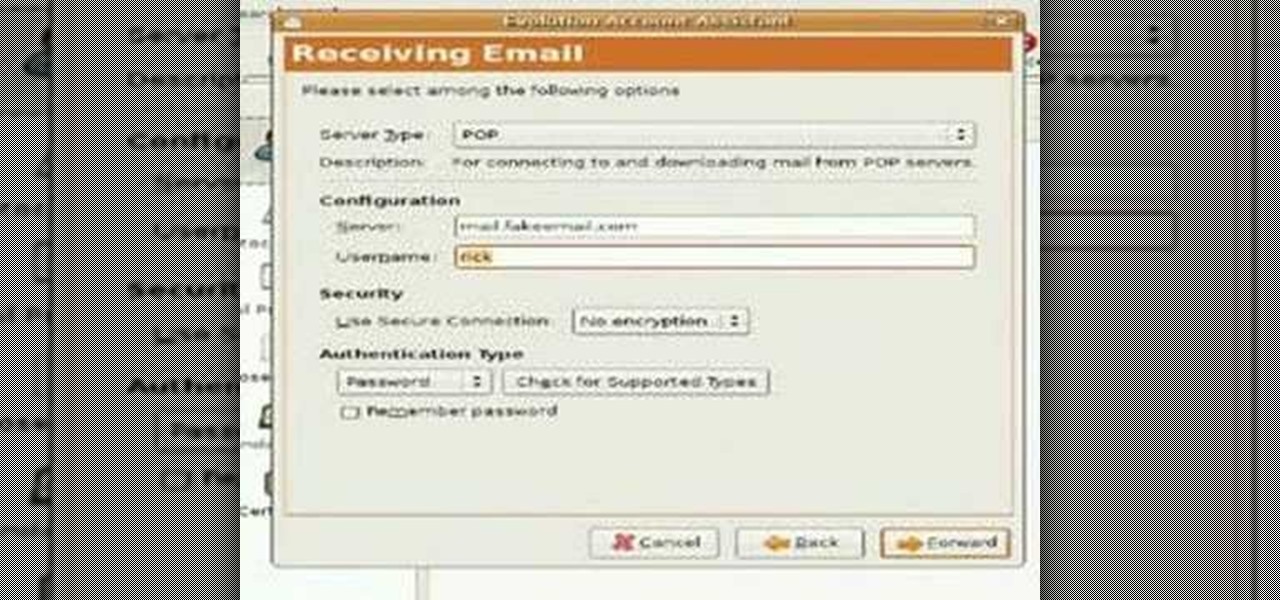
New to the Ubuntu Linux distribution? Ubuntu has a great built-in email client in Evolution. This video tutorial will walk you through the Evolution setup process, using the Evolution Setup Wizard. To get started setting up your own Evolution client, watch this Ubuntu tutorial!
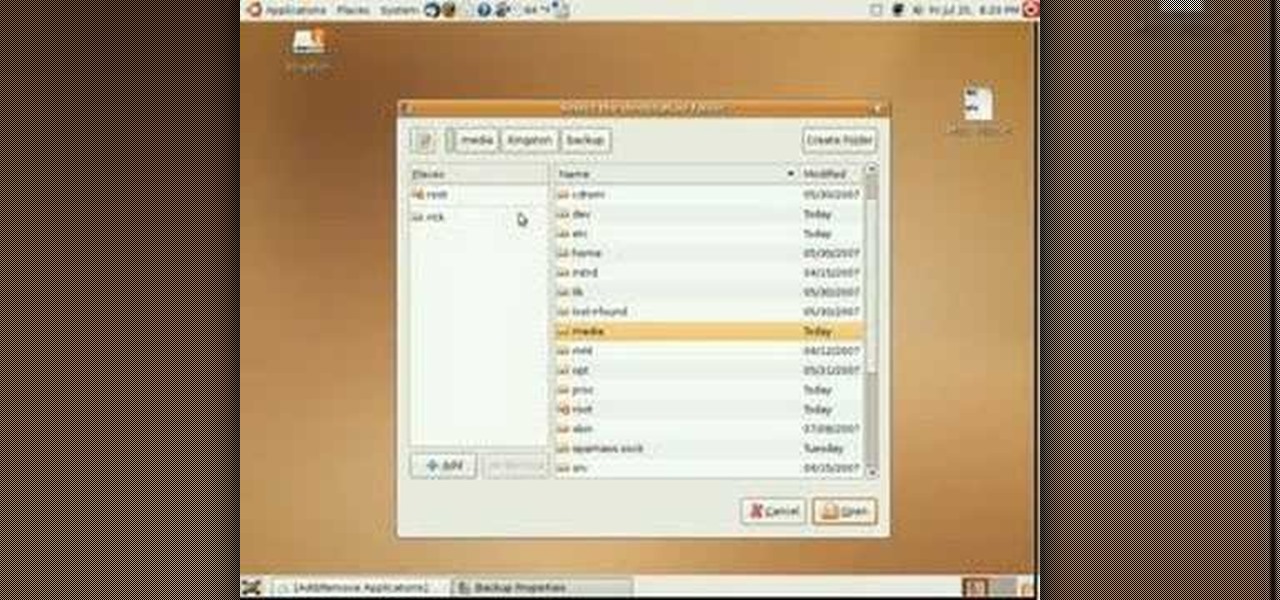
In this video tutorial, users of the Ubuntu Linux operating system will learn how to use the Simple Backup application to either manually or automatically back important data. For more, or to get started using Simple Backup on your own Ubuntu Linux system, watch this handy how-to.

