The next time you find yourself in need of the same element in multiple places on your page, it’s probably time to check out Adobe Illustrator CS2’s Symbols. Symbols are more efficient than just duplicating elements in your document, and they also allow your Illustrator documents to print faster. Lastly if you ever need to update all those elements it’s much faster to update the master symbol.

You may be wondering what exactly makes the Pixel 4a's camera so great. Compared to its predecessor, it has the same Sony IMX363 sensor and no additional hardware. Well, beyond stellar image processing, it also has several great new features that Google has added since they released the Pixel 3a last year.
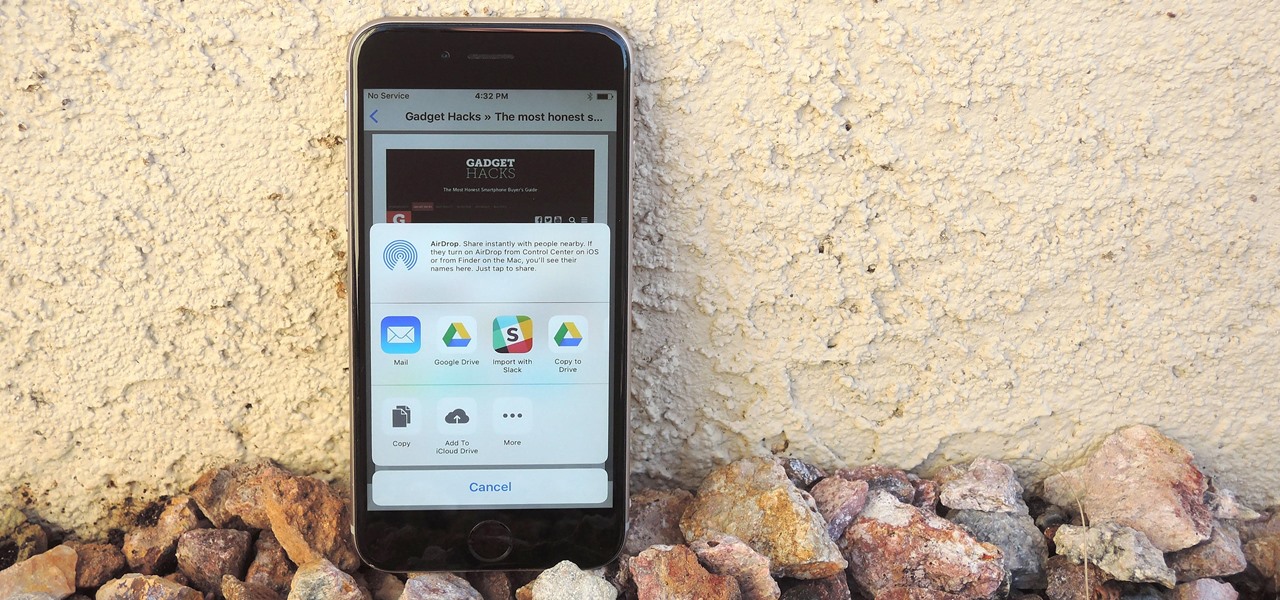
Apple lets you save webpages as PDF files in iOS 10, but the only obvious way to do this is by using iBooks. The thing is, most people would probably rather save their PDFs to a service like Google Drive or Dropbox to make sharing a bit easier. Plus, iBooks isn't officially available for Windows or Android, so there are some cross-platform problems there, too.

