In this video they are teaching about "How to connect XBox 360 to computer for wireless internet". For all this we have to have a laptop or a computer. And it also needs an Ethernet cable. It will be portable both for computer and laptop. Connect the Ethernet cable both to the laptop and XBox. After connecting that switches on the XBox, go to the network connections in laptop and advance the settings there. Switch on the XBox and see if its showing connected. If it does not show just go to th...
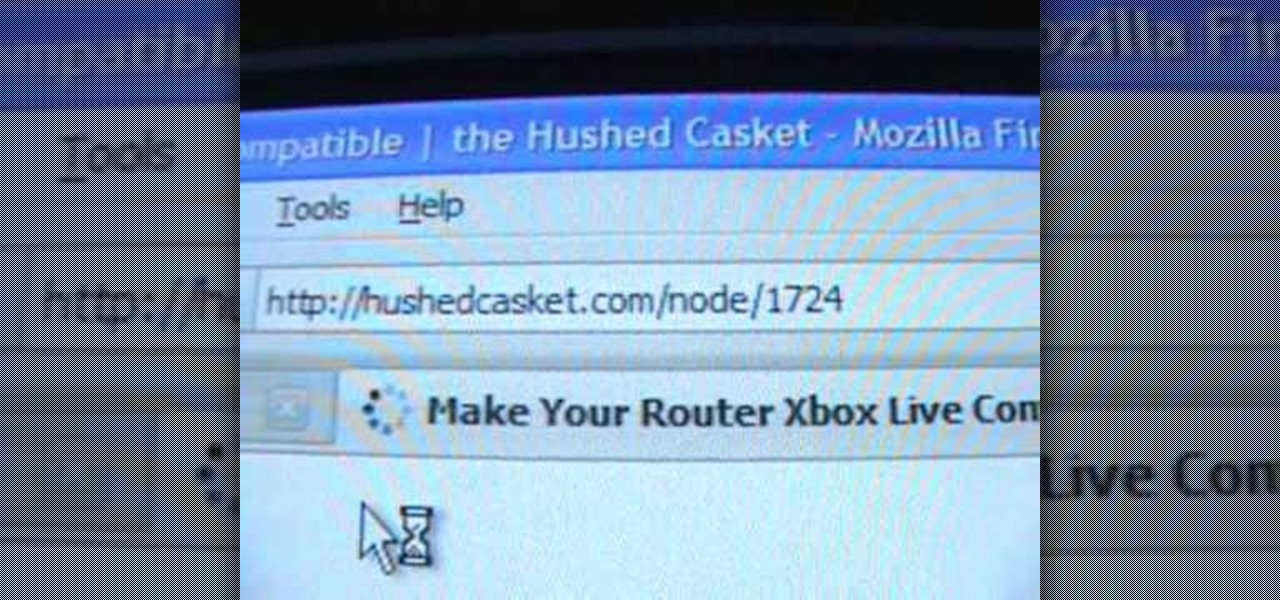
Open your internet browser, type in the address bar 192.168.1.1 and enter your user name and password to access. Look in the right and search for Port Forwarding / Port Triggering. Click on Add Custom Service. Type a name to the service, like XBox Live, now access HushedCasket and scroll down to see the ports you need to open. Go back to the setting and select UDP in Service Type. Put 88 in Starting Port and Ending Port. Go to your XBox and enter in System Settings, go down to Network Setting...

This video will show you how to find your own IP address in Windows Vista, which is more difficult and confusing to use than Windows XP was. First, you should go down to the bottom right hand corner and find an icon of two computers, which is your network connection button. Click on the Networks and Sharing selection and find the section which says "View status". After clicking on this, you will find a section which will be labeled "IPv4". The numbers which are indicated after this are the nu...

Watch this video to learn how to get Aircrack on your iPhone or iPod touch. You can use Aircrack on your iPhone or iPod touch to recover wireless network keys. The program runs directly on your iPhone or iPod touch device. It is installed as any other third party iPhone app, easy to launch and speedy to set up. Aircrack can be used as a security testing tool. Use it to verify that your network is attack immune.

