
How To: Pot a spiral topiary for outdoor or indoor use
The art of floral arrangement is a fun and valuable skill. Dana Plazyk of Flowers by Design lends useful tips and tricks on making simple flower arrangements.


The art of floral arrangement is a fun and valuable skill. Dana Plazyk of Flowers by Design lends useful tips and tricks on making simple flower arrangements.

The art of floral arrangement is a fun and valuable skill. Dana Plazyk of Flowers by Design lends useful tips and tricks on making simple flower arrangements.

The art of floral arrangement is a fun and valuable skill. Dana Plazyk of Flowers by Design lends useful tips and tricks on making simple flower arrangements.

The art of floral arrangement is a fun and valuable skill. Dana Plazyk of Flowers by Design lends useful tips and tricks on making simple flower arrangements.

The art of floral arrangement is a fun and valuable skill. Dana Plazyk of Flowers by Design lends useful tips and tricks on making simple flower arrangements.

The art of floral arrangement is a fun and valuable skill. Dana Plazyk of Flowers by Design lends useful tips and tricks on making simple flower arrangements.

The art of floral arrangement is a fun and valuable skill. Dana Plazyk of Flowers by Design lends useful tips and tricks on making simple flower arrangements.

The art of floral arrangement is a fun & valuable skill. Dana Plazyk lends useful tips and tricks on making simple flower arrangements.

August is a time when it is common to see bats flying overhead while taking an evening stroll or night fishing at your favorite spot. The two most common bats in Ohio are the little brown and the big brown bats and both are found in rural and urban settings. Bats serve a valuable purpose for humans because they feed on insects, including mosquitoes and those which plague farmers’ crops. However, bats sometimes create roosts, or gathering places, in people’s homes. Join Wild Ohio’s Donna Danie...

