In an attempt to increase advertising revenues, Snapchat introduced Discover back in January of this year, a feature that brought a handful of prominent media partners, such as CNN, ESPN, and Vice to your feed, along with their tailored news stories and videos.

There are few kitchen tools as elusive as the oyster knife. Many people—even seafood lovers—don't own one. If you do own one, it probably gets used so infrequently that it gets sent to the very back of the shelf where it proceeds to get lost. Then you accidentally find the knife once a month when you don't need it, but can't for the life of you find the sneaky little thing when you do need it.
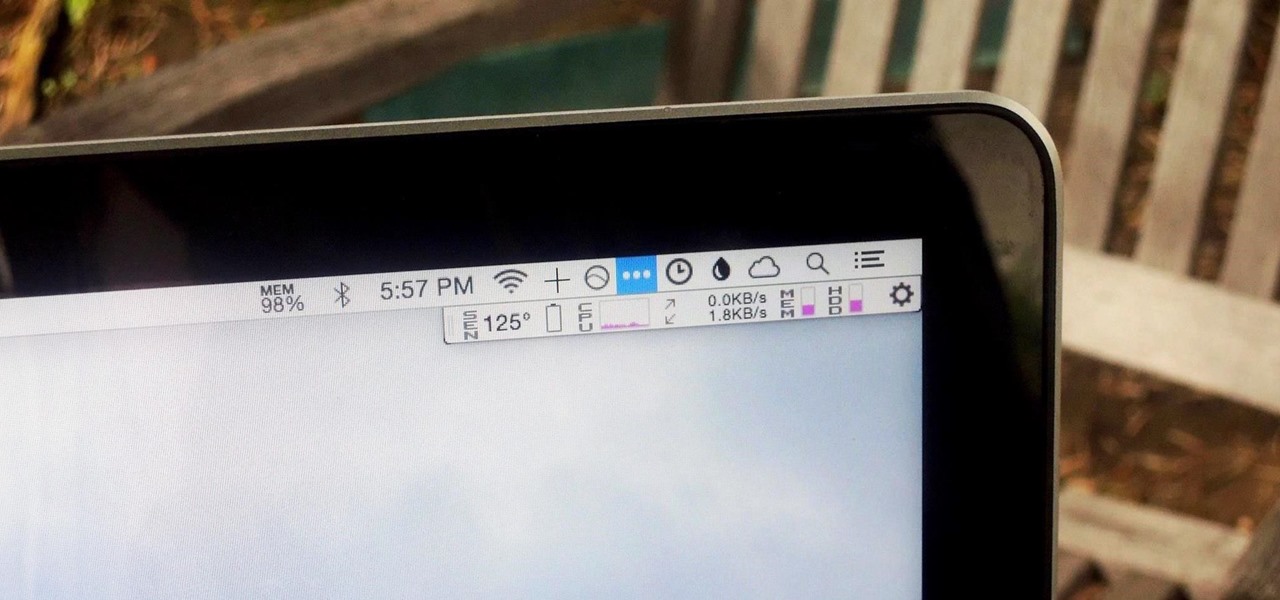
We recently showed you 8 menu bar apps that ever Mac power user should have, covering apps that allow you to control iTunes, eject drives, organize screenshots, and more—all from that tiny strip at the top of your screen.

This past weekend, one of the most notorious hacker organizations in the world, Hacking Team, was hacked by some unknown organization. The Hacking Team is an Italian company that sells it software and services to companies and governments (yes, my rookie hackers, there are legitimate companies who sell their services to governments—Vupen, being one of the most famous and lucrative).

A while back, I wrote review of my favorite hacking movies of all time. Two of my key criteria were; (1) how realistic was the hacking, and (2) are the hackers portrayed as the "good guys." This past winter, a new hacker movie was released, appropriately named Blackhat starring Chris Hemsworth (from Thor fame) as a blackhat hacker who is released from prison to stop a notorious and destructive hacker that only he can stop. Although the movie did very poorly at the box office, I thought it was...

