
How To: Find IP address of any PC
Learn to create a script in Windows XP that will find the IP address of a network PC.


Learn to create a script in Windows XP that will find the IP address of a network PC.
Gary Rosenzweig answers viewer questions about saving Web pages, sharing a network connection and creating a podcast playlist.

In this episode we demonstrate how to sniff Voice Over IP (VOIP) conversations, which basically means how to tap an Internet phone.

This video demonstrates how to discover the dating history of people by searching on the website www.rateabull.com. The site searches their own dating database, as well as several other social networking sites.

Need internet access and you don't have a login? Hack into a private or controlled network with this tutorial. Thefixed.org also shows you how to build a smoke bomb!

Got movies and music on your PC? See how to stream through your Xbox 360 right onto your TV screen. You'll need to have your Xbox 360 connected to your home network first.

DNS spoofing - how to use the hosts file in Windows XP to block unwanted spyware/popups/etc, block programs from reporting to a site, filter/block/redirect websites, and locally create forward lookups (IP to name resolution in network)
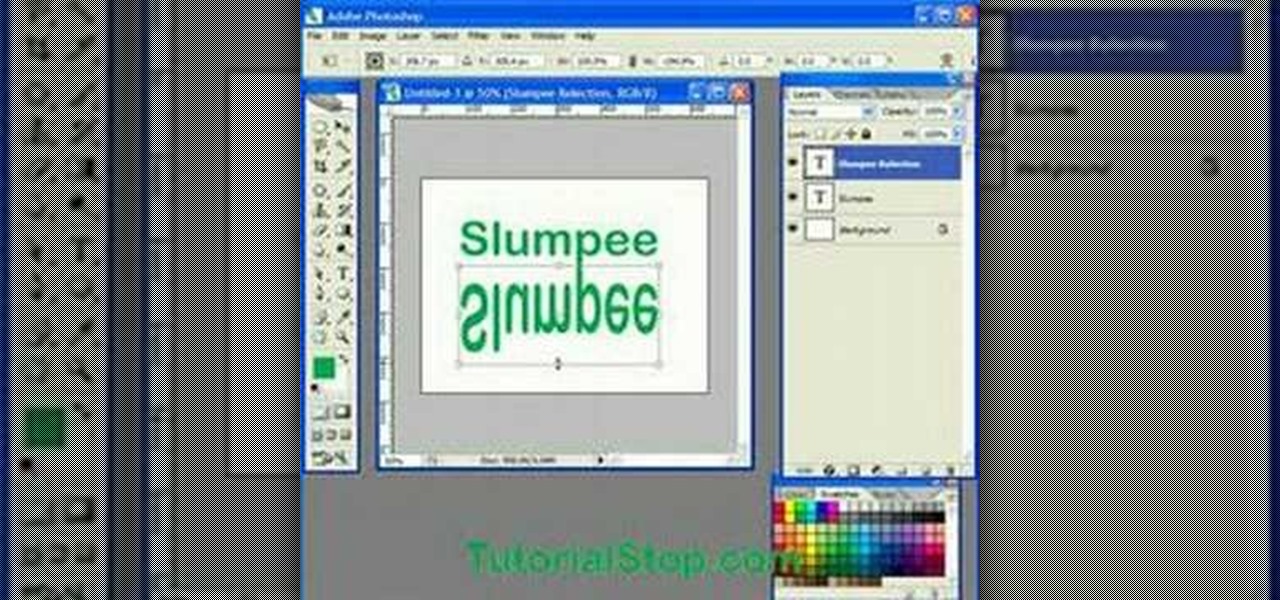
In this video tutorial you will learn to use Photoshop to create a shiny reflective logo in a web 2.0 style. Not sure what Web 2.0 is? It generally refers to a perceived second generation of web-based communities and hosted services — such as social-networking sites, wikis and folksonomies — which facilitate collaboration and sharing between users.
This video helps you to protect your computer against viruses and spyware often contracted when using peer to peer (p2p) networks like limewire, kazaa and emule.
Speed up your EDGE network connection on the iPhone up to 5xs. Change your settings to optimize connection speed not using WiFi.