Drag and drop doesn't work automatically in the Ubuntu Linux distribution. You'll need to make some settings changes to enable it. For a step-by-step look at the process to enabling drag and drop file management in Ubuntu, watch this Ubuntu tutorial.
New to the Ubuntu Linux distribution (or one of its derivatives) and looking for a way to start programs automatically when you boot up your machine? Take heart: This video tutorial will show you how to accomplish just that using your system preferences. Take a look!

New to the Ubuntu Linux distribution and interested in setting up an address book for to keep track of your contacts? In this how-to, you'll learn how to make maximum use of the address book built into the Evolution email client. Take a look!

Interested in running Linux but are afraid of accidentally formatting your primary hard drive? One solution is to bypass your hard drive altogether and run your Linux distribution live from a CD. This three-part video tutorial series will show you how to do just that using Ubuntu.

Measuring out a bicycle frame is useful knowledge. This instructional video shows how to determine the best sizes and angles for weight distribution on the bike frame. Georgena Terry's drawings and geometry help explain which bicycle frame designs are best for riding.

Oh how we love open source software. If it wasn't for Open Office, we never would have been able to write that seven-page English paper while on our friend's Microsoft Office-lacking laptop during an impromptu road trip to Mexico. And Ubuntu, an open source secure operating system, offers you similar convenience. A much more intuitive computer operating software than your standard Windows or Mac OS, Ubuntu is great if you know what you're doing.

With the economy as terrible as it is these days, obtaining any sort of job, from receptionist to screen writer, requires thorough networking.

