Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highlight all of the features and changes.

The once blurry and mysterious vision of Magic Leap's future is slowly coming into focus in the present, despite the company's obsessive attempts to keep any and all information under wraps until the next reveal is absolutely necessary. A new tidbit of information hints at an addition to the company's unfolding story that almost no one had accounted for: retail stores.

Samsung hopes to make a splash with the new Galaxy Note 9 to make up for the underwhelming sales of its signature Galaxy S9 series. This flagship is a radical departure from its predecessors — it's now optimized for gaming and paired with the most advanced S Pen stylus to date. Here's everything you need to know.

After testing a series of Android 8.0 builds, Essential hit the reset button and jumped to Android 8.1 Oreo. The beta program didn't last long, as Essential has now released the official 8.1 update to the masses. The features from the 8.0 betas are all still there, plus a few goodies specific to the updated version. We'll highlight the standouts here.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

No matter your reasons, you might need a second phone number that's a little more disposable than your primary number — a "burner" number, so to speak. If you create this burner number using Google Voice, you'll get new functionality like call forwarding and voicemail transcripts, and best of all, it's completely free.

Nintendo set the internet ablaze Wednesday night with two big announcements. First, Nintendo revealed that the Switch's paid online service will begin in September (boo), but it was the other report that really got fans excited — Mario Kart is coming to your iPhone.

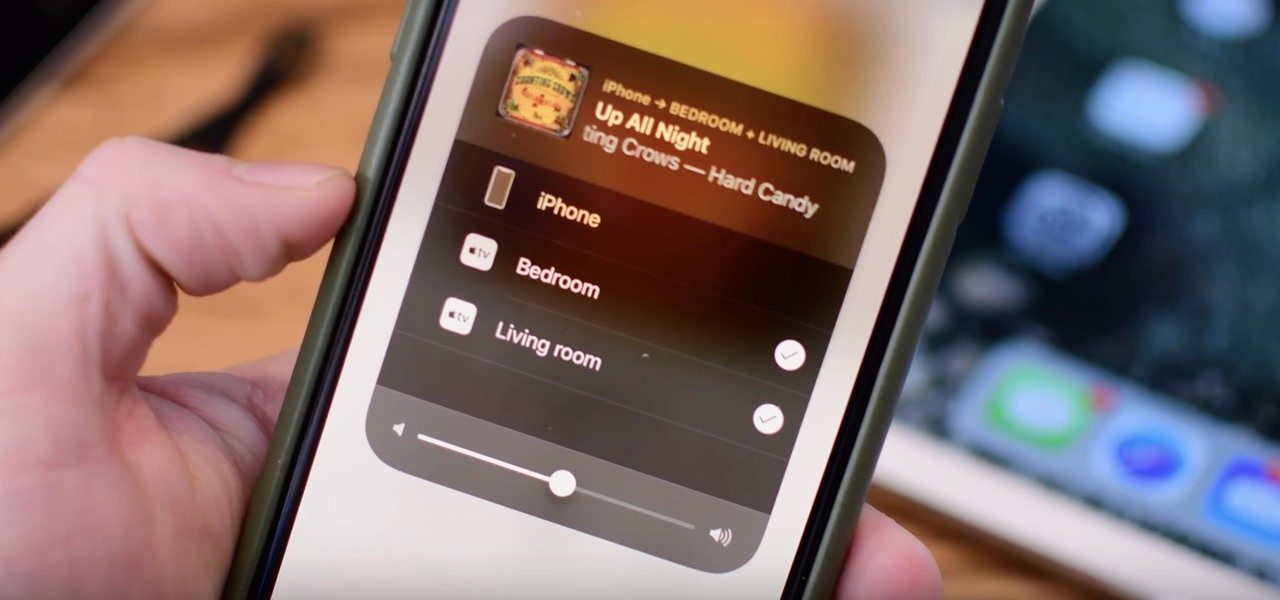
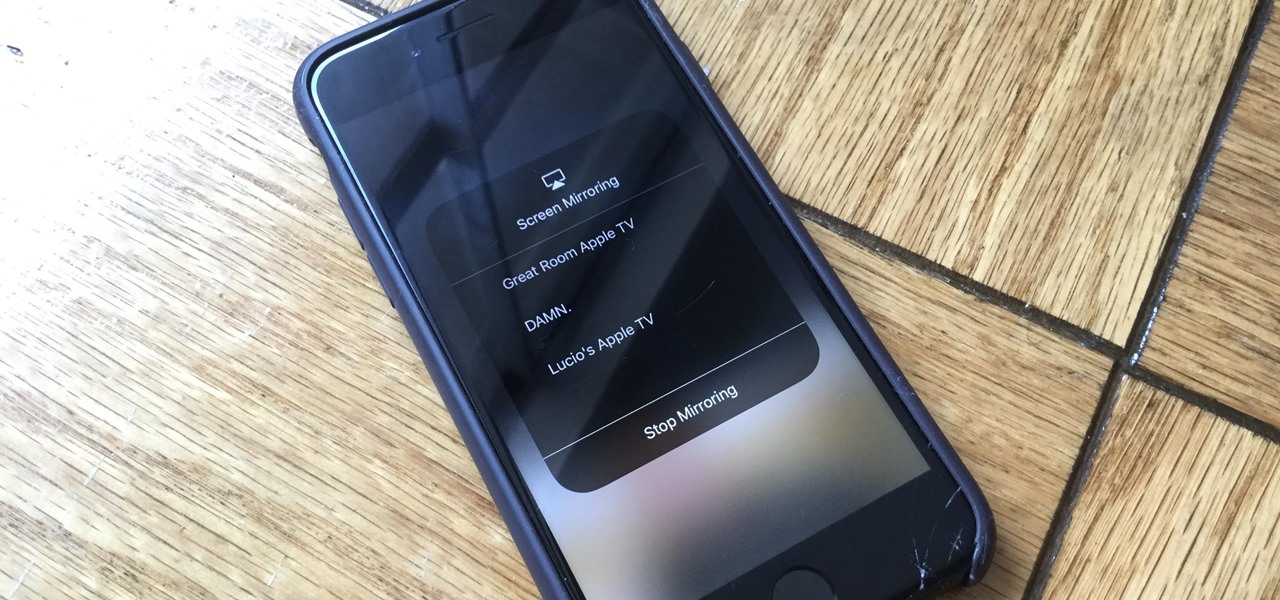
Back in June 2017, Apple promised us AirPlay 2, a simple way to connect and control multiple speakers together via an iPhone or other Apple device. While the feature was included in early iOS betas, by iOS 11's official release, AirPlay 2 was nowhere to be found. After all the numerous subsequent iOS 11 updates, it's finally here in iOS 11.4.