In this tutorial, we learn how to make croissant bread pudding with Food Network. First, combine 3 whole eggs and 5 egg yolks with 3 cups of half and half. Whisk this together, then add in 1.5 c sugar and 1.5 tbsp vanilla and mix together again. After this, cut croissants in half and place on the bottom of a casserole dish. Now, layer raisins on top of this, then add on a second layer of croissants. Pour the liquid mixture over these, then push the croissants down into the custard so they abs...

Looking to give a personalized gift for a birthday or for the holidays? How about a personalized bar of soap, specific to your friend or family's style? In this episode of ThreadBangers's Decor It Yourself, Meg visits Bobbie Thomas, an editor for the "Today Show" and learns how to make your own soap, and how to customize it to be just about any color, shape, or size!

Ever desired your very own masquerade mask? ThreadBanger takes us through the fun, multiple steps to acquire your very own custom-fit plaster mask! Materials needed include plaster wrap cloth, water, scissors, petroleum jelly, spray paint (in your color choice), sand paper, paint sealer spray, and decorative additions to personalize your mask! This project will need to dry overnight, so be sure to leave enough time before your party or event.

Steal Lady Gaga's eccentric look from MTV's 2009 VMA Awards for your next big costume party with help from ThreadBanger. You will need some poster board, red spray paint, flesh-colored stretch fabric, an excessive amount of red lace, sewing skills... and about four hours. Blonde ratty wig not required, but a big plus!
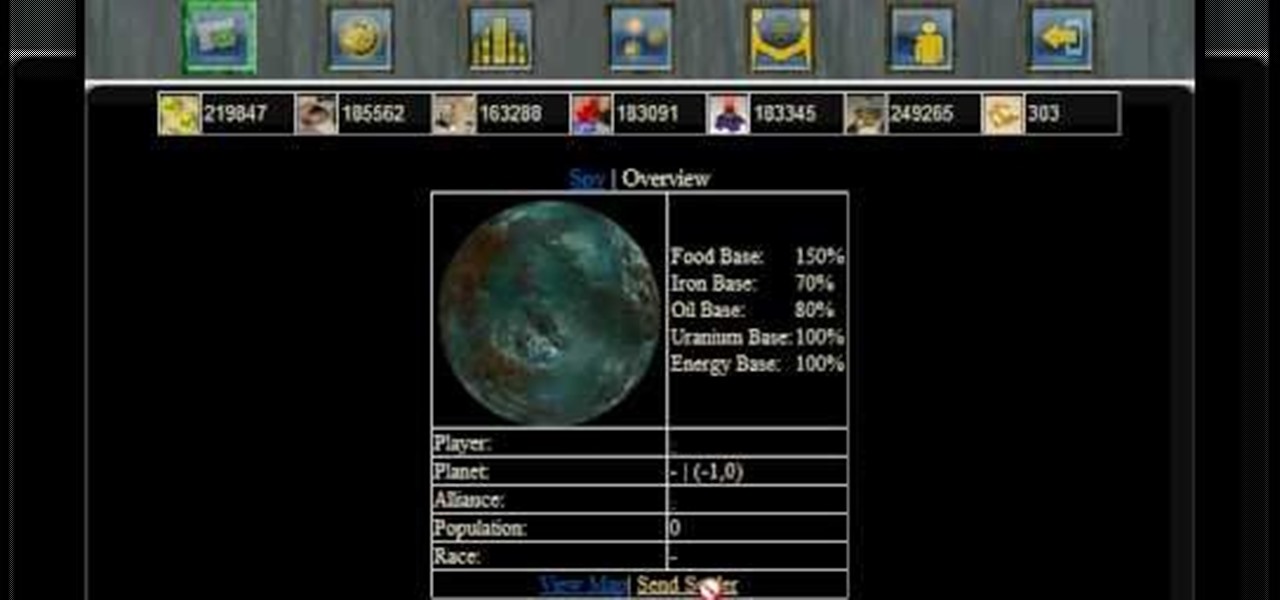
Settling a new planet will decrease your pride ratio, because your population will increase when you're settling a new planet. If you're not sure how to even settle planets...
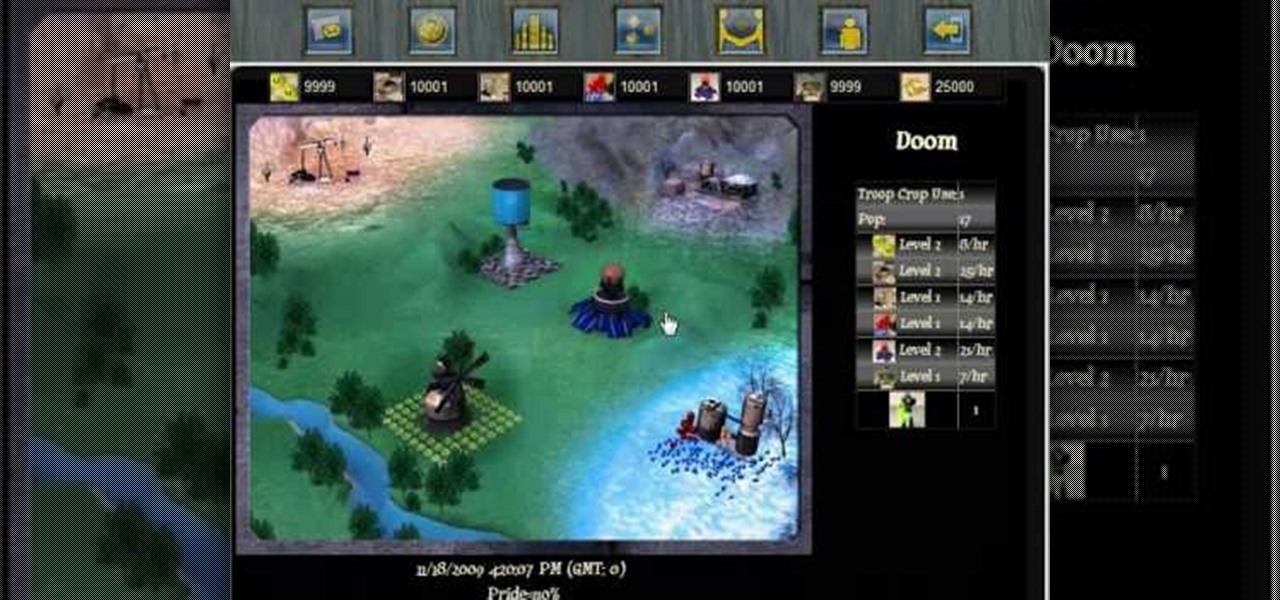
In order to spy and gain intelligence on your Conrohl enemies, you need to make an intelligence agency. Then you recruit your spies to perform simple espionage.

Ready to get into custom hat-making? Be your own milliner, with the tips from this video fashion lesson. In this video episode, Rob and Corinne hook up with Hat make Victor Osborne for a super DIY lesson on how to make Hat Molds on the cheap.