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

Welcome back, my tenderfoot hackers! One of the issues we often encounter with Metasploit is how to add new modules. Although Rapid7 (Metasploit's owner and developer) periodically updates Metasploit with new exploits, payloads, and other modules, at times, new modules appear that are not added to the Metasploit repository.

A recently discovered bug in iOS 8's Mail app by Jan Soucek can allow the maliciously-minded to quite easily phish your iCloud password without you ever thinking something has gone awry. Using a bug that allows remote HTML content to be loaded in place of the original email content, unsuspecting victims would be prompted for iCloud credentials in a popup that resembles the native one found on iOS.

While the app switcher in iOS makes it easy to go from one open app to another fairly quickly, it's still not a great option if all you want to do is return to the previous app you were in.

The Ring/Silent switch on the side of the iPhone has always had one purpose—to toggle ring mode/silent mode. But in iOS 9, Apple gave us another choice, and that's locking the orientation of the screen.

I spend a lot of time helping friends and family with their tech problems, like clearing a browser's cache, scanning a Windows computer for malware, and speeding up a Mac. However, the issue I deal with most frequently revolves around forgotten network passwords.

The menu bar is a great place to perform quick searches, track battery life, and switch Wi-Fi networks on your Mac, but it can do way more than that if you let it. I've rounded up some menu apps below that not only have features that will boost your productivity, but are lightweight enough to run entirely from the menu bar.

Android Lollipop, introduced an array of new features and aesthetics that pleased many loyal users. One of those additions being the new heads-up notifications. Taking subtle inspiration from iOS, these notifications are visually appealing and can be easily dismissed or expanded, but they do require that you take an action before they go away immediately. Of course, you can always wait 10 seconds for them to disappear, but that can be really annoying if you're in the middle of a game or editi...

The Google Play Store may have fewer restrictions that its iOS counterpart, but that doesn't mean that all apps make the cut. Ad blockers and Xposed modules that bypass paywalls have never had a place on the Google Play Store, which makes tracking their app-updates a painful process.

While some of the additions to the emoji keyboard in iOS 8.3 have been criticized for actually doing the opposite of their intended purpose, they've been well received overall. But the biggest winner of the new emojis was one that actually wasn't even released—the "Vulcan salute" emoji.

With an Android device, you can replace almost any default app with a third-party offering. Don't like your home screen app? Replace it. Tired of the text messaging interface? Upgrade it. The same can be said for Android's lock screen. But while many third-party lock screen apps are available, so far, only one has been designed with the Samsung Galaxy S6 and its fingerprint scanner in mind.

The Apple Watch may be a much simpler device than your iPhone, but that doesn't mean it's free of bugs, glitches, and crashes just like your other devices. A common problem that you'll run into is a frozen screen due to a malfunctioning app. While this can be frustrating, the solution can be as simple as a quick reboot.

One of the many additions that appear on Android 5.0 Lollipop is a handy menu that lets users correct for or simulate different types of color blindness. While Google didn't flip the switch on this new feature until Lollipop was released, it turns out they had been working on it for quite some time.

Technology has progressed by leaps and bounds and has blessed people in a number of ways, but at the same time, it has troubled them also. Computers are now used in every aspect of life. No matter if you are a businessman, an employee, a student, or even a housewife, a computer can assist you in your routine work. You save your personal information, documents, and other similar sensitive stuff on your computer that can hurt you if they get compromised.

Android's auto brightness feature was recently updated, and as of version 5.0, a new "Adaptive brightness" feature was added. This allows users to set a preferred overall brightness level, but still have the ambient light sensor adjust the backlight accordingly.

