The Unity 3D engine is not only responsible for facilitating the creation of 60% of AR and VR content but it also plays a significant role in producing the immersive stories that increasingly push the boundaries of cinema.

After establishing itself as a leader among media companies in augmented reality in journalism over the course of 2018, The New York Times pulled back from the technology this year.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.
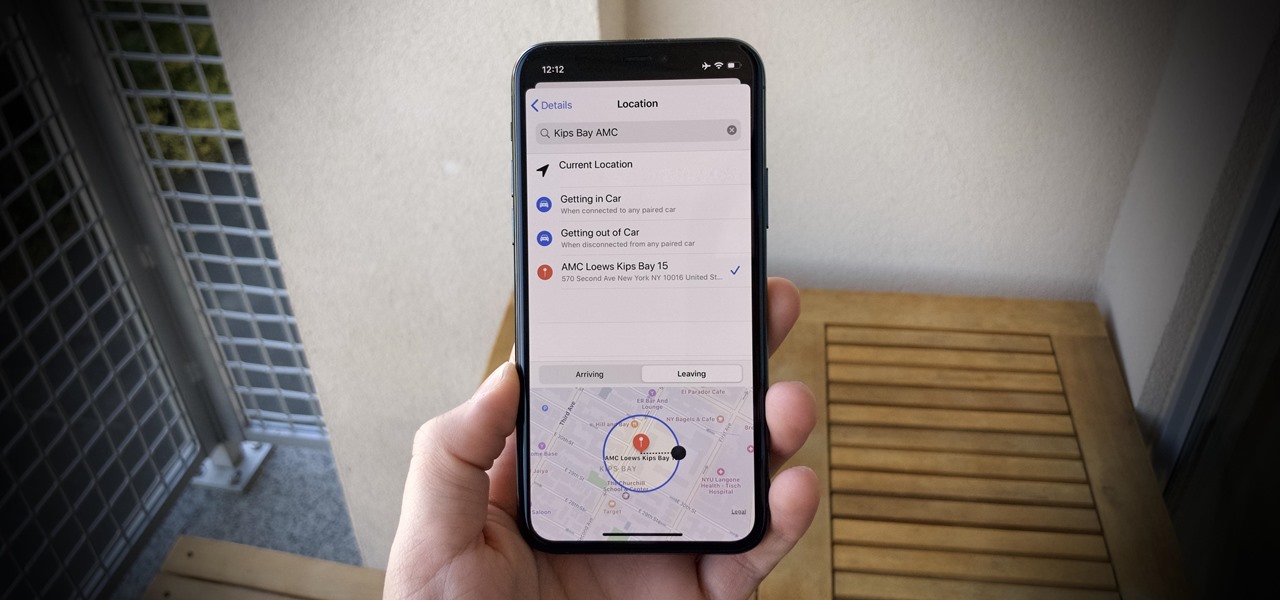
Apple's Reminders app is essential for those of us with a forgetful memory. But a standard Reminders entry isn't foolproof. They aren't great if you need to do something right when you get somewhere, since it can be tricky to set a specific time for that reminder. That's why Apple's location-based reminders are so darn useful.
