For a rich, tender and juicy pork chop, try grilling it with pineapple. This cooking how-to video is part of Paula's Home Cooking show hosted by Jamie Deen, Paula Deen. Paula Deen, owner of Lady and Sons, a famous Savannah restaurant, is Food Network's resident southern chef. Step inside her kitchen and discover delicious food that's both uncomplicated and comforting. Watch as she grills up pork chops and pineapple for a sweet and salty meal.

A tutorial showing how to set up a free dynamic DNS address with DynDNS.org and configuring the home router/firewall to forward traffic to your webserver.

This is the second episode of Full Disclosure by InfinityExists.com. This episode includes how to crack WEP encryption, and why it can be cracked so easily.
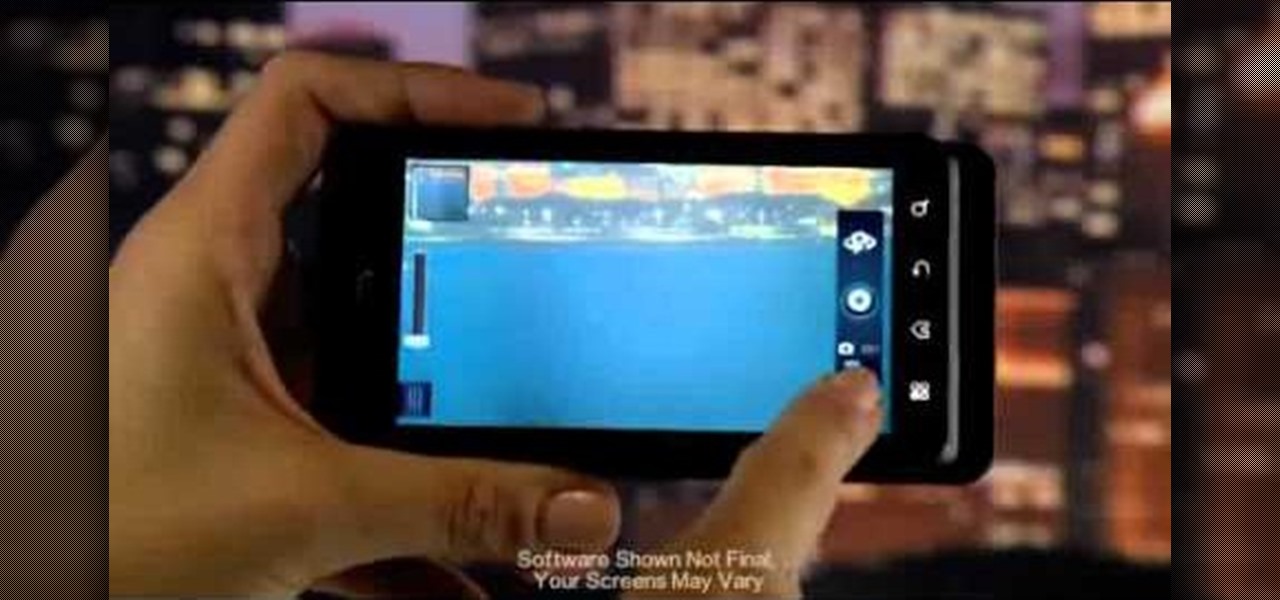
The Droid 3 smartphone from Verizon has a great camera perfect for taking beautiful photos. If you want to learn how to perfect your on-the-go photography, take a look at this tutorial from Verizon Wireless that features instructions on all the different settings in the Camera app on the Android device.

Nike Bootcamp brings you this soccer training video. Learn how to Go Long with this pro soccer drill. It’s that laser-guided pass in the dying seconds of a game that can make the difference between ninety deadlocked minutes and three vital points. Watch Klaas Jan Huntelaar’s masterclass in grasscutting distribution and you’ll soon learn one of Nike Bootcamp’s most valuable lessons: master Go Long, and you’ll go far. Brush up on those soccer drills with this soccer training video from Nike Boo...

One of the best features of Apple's Final Cut Studio is the disc designing feature DVD Studio Pro. With its ability to create high-end DVD masters, you can easily make discs for your indie film, or maybe even a professional movie. DVD Studio Pro is tightly integrated with Final Cut Pro and Motion, rendering the projects into DVD format without encoding to intermediary formats.