In this tutorial, we learn how to clear the ARP cache. First, go the command prompt on your computer and type in "C:/>netsh interface ip delete arpcache Ok". Press 'enter' on your keyboard and then it should be cleared out. If you want to view your ARP cache, type in the command "C:/>arp -a". If this fails, then you will need to use Microsoft Windows to repair the network connection. If this doesn't work, talk to the person that manages your connection. If successful, this will help make your...
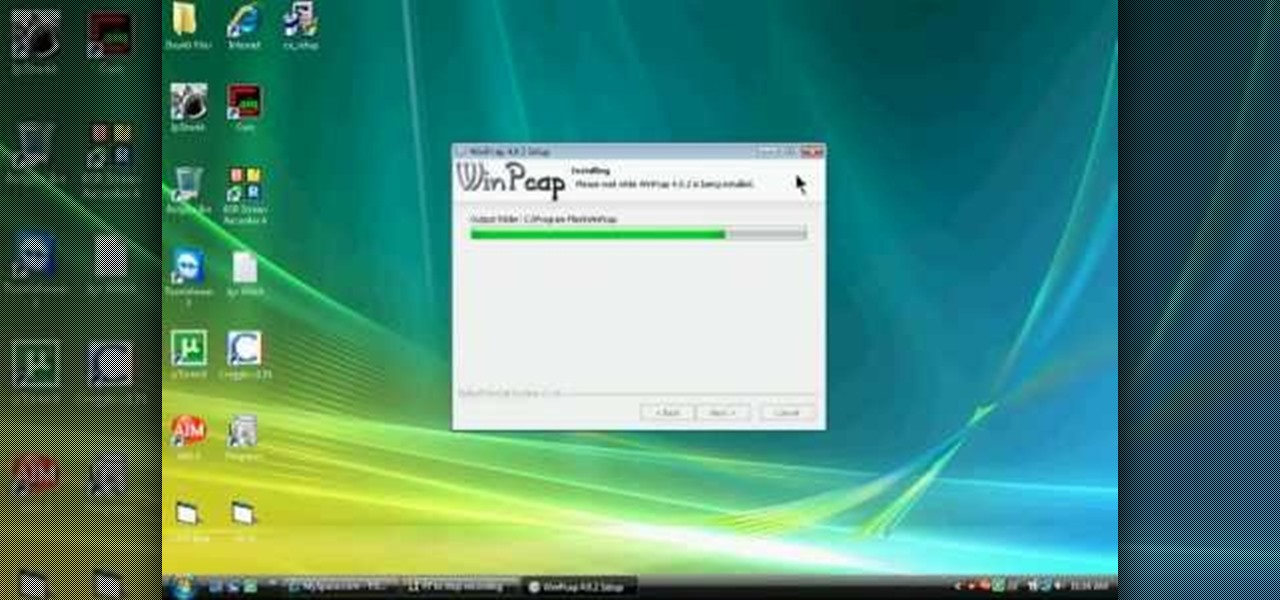
First you have to install program, called 'Cain and Abel'. Then, you will be automatically asked to install 'Win Pcap' and you should do that. After installation you have to click on 'Cain and Abel' program icon with right mouse button and start it as administrator. Then push blue plus sign to scan Mac addresses. After scanning go to the bottom of program window and press APR tab. Then push blue plus icon again. When table appears push first option in first square and first option in second a...
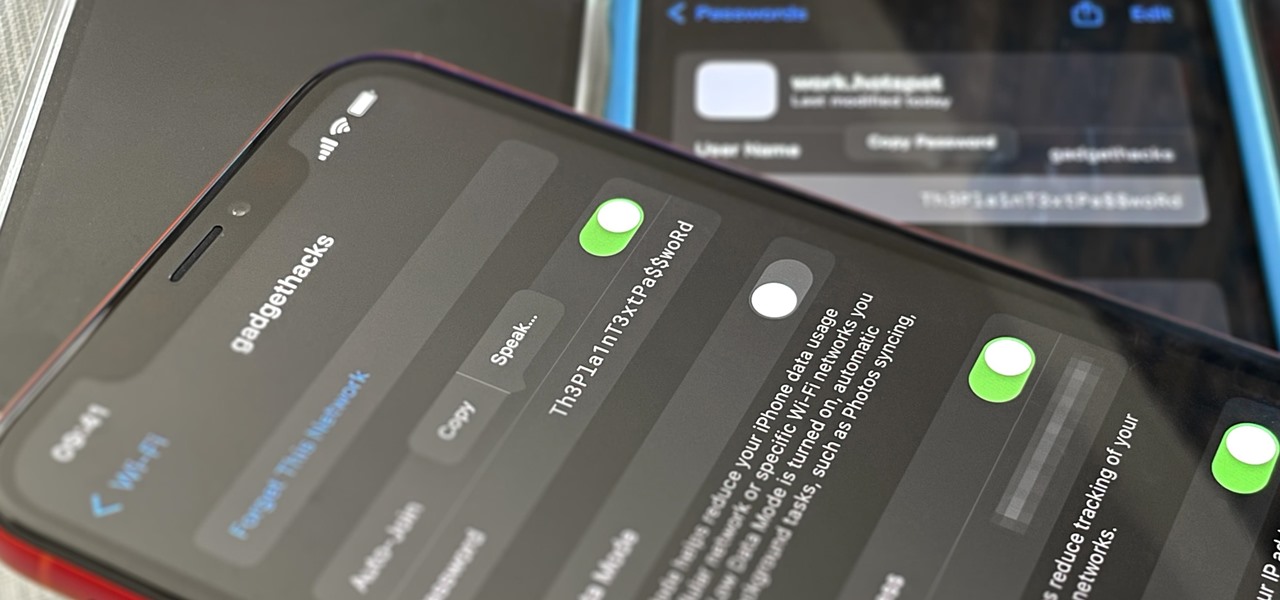
Your iPhone goes with you pretty much everywhere you go, and unless you have unlimited data on your cellular plan, you've probably connected to dozens of Wi-Fi hotspots over the years. Wi-Fi passwords are saved to your iPhone so you can auto-connect to the router or personal hotspot again, but finding the plain text password for a network hasn't always been easy.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