Learn how to improve wireless networking on Verizon's FiOS Router. You'll see some easy tips on how to improve wireless networking with the MI424WR Verizon FiOS Router, by Actiontec.
Learn how to change your wireless network name on Verizon's FiOS Router. You'll see the easy steps on how to change your wireless network name and / or password for your MI424WR Verizon FiOS Router, manufactured by Actiontec Electronics, Inc.

I spent hours writing a guide on how to record a screencast, or record what is on the desktop, and convert it. I then found out that this is much simpler & faster and doesn't even involve opening the commandline.

Matt describes the necessary steps to take before you begin to build your infrastructure. Find business and design requirements.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

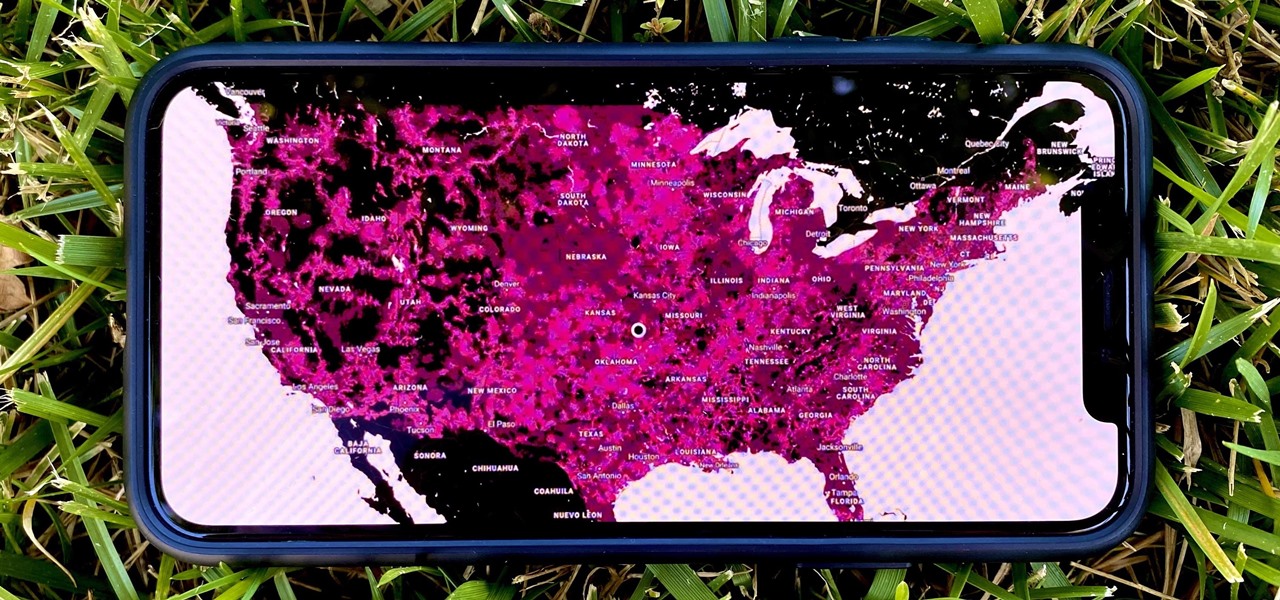
We are now in the age of 5G. Carriers worldwide are upgrading their networks to the newest standard for mobile, which will dramatically improve your phone experience. How? By giving it download speeds and latency that surpass Wi-Fi. But before you upgrade, there are few things you should know first.

There's a lot of talk about 5G these days. You might even think your iPhone is 5G-ready, since, well, it says so right in the status bar. 5G E, right? Sorry to burst your bubble, but no iPhone is capable of connecting to 5G networks yet, no matter how much you pay for that 11 Pro.

In 2009, 4G LTE networks rolled out in Stockholm and Oslo, replacing 3G as a better upgrade to the mobile data technology that gives us the broadband speeds we have on our mobile devices. Over a decade later, and we have the latest, next-generation wireless network technology among us, 5G, but can you even use it?

For a hacker, there are a lot of advantages to creating a fake network. One advantage forces nearby devices to use their real MAC address if you happen upon a network that's stored in their preferred network list.