In this video we learn how to do a heelside pendulum in snowboarding. Start by sideslipping on your heal edge. Then, tap on one leg to increase pressure on that foot. Reduce the angle and then you can slide your board down where you are facing. Look and point in the direction of desired travel. Tapping on both legs means even pressure distribution on both feet. Increase edge angle with even pressure on both feet to slow down and stop. Although you will start out slow at first, these are great...

In this video the instructor shows how to check if your computer has a home group setup or setup one if required. Home group is Microsoft's new way of making networking easier with computers. They allow you to share documents, pictures, videos and all kinds of media between computers that are a part of a home group. Go to the start menu and go to Control Panel. In the Control Panel select the Network and Internet link. Now in the Network and Internet window select the Home group. In this page...

Windows 7 is the hot, new operating system replacing the past XP and Vista systems. Windows 7 is the most simplified, user-friendly version that Microsoft has developed - ever. Get acquainted with your new version of Windows straight from Microsoft.

Mike Lively of Northern Kentucky University shows you how to create a light switch in Second Life with scripting. Part 1 demonstrates how to create a prim switch which turns on (brightens) a prim in Second Life. Part 2 goes through the Light Switch code line-by-line and adds a rotor to the light switch. The code is provided for free distribution on Google Code at

In this tutorial, Mike Lively of Northern Kentucky University gets you started in getting the Adobe Air Content Management System up and going.

Having problems unwrapping in Autodesk 3ds Max? Don't worry—this video tutorial will show you what you need to know about unwrapping UVs for organic models. It's a complete unwrapping session in two videos (so make sure to watch both parts). You'll learn some of the common problems encountered, as well as things like pelt mapping, relaxing UVs and pixel distribution. If you just happen to master these techniques, maybe it's time to check out RoadKill, a great UV tool.