We're living in uncertain times. The sudden outbreak of the novel coronavirus and subsequent self-isolation of roughly half the world's population has led to a massive reorganization of the economy, countless layoffs, compromised security networks, and a variety of other significant disruptions that will forever alter the landscape of our daily lives.

One of the main goals of Google Wifi (and Nest Wifi after it) is to make managing your internet connections as simple as possible. A great example of this is how easy it is to prioritize one device and allot it more bandwidth when your network is bogged down with other traffic.

A virtual private network is a necessary part of your arsenal if you're insistent on surfing the web privately and securely on your iPhone. The App Store is littered with hundreds of different VPN services that encrypt traffic and mask your IP address, but what they all have in common are connectivity issues.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

While augmented reality made more of a cameo appearance during Samsung's official grand unveiling of the Galaxy S10 line-up on Wednesday, it's the company's move into 5G connectivity that has huge implications for AR.

The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each type of packet. The pattern of these colors can also allow us to fingerprint the tool being used to attack the network.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

The pending union between Prince Harry and American actress Meghan Markle is almost guaranteed to set the internet ablaze as millions tune in to experience the spectacle and pageantry of such a momentous event. If you've cut the cord and are wondering where you can stream the royal wedding for free, we've got you covered.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

Toyota is testing blockchain and distributed ledger technology (BC/DL) for data sharing for driverless cars and other applications. This could eventually reassure buyers of its upcoming high-end cars by making sure their sensitive data is secure.

Who pays for live TV anymore? Better question, who watches live TV anymore? With a ton of streaming services available, there's no room in our lives for things like schedules, commercials, or going weeks between episodes. (What is this, 2010?)

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

Copying files from a computer to your Android device has always been pretty straightforward—just connect the two devices with a USB cable, open your desktop file explorer, then move the files over. But what if you didn't need any wires at all?
So you're finally ready to head out on that big trip you've been planning for months, huh? It's an exciting time, but there are plenty of things you'll need to prepare before you head out. For instance, it's hard to imagine life without a smartphone these days, and with useful traveling apps like Google Translate and maps, you'll almost have to make sure that you have a working smartphone when you arrive at your destination.

I have came across a lot of members on the forum that didn't have a clear idea of what port forwarding is and what it does. So...Let's get started...

Welcome back, my tenderfoot hackers! Generally, you will want to perform a vulnerability scan before doing a penetration test. Vulnerability scanners contain a database of all known vulnerabilities and will scan your machine or network to see whether those vulnerabilities appear to exist. If they do, it is your job to test whether they are real and can be exploited.

Welcome back, my neophyte hackers! In the world of information security, the most common intrusion detection system (IDS) you will ever encounter is Snort. As you probably already know, an IDS works similarly to antivirus (AV) software on your desktop; It attempts to identify malicious software on your network and warns you of its presence.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.