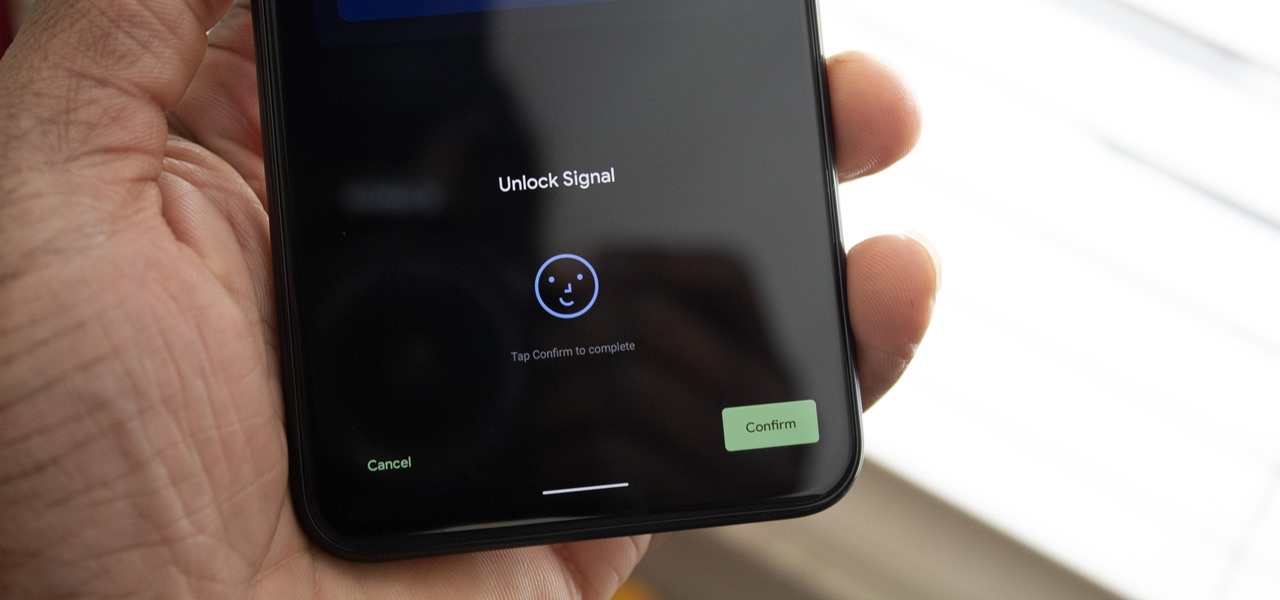
The Pixel 4 and 4 XL are the first Android phones released in the US to support secure facial recognition. You no longer have to hate on your Apple's friends because you now have "Face ID" as well. So I assume you want to set it up right away — here's how.
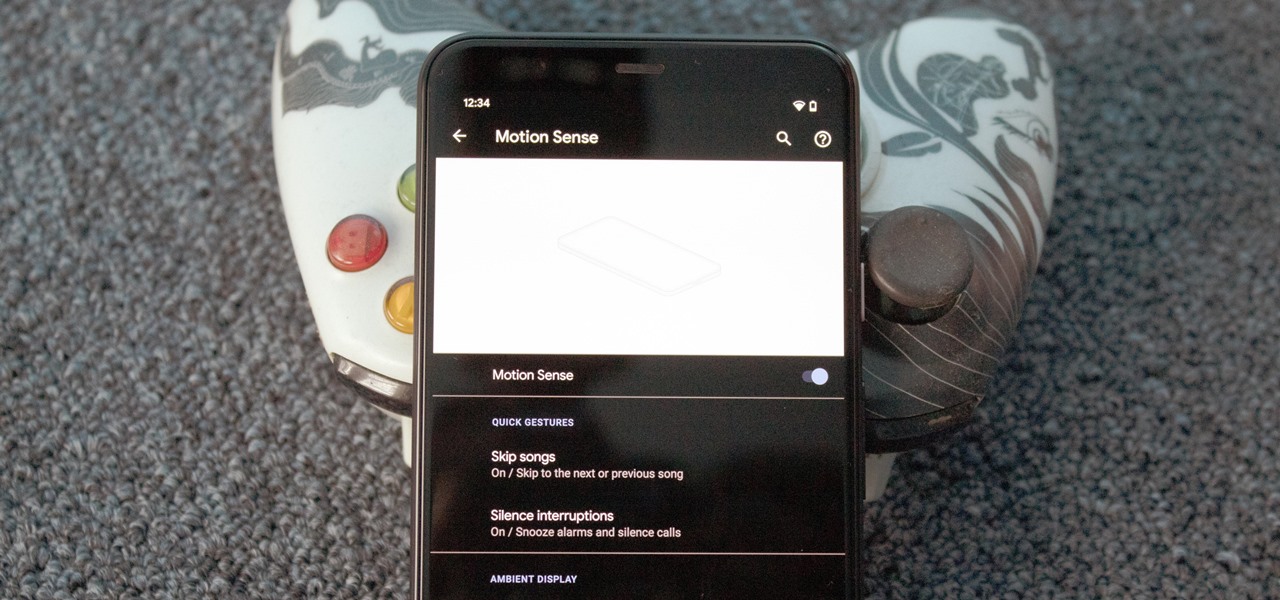
One of the major additions in the Google Pixel 4 is the new Soli chip. It's the miniature radar sensor that powers Motion Sense, a new way to interact with your phone without touching it. There are a few new gestures you'll need to learn to take advantage of Motion Sense, so let me break them down for you.