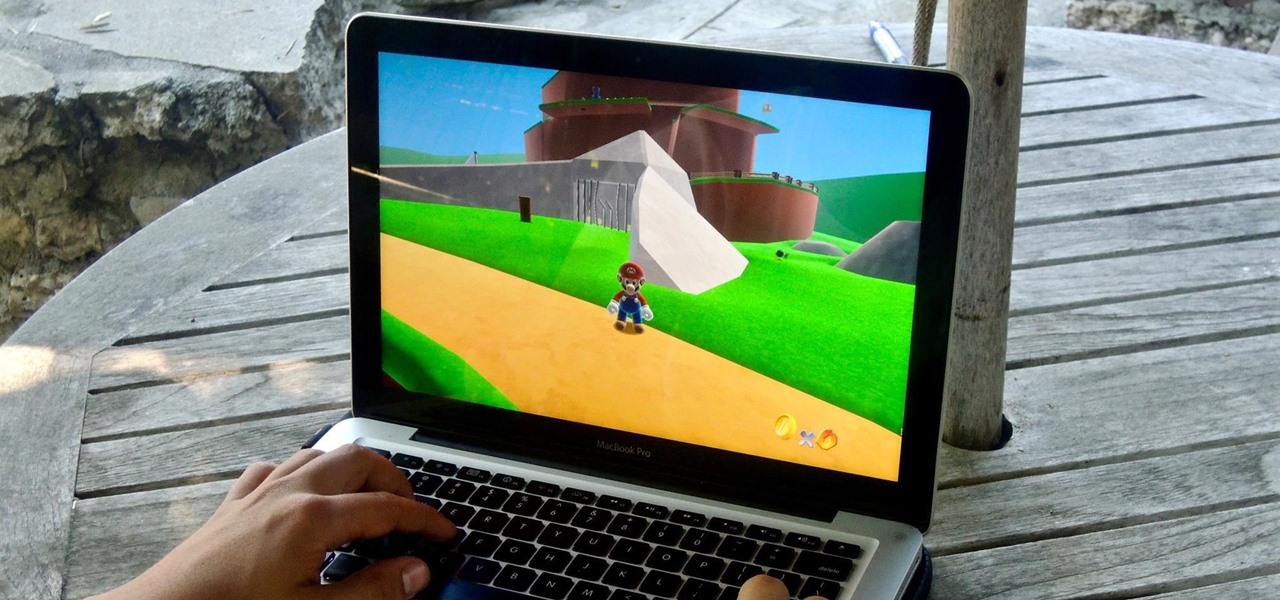
Yup, you read that right. As of now, you can actually play the first level of one of the most popular video games of all time—Super Mario 64—directly in your web browser.

Instagram recently rolled out their new Layout app that helps users build photo collages more easily, and it's quick and easy to use with great results. Unfortunately, only those with an iOS device can enjoy Layout at the moment, with the Android version slated for release "in the coming months." Luckily, there are a trove of alternatives that you can use right now, and here are the three we like best.

As an Android user, there aren't many elements of my friend's iPhone that I find myself envious of, because anything he can do on iOS, I can surely find a way to do on Android...often better.

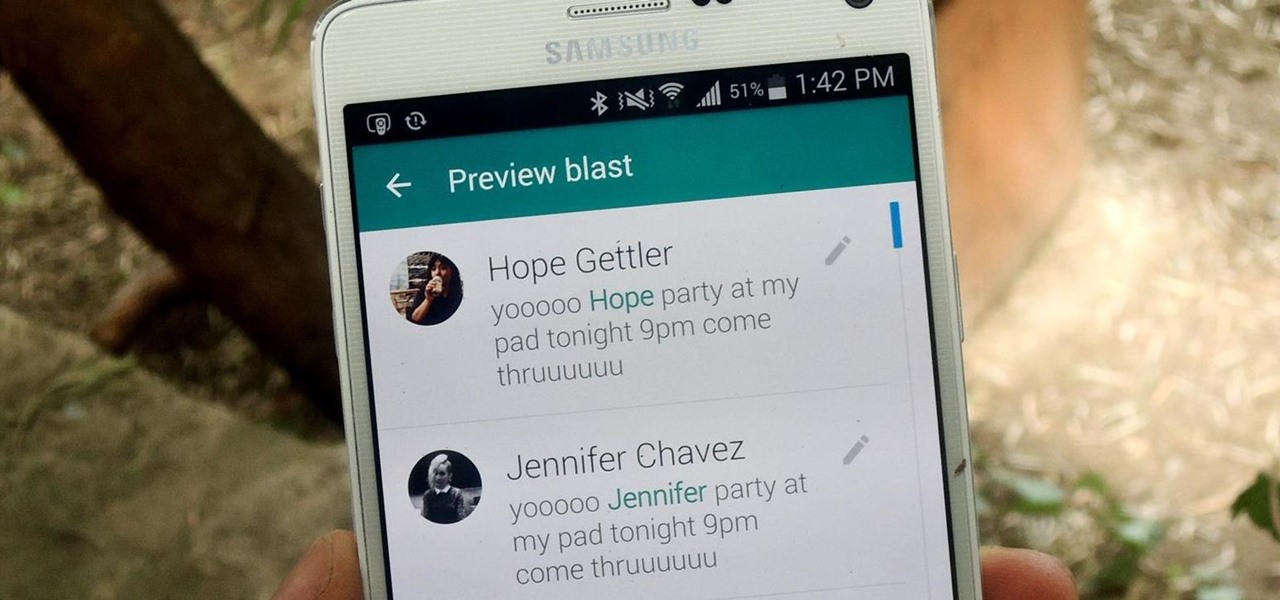
We've all received those impersonal mass text messages, whether we're getting invited out to a birthday party, graduation celebration, or just a group dinner or outing.

