
How To: Make Dry Ice at Home Using a CO2 Fire Extinguisher
Here's how to make dry-ice at home, or wherever you feel like it! All you need is a pillow case, and a CO2 fire extinguisher.


Here's how to make dry-ice at home, or wherever you feel like it! All you need is a pillow case, and a CO2 fire extinguisher.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.
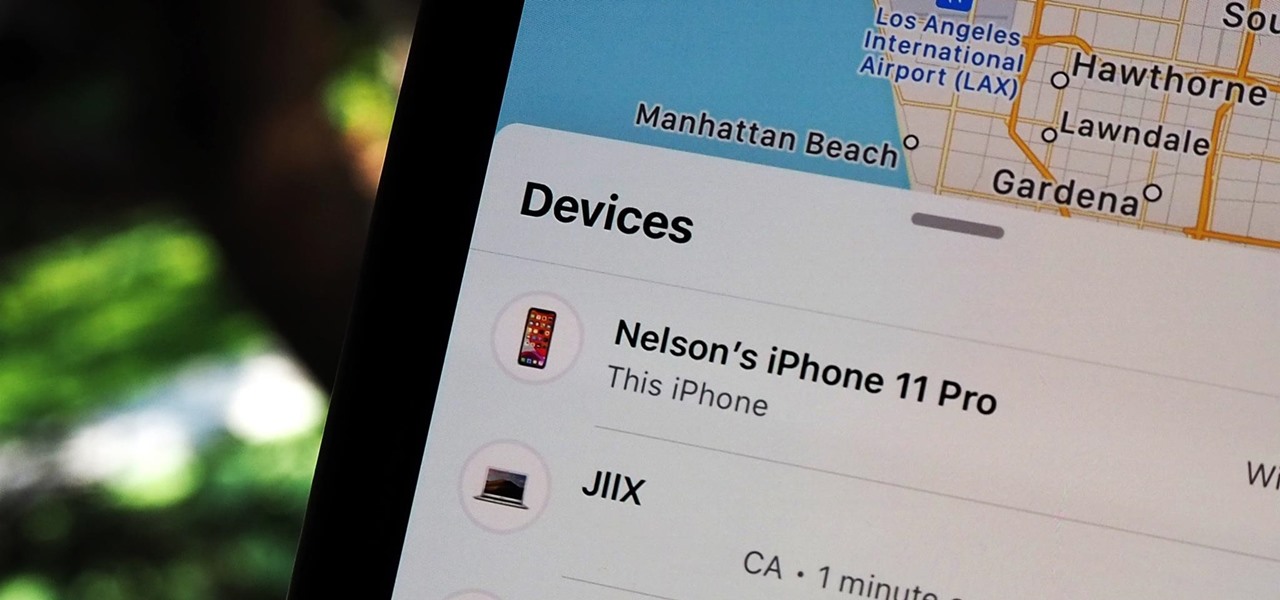
You might be giving out your name to every stranger you see, and you don't even know it. That iPhone of yours has a name — generally a combination of your first name and device model — and it broadcasts it to others via AirDrop, Personal Hotspot, Bluetooth, Wi-Fi, and other connections. Sure, it's useful to keep your device name simple and to the point, but there are upsides to changing it.

A little-known setting on your iPhone gives you the power to change the color of certain contact names and email addresses when drafting an email. Customizing the color works well for visually separating contacts at a glance, and it can even help you from sending an email to the wrong person.

The march to the mainstreaming of augmented reality can sometimes seem slow, but this week things picked up in earnest.

One fight for augmented reality branding that we thought had been settled has suddenly turned into a full-fledged legal battle—again.
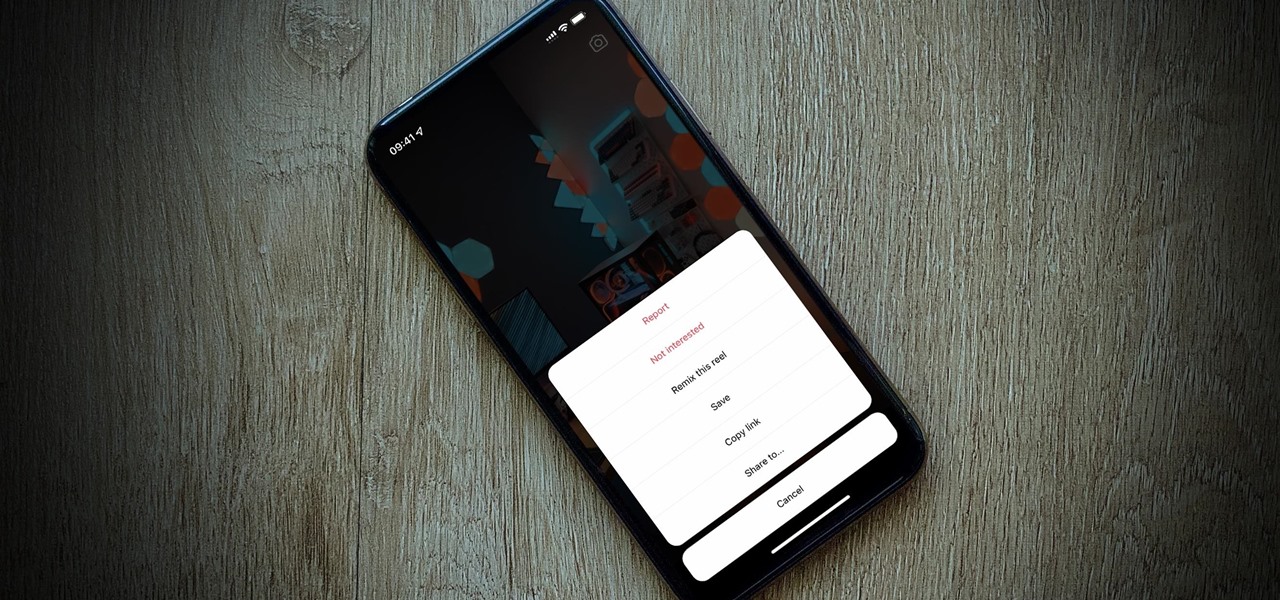
So, you're trying to show a friend or two a hilarious Reel you liked or saved on Instagram, but where is it? Unlike TikTok, Instagram doesn't make it clear where you're supposed to find your liked and saved Reels. Luckily, we can help.