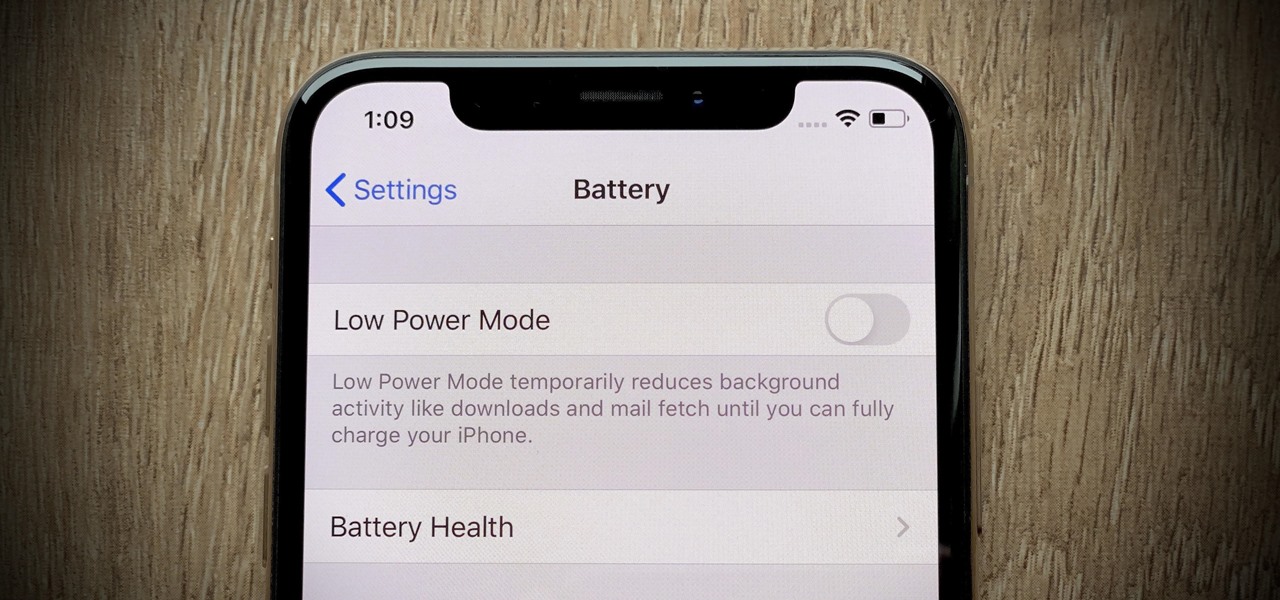
There are plenty of jokes out there about the battery indicator on iPhones. Some people complain about their iPhones dying randomly at 11%, while others see hours of use at the 1% mark. Despite its inconsistencies, that battery percentage is a useful tell for how desperate you need a charger. There's just one problem: the icon is hiding on your iPhone 11, 11 Pro, or 11 Pro Max.

Until Star Wars-style 3D hologram projection technology becomes commonplace, the near future of certain kinds of remote work is in robotics. Now, a new dynamic is using augmented reality to give this kind of telepresence a kind of superpower.

This week, Snapchat parent Snap came closer to fulfilling its smartglasses destiny by adding new 3D content capabilities to its third-generation Spectacles. At the same time, the now defunct Meta Company continued its fall from grace, as a judge ruled in favor of the plaintiff in the patent infringement case against the Meta 1 and Meta 2 headsets.

Thanks to improvements in technology, AR has become more prominent on our phones. With all the power of the Galaxy Note 10 and Note 10+, Samsung decided to add some pretty nifty AR features. One of these is the new AR Doodle mode, a feature that will make your videos pop.

Unlike many other OEMs, Samsung has two prolific phone series they release each year, the Galaxy S series and Galaxy Note series. At first, the latter was the bleeding edge of technology, but in recent years, the line has been blurred. So what do you get with the Note 10+ over the S10+ besides a stylus? Let us compare.

Every fall, we can expect a few things: leaves changing colors, cooler temperatures, and Samsung and Apple releasing new phones that fanboys and fangirls will argue about until the following year. This year, Samsung is mixing it up, releasing two phones in the Galaxy Note series. Let's see how the larger phones compare.