It's 3 a.m. and you're wide awake—your mind is running wild with worries, workplace stress, and panic about the day that lies ahead. How can you possibly slip back into sleep and snag a few more hours of rest when you're so anxious?

When going out to eat with friends, it's inevitable that one person takes charge at the end of the meal to split the bill. They whip out a pen and begin asking everyone what they ordered, carefully dividing, adding, and subtracting on the back of the receipt for everyone to use. Unfortunately, that never seems to work as intended. One person will end up paying a little more, while another will pay less.

Samsung's got a pair of beautiful new flagship devices coming out this spring that will surely top the sales charts. The Galaxy S5's successor is truly worthy of that title, but a second variant with a curved display turned heads at Mobile World Congress this weekend.

Here's a short and to the point tutorial teaching how to Bass Boost your songs with Audacity. To download Audacity for FREE you can go to the official Audacity website. You may want to Bass Boost your songs for many reasons, so here's a tutorial on how to do just that with the popular, Free, and easy to use software called Audacity.

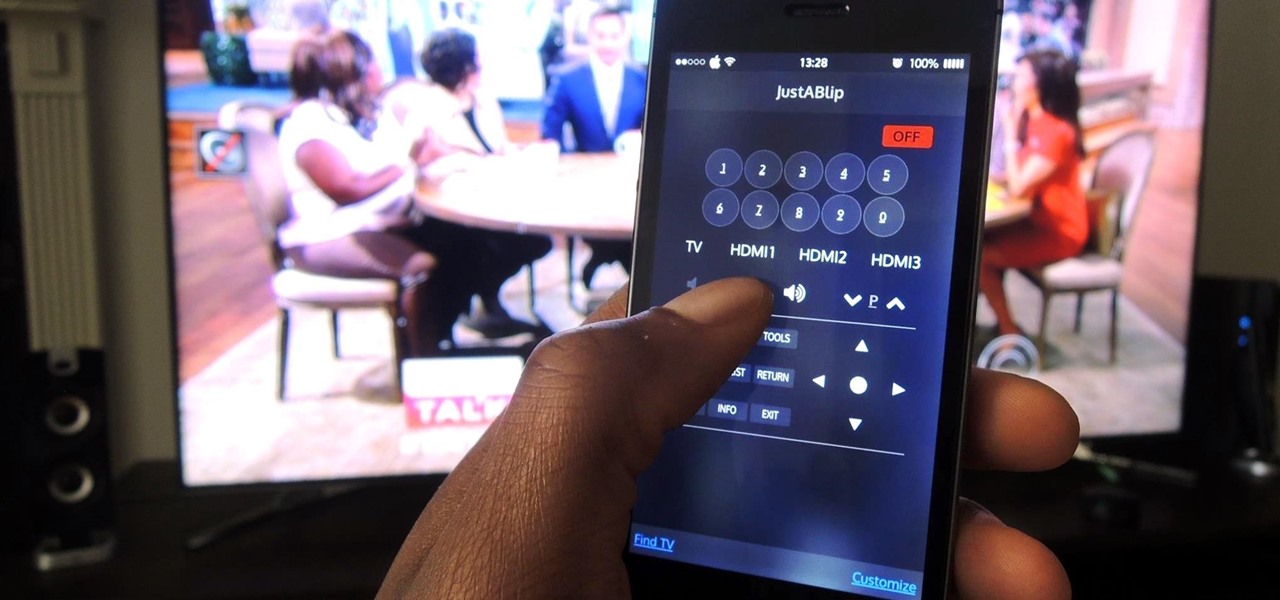
After I traded in my Samsung Galaxy S5 for an iPhone 5S, the one feature I truly missed was the Smart Remote app. My television remote was broken and the S5 saved me from, you know, actually having to get up and change the channel.