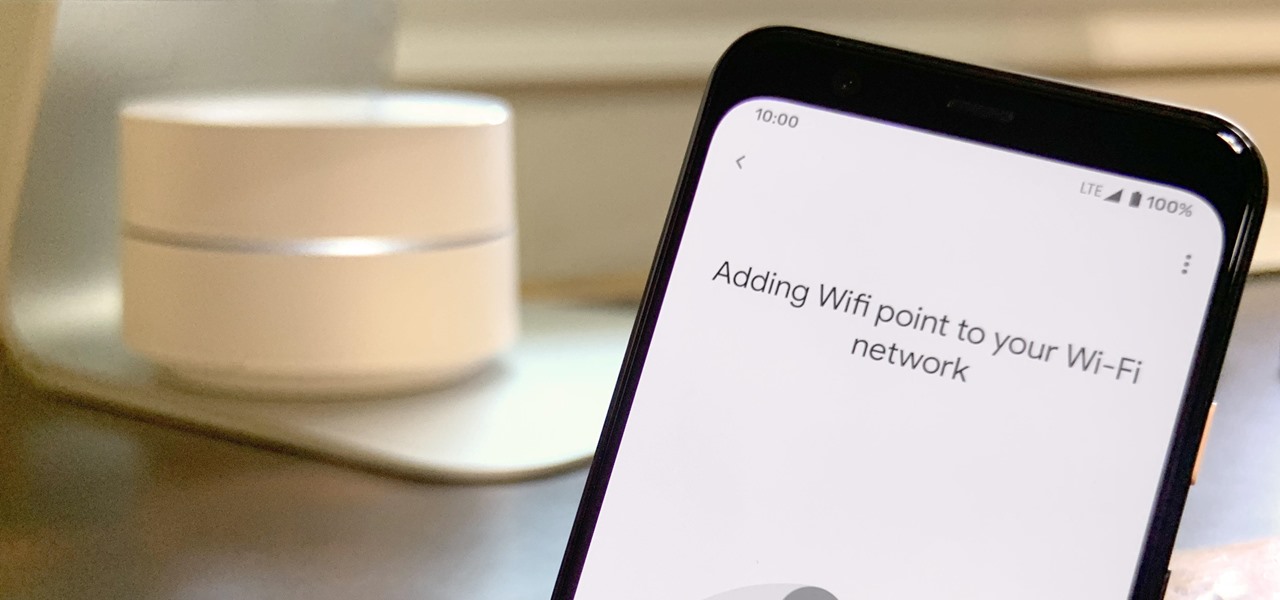
Google is known for merging older products into a new one's ecosystem for ease of use. The transition can take time, and that's the case with the old Google Wifi system now that Nest Wifi is out. Google is working on phasing out the dedicated Google Wifi app in favor of using the Google Home app for all your IoT needs.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

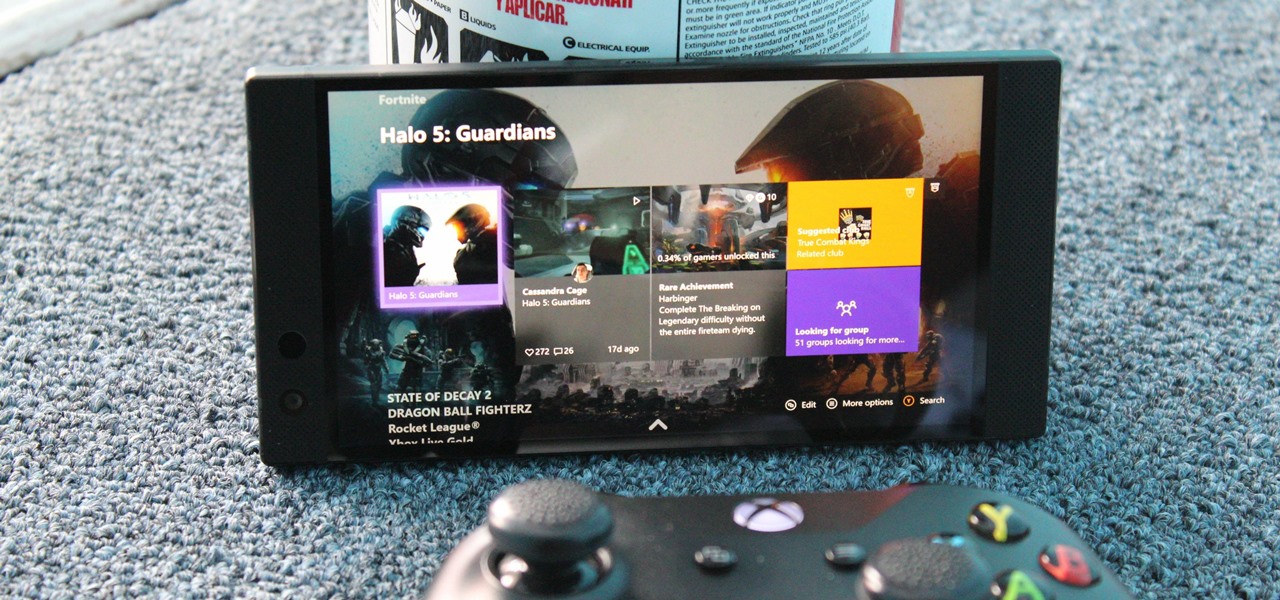
Game streaming has never been better. Not only can you watch your favorite Twitch streamer play, but with the new tools being added to YouTube, you can even play along with them. And now, with a solid internet connection, you can stream your Xbox One games to your phone to enjoy console games on the go.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

