There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-depth article. In this article I'm going to walk you through one of the main networking protocols when it comes to communication across the Internet between programs, aka UDP(User Datagram Protocol).

The oven is arguably our most essential kitchen appliance (right alongside the fridge, freezer, and yes, even the microwave). But even though we've been using them for a few millennia, many of us know so little about our ovens that our cooking or baking can feel like a roll of the dice sometimes.

What if the code you are trying to reverse engineer is obfuscated or somehow corrupted? What if no way is left? Here comes what I like to call (wrongly and ironically) the "brute force of reverse engineering".

We see Steampunk props all the time and wonder where the maker found all their pieces. In fact, for some people it's almost like a game to examine each prop and see if they can name all of the original parts.

If you've been to a convention of any sort before, you know that there are good and bad panels, and that their inherent goodness or badness often has little to do with the actual content being discussed. That's because giving a panel is a skill that not everyone has. However, it is a skill that everyone could have! In this article, I'll tell you how to give a good panel on practically any subject. Image by Shannon Cottrell

Apple Card has generated quite the buzz since its March 2019 announcement. The iPhone maker's new credit card pairs with Apple Wallet on your device, is simple to sign up for, includes enhanced security over other cards, has zero fees, and provides daily rewards right to your Apple Cash account. And as good as that sounds, the fine print can complicate things real quick.

Overall, iOS is more impressive than ever with its stability enhancements, security tools, suite of apps and services, and intuitive user interface. With each passing update, things just get better and better for iPhone users. But don't think for a second that this is all because of Apple's genius — many of these features were at least partly inspired by tweaks made by the jailbreak community.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

Give an 18-month-old a shoe, check back 10 minutes later, and it's a very big maybe he will have it on his foot. But give him your smartphone, and in a mere five minutes, he can take 100 pictures of the carpet, send weird messages, and delete essential apps. Imagine what your child could do if they were able to harness this technical aptitude and put it to good use — and they can, with learning apps.

If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs at all, such as Cerberus, an anti-theft solution available right on Google Play.

So, your grandmother finally wants to ditch her flip phone for a shiny new smartphone? Congratulations. But helping her get used to her new device, even when it's an iPhone, is no small task. Grandma mastered checking her email in late-2012 and just recently learned there's a thing called "Facebook." But we love grandma, and thanks to this guide, we can definitely make this happen for her.

First of all, I would like you all to meet my good friend Iggy. There he is, in all his scaly reptilian glory. As you can see, he spends a lot more time on top of his cage than inside of it. You see, Iggy here doesn't deal well AT ALL with confinement. I don't know if it's possible for a lizard to be claustrophobic, but if it is possible, then Iggy definitely is. When his previous owner gave him to me, I tried to keep him in the cage, but I quickly realized that it was a bad idea. When confin...

Our everyday lives are inundated with displays from smartphones, computers, tablets, TVs, and other devices, so it's important to find ways to limit your screen use wherever possible to improve your overall digital well-being. One simple thing you can do if you have an Apple Watch is make your watch tell you the time so you don't have to look yourself — and this little-known feature is easy to unlock.

Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.

Stories are everywhere in social media today, but that wasn't always the case. In 2013, Snapchat introduced the world to these temporary windows into our daily lives. Since then, stories have infiltrated other popular apps. However, to stand out, you can't solely rely on the app where the story will be posted. Instead, you need a suite of apps that can turn your story into something special.

You've protected your Ubuntu system from physical attacks, annoyed network hackers, and sandboxed potentially malicious applications. Great! Now, the next logical steps to locking down your OS include thoroughly auditing Ubuntu for weak points, using antivirus software that respects your privacy, and monitoring system logs like a boss.

After installing Ubuntu as your primary OS, you should have protected against USB Rubber Ducky payloads, defended against hard drive forensics, and reduced the overall attack surface against physical strikes. When defending against network-based attacks, you'll want to minimize hardware disclosures, prevent packet sniffers, harden firewall rules, and much more.

Windows 10 and macOS have poor reputations when it comes to customer privacy and user policies. Our hacking Windows 10 and hacking macOS articles might make it seem like a reasonably secure operating system doesn't exist. But I'm here to tell you that there is a viable alternative that could provide some sense of security and trust.

Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, it requires no special dependencies and can be run via SSH, making it easy to deploy remotely.

Sometimes I forget that I'm also a fiction writer, so I thought it might be a nice change of pace to share one of my stories with you. I wrote this piece awhile ago for an anthology that never came together and I'm tired of just sitting on it.

