Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.
According to a study done by Kaspersky, 7.6% of Android users root their phones. That may not sound like a lot, but with over 2 billion Android devices out there, the math works out to over 150 million rooted phones — more than the total population of Russia, Mexico, or Japan — so root nation is an important demographic that deserves being catered to.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

One of the best things about Android is the ability to customize every aspect of your device to make it your own. However, unless you have prior knowledge or experience with every single setting available to you, you might have missed a few critical features without even knowing it. Some settings are easy to find, while others might be tucked away in another menu of their own.

There have been concerns with how much personal information Google tracks and all the things they know about us. Of course, that's what makes Google services so useful, they can use that information to cater to each of us individually. So yes, it serves a purpose, but it's not great for personal data security.

Overall, iOS is more impressive than ever with its stability enhancements, security tools, suite of apps and services, and intuitive user interface. With each passing update, things just get better and better for iPhone users. But don't think for a second that this is all because of Apple's genius — many of these features were at least partly inspired by tweaks made by the jailbreak community.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

Coinbase is the primary go-to for many users when it comes to investing in Bitcoin (BTC), Ethereum (ETH), Litecoin (LTC), Ripple (XRP), and more, due to its user-friendly interface. But before you join them, know that the ease of use comes with a price. Coinbase charges fees for each transaction, and your bank might even add charges on top of that. Plus, there is some fine print to be aware of.

Our everyday lives are inundated with displays from smartphones, computers, tablets, TVs, and other devices, so it's important to find ways to limit your screen use wherever possible to improve your overall digital well-being. One simple thing you can do if you have an Apple Watch is make your watch tell you the time so you don't have to look yourself — and this little-known feature is easy to unlock.

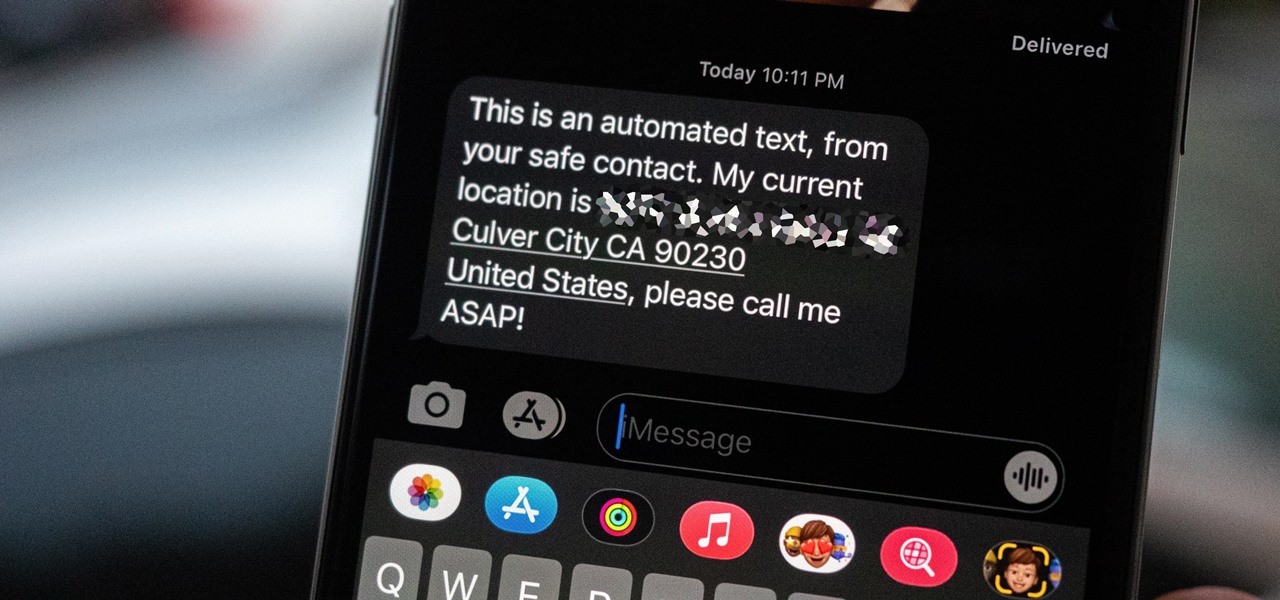
Your iPhone has a safety feature that makes it easier to call 911 in the U.S. and other emergency services abroad. Instead of fumbling with your iPhone's dialer, you can call someone for help in various ways — with or without your hands.

There's an iOS feature that benefits many users, but it's absolutely vital if you wear AirPods or other headphones models connected to your iPhone. A large number of iPhone users don't even know about it, especially since it's disabled by default and hidden deep in the system settings.