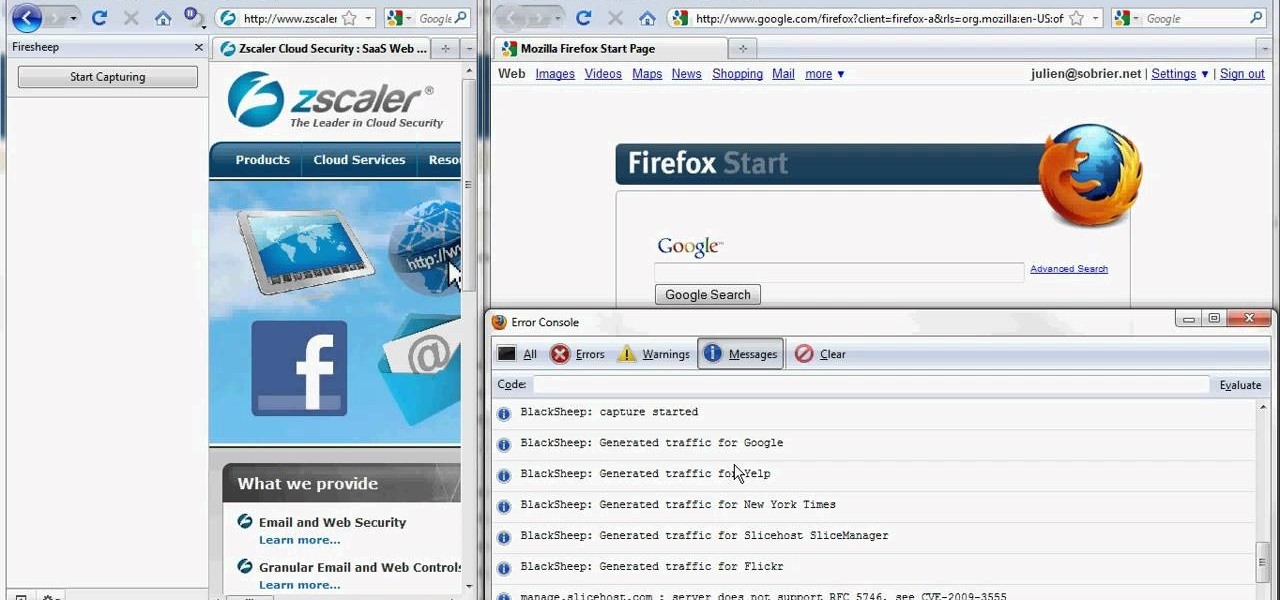
If you're scared of using public Wi-Fi networks with Firesheep out and about, then maybe you should fight back. Don't switch to another web browser— keep using Firefox safely with the help of a new Firefox Add-on that combats Firesheep's password stealing capabilities. It's called BlackSheep, and when installed and running, it will alert you whenever Firesheep is active on your network connection.

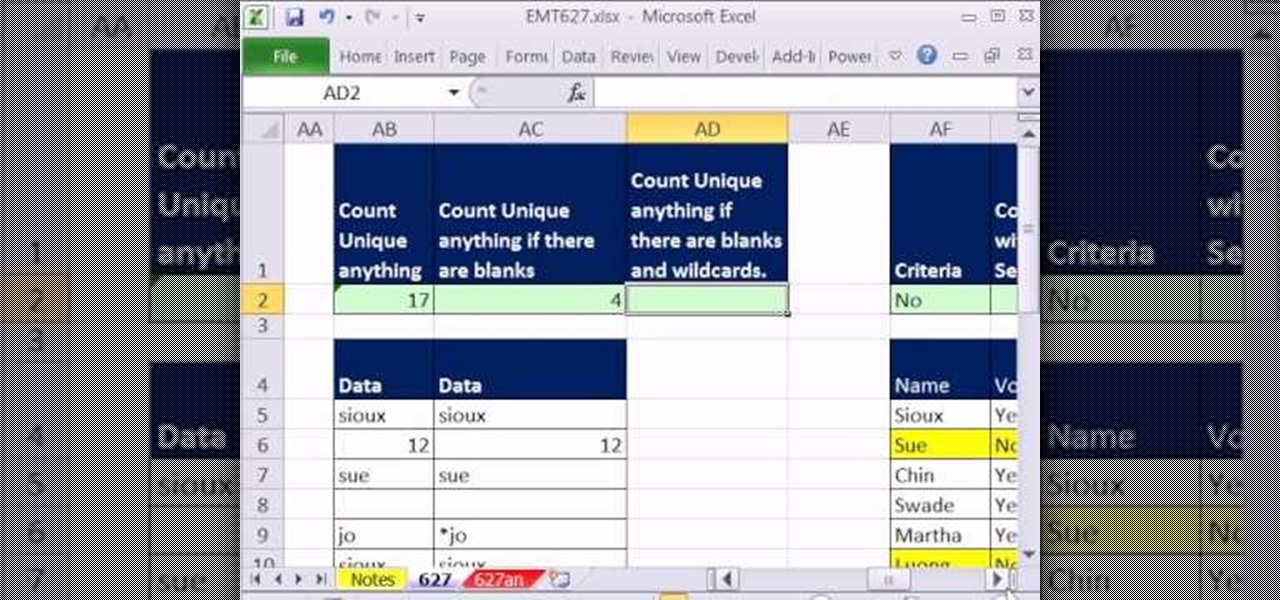
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun and Mr. Excel, the 627th installment in their joint series of digital spreadsheet magic tricks, you'll learn how to create, edit and otherwise work with FREQUENCY array functions.