Apple's Mail app for iOS isn't a bad email client by any means. However, it just doesn't cut it for iPhone users that want a more intelligent and advanced email solution. If you're in the market for an app like that, Spark is absolutely your best bet.

The reveal of Magic Leap One: Creator Edition brought with it some insight into the path the device took from prototype to "final" design.

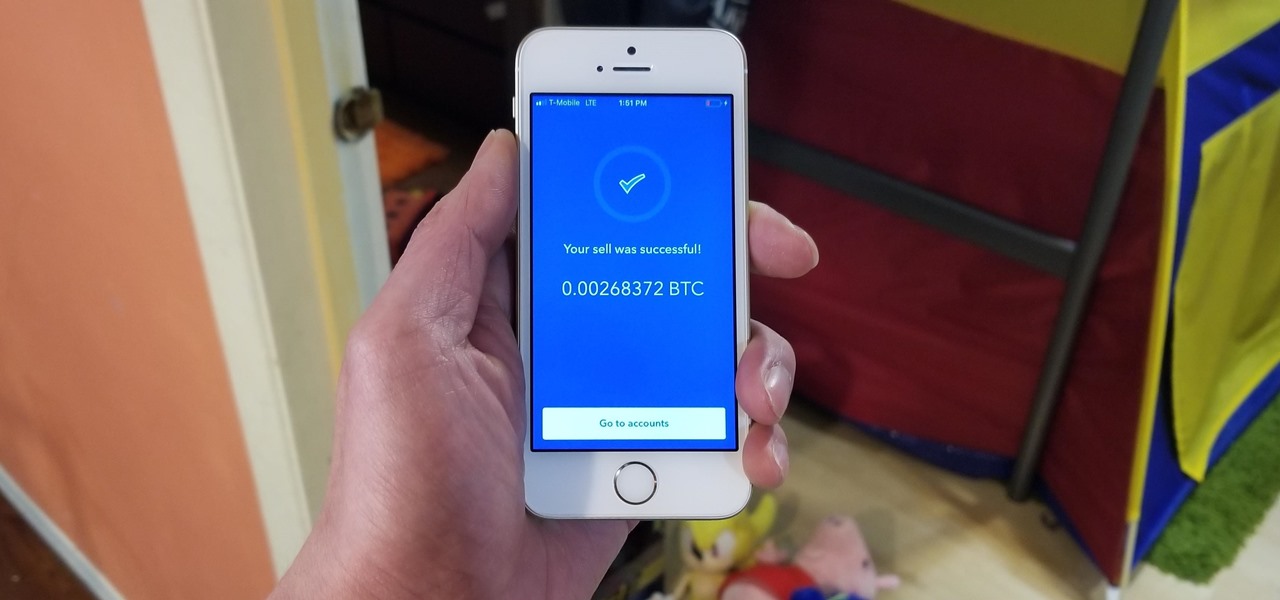
Coinbase has become the most popular mobile wallet app due in large part to its user-friendliness. The app takes the hassle out of buying and selling Bitcoin (BTC), Bitcoin Cash (BCH), Ethereum (ETH), and Litecoin (LTC), letting Android and iPhone users alike trade their favorite cryptocurrency in a few easy steps.