Learn how to distribute in simple algebraic expressions to help solve those mathematical equations.
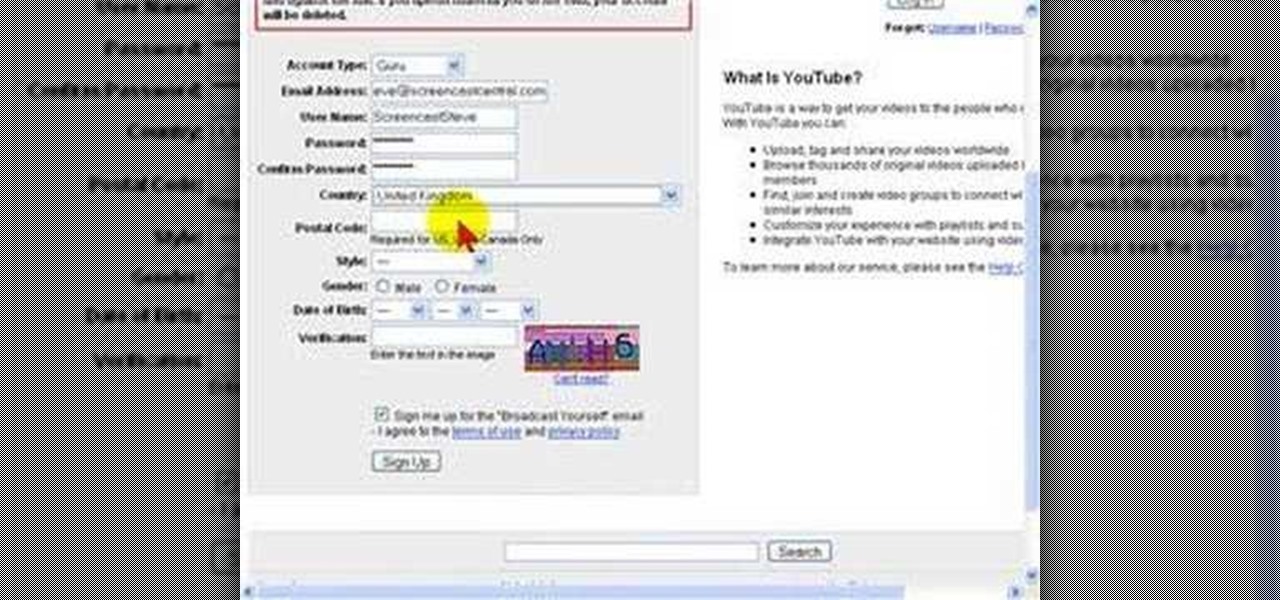
YouTube is the latest craze to hit the web, allowing users to upload and distribute their own videos. YouTube now boasts more than 100 Million Video Views per day.
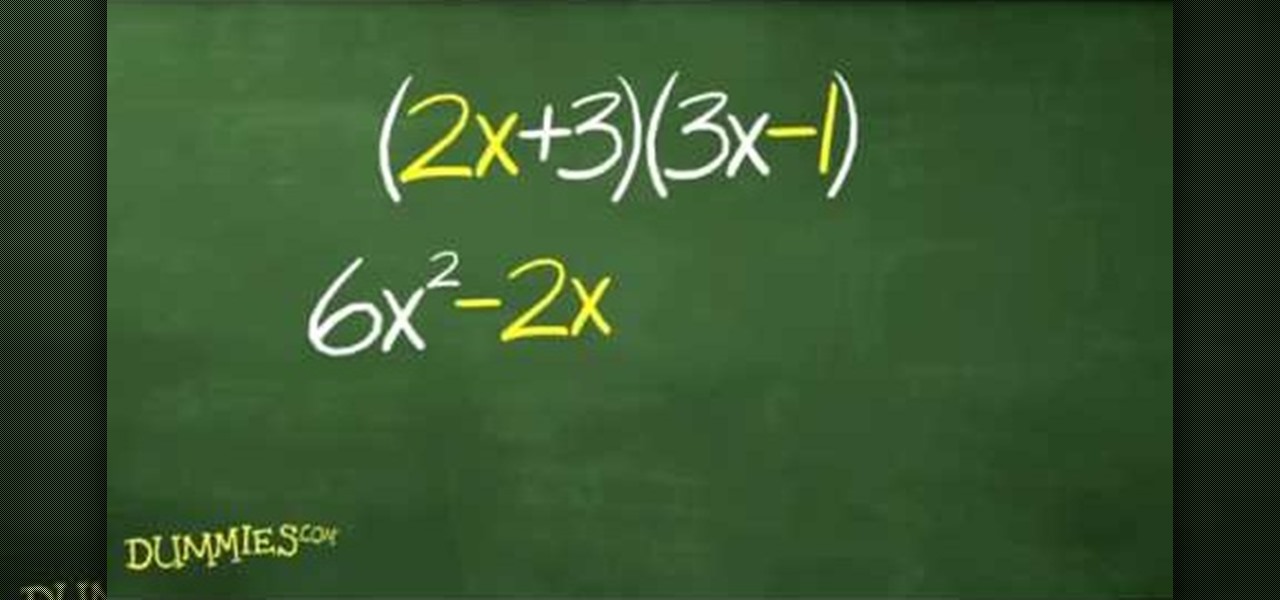
Learn how to use the FOIL method to distribute two binomial expressions in algebra. The FOIL method — which stands for first, outer, inner, and last — takes two binomials and multiplies them for a single quadratic equation. Solving for binomials with FOIL takes just a few steps. Could you use a little help figuring out how to divide fractions? Watch this free video lesson. From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have b...

Tax season is always stressful, especially for entrepreneurs and small business owners. Rather than wait until March to get your finances in order every year, learning how to keep track of your expenses is a valuable skill that saves you and your business time, money, and plenty of anxiety.

If you ever had trouble trying to properly write a research paper then this quirky, 1950's style filmstrip movie will break it down for you, even if you're a dummy. The Oscar-worthy performances in this movie will help teach you valuable lessons when it comes to preparing and working on a research paper. The narrator in the movie will give you essential tips and strategies to guide you in the research paper writing process. The key things the movie will share with you are: (1) Choosing a topi...

Ramen noodles don't have to be just plain old noodles. Cheap meals don't have to taste cheap. Take Ramen noodles to the next level with some green onions, mushrooms, red bell peppers and more. Check out this video tutorial to learn how to rock out and make ramen noodle stir fry.
MAKE and Collin Cunningham brings the do-it-yourself mindset to all the technology in your life. Make Magazine celebrates your right to tweak, hack, and bend any technology to your own will.