In this tutorial, learn how to save yourself the money you'd pay someone to unlock your Google G1 phone from T-Mobile and do it yourself in just a few quick minutes. This is actually a very easy process and this clip will walk you through the process step by step so you can freely use your phone on any network and not be limited to T-Mobile. This is also helpful if you wish to give away or sell your phone to someone on a new network.

In this clip, learn how to tether your rooted Droid to a WiFi network and use it as a modem for your other Wireless devices. This process is pretty easy and only requires a network and that your phone be rooted.

In this culinary how-to from the Food Network's Ellie Krieger, you'll learn how to bake delectable, almost-healthy carrot cupcakes using whole carrots, lemon zest, canola oil, brown sugar, two eggs, 3 quarters of a cup of whole wheat pastry flour, 1/2 cup all-purpose flour, 1 teaspoon of baking powder, 1/2 teaspoon of cinammon, 1/4 teaspoon of nutmeg and a 1/4 teaspoon of salt.

Watch this video fashion design lesson to see who took second place in the Generation-t tee recon contest with how-to make a wrap shirt. All you need is two t-shirts and the steps, so follow along and get sewing.

Watch this fashion design lesson to see who took third place in the Generation-t tee recon contest with a how-to for making a no-sew fringe halter top!

This week Meg takes us back in time and shows us how to make an amazing Starburst mirror. Follow along with the home interior how-to video, and learn how to add a little vintage flair to your own home decor.

In this tutorial Mike Lively of Northern Kentucky University shows you how to get started with Wireshark. Wireshark is a network protocol analyzer for Unix and Windows. It is used for network troubleshooting, analysis, software and communications protocol development.

In many urban areas, GPS doesn't work well. Buildings reflect GPS signals on themselves to create a confusing mess for phones to sort out. As a result, most modern devices determine their location using a blend of techniques, including nearby Wi-Fi networks. By using SkyLift to create fake networks known to be in other areas, we can manipulate where a device thinks it is with an ESP8266 microcontroller.

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

A long-standing request for the iPhone has been a way to quickly browse and connect to available Wi-Fi networks and Bluetooth devices without having to dig through the Settings app. With iOS 13, Apple has finally built this essential feature into Control Center, giving you quick access to wireless settings from anywhere, including the lock screen.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

Nvidia has emerged as the indisputable leader in chips for Level 3 and even more advanced driverless applications, catching some of the world's largest semiconductor makers and automotive suppliers by surprise.