When life hands you lemons, make lemonade. At Magic Leap, the lemons are the COVID-19 pandemic, and the lemonade is a new solution for virtual meetings born out of social distancing.

Strange or uncomfortable encounters can be difficult to get away from sometimes if you're overly polite and don't want to hurt anybody's feelings. Thankfully, your iPhone can help save the day, providing you with a plausible excuse to exit the scene without having to conjure up some last-minute reason on the spot.

One of the most promising avenues of attack in a web application is the file upload. With results ranging from XSS to full-blown code execution, file uploads are an attractive target for hackers. There are usually restrictions in place that can make it challenging to execute an attack, but there are various techniques a hacker could use to beat file upload restrictions to get a shell.

You can feel it in your bones. You may die if you don't get this phone. There's just one problem — the price. Suddenly, you come across what seems like manna from heaven. That very device, at a deeply discounted rate, can be yours.

Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, it requires no special dependencies and can be run via SSH, making it easy to deploy remotely.

All fields of study have their own language. For people interested in learning about microbes, the language can sometimes be downright difficult — but it doesn't need to be. From antibiotics to xerophiles, we have you covered in an easy-to-understand glossary.

While iOS 11 is ready to take over your iPad, iPhone, and iPod touch, let's take a step back and check out all of the new features that iOS 10 brought to the public when it was released to everyone in Sept. 2016.

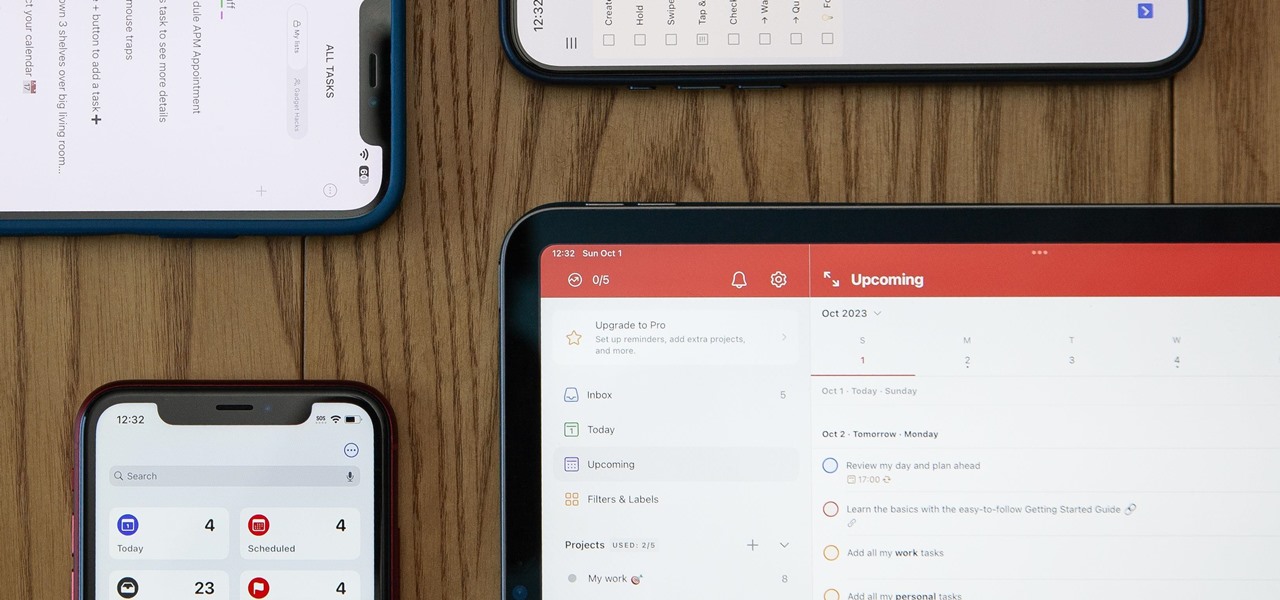
When you want a helpful task manager on your iPhone or iPad, any of the nine apps in this guide should be at the top of your list. But we'll review each app's features to help you determine which one might be best for your workflow.