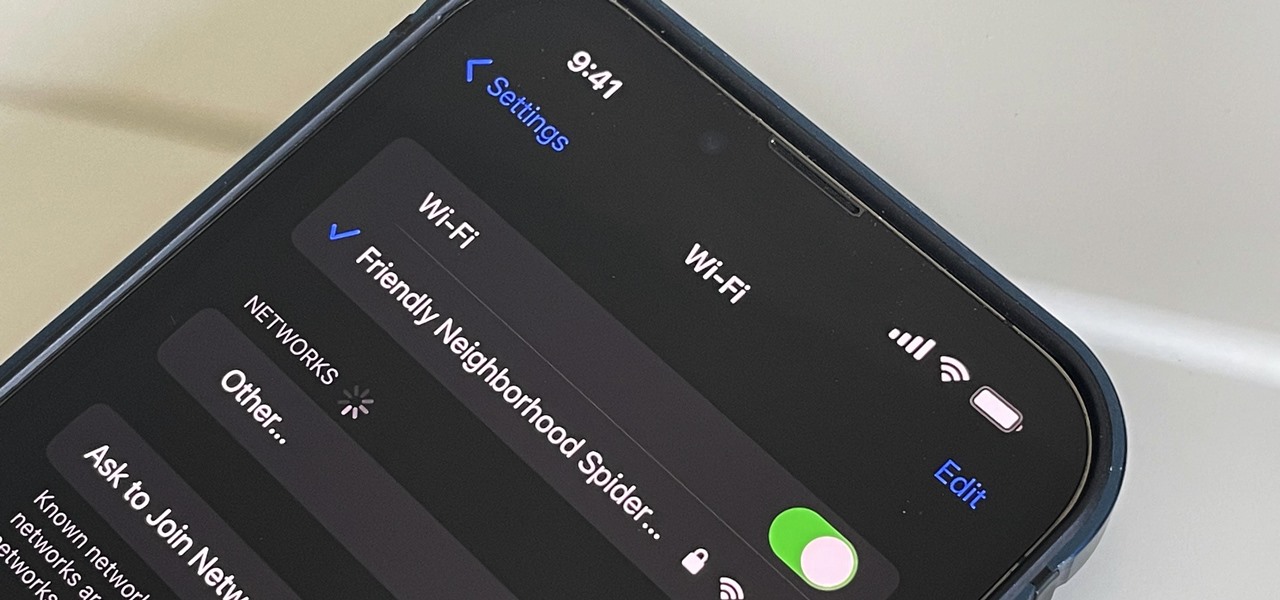
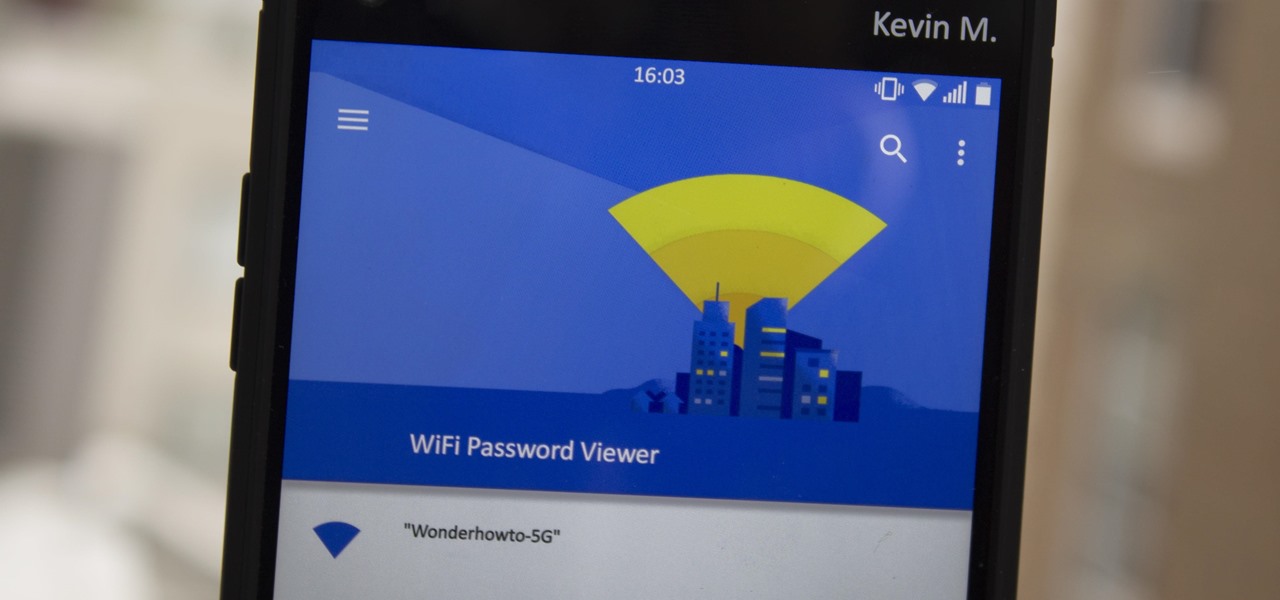
For years, Android has provided easy ways to view all the Wi-Fi networks you connected to in the past, and you can even see the saved passwords in plain text. With iOS 16, Apple finally gave us a similar way to view saved Wi-Fi hotspots, copy their passwords, and remove old ones without being near their access points.

When you look at the top corner of your phone, what do you see? Upon upgrading to Android 11 or iOS 14, you'll see either "5G," "5G+," or "5G E" if you're connected to the right network. But what exactly do these symbols mean? They indicate not only if you're using 5G, but also what type you're connected to.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

For the most part, Google Wifi and Nest Wifi systems take care of themselves. But there are still a few manual features that might come in handy, like being able to check on network activity to see which devices are using the most bandwidth when your connection gets bogged down.

Google recently released a new mesh router known as Nest Wifi. The updated and rebranded Google Wifi brought many improvements, such as faster processing power and an increased level of wireless security called WPA3. But while it's not enabled by default, you can still get the new WPA3 security on your original Google Wifi.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

When Pokémon GO developer Niantic launches its Real World Platform for augmented reality gaming, it will run over 5G speeds courtesy of T-Mobile parent company Deutsche Telekom and the edge servers of its MobiledgeX subsidiary, the companies announced today.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

5G is showing up more and more in the news, as an increasing number of companies jump on the bandwagon. AT&T made a splash earlier this year with their embarrassing "5G Evolution" debacle, and the other three major wireless carriers soon followed suit, detailing their own vague plans for 5G. Today we find another company has joined the fray, just not a cellular one — Apple has officially been approved to test 5G networks.