The come command is the most valuable training tool for your dog. Learn the importance of dog training and how to get your dog to come with this free dog training video series.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

EXPAND YOUR VISION: So many people don't achieve their goals and dreams in life because they don't have a big enough vision for themselves. The biggest enemy lies within. Picture and see yourself achieving your goals, becoming financially independent, making yourself more valuable to the market place, or losing that excess weight that you have always wanted to lose.
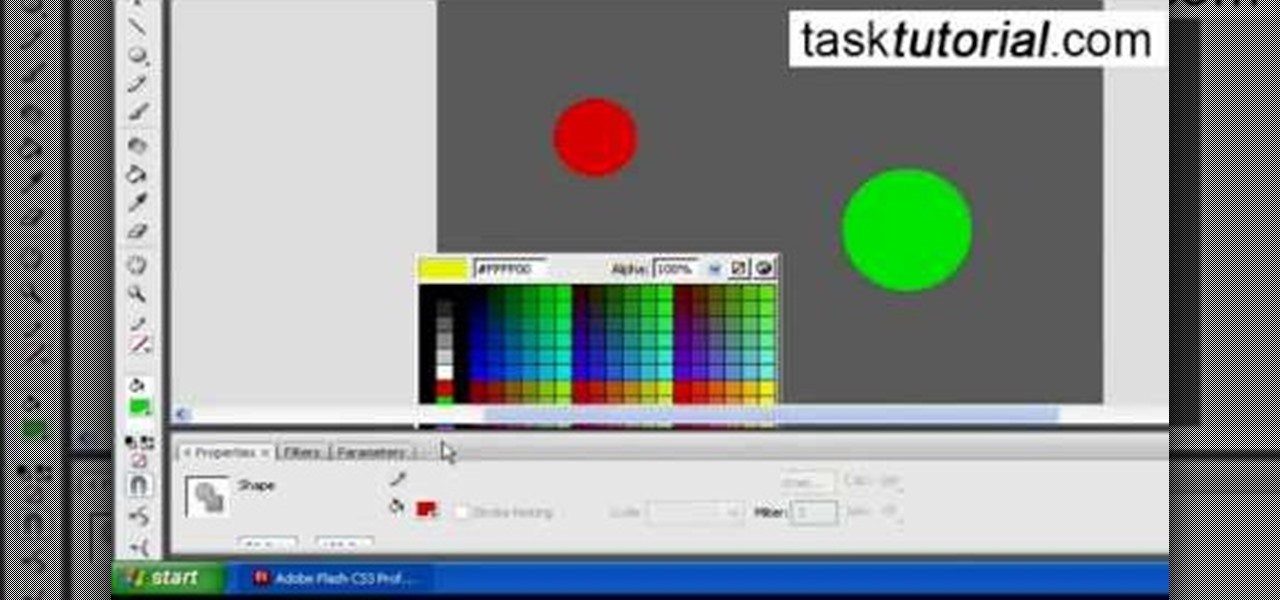
Tasktutorial.com shows us how to create drag and drop functionality into a flash program. Start off by making a few shapes in flash and then add color to each of them, a different one for each shape in order to differentiate between them. After doing this select all the shapes by dragging the cursor over them, once done distribute the shapes into layers by going into the 'modify' drop-down button at the top, then timeline and there will be the option to distribute. Now we have to turn the sha...