When Apple acquired the popular Workflow app in 2017, many were worried that it would either get replaced with something much worse, or just disappear entirely. Thankfully, Apple put these concerns to rest with the launch of Shortcuts. In iOS 13, Shortcuts is becoming more powerful than ever, providing functionality on the iPhone that the original Workflow team could only dream of.

Apple Card has generated quite the buzz since its March 2019 announcement. The iPhone maker's new credit card pairs with Apple Wallet on your device, is simple to sign up for, includes enhanced security over other cards, has zero fees, and provides daily rewards right to your Apple Cash account. And as good as that sounds, the fine print can complicate things real quick.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.
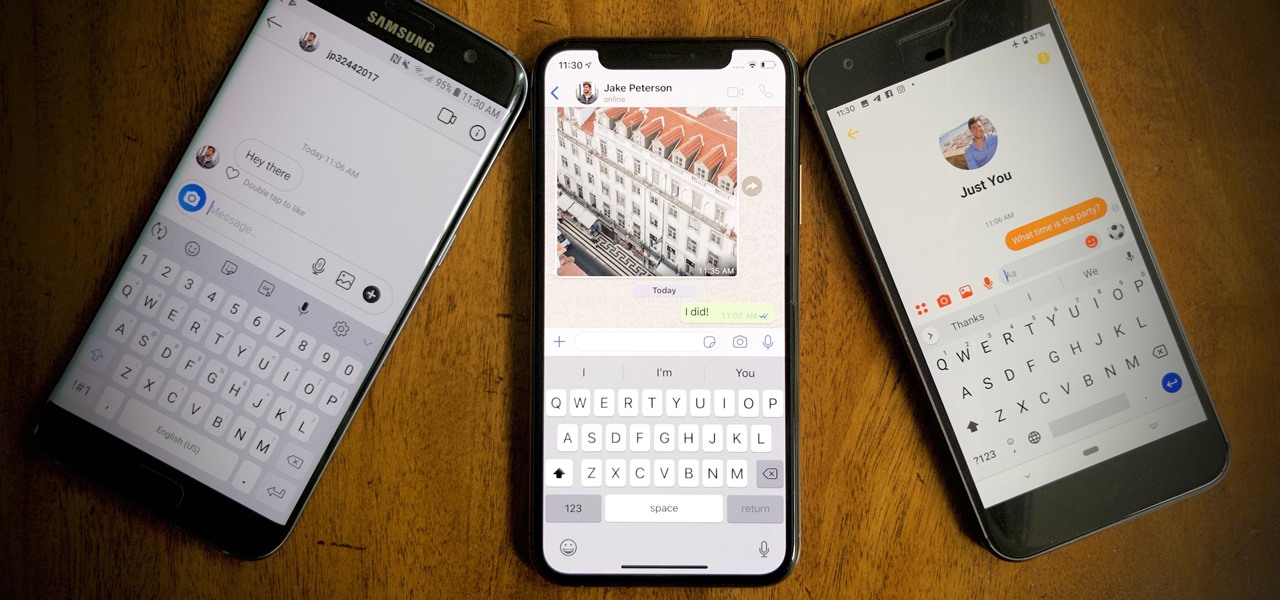
You're in constant communication with your friends and family. The only issue? Nobody uses the same app. Messenger, Instagram, WhatsApp — you have contacts spanning all three, and the resulting balancing-act to keep in touch can be overwhelming. That's why Facebook — who owns all three apps — is coming out with a way to call and message friends across all three platforms from one place.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something.

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

My years in the restaurant business have taught me many things. Some of those things are best left unsaid and other things require a PhD in vulgarity, but the one thing I learned that I keep coming back to night after night is that you do not have to spend a lot of money to drink excellent wine. This is especially true of champagne...I'm sorry, sparkling wines.