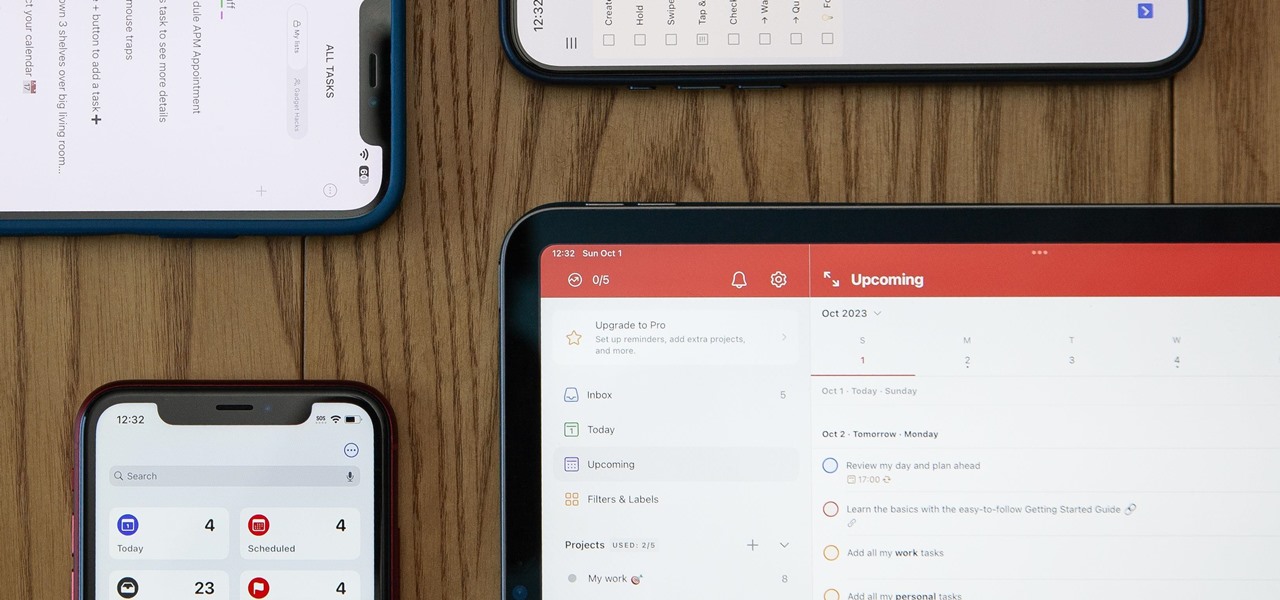
When you want a helpful task manager on your iPhone or iPad, any of the nine apps in this guide should be at the top of your list. But we'll review each app's features to help you determine which one might be best for your workflow.

The blue curacao gives this rum martini it's distinctive hue, and it's light, fruity flavor makes it a great summertime drink. Besides the curacao, you will need: 3/4 ounce rum, 1/2 ounce Midori, 1/4 ounce fresh lime juice, 1/4 ounce simple syrup, ginger beer and ice. Make a Turquoise Blue martini with rum and curacao.

Have a lot of female friends but not many girlfriends? Follow the advice in this dating advice how-to video as we show you how to avoid slipping into platonic relationships with people you actually fancy. The dating recommendations in the video are based on advice given by love doctor Sam Van Rood in his book Teach Yourself Flirting. Watch and learn how to turn yourself into the boyfriend material that everyone wants a piece of. Turn yourself into boyfriend dating material.

The independent film Juno featured one of the most distinctive opening credit sequences in recent memory. It has a wonderful handmade look - which it turned out was created by hand! Whether you have seen Juno or not, Cow leader Simon Bonner shows a much easier way to create unique, handcrafted looks, without the pain.

Garam masala literally means a blend of hot spices. It's an integral part of most curries, acting as a distinctive seasoning. Many Indian households blend their own. Here we'll show you how to make your own- add a personal touch to your Indian cooking. Make garam masala (blend of hot spices).

Ensure your orchids last for years with Sarah Raven's video advice on caring for cymbidium and phalaenopsis varieties as houseplants.

Learn how to divide and pot on congested day lilies by following Chris Beardshaw's video advice. Gardeners' World is brought to you by the BBC. Search Gardeners' World on WonderHowTo for more videos that give practical gardening advice from experts. In this video, learn how to divide day lilies. Divide day lilies.

Discover how to create and maintain acid soil conditions for growing blueberries and cranberries, with Chris Beardshaw's step-by-step video advice.

Learn how to grow runner and haricot beans up a wigwam with Chris Beardshaw's video advice. Gardeners' World is brought to you by the BBC. Search Gardeners' World on WonderHowTo for more videos that give practical gardening advice from experts. In this video, learn how to plant climbing beans. Plant climbing beans.

Follow Monty Don's video guide to planting courgette plants, with advice on planting depths and watering frequency.

Learn how to grow an early crop of beetroot in or out of the greenhouse, with video advice from Sarah Raven.

Carol Klein explains how to hand-pollinate hellebores and guides you through the process, offering practical tips and advice.

Monty Don demonstrates the most effective method for harvesting carrots, with advice on companion planting and deterring carrot root fly.

This classic 1949 Kodachrome film, Dating:Do's and Don'ts, will teach boys proper dating etiquette, how to select that perfect girl, how to ask her out, what to do on your date, and most importantly, how to say goodnight! Watch this how to video for some dated but still helpful dating advice. Go on a date with a girl.
Dr. Joy Maxey gives advice for hydration in sports.

What is your body language really saying? What are the six deadly sins of body language? Tracey Cox will tell you while offering advice on the proper body language to both appear attractive and convey attraction Use body language to attract men.

Researchers at Northwestern University have hatched a robotic replica of the ghost knifefish, an amazing sea creature with a ribbon-like fin, capable of acrobatic agility in the water. The fish is distinctive in its ability to move forward, backward and vertically, but scientists didn't understand its vertical movement until the creation of its robot replica, GhostBot (shown below). They now know its vertical propulsion is caused by two waves moving in opposite directions, crashing into each ...