The latest business move by Magic Leap could result in a significant boost to its spatial computing platform's performance and headset design.
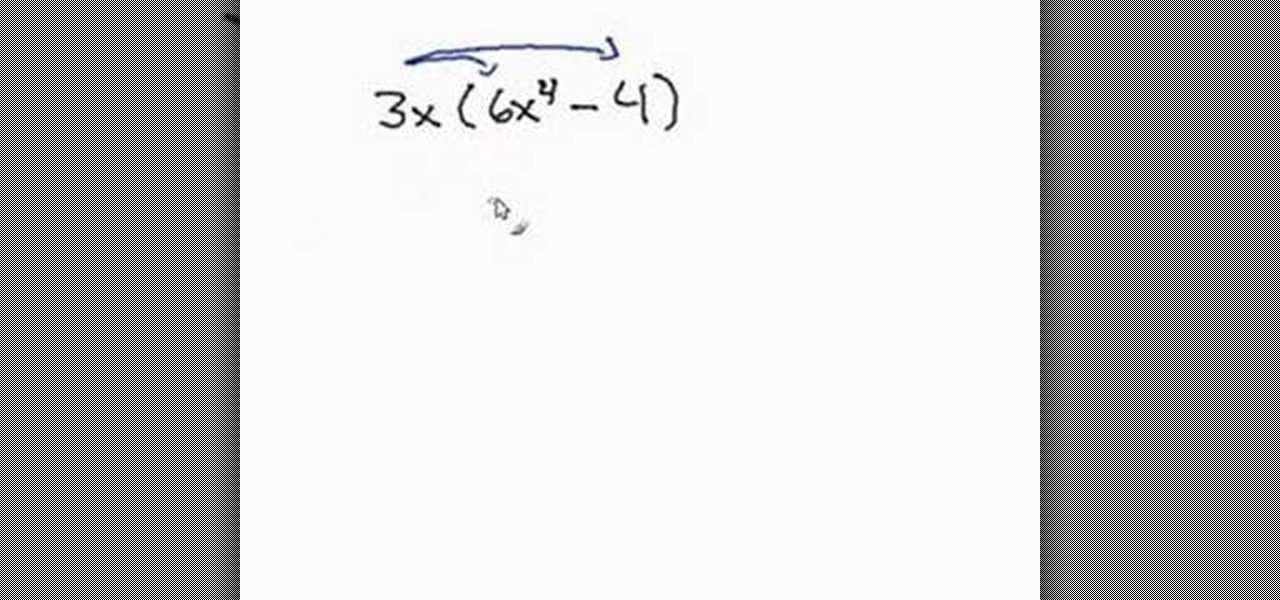
The distributive property is a very important factor to consider in math and may save you a lot of trouble on your math homework. For values which lie right outside parentheses, you will need to distribute this value across the contents of whatever is inside the parentheses. You will need to multiply the value outside of the parentheses by first the first term inside the parentheses and then by the following terms inside the parentheses, distributing the value across all the terms found insid...

Confused by TikTok? Trying to grow your Instagram fanbase? Aiming to create the perfect Facebook ad? Growing an audience might be challenging, but with the right strategies, it is possible — and fun.

We've already highlighted the importance of learning Microsoft Excel from a hacker's standpoint, but it's also just a good skill to have as you'll likely come across the number-crunching powerhouse at school and work, as well as in other areas of your life, such as budgeting.

Demand for Tesla's driverless features as well as its ultra-long battery ranges and a reputation for offering the best-in-class electric car driving experience helped Tesla see a 32% surge in its value as a brand, topping out at $5.9 billion in the BrandZ Top 100 Most Valuable Global Brands study, released June 5.

Chopping veggies is pretty straightforward: grab the right knife and start slicing. Nothing to it! However, the way you cut your food does affect the length of time it takes to cook, as well as how evenly it cooks. So the next time you need to get your vegetable from hard and crunchy to perfectly soft in mere minutes, give the oblique cut a try.

The Null Byte community is all about learning white hat hacking skills. In part, this is because I believe that hacking skills will become the most valuable and important skill set of the 21st century.

Nowadays, protecting your valuables can be challenging especially when you're on the go. That's why I decided to make a little secret compartment inside my car. Only you'll know it's there because nobody will be able to find it. Not only that, but you'll have easy access to it. It's fairly cheap and the total cost was under $5.00. Let me show you how to make it. You can watch the video or scroll down below for the written guide.

Robert Templeman from the Naval Surface Warfare Center in Crane, Indiana and several of his friends from Indiana University recently developed an Android application that is capable of gathering pictures and videos from mobile devices in order to reconstruct a user's environment in 3D. The malware would come coded inside of a camera application that the user would download. The malware, called PlaceRaider, would then randomly take pictures throughout the day and carefully piece them together ...

Is it time for your planned hiking adventure? Hiking is great, but mountain hiking, through the brush and rocks, is even better. Going for a hike in the mountains can be exhilarating, but it also has its dangers. Make sure you pack for the occasion.
Vimeo is a fantastic way of distributing your video on the internet and making it accessible for people to watch. Watch this tutorial and learn how to use Final Cut Pro to prepare your completed video for compression and export to Vimeo.