If you're a regular reader of Next Reality, you're more likely to spread the joy of augmented reality than most others. But it can be difficult to introduce newbies into the AR fold if you don't give them exactly the right starting point in terms ease-of-use and affordability. But fear not, oh gift-giving AR pioneer, we're here to help!

The holidays are stressful. Between traveling, family, and dinner, Thanksgiving weekend can feel like weeks. Many families have traditions that make the days long, but some of us would rather curl up somewhere and watch our favorite shows. But all is not lost — our phones do so much for us now that they can help make the long stressful weekend much more bearable.

Samsung has finally rolled out the Android Oreo update for the Galaxy S8 and S8+. If you're just now getting the update, you'll be happy to know that your Galaxy just got upgraded with plenty of cool new features. Like previous updates, Samsung has improved upon its software by including a new look and new functionality.

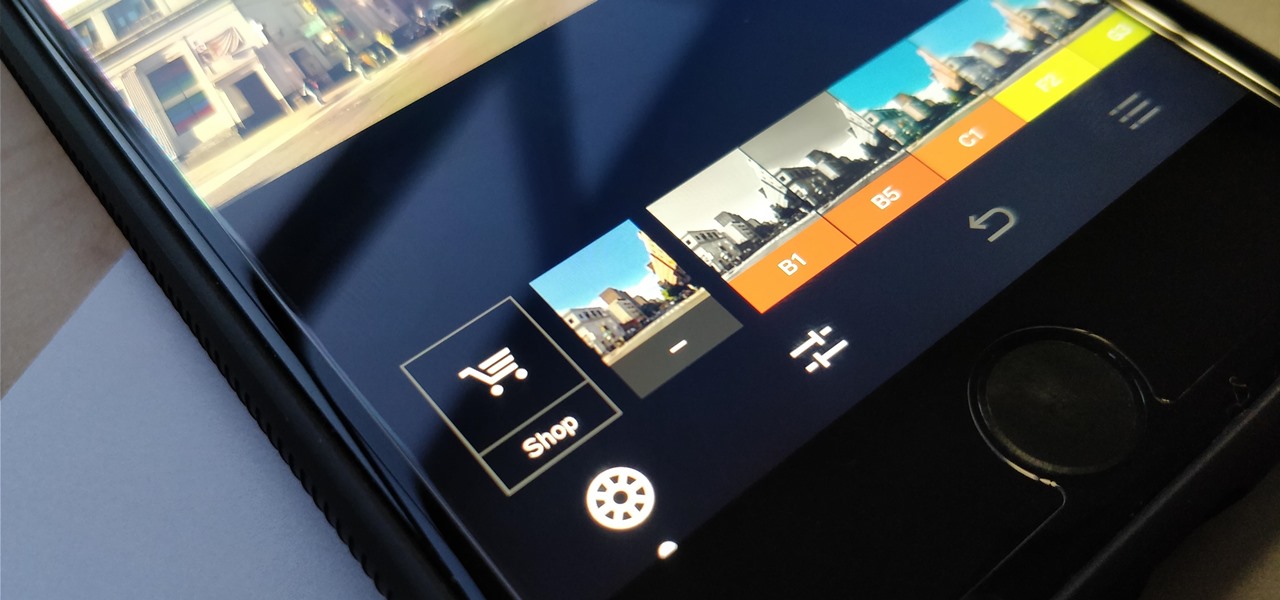
One of the best features VSCO has to offer is its presets, also known as filters — they reduce the labor it takes to make your images look better by applying unique preset edits to each. Presets can make your photo look like it came from a professional studio or a black and white camera from the '70s. Sounds great, right? So, how do you get started?