Back when CRT and plasma monitors were still a thing, screensavers served a purpose beyond just aesthetics: the moving images and patterns prevented static images from being burned into the display.

Before phones became mobile-gaming, music-playing, app-downloading devices, they were used simply to make convenient, cordless phone calls. There's so much on phones these days that a passcode is needed to keep everything secure, and making calls is now more complicated.

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

While shortcuts to your Camera and third-party apps like Snapchat are great for capturing fleeting moments, it still takes a few seconds to open them and snap a photo. That means you could potentially miss a great shot if you're not quick enough. But now there's a super-fast way to capture and send photos without having to waste time unlocking your device.

It's been over a year now since Google introduced a visual way to track down which tabs are playing audio in Chrome, something that was previously only available using third-party extensions. However, they still didn't give an easy option for shutting those tabs up without having to stop what you're doing.

Looking back at my childhood in the '90s, I can't help but feel like I was deceived. Movies that took place in the "future," like in the year 2015, would showcase awesome technology. You know, self-driving or flying cars, hoverboards, and virtual displays controlled with hand gestures—so where are they?!

With over a billion monthly active users, it seems that Facebook is nowhere close to being dethroned as the most popular social media service in the world (sorry, Ello). While their stats may be impressive, it doesn't mean that Facebook is as good as it can be.

The Nexus 6 came with a hidden kernel module that allowed for double-tap-to-wake functionality, essentially letting you turn your screen on just by tapping it. A simple root app allowed us to activate this feature, which meant we were always two quick taps away from waking our device.

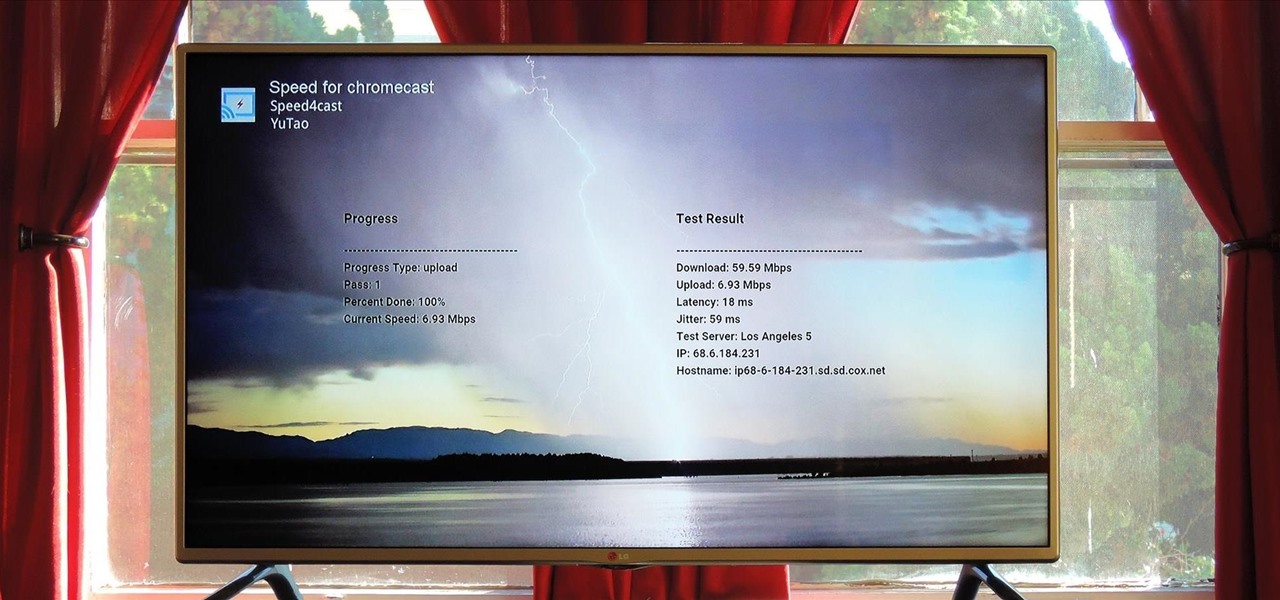
At its core, the Chromecast is essentially a web browser on a stick. When you cast content from your computer or smartphone, all you're really doing is telling the Chromecast which website to load.