You can find chili peppers in practically every cuisine. From the sweet Italian variety to the spicy Thai bird's chili and the smoky Mexican chipotle, peppers are ubiquitous and universally loved. But if you find the range and scope of these little fireballs overwhelming, you're not alone.

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

Tea has been around for thousands of years, and as a result, tons of customs and ceremonies have sprung up around its consumption. Some cultures take their tea plain, while others put things in it. Sometimes there are special tea-holding vessels, other times not. Maybe there will even be special foods meant to be eaten with tea. However, in America, our appreciation of tea has waned. For many, iced tea is their biggest source of tea consumption, and it's imbibed with no ceremony whatsoever in...

Using different sounds on your iPhone for different notifications can help you determine — just by listening — alerts you may want to look at immediately versus untimely alerts or even ones you typically ignore. But Apple has never given us complete control over notification sound customization on iOS, though the latest iOS update is a step in the right direction.

Apple does not provide a native way to lock apps on your iPhone behind Face ID, Touch ID, or your passcode. For a long time, we've wanted that option for improved privacy and security, but Apple does allow developers to use its authentication protocols. Apps like Messenger, Outlook, and WhatsApp give the option to lock them down, but for the apps that don't, you can force it with a little time and effort.

Google has added a flurry of new features to its YouTube Music recently to prepare it to replace Google Play Music, which will be sent to live on a farm with Google Reader, Inbox by Gmail, and other sunsetted Google products by the end of the year.

People fundamentally distrust magicians. And they should. The illusions they proffer are just that, illusions meant to astound rather than tangible interactions and results that have weight and meaning in our real world. Our lizard brains know this, and, no matter what the outstanding feat of "magic" presented, we nevertheless hold fast to our survival-based grip on the truth: we just saw simply "can't be real."
Apple's iOS 13 for iPhone includes new features in Safari that make browsing the web a little bit better when compared to iOS 12. Some changes are small while others add functionality that just wasn't there before. Plus, there are more security enhancements.
After poor sales of the Pixel 3 and Pixel 3 XL, Google needs to reinvigorate its Pixel lineup, devices it's been pushing heavily over the last couple years. On May 7, Google had the eyes and ears of the technology industry at its Google I/O keynote, making it the perfect time to announce new devices that would attract a different crowd of users. Meet the Pixel 3a and 3a XL.

The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each type of packet. The pattern of these colors can also allow us to fingerprint the tool being used to attack the network.

The transcribing app can be an invaluable tool, especially if you're a student or are in a profession that relies on audio journals or interviews. These apps can convert important recordings like lectures and meetings into text for you to carefully read through to better comprehend.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

TouchWiz might not be the Android skin of choice for hardcore aficionados, but the Galaxy's OS still has a ton of great features up its sleeve that help provide one of the most enjoyable smartphone experiences out there. Many of these are relatively hidden and overlooked features that you may not be aware of.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

They're finally here — Samsung has officially revealed the Galaxy S9 and S9+, which run Android Oreo out of the box. Since we've spent plenty of time with the Oreo beta for the Galaxy S8, we already know about some of the best new software features coming to the Galaxy S9. Like previous updates, Samsung has enhanced its software with a fresh look and brand new functionality.

There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distribution which can be easily weaponized with the Black Arch expansion, creating a friendlier first-time Arch experience.

Samsung has finally rolled out the Android Oreo update for the Galaxy S8 and S8+. If you're just now getting the update, you'll be happy to know that your Galaxy just got upgraded with plenty of cool new features. Like previous updates, Samsung has improved upon its software by including a new look and new functionality.

When shopping for a new smartphone, you'll encounter comparisons and spec sheets that are filled to the brim with values like mAh, GB, and GHz. To the average consumer, however, these values are meaningless, so we end up looking at which device has the specs with the highest actual numbers.

Whether scheduling meetings, events, tasks, or even keeping tabs on the weather, a good digital calendar can help you stay on top of your game in ways that a normal calendar could never do. Indeed, there are many calendars to choose from, but Google Calendar is one of the best due to Google's excellent cloud service, feature-rich web-client, and their easy-to-use Android and iOS applications.

It's super easy to add filters, adjust levels, and crop images using the default photo editor on your smartphone, but there's rarely any built-in tool for removing the background in a photo. A third-party app can help isolate people and objects in your pictures, and we've found a free one that's easy to use, works with high-resolution images, and is available for Android, iOS, iPadOS, and the web.

The beginning of autumn has delivered a number of new augmented reality developments, and we're on top of it.

After the dust settled from Apple's annual iPhone event, there's not a lot to get hyped up about the iPhone 13 lineup, particularly if you upgraded your smartphone last year.

Apple wants to support the advertising economy, but its primary focus of late has been user privacy and security. In Safari, cross-site tracking, which lets content providers track you across websites and apps to show you more targeted ads, is disabled by default. However, content providers can get around that using less privacy-invasive ad measurements, but you can stop that too in iOS 14.5.