Most Android launchers limit you to three choices: Icons, widgets, and folders. It's better than nothing, but it's still pretty hard to find the best look without overcrowding your home screen. You could fill everything up with icons, but then you'd have an iPhone. You could toss everything into folders, but that would always require an extra tap. You could mix in some widgets, but that would take up valuable space. So what do you do? Action Launcher has the answer.

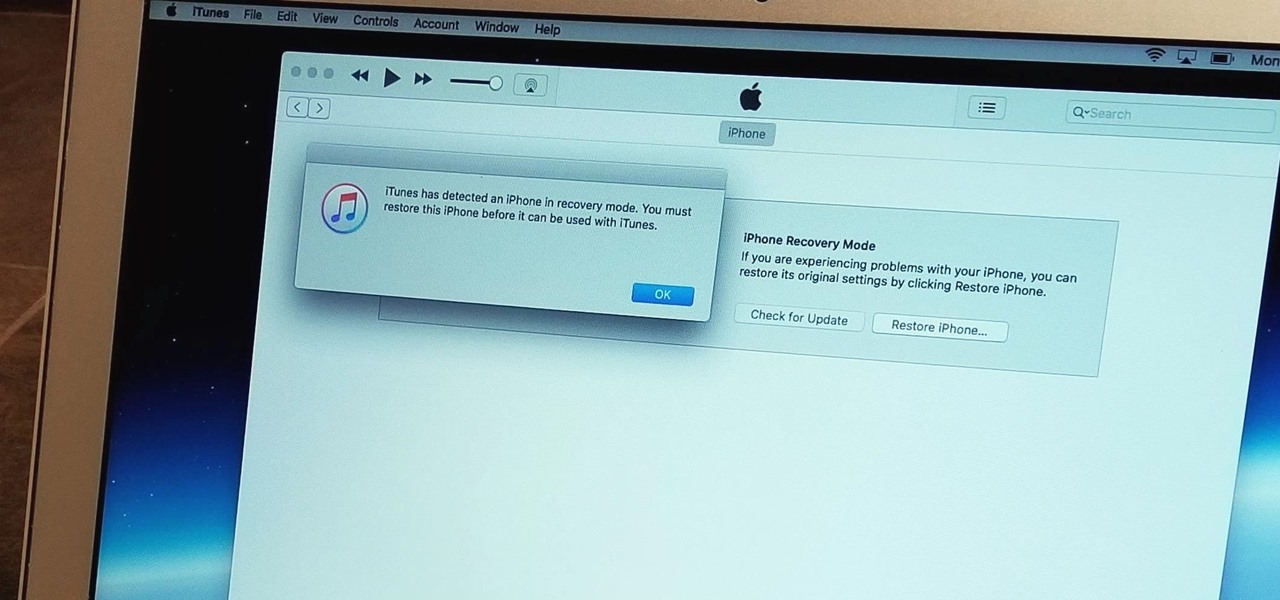
With the iPhone 8, 8 Plus, and the exclusive iPhone X, Apple has come full circle in transitioning its users away from the home button present since the first iPhone a decade ago. This gives us a window into Apple's design philosophy moving forward, but it also presents some new problems, especially when it comes to entering and exiting DFU mode in iTunes.

Now that iOS 11 is official, everyone can enjoy all of the great new features available, but there are certainly a few bad seeds in there that you'll probably find annoying. Luckily, a lot of these disagreeable quirks can be changed for the better.

When it comes to applying augmented reality to various business functions, as the saying goes, there's more than one way to skin a cat.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

While HBO Now does not support offline viewing yet, your smartphone is the perfect way to watch your favorite shows and movies on-the-go. Whether you're in a hotel running off Wi-Fi or you have an unlimited plan and are on the bus, if you want to binge some Game of Thrones, the HBO Now app is there for you.