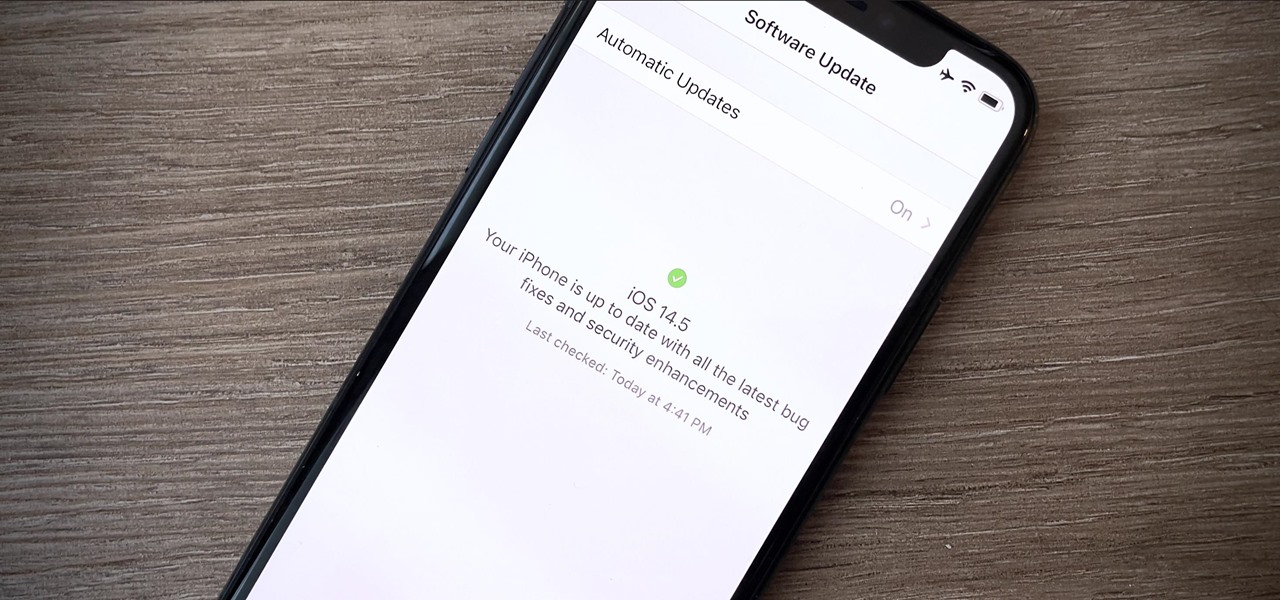
Apple's "Spring Loaded" event introduced us to many new and exciting products, including iMac and iPad Pro models with the M1 chip, an upgraded Apple TV 4K, a purple iPhone, and the long-awaited AirTag. However, one of the most anticipated announcements came in the form of a software update — the biggest update since iOS 14.0 and iPadOS 14.0 came out — and that's iOS 14.5 and iPadOS 14.5.

Your iPhone is full of features, many of which you might not even know about yet. Still, Apple keeps adding feature after feature with each new iOS update, and iOS 14.5 is no exception. The latest iOS version adds at least 69 features for your iPhone that you should be happy about.

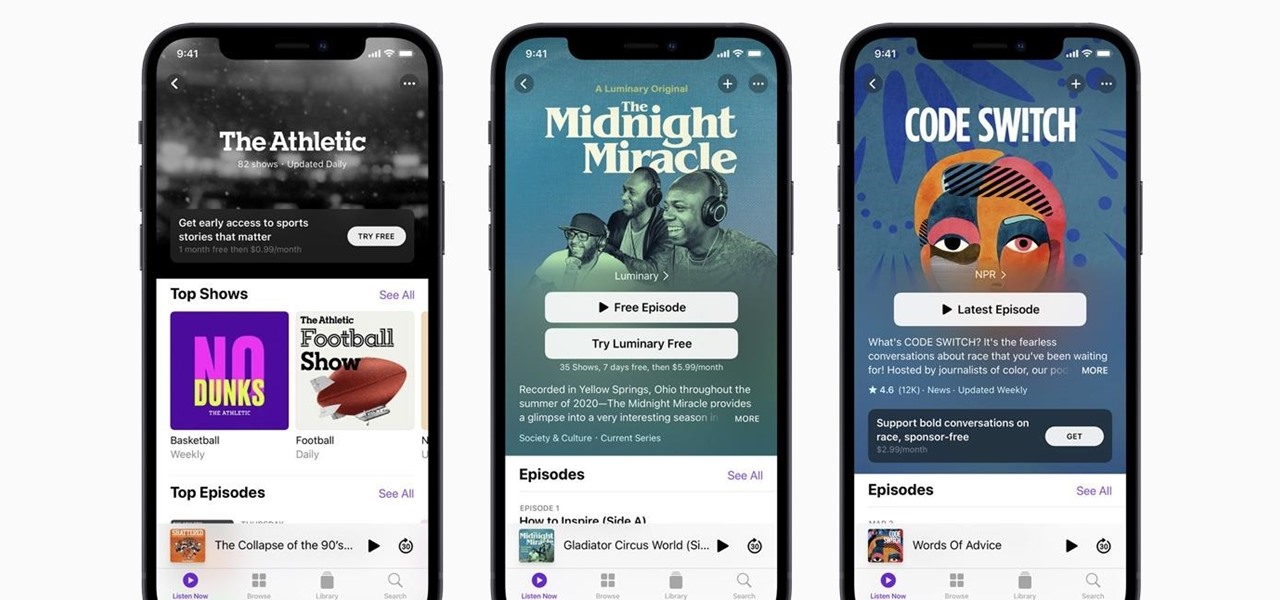
Apple's new iOS 14.5 will be coming out very soon, and that's even more evident now with the release of the iOS 14.5 Release Candidate (RC) on Tuesday, April 20. Anyone can install this update and get all of the same features iOS 14.5 will give everyone for iPhone; only you'll have a head start to using all of the updates in Maps, Music, Podcasts, Reminders, Shortcuts, Siri, and more.