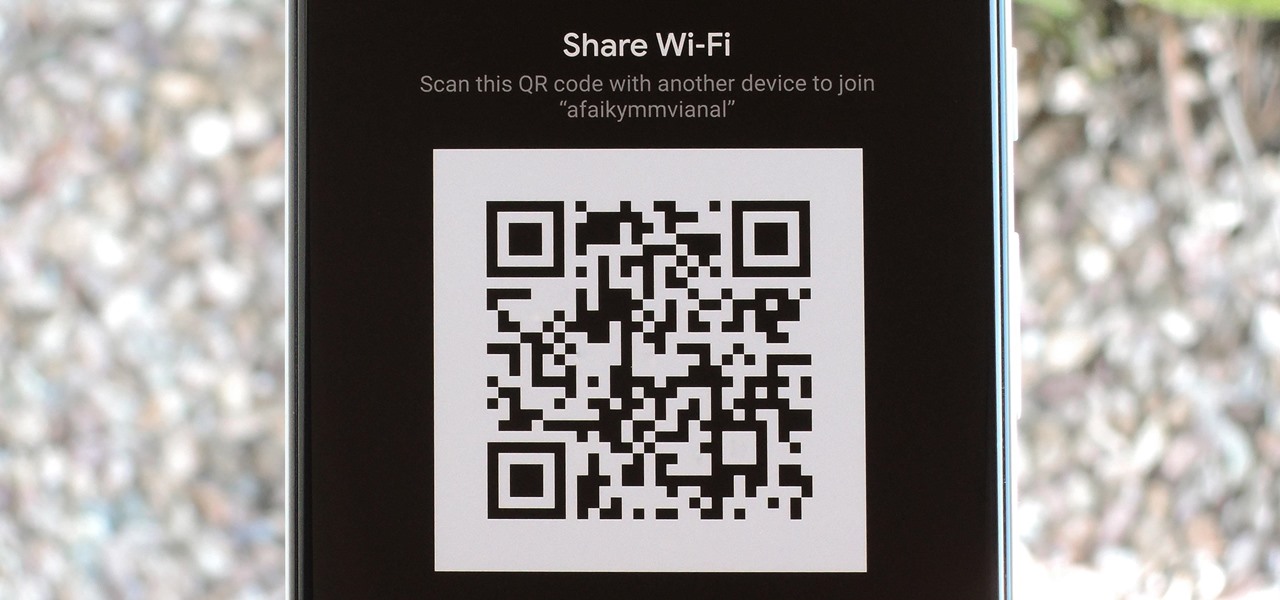
If your phone is running Android 10, you can now share your Wi-Fi network with friends using a handy QR code. The other person doesn't have to be running Android 10 — in fact, you can even share this code with iPhone users. In most situations, this is now the fastest way to share your Wi-Fi password.

Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to sniff the air for packets from any device we want to track, turning on an LED when it's detected nearby.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

Upon Google's release of ARCore in February, the platform wasn't only playing catch-up with Apple and ARKit in terms of downloads, but it also lagged in capabilities, as Apple already had vertical surface recognition and image recognition on the way with ARKit 1.5 for a March release.

Local port forwarding is good when you want to use SSH to pivot into a non-routable network. But if you want to access services on a network when you can't configure port-forwarding on a router and don't have VPN access to the network, remote port forwarding is the way to go.

A weak password is one that is short, common, or easy to guess. Equally bad are secure but reused passwords that have been lost by negligent third-party companies like Equifax and Yahoo. Today, we will use Airgeddon, a wireless auditing framework, to show how anyone can crack bad passwords for WPA and WPA2 wireless networks in minutes or seconds with only a computer and network adapter.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

Shapr is a new networking app that aims to help professionals connect more efficiently, and draws much of its format from dating-focused social networking apps. Shapr could be especially useful for those who have recently moved into their industry or location, and for those seeking employers or employees. For example, the app already has 65,000 users just in New York City alone.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

Five Phases of Hacking:- The five phases of Hacking are as follow:

These days, if you're having friends over, they'll probably ask to log into your Wi-Fi network before asking for a drink. But if you've forgotten your password, it can be quite hard to find, since most devices obscure the characters with asterisks.

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.

Long time reader, first time 'How To' poster. This tutorial has been highly requested. Here are the steps to perform a Pixie Dust attack to crack a WiFi password that has WPS enabled.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

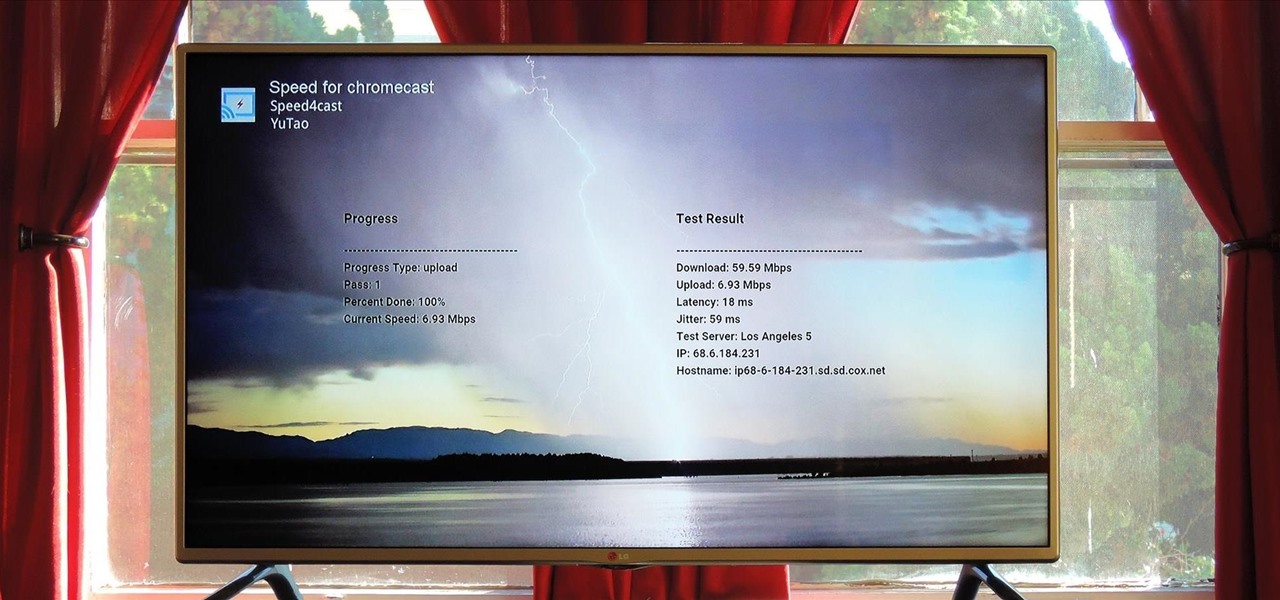
At its core, the Chromecast is essentially a web browser on a stick. When you cast content from your computer or smartphone, all you're really doing is telling the Chromecast which website to load.