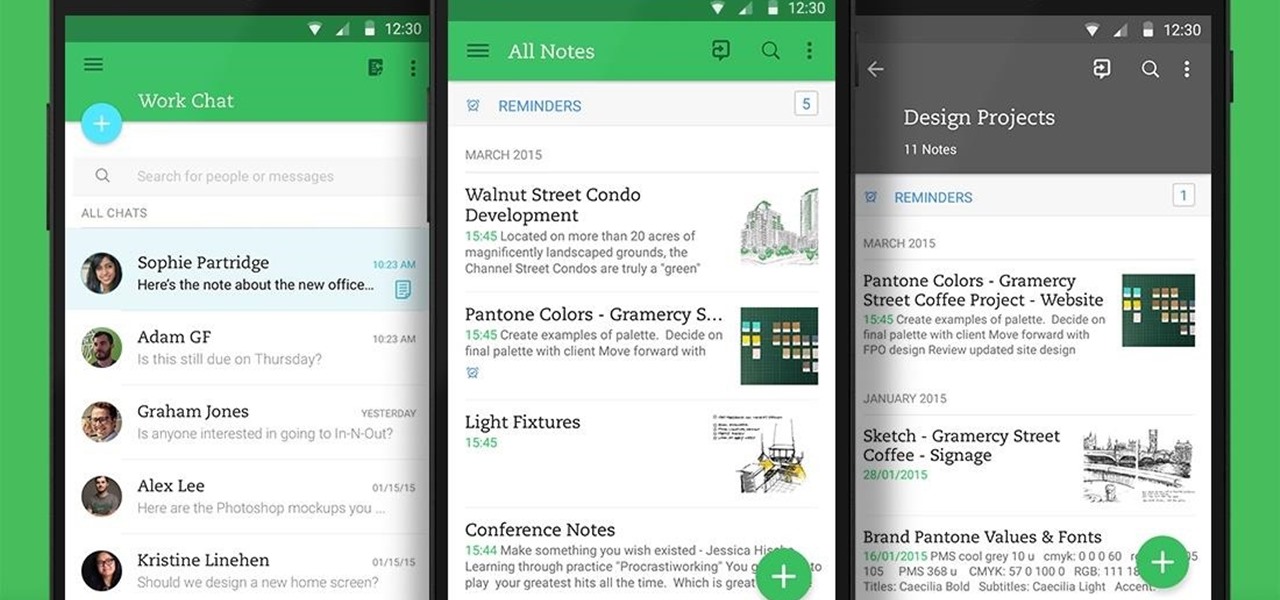
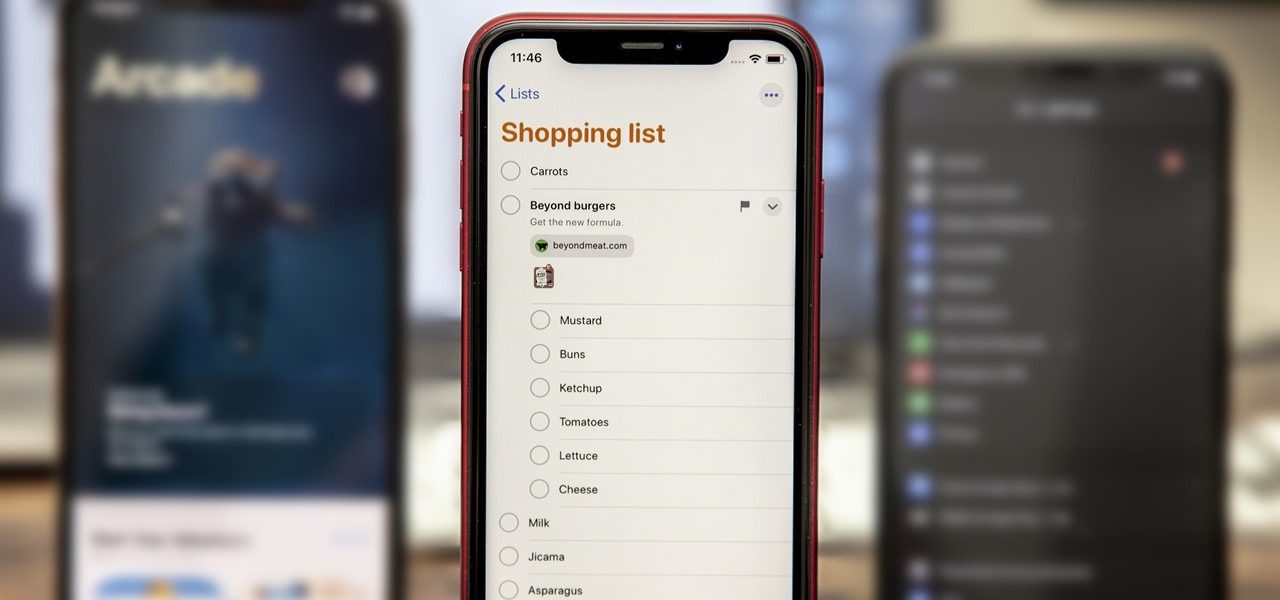
When you think of all the fun and games smartphones have to offer, it's easy to forget that they also make a great tool for getting things done. With utilities like document scanners, calendars, to-do lists, office apps, and password managers, that little computer you carry around