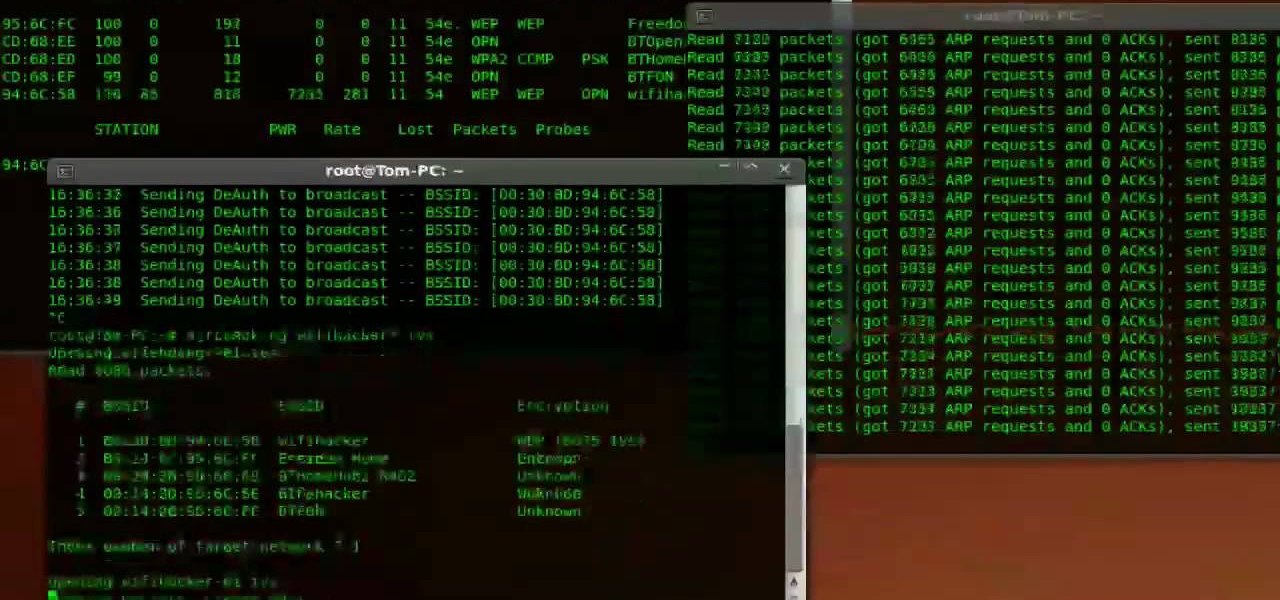
To hack a Wi-Fi network using Kali Linux, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, so I've rounded up this list of 2019's best wireless network adapters for hacking on Kali Linux to get you started hacking both WEP and WPA Wi-Fi networks.

Apple announced upcoming changes today to prevent third-party tracking of users and prevent autoplay, on Safari. Safari will prevent the recording (by anyone other than Apple) of users' browsing behavior, and by doing so prevent advertisers from targeting ads based on individuals' history.

Those of us with modern smartphones know that 4G LTE networks have provided us with a phenomenal experience. One light years beyond what we had access to before. For some time, AT&T has been teasing its dive into the next iteration of network speeds, agonizingly doing so without any specific dates for when they would actually deliver. But today, AT&T confirmed what they call the "5G Evolution," and it's available now.

