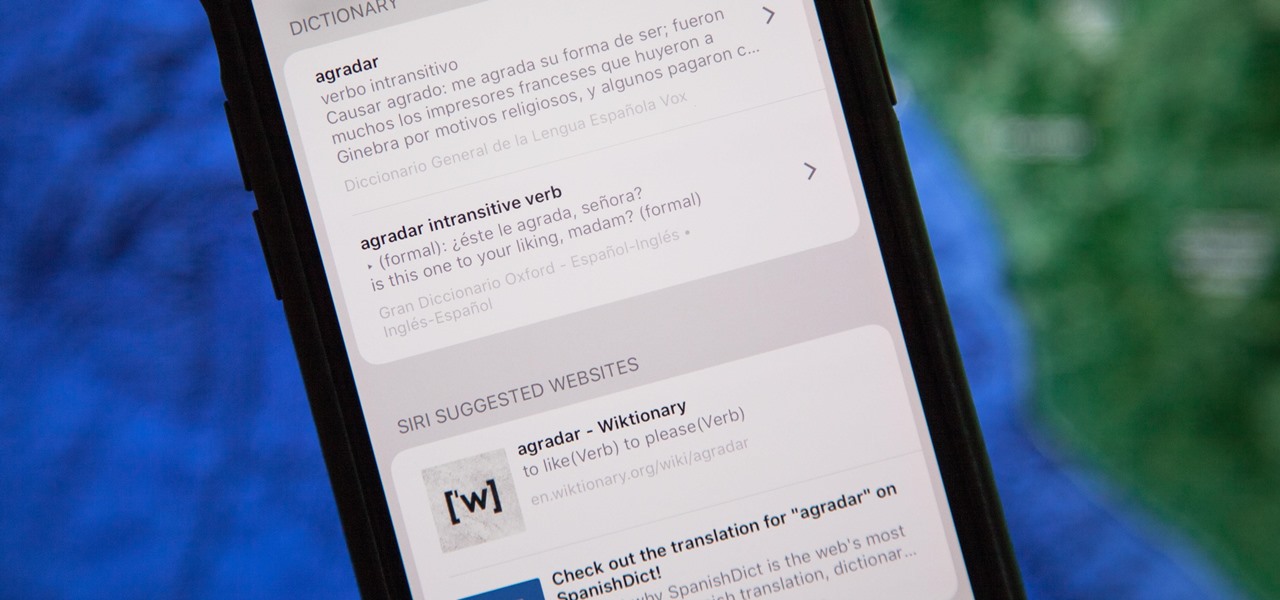
The native dictionaries in iOS, which have been around since 2011, let you define words on your iPhone on the fly in Safari, News, Notes, and other apps. But if you read or write in more than just English, you won't be able to see accurate definitions unless you add those other languages to your list of dictionaries manually.

Smelly foods are what make my culinary world "go 'round," so to speak. I grew up with fish sauce, learned to cook with and love fermented beans and veggies, and am one of the biggest garlic advocates I know... other than my husband, who thankfully shares the same smelly food sensibilities. (Let's put it this way: anyone that can stomach stinky tofu can handle anything I could possibly cook up.)

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/

Hello everyone. I've recently made the annoucement of the Null Byte suite of tools, and we've covered how to download and install it. Now it's time we cover how to submit a tool for inclusion into the suite. It's relatively simple, but we need to get a few ground rules out of the way.

Pop-Tarts are a pretty iconic breakfast food. And while I'm more of a bacon, eggs, and toast person myself... sometimes a sweet, gooey, artificially-flavored treat is just what you need in the morning. Yet, despite the fact that I do enjoy Pop-Tarts, I've always found them a little bit bland. Therefore I decided to make them better—by cooking with them.

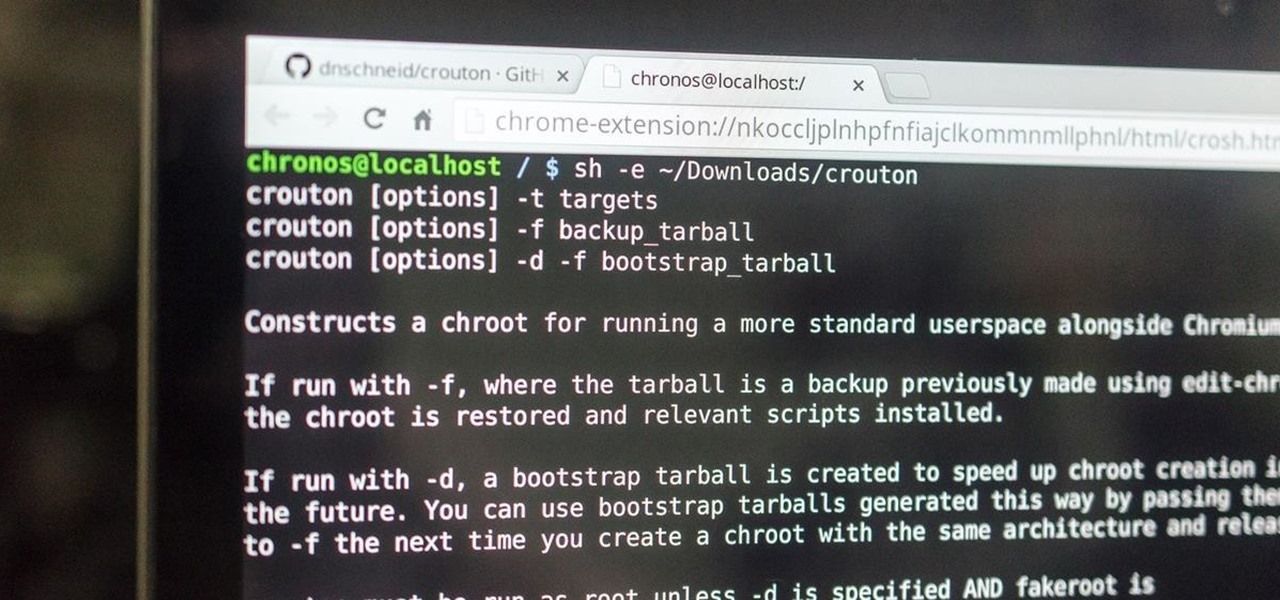
This is my first how-to for this site so feel free to let me know if I can somehow improve! Inspired by the great Jailbroken iDevice and Rooted Android PenTesting tutorials I decided to share how I use my Toshiba Chromebook 2 with Kali Sana.