in your pocket has the potential to increase your productivity levels in all aspects of life.
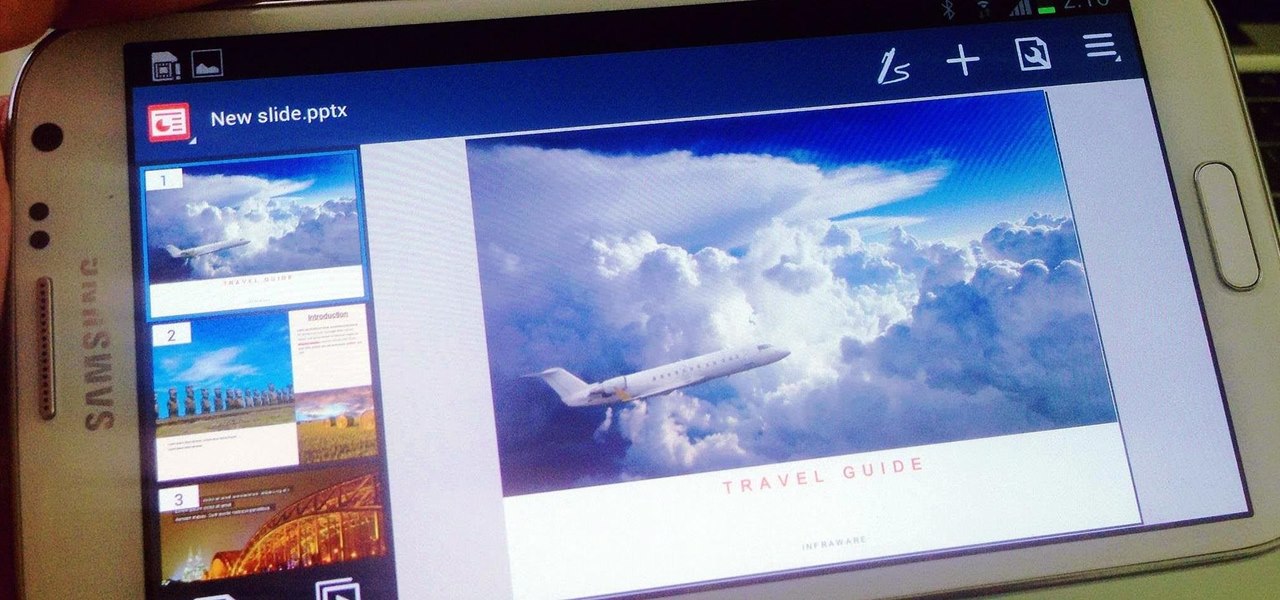
There are a lot of apps in Google Play for your Samsung Galaxy Note 2 that let you create, edit, and view Microsoft Office files on the go, but none match up to the power of an app called Polaris Office for Samsung Galaxy devices.