When it comes to the business of augmented reality, companies that aren't already introducing new products or apps are focused on producing the AR technology of the future. But in the realm of real products and apps, Magic Leap continues to show off what its headset can do, this time via a new app that transports users to the ocean's depths.

With Google taking on the sidewalks with augmented reality walking navigation for Google Maps, Apple has its sights set on the road.

Sometimes, you encounter words in a non-native tongue while using your Android device. The Google Translate app has an awesome feature where it will translate any text you highlight. An overlay will appear, and on this overlay, there will be the translation of the foreign word. This can help you if you need a translation quick fix or if you are learning a new language.

Closed captions are great for watching YouTube videos on mute, or simply following along with a video that's hard to understand. It's easy to turn on captions on YouTube's desktop site, but in the YouTube Android app, the closed captions settings are tucked away.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

With the new navigation gestures in Android 10, you reclaim a lot of screen real estate that used to be occupied by the back, home, and recent apps buttons. But there's still a small bar on the bottom edge of the screen, and in most apps, it still sits atop a black background. Thankfully, an easy hack will give you true full-screen without breaking the new gestures.

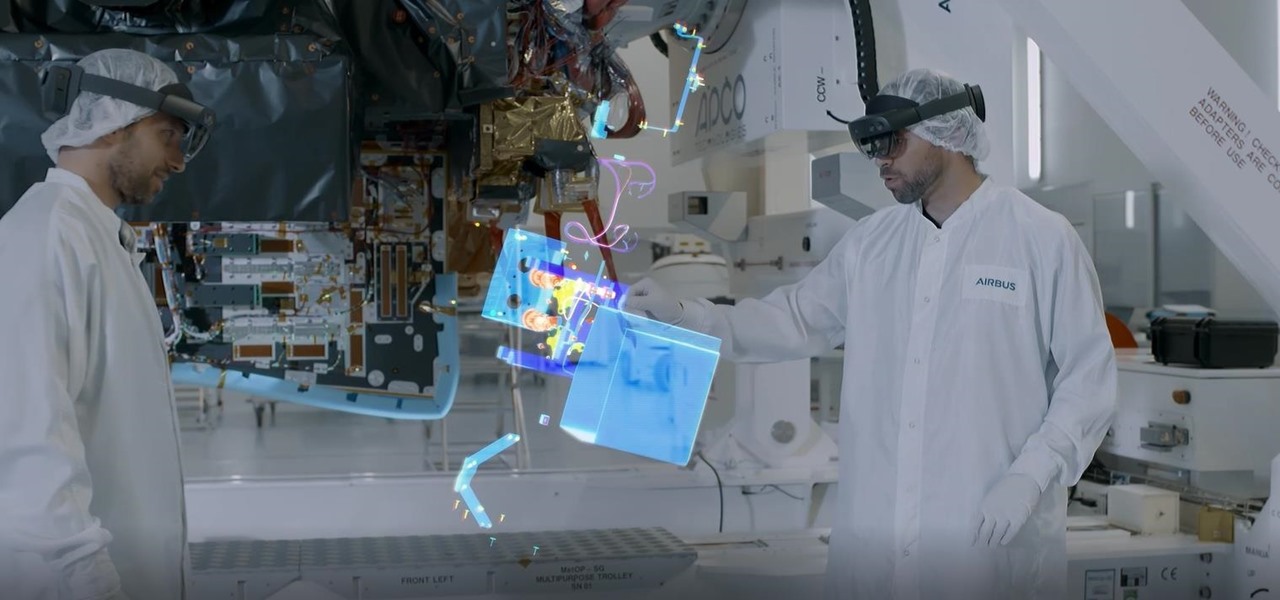
Aircraft manufacturer Airbus is so impressed with the boost in productivity it has gained from Microsoft's HoloLens, the company will begin offering augmented reality software to its customers.