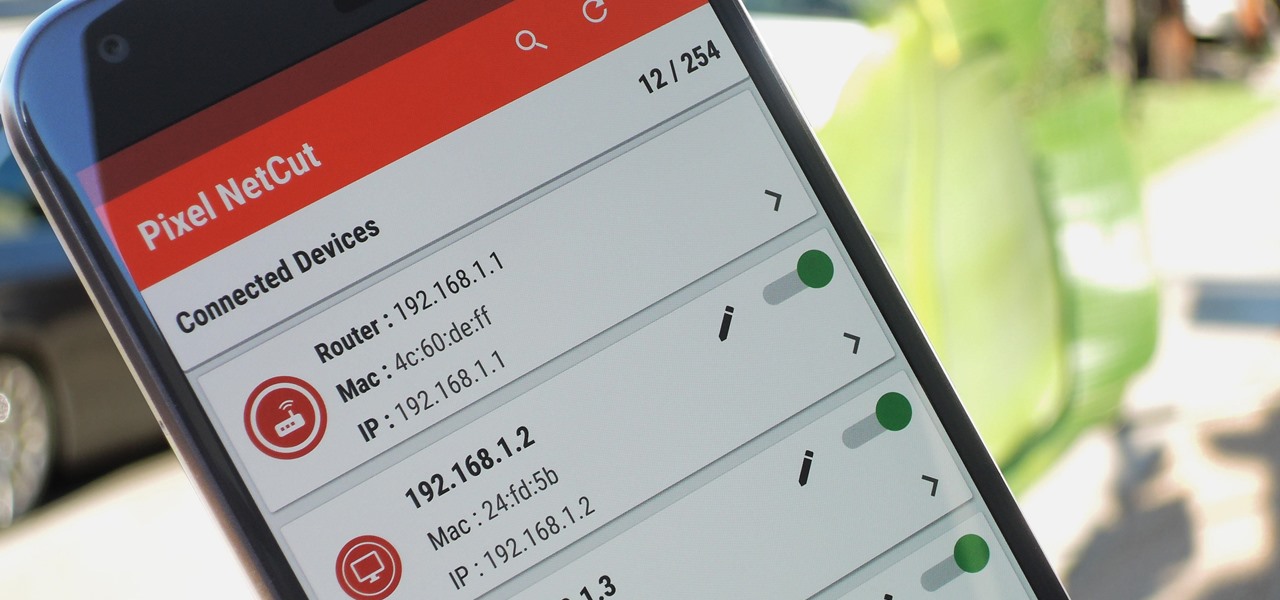
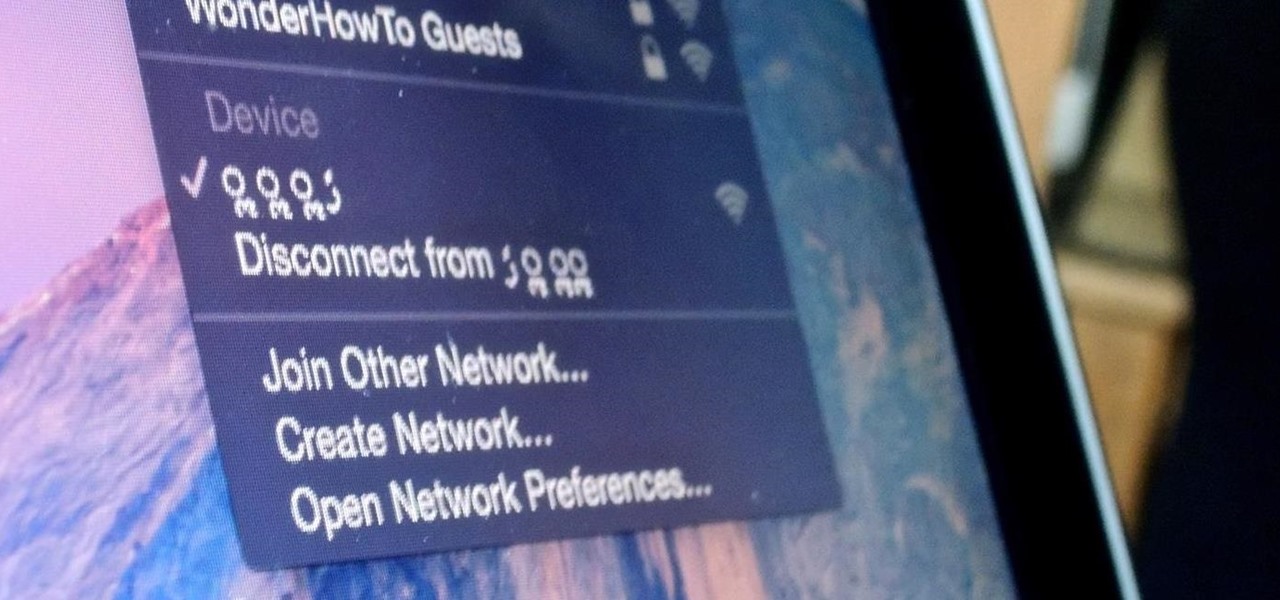
Let's say you gave your Wi-Fi password to your neighbor a while back, under the assumption that they'd only use it while they were at your house sharing stuff via Chromecast. But now, your connection is slower than it normally should be, and you have this sneaking suspicion that the dude in apartment 3C is flat-out piggybacking off of your home network.

Welcome back my networking geeks. In this part we are going to keep discussing about IP Addressing and I hope after you finish reading it you will become an IP wizzard.

Once you connect all of your devices to your Wi-Fi router at home, you'll never need that long, complicated Wi-Fi password ever again, right?

As mobile devices become more and more popular, service providers have unfortunately resorted to capping data. What this means is that, depending on the plan you have with your ISP, you could have limits placed on how much data you can use for a set period of time. Once you've hit the limit, your ISP could drastically slow down or throttle your internet speed or charge you outrageous overage fees.

Relentless in its fury, the iOS text messaging exploit that exploded onto the scene late last week seems to do more damage than initially reported.