A dead man's switch is a fairly simple concept. If you don't perform a specific task before a set amount of time, it'll perform a specific action you set. They can be handy not just for hackers but for everyone who wants to protect themselves, someone else, or something tangible or intangible from harm. While there are more nefarious uses for a dead man's switch, white hats can put one to good use.

The blue curacao gives this rum martini it's distinctive hue, and it's light, fruity flavor makes it a great summertime drink. Besides the curacao, you will need: 3/4 ounce rum, 1/2 ounce Midori, 1/4 ounce fresh lime juice, 1/4 ounce simple syrup, ginger beer and ice. Make a Turquoise Blue martini with rum and curacao.

The independent film Juno featured one of the most distinctive opening credit sequences in recent memory. It has a wonderful handmade look - which it turned out was created by hand! Whether you have seen Juno or not, Cow leader Simon Bonner shows a much easier way to create unique, handcrafted looks, without the pain.

Garam masala literally means a blend of hot spices. It's an integral part of most curries, acting as a distinctive seasoning. Many Indian households blend their own. Here we'll show you how to make your own- add a personal touch to your Indian cooking. Make garam masala (blend of hot spices).

Researchers at Northwestern University have hatched a robotic replica of the ghost knifefish, an amazing sea creature with a ribbon-like fin, capable of acrobatic agility in the water. The fish is distinctive in its ability to move forward, backward and vertically, but scientists didn't understand its vertical movement until the creation of its robot replica, GhostBot (shown below). They now know its vertical propulsion is caused by two waves moving in opposite directions, crashing into each ...

Janelle Monáe is simply in a class of her own. Genre-bending beats, distinctive fashion sense (à la the fabulous Grace Jones), and sweet dance moves to boot. Whether or not Monáe falls within your musical realm, you've gotta admit: the tiny five-foot-tall singer is chock full of infectious energy and exceptional talent.

Find out if there are local restrictions on color Before you fall in love with “Brilliant Blue”, “Gauche Green”, or any other paint color, check to see if any local authority restricts the colors you can use. This is especially important if you live in an historic area, newer subdivision, or townhouse community. It’s not uncommon to find a list of “approved” colors in these types of neighborhoods.

It's almost time for the new Xbox 360 dashboard to invade gamers everywhere. Microsoft expects to update the Xbox Live user interface sometime next month, which is said to be the most significant update to the dashboard since the NXE update three years ago. This new Metro-based update is meant to bring a unified and distinctive look across all of Microsoft's consumer products and services, including Windows Phone 7, Windows 8 and Zune.

Love this Rubik's Cube stamp with movable type Chinese characters by Shaun Chung. Chung laser-etched the characters from wood, and then adhered them to a regular Rubik's Cube to create verses from a traditional Chinese text.

Ni no Kuni is a gorgeous hand drawn and animated game coming to the PS3 and Nintendo DS. The story is about Oliver, a 13 year old who has lost his mother. Wishing for her to come back, a magical toy tells him that this might be possible and they set off on a journey in a parallel magical world. In the trailer above, the PS3 is able to almost match the visual quality of the cartoon animations originally made for cut scenes in the DS game.

Waiting for that first kiss can be an eternity.

Cinematographer Anna Foerster shot tests for Roland Emmerich's new period film "Anonymous". It's nice to actually see a test shot by a legit DP under controlled circumstances.

If you rely on WhatsApp as your messaging go-to, you're probably all too familiar with the default background in chats. While its distinctive look definitely sets it apart from other messaging apps, you're free to swap it out for something more appealing.

Sometimes strange things happen on the golf course, you are outdoors after all. In this video from the New York Times, PGA golf pro Bryan Jones offers advice on what to do in stranger circumstances.

If you’re so smart, why aren’t you rich? Although money and mental muscles may seem a natural match, brains, alas, may be more hindrance than help when it comes to getting rich, concludes a new study in the journal Intelligence.”It is still not well understood why some people are rich and others are poor,” writes study author Jay Zagorsky of Ohio State University. “Luck, timing, parents, choice of spouse and many other factors play important roles in shaping an individual’s circumstances,” he...