In Safari for iPhone, as far back as iOS 7, you can request the full desktop version of websites. The process was streamlined starting in iOS 9, but the process remains relatively hidden and easily missed. Now, iOS 13 shines a light on it, as well as adds functionality to set the desktop view for individual websites indefinitely.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

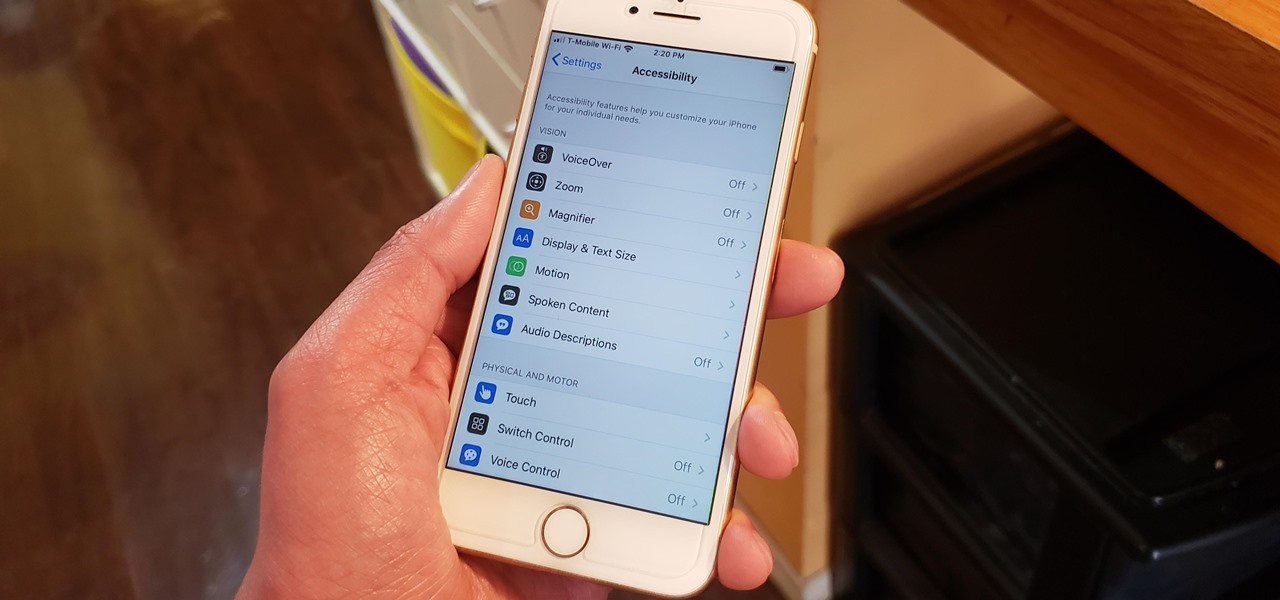
The iPhone's "Accessibility" menu is one of those options that's very easy to overlook but incredibly handy in certain situations. You can set AssistiveTouch to help navigate your device, use a Bluetooth mouse when your screen is acting up, and enable the red screen filter for nighttime escapades. For as long as the menu has been available, it's been in the "General" settings, but not in iOS 13.

Imagine being able to play a video instantly on hundreds of thousands of devices across the globe. It's totally possible, as long as all of those devices have a Chromecast plugged in. When Chromecasts are left exposed to the internet, hackers can use add them to a botnet that can play YouTube videos at will. The "attack" is made even easier thanks to a simple Python program called CrashCast.

If you've been paying attention to the smartphone industry, you've certainly noticed a rise in dark mode lately. With most phones now sporting OLED panels, which use less power to display darker colors, users have been begging developers to include a dark theme in their apps. Lately, Google has been happy to oblige.

Filmic Pro harnesses the full native power of your iPhone or Android phone — and then some. If your smartphone shoots in 4K resolution, Filmic Pro will let you choose that resolution. However, it's not all about the pixels — bit rate is an essential factor in determining the overall quality of your 720p, 1080p, or 4K video, something Filmic Pro gives you full control over.

Because of the way Android is laid out, you automatically lose a portion of the top and bottom of your screen thanks to the status and navigation bars. The thing is, you don't always need the navigation buttons. By hiding them, you can enjoy more of your Galaxy S10's big, beautiful display.

The camera punch hole on the S10 has gotten our creative juices flowing more than any notch ever could. First, we saw wallpapers that served to camouflage the cutout or even accentuate it. Now, if you want to go the opposite direction and highlight your S10's camera hole, there's an app that turns it into a circular battery meter.

New updates are always exciting, even more so when Google's behind the wheel. Yes, Android 10 "Q" is here, at least in beta form, ready for software testers to dive in and explore all the new changes. Among those changes, however, lie some issues. We won't sugarcoat it — there are some annoying things baked into Android 10.

Now that we've officially seen the HoloLens 2 and Microsoft has shown off the improvements and new superpowers of the augmented reality headset, what about the specs?