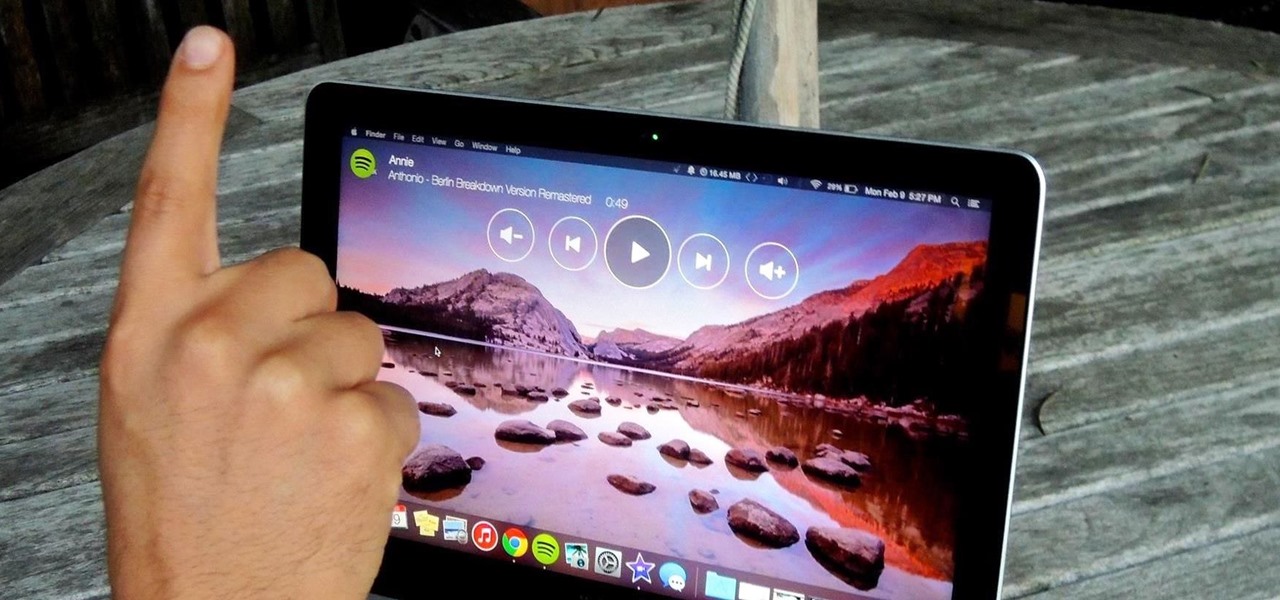
Using shortcuts to control the playback of your music on your computer makes life just a little bit easier. Instead of needing to open up an app, we've shown you how to use keyboard shortcuts, a Notification Center widget, and even Siri to control music on your Mac. Now we're going to show you how to use your iPad, iPhone, or iPod touch as a remote control.