Last week, Google updated the YouTube layout to be more in tune with other Google properties. One thing that's different is the new, more Google+ look of your YouTube homepage. Though some may like the change, some definitely do not. Also new is the "Guide" on the left side when you're watching a YouTube video. for you folks looking to get back to the normal YouTube layout, it's as easy as copying and pasting some code into your browser.

Apple has revolutionized how we write with the introduction of its new Writing Tools, powered by Apple Intelligence. In beta on iPhone, iPad, and Mac, these tools allow you to select text and use intelligent features to summarize, proofread, or rewrite it until the tone and wording are just right. In a future beta, Writing Tools can even write original content for you.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

Not many people use their phone exclusively for making calls or sending messages today. If you're an Android user, the chances are high that you're using your phone or tablet for work-related activities. However, the basic set of apps and services your device was shipped with won't satisfy most users. The good thing is that Google Play Store has a nice selection of productivity apps for every task. Below you'll find a list of apps that will help you gradually optimize and organize your digita...

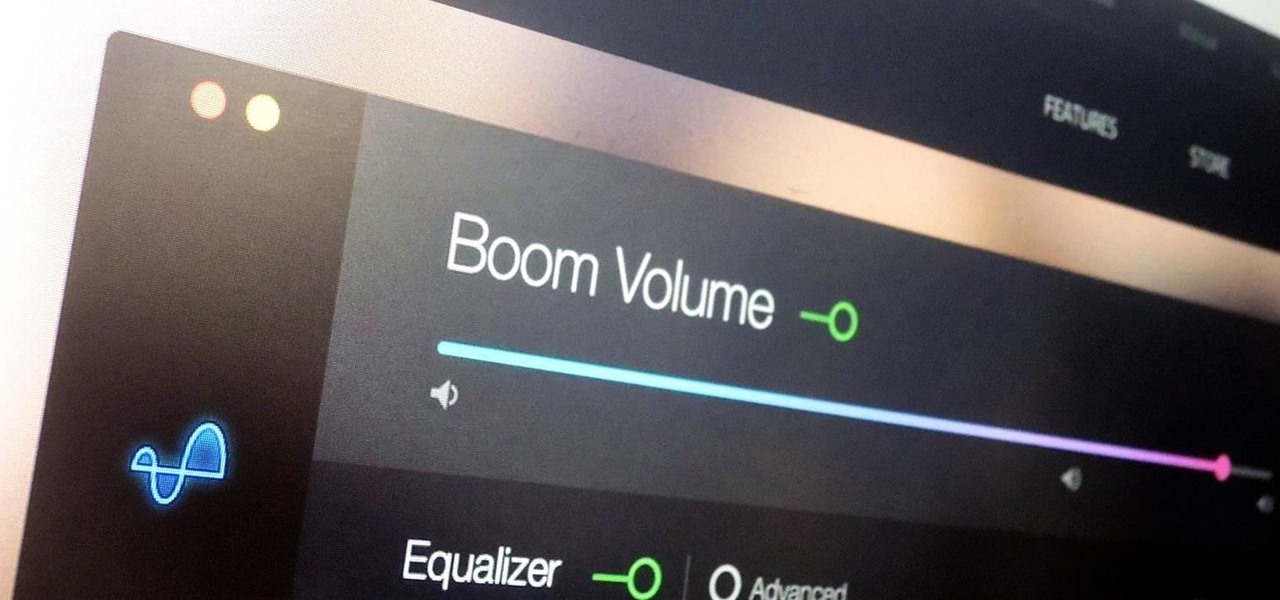
During a power outage at my apartment this year, I watched movies on my MacBook Pro instead of on my television. While I had no complaints about the screen size, I did have an issue with how low the audio coming from my speakers was. External speakers would help, but I don't want to buy them or lug them around every time I want to watch a movie.

Still on the fence about Apple's native Notes app? The latest Notes update for iPhone, iPad, and Mac is about to change your mind. With some fantastic new features and plenty of valuable tools from previous software versions, Notes is becoming a clear winner when it comes to saving important information from your personal and professional life.

Never being contacted for a job you're interested in interviewing for is a terrible feeling. It might make you feel inadequate as if your qualifications aren't up to par, but the problem might be that your resume isn't even getting read in the first place.

In this tutorial, we learn how to bypass a blocked site on a school computer. You will need a proxy to do this safely. First, go to a proxy site like Proxify. Going through here will prevent the school blocking system from coming up and ruining your fun. If you are blocked, you can use a text file document and run CMD on your computer. This would be the more technological way to do it. Try doing the website first to see if it works, if not, then you can try to change the firewall on the compu...