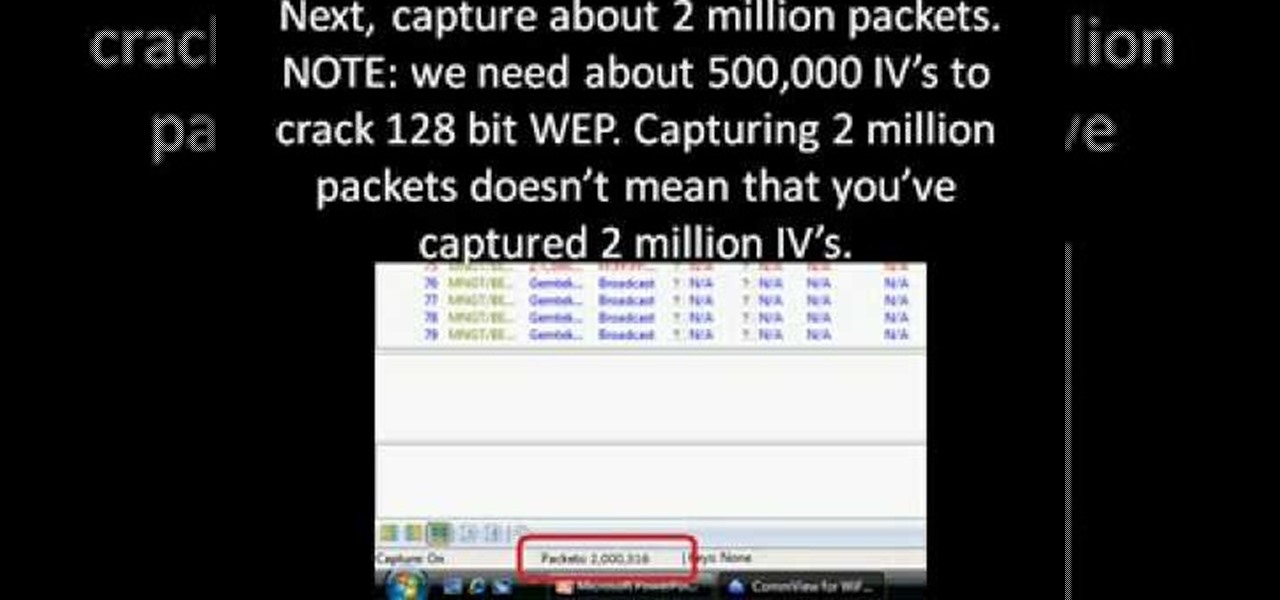
First you need to download Aircrack-ng and Second thing you need to download is CommView for Wi-Fi. Now you have to install CommView for Wi-Fi and then install the right driver.

1. Describes how to setup a VPN connection on Windows XP. 2. Goto Start-> Control Panel-> Network connections.

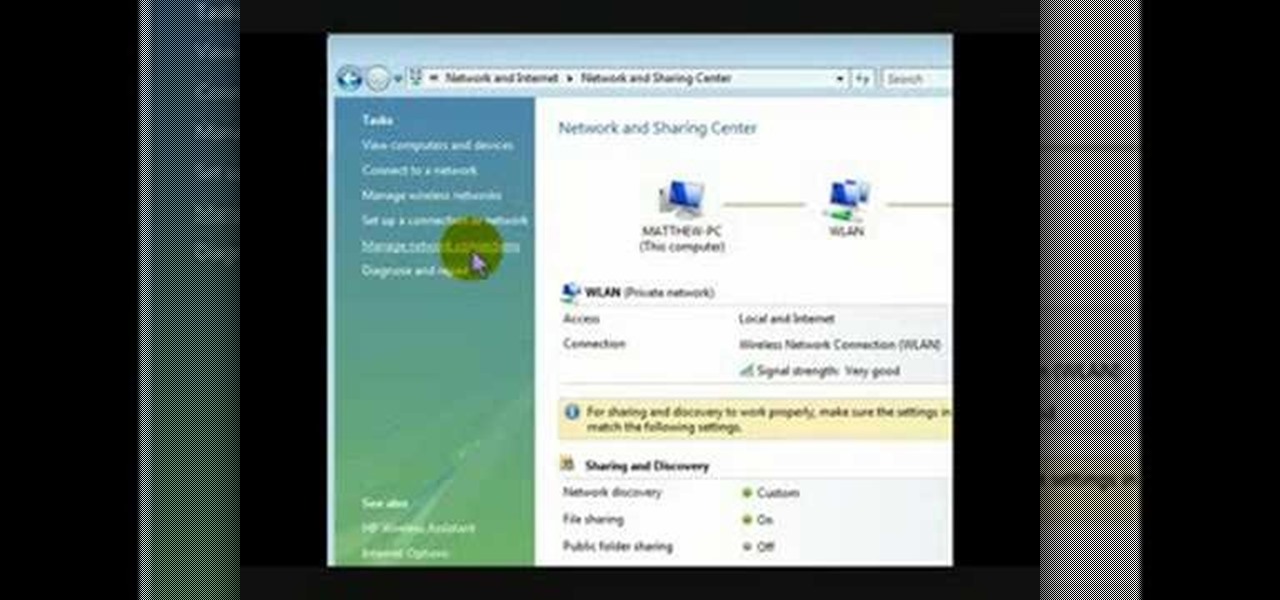
This is a video that is describing how to connect your xbox360 to the internet using a laptop. First what their showing is going to the start menu, and then to the right of it, click on control panels. A little page will pop up, and you click on network and internet. It takes you to another page and then you click network and sharing. It will take you to another page, where you see three computers, and to the very left of that page there it says "tasks" look in the columns under tasks and cli...