The new iOS 11 was just released by Apple, and you can install it right now. Overall, it's got some great features, but how does it fare battery-wise on your iPhone? And how can you increase daily battery life for more juice and less charging every day?

People who have heart disease get shingles more often than others, and the reason has eluded scientists since they first discovered the link. A new study has found a connection, and it lies in a defective white cell with a sweet tooth.

The Galaxy S8's AMOLED display is prone to screen burn-in, particularly with the navigation and status bars. But hiding these bars would make it hard to navigate your phone — that's where Pie Controls come into play.

Deep down inside, Kindle Fires are actually Android tablets — the only trouble is, Amazon has layered so much of a skin on top of it all that you can't normally use Android's main app store, the Google Play Store. The Amazon Appstore, which comes bundled with Kindle Fire devices, only has about 600,000 apps, so it would be great if you could access Google Play's library, which boasts 2.8 million.

The new Samsung Galaxy S8 and S8+ are two of most head-turning phones we've ever seen, thanks to gorgeous build quality and a seemingly bezel-less Infinity Display. Combine that with flagship-grade internals for top notch performance, and you can almost guarantee that Samsung has a hit on its hands—which means it's probably not going to be easy to get your hands on one of these beauties.

Long before Apple and Android became household names, Nokia dominated the mobile industry. The Finnish company was one of the first to develop smartphones, and their classic N95 with 2G "high-speed" internet connectivity was declared the "best smartphone ever" by some in 2007. Outside of the US, before the iPhone became all the rage, owning a Nokia phone was a status symbol akin to wearing a Rolex or Omega watch.

BlackBerry has formally announced the arrival of its flagship, the KeyOne, during Mobile World Congress 2017 in Barcelona. The all-Android KeyOne looks distinctly BlackBerry, with its 4.5" screen and physical QWERTY keyboard. Here's the lowdown on this elegant handset that hearkens back to BlackBerry's heyday, which had previously been known by its code name, the BlackBerry Mercury. Aluminum Unibody with Physical Keyboard

Augmented, mixed, and virtual reality are all a little bit different, but as many expect—including Metavision—the continuum of our next realities will converge and give us one head-mounted display (HMD) platform that can do it all. If Vrvana, a Canadian company building AR and VR headsets, succeeds, that convergence could begin as early as next year.

For years, smartphone makers have been caught up in a megapixel spec race to prove that their camera is better than the next guy's. But we've finally come to a point where even the lower-end camera phones are packing more megapixels than they need, so it's getting harder to differentiate camera hardware.

Considering how much smartphones cost in the first place, we're understandably reluctant to throw them out when we've bought a newer model. And this is probably the best practice, too, as there are many great uses for an old Android device.

Microsoft's HoloLens is certainly a leap into the future of mixed reality interfaces, but it's not without drawbacks.

Welcome back, my greenhorn hackers! In many cases when a computer, phone, or mobile device is seized for evidence, the system will have graphic images that might be used as evidence. Obviously, in some cases these graphic images may be the evidence such as in child pornography cases. In other situations, the graphic images may tell us something about where and when the suspect was somewhere specific.

Welcome back, everyone! In this lesson, I'm going to go over the use of the echo function and variables, as well as basic syntax.

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.

With over 10,000 possible combinations, a four-digit passcode may seem secure, but it's fairly easy for someone to crack your code—no matter how clever you think it is. Luckily, there are many other options for securing your iPhone's lock screen—especially if your running iOS 9.

Greetings all. I'm back with another informational review of the diversity of utilities for use in the sphere of hacking at your disposal. Today we are going to cover the insides of CUPP (Common User Passwords Profiler) in its entirety. The tool is very basic in nature, as there is little to no configuration needed to get cracking (worst pun ever). So let's get started, shall we?

In the last iteration of how to train your python, we covered basic string manipulation and how we can use it to better evaluate user input. So, today we'll be covering how to take user input. User input is very important to scripting. How can we do what the user says if we can't tell what the user wants? There are multiple ways to take input, we can give the user a prompt and take input from them directly, or we could use flags/switches, and take their input before the script is even execute...

Historically, battery life has not been a strong suit for machines running Windows. Poor decisions by hardware manufacturers combined with the resource-hogging behavior of Windows are to blame. However, Microsoft is trying to resolve this issue, once again, with the release of Windows 10.