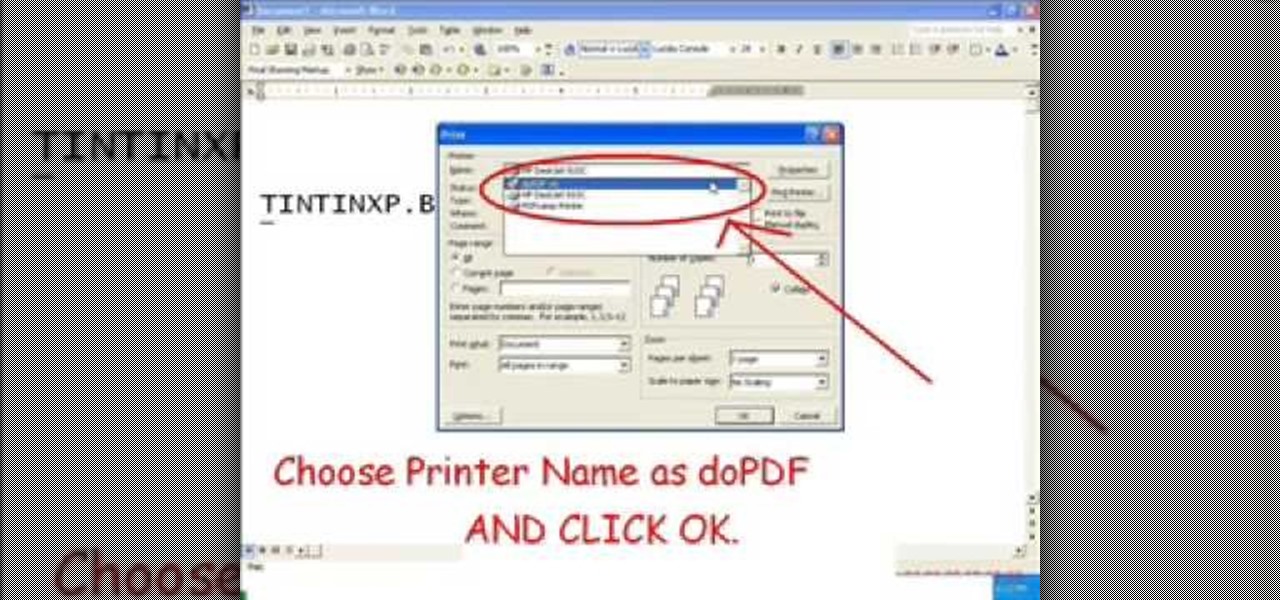
In this video tutorial, viewers learn how to convert word documents to PDF format. This task is very easy, simple and fast to do. Users will need to download a program from this site: DoPDF. Once downloaded and installed, open the program and open the file that you want to convert. Then click on File and select Print. Choose the printer name as "doPDF" and click OK. When a window pops up, select the location where you want to save the file. This video will benefit those viewers who have a tex...

This video will show you how you can simply type a symbol of a bomb in Microsoft Word. Using three easy steps, the symbol can be simply inserted into a word document. After opening up the Microsoft Word program, the user should then change the font type to a font which is called "Wingdings". This font will create symbols in the place of the regularly typed letters. In order to obtain the bomb symbol, simply type "M" (capital m) and the symbol will appear. The symbol should appear as a simple ...

In this Software video tutorial you will learn how to mount an image using Daemon Tools Lite. This software takes many different types files and puts them on a virtual DVD drive. Go to www.daemon-tools.cc and download the Daemon Tools Lite program. You then install it. After that double click on the icon on your desktop and it will appear on the bottom right hand corner of the screen. It will say Daemon Tools and the version. Right click > virtual Cd/DVD ROM. To mount an image, click on ‘mo...

So you spent all day customizing your phone. You tinkered with all the settings, searched the web high and low for the perfect wallpaper, and found an ideal icon pack to complement the color scheme. You go to sleep, proud of the work you accomplished when the unspeakable happens — your phone freezes and tech support is telling you to do a factory reset to fix the problem.

With iOS 11, Apple's very own Notes app will now come standard with a number of new features that aim to make it significantly more user-friendly and help it compete against more popular notepads like OneNote and Evernote.

A fairly hidden feature in iOS 10 let you turn websites and documents into PDFs, but thanks to the new Markup function in iOS 11, this process has become a lot more streamlined.

While clicking random links on the internet probably isn't the best idea to begin with, now you can rest easy knowing that your iPhone won't repeatedly dial 911 after tapping a malicious link in Twitter, Facebook, or other apps that use iOS's WebView.

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

All of Apple's products are praised for being extremely easy to use. So much so, that your grandma can pick one up and be a "pro" within a few hours. However, this isn't necessarily a good thing for us real power users who want more granular control of our devices.

Now that we have control over a victim's browser, we need to use some attacks to maintain the connection, or even better: upload a shell.

Welcome back, my tenderfoot hackers! I recently began a new series on digital forensics to help tenderfoot hackers from being detected and ultimately, incarcerated. In this installment of that series, we will look at recovering deleted files. This is important to hackers because you need to know that even when you delete files on your computer or on the victim's computer, a forensic investigator can usually recover them.

If you want to protect your word doc from other, you can give it a password. When anybody wants to open, it will ask a password. This way your valuable document will be secured from unauthorized access.