Have you ever gone to a friend's house and not asked for the Wi-Fi password? Probably not, and the same can likely be said of any friends that come over to your place. But the actual act of sharing Wi-Fi passwords is still incredibly clunky, and it's particularly hard if you have a nice and secure password with uppercase and lowercase letters, numbers, and symbols.

Even though your phone has a built-in media player, it's got nothing on VLC. The popular third-party video player supports virtually every codec and file format, and even better, you can use it to stream movies, shows, and other video files from your computer to your phone.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. government agencies and officials could have been compromised over the last three years.

After I traded in my Samsung Galaxy S5 for an iPhone 5S, the one feature I truly missed was the Smart Remote app. My television remote was broken and the S5 saved me from, you know, actually having to get up and change the channel.

Thanks to Verizon Wireless, I pay over $220 a month for my phone bill. It's just me on the plan—no family members, and it's not even unlimited data. So, when I receive that data alert message telling me that I've used up 90% of my plan and that I've still got a few more week until my billing cycle starts over, you know that I'm left scrambling to connect to some Wi-Fi.

If you work at a large office or have a multi-story home, you're probably familiar with Wi-Fi range extenders. Since one hotspot isn't always enough to cover an entire area, Wi-Fi repeaters are generally set up in larger areas to capture and rebroadcast the original signal.

When people first learn that their Android device is capable of dual-booting different operating systems, e.g. Linux, they almost universally respond with, "That's so cool." And for those of us ambitious enough to actually try one out, we are typically filled with glee as we see Ubuntu, or something similar, boot up for the first time on our tablet or phone.

One thing I absolutely cannot stand is lag when I'm gaming. Every time I'm about to beat my killstreak record on Call of Duty, my internet connection drops and I'm a goner. It never fails. This usually happens because someone else on my Wi-Fi is streaming a movie or downloading a huge file.

If you're spending hours on your phone playing games like Angry Birds and Candy Crush Saga, or posting online to Google+ and Pinterest, you're probably being spied on. The latest releases from NSA whistle blower Edward Snowden reveal that the National Security Agency, and its UK counterpart, GCHQ, are mining the ad networks utilized in these apps to collect a trove of information on you.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

Welcome back, my fledgling hackers! Nearly every commercial enterprise worth hacking has an intrusion detection system (IDS). These network intrusion detection systems are designed to detect any malicious activity on the network. That means you!

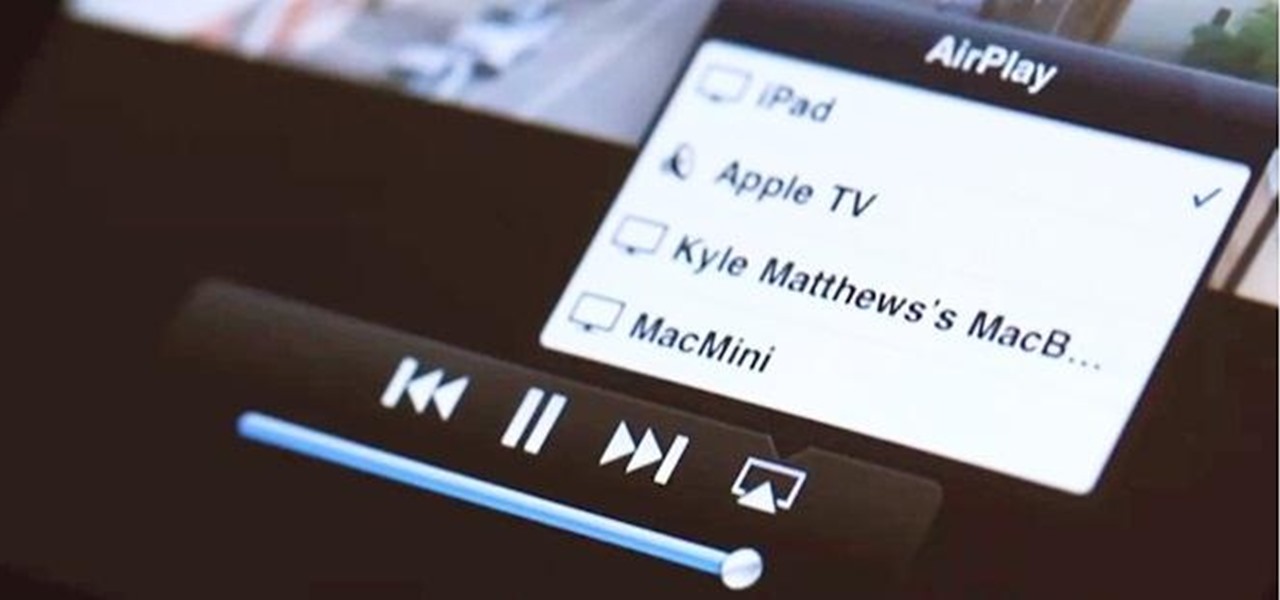
AirPlay is probably one of the most underutilized features in Apple products. It allows users to wirelessly stream photos, music, or video directly from their iPad, iPhone, iPod touch or Mac to their Apple TV or AirPlay-supported speakers. The Apple support page has a complete list of all the supported and needed devices. Mirroring is also available, but only for the iPhone 4S, iPhone 5, and iPad 2, all of which need to be running iOS 5 or later.