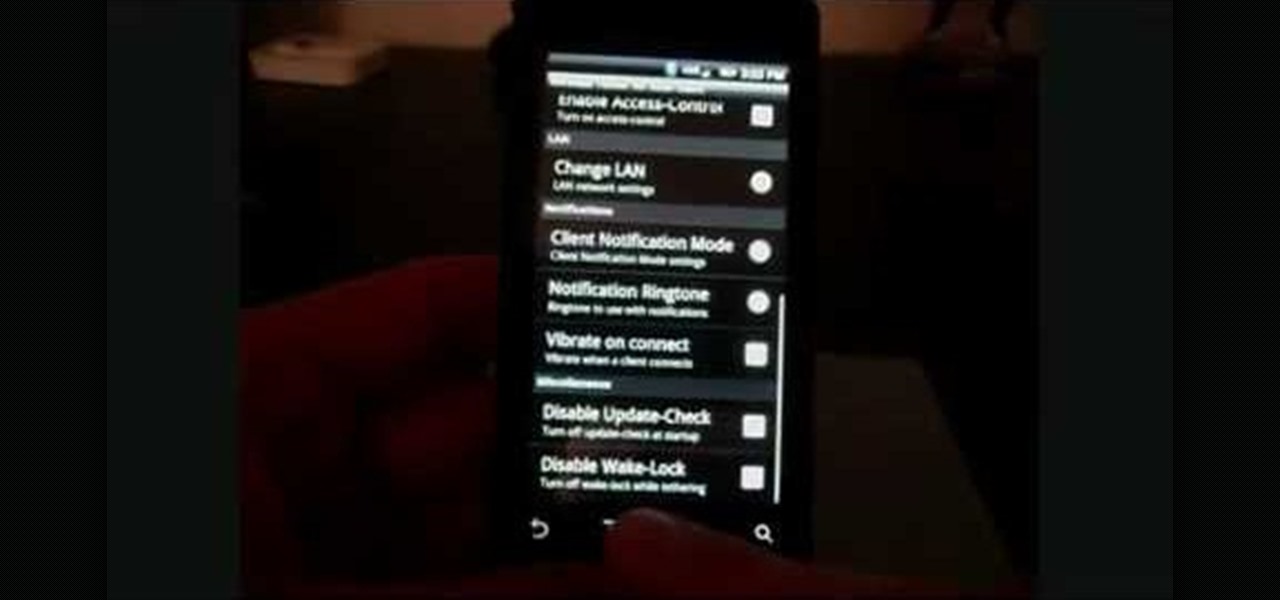
Wrestling with the whys are wherefores of WiFi? Can't figure out how to secure your network? Take heart: This remarkably thorough, seven-part home networking tutorial will get you up and running faster than you can say `Wireless G.'