If you've already finished your movie and are ready to start distributing it, you're going to want to include a really awesome intro. Here's how you can use the iDVD program to create your own really cool DVD intro sequence.

Ribbons are really kind of a hot commodity, believe it or not, because they're actually quite trick to make. But knowing how to make some ribbons could make you very valuable and you could implement them into your own designs. Watch this Illustrator video tutorial to work with vector ribbons. Learn how to create a smooth silver ribbon with multiple folds. It is entirely vector and very versatile. This one gets a little complicated, so prep yourself to be frustrated at first glance, but once y...

Get an inside on how to build a home server that hosts all of your DVDs and movie content.

The Nessus vulnerability scanner, is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an entire enterprise, inside DMZs, and across physically separate networks. In this network security video tutorial, you'll learn how to hack a network using Nessus 3.
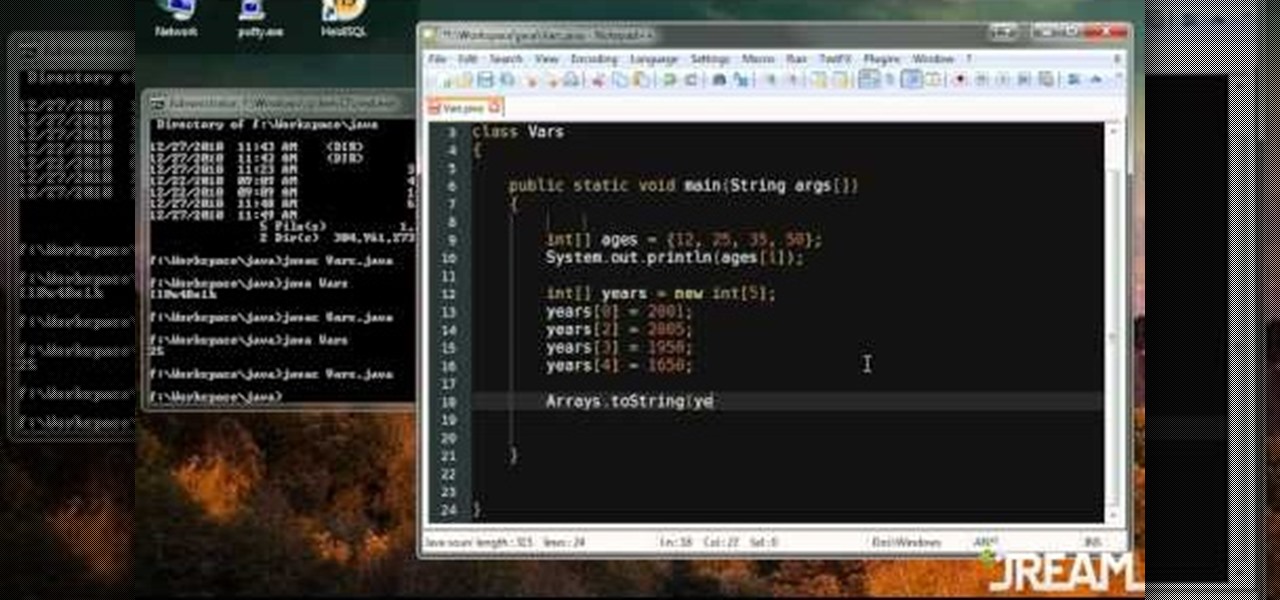
Arrays are little pockets of data distributed throughout your program. They're useful because having arrays keeps you from needing to work with hundreds of variables when programming. This specific tutorial shows you how to work with arrays when you're using Java to program.

This a super cute puzzle solving game available on Xbox Live Arcade! This tutorial shows you how you can gather up all the multiplayer eggs that are distributed throughout the various levels of Ilomilo. Make sure you find them all!

It's not just about putting a pile of TNT together and lighting the fuse, it's about focusing your munitions in a specific area and then strategicially distributing other packs around the epicenter. This creates a giant explosion which can leave a significant crater behind.

This video starts off by showing you how to complete this quest. Start in one of the casinos, and distribute four cards to different NPCs you can find on the Strip. The benefit of thsi quest is that it gets you more money!

When it comes to staying safe, we all know that dish detergents, spray cleaners, and any sort of bleaching cleaners are bad for our health, since they distribute potentially cancer-causing toxins into the air.