Although all signs points to Microsoft releasing a new HoloLens in the coming days, the company is nevertheless looking to distribute its augmented reality apps to other operating systems.

While augmented reality made more of a cameo appearance during Samsung's official grand unveiling of the Galaxy S10 line-up on Wednesday, it's the company's move into 5G connectivity that has huge implications for AR.

After years of rumors and waiting, Samsung's first foldable smartphone is finally a reality. The phone itself is a bit wild, but with Samsung going so far out of their comfort zone with this one, there were some bumps in the road that caused a delayed release. The launch has been pushed back yet again, but when it does hit stores, it could end up being one of the most influential devices in years.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

Update: The LG G8 ThinQ has been announced. You can read all of the official specs at our full article on the new phone.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

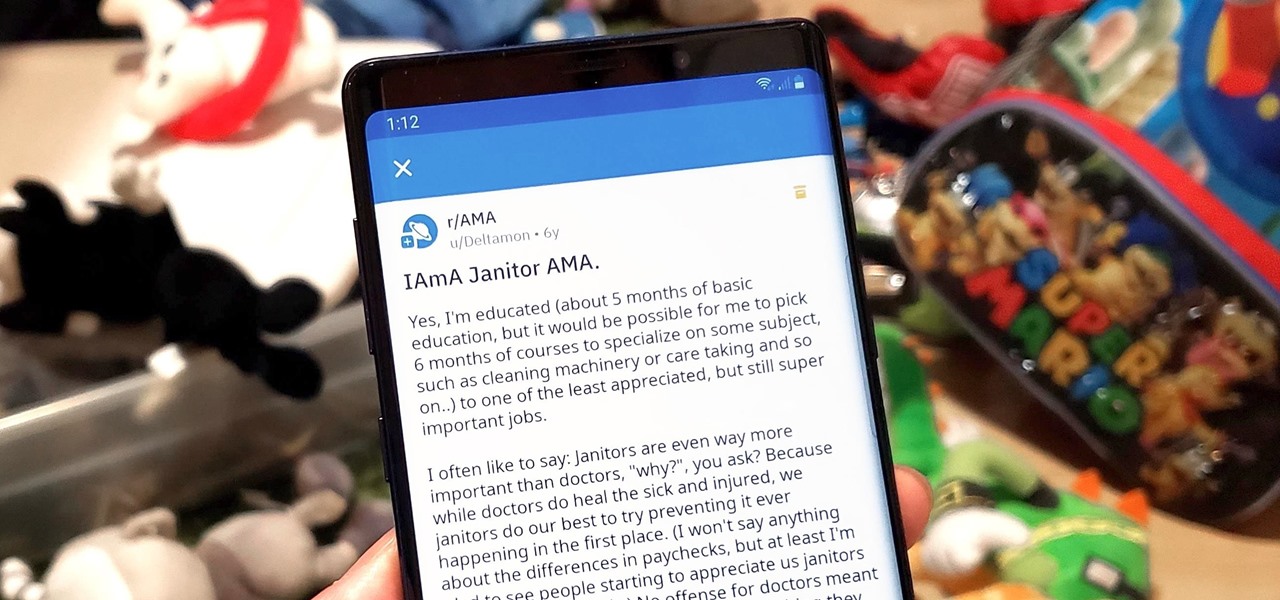
Short for Ask Me Anything, AMA threads are one of Reddit's signature features. They enable you to directly interact with a whole range of interesting personalities, from common folk with amazing life experiences to influential celebrities that help shape politics and culture.

The release of Avatar Chat for Magic Leap One and Spatial for HoloLens during the fourth quarter of 2018 appeared to revolutionize video calling via augmented reality.

The last time we heard from Meta, the makers of the Meta 2 augmented reality headset, things looked pretty bleak. Now, as several new facts have come to light, we have confirmation regarding the beleaguered company's fate: Meta is done.

If you salivate at the idea of waking up to the Jarvis-powered smart window from the opening minutes of Marvel's Iron Man, then connected home appliance maker CareOS is here to make your playboy billionaire philanthropist dreams come true.

The Google Feed is a great source for relevant news articles from your search history, package delivery updates, and much more. Now known as the "Discover" page, many Android users turn to this useful menu on a daily basis. However, as Google recently pointed out, the all-white theme is not ideal for battery life, nor is it easy on the eyes at night.