Tahini: it sounds like the name of a high-end fashion designer... or perhaps a variation on a two-piece swimsuit. But this "weird ingredient" is actually a delicious and nutritious paste made from toasted sesame seeds and oil.

Garlic is magical. It fends off vampires (or so I hear), helps lower blood pressure, reduces the production of cholesterol in the body... oh, and it's also freaking delicious, of course. Garlic is a culinary staple in countries all over the world. That lovable stink and sharp bite of flavor are essential to many dishes we know and love today, from spaghetti to sesame chicken.

Android Beam is one of those features that makes you look at technology in awe, wondering how exactly something like that works.

There's only one day that can top the aftermath of Easter and its copious amounts of leftover candy, and that is November — the day after Halloween. As you come down from your sugar rush and realize you now own more chocolate than your stomach can physically hold in one sitting ... fear not! Here are several ways to turn your Halloween chocolate into delicious snacks and desserts that you can enjoy at your leisure.

Hello, everyone! Many of you don't even know about my existence here on Null Byte, so I thought of contributing something rather interesting. Recently, someone asked how to make your own "Bad USB," and I promised to make a how-to on this topic. In addition, it would be nice to have something related on our WonderHowTo world. So here it is!

In the last iteration of how to train your python, we covered basic string manipulation and how we can use it to better evaluate user input. So, today we'll be covering how to take user input. User input is very important to scripting. How can we do what the user says if we can't tell what the user wants? There are multiple ways to take input, we can give the user a prompt and take input from them directly, or we could use flags/switches, and take their input before the script is even execute...

A perfectly ripe avocado half is a lovely snack, and a creamy bowl of homemade guacamole can make a meal. But the following ten ideas take green-eating up a notch by stuffing avocado halves with your favorite salads and ingredients, turning them into a snack or side dish fit for a king.

In case you didn't know, Android has an awesome hidden settings menu called "Developer options" that contains a lot of advanced and unique features. If you've ever come across this menu before, chances are you just dipped in for a minute so that you could enable USB debugging and use ADB features.

Practically every smartphone comes with a built-in camera app, but these apps are generally created by the device's manufacturer. And let's face it, manufacturers are hardware companies first and foremost, so they don't always produce the best software.

One of the first orders of business after purchasing a new smartphone is to load up your shiny new toy with phone numbers, email addresses, and general contact information for all the important people in your life.

To be twentysomething is an awkward time for entertaining. As we graduate college and begin to work in “the real world,” there is a yearning to transition from keg parties into dinner soirées. However, though the desire is there, often the bank account is not. Here are some ways to do in the kitchen what twentysomethings do best: fake it until you make it. (In other words, host a fabulous dinner party for four and still be able to make rent this month!)

Whether you are sending your phone in for repairs or finally selling it to upgrade to a new flagship, you are going to need to make sure all of your personal data is removed from your device.

Unruly customers. Crazy exes. Horrible bosses. When you need proof of insanity or just want it for your records, recording a phone call is a must. Problem is, it's not the easiest thing to do on an iPhone — but it's completely possible.

SET is great when you have a short space of time at hand, however sometimes you want to know whats actually going on under the hood or have found a site you can't clone with SET.

Researchers at the cyber security firm Zimperium have recently uncovered a vulnerability in roughly 95% of Android devices that has the potential to allow hackers to take total control over your phone with a simple picture message (MMS). The gritty details of this exploit have not been made public yet, but hackers now know the general framework for this type of attack, so you can be certain that they'll hammer out the details in no time.

For many of you, this is common knowledge. But I still regularly see comments posted here and elsewhere asking, "This <AV bypass> doesn't work, because when I upload my payload to VirusTotal...."

Flowers may be beautiful, but they're not usually appetizing. Sure, nasturtiums are hip in fancy restaurants, but they're primarily used as a garnish. Granted, fried squash blossoms are incredible, but the point remains: flowers are usually reserved for looking at, not masticating.