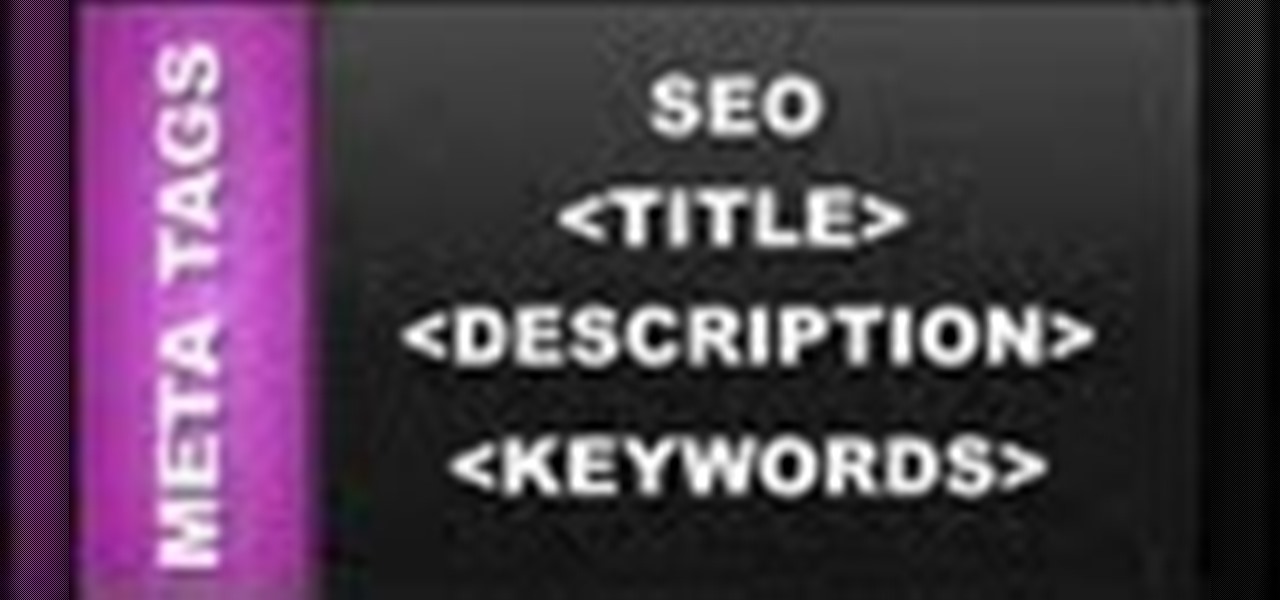
This web design tutorial will teach you how to add titles and descriptions that are relevant to your web page. Also you will learn how to add keywords for your website by using the website properties panel to add relevant keywords and phrases to your document in Xara Web Designer. The concepts taught for this web design tutorial are also referred to as Search Engine Optimization (SEO) meta tags.

In this web design tutorial we will show you how to protect yourself from losing your work just in case the program malfunctions, computer crashes or you accidentally forget to save document and so on. I highly recommend you utilize this Web Design Tutorial especially if you are working on large websites for clients.

Apple just released the fifth public beta for iOS 14 today, Wednesday, Aug. 19. This update comes one day after Apple released iOS 14 developer beta 5. It follows iOS 14 developer beta 4 by 15 days, and iOS 14 public beta 4 by 13 days.

Apple just released the fifth developer beta for iOS 14 today, Tuesday, Aug. 18. This update comes two weeks after Apple released iOS 14 developer beta 4, and 12 days after the release of iOS 14 public beta 4.

While the Reminders app has been largely ignored by Apple for years, iOS 13 finally makes it a force to be reckoned with. The app has been completely redesigned with easier navigation and more useful features that can compete with other task managers. After giving the new Reminders a shot, you may want to ditch that third-party to-do app you've been using.

For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

If you're an Android fan, you're probably familiar with Qualcomm's Quick Charge technology or, at the very least, what it can do. Quick Charge 3.0, the third generation of Qualcomm's fast-charging technology, is built into most Snapdragon SoCs and it's what lets you charge your phone's battery up to 70% power in just 30 minutes. What's not to like?

In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic.

Hello Hackers/Viewers, It is a new day, and you might be thinking, It is so boring, why not try to be cool with computers in front of my friends? That is why, I have made this tutorial to make fake viruses using notepad to look cool!

YouTube's main player interface got a pretty big makeover recently, but chances are, the new UI hasn't made it your way just yet. Google has a habit of slowly testing the waters as they roll out new features, so cool tweaks like this can take some time to reach all users.

Our workdays are typically filled with one thought: get as much completed as possible. Whether you face an inbox filled with tasks or just a project or two, both our bosses and our inner workhorses encourage us to knock out as many tasks as we can each day. But is being super-productive the best course of action for our minds and our employers?