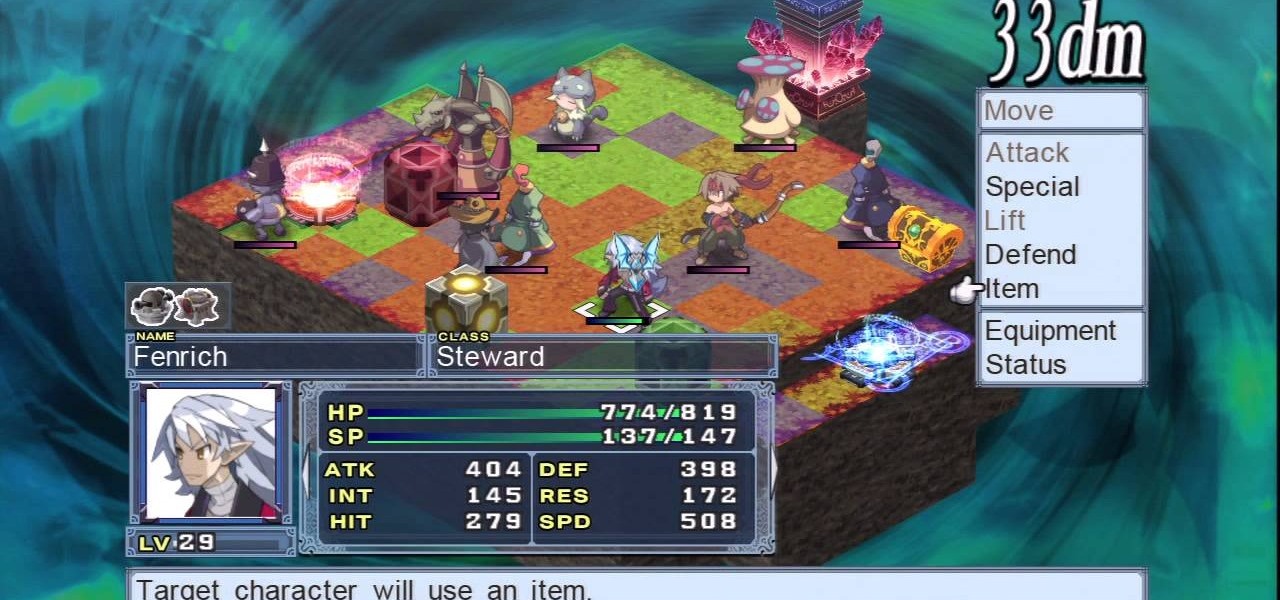
After beating chapter 2 in Disagaea 4, the Cabinet feature for multiplayer unlocks. This allows you to interact with other Disgaea 4 Playstation Network players within the game. This guide overviews the functionality of the Cabinet, as well as how to use the Red Cell Phones in game to call upon other player's characters.

The 'Light My Fire' Dead Island accomplishment exists as both an Xbox 360 achievement and a trophy on the Playstation Network. You will need to "collect" a ton of zombies into a group so that you can burn them all down with a single molotov cocktail weapon to unlock either the trophy or the achievement.

If you just brought home a Windows 7 notebook or desktop PC, but you can't figure out how to configure the WiFi connection to get internet on it, take a look at this guide to learn how to connect your Windows 7 computer to a home network.