
How To: Facebook Credentials Revisited
Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.


Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.

Welcome to my tutorial where Voidx and I will be expanding on my previous article to provide more clarity into the logic of the code.

With the sheer amount of photos, videos, and miscellaneous files we place on our computers, proper organization becomes necessary. Not only so that we can quickly get to a file when it's needed, but also to declutter folders and keep them from looking like random file dumps.

Greetings. This how-to on hacking Windows 7/8/10 etc. admin account passwords using Windows Magnifier is focused on adding, changing, or deleting an admin level account on a Windows 7/8/10 etc.

Do you have an Alfa AWUS036NH Wi-Fi adapter that claims it can go to 2000 mWs, or some card that can supposedly transmit power over 1000 mW? If so, you may have run into problems setting your card's TXPOWER higher than 30 dBm, which is about 1000 mW. Well, I will show you how to break that barrier and go as high as you want!
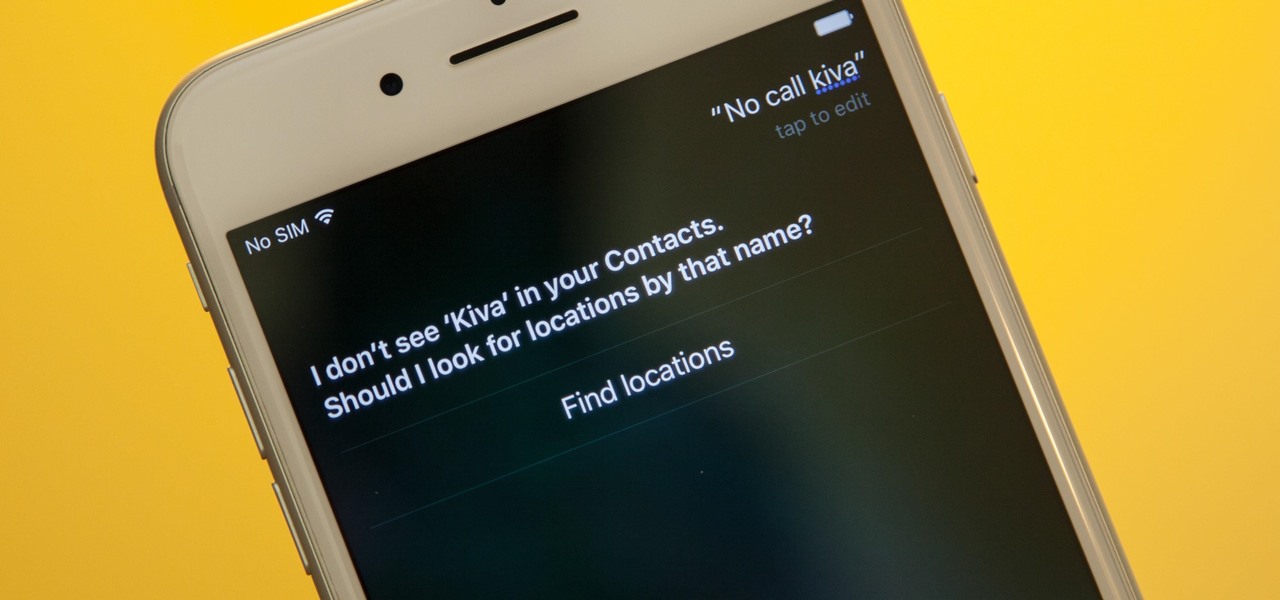
Siri makes it easy to call almost any contact on your iPhone with just a quick verbal command. I say almost because counterintuitive name pronunciations such as Caoimhe, which is actually pronounced "Keeva," will confuse the hell out of Siri. Luckily, there's a way to get Siri to understand pronunciations for the tricky names in your contact list ... it just takes a little grunt work on your part.
Hello! I invite all the readers, interested in space, to discover the origin of the names of the planets in our galaxy. Just simply follow my words,... Step 1: Planets and Stars
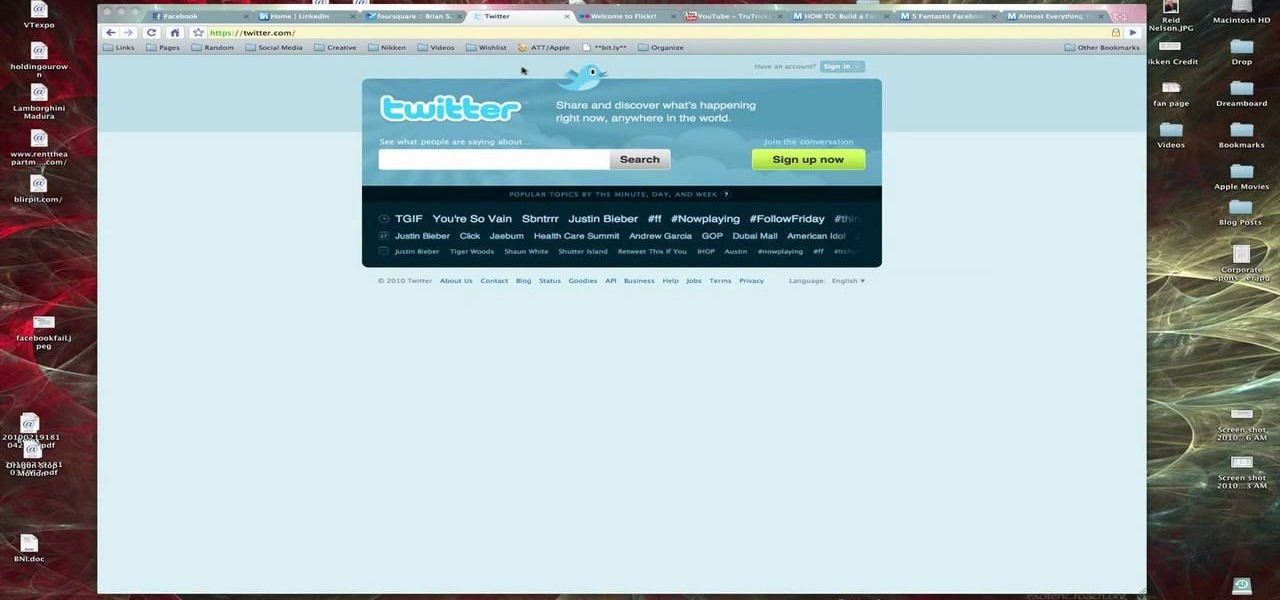
In this video, Brian from Trutricks shows us how to create a new Twitter account. First, go to Twitter and click on the "sign up now" button. You will now be brought to a new page where you can choose your user name and enter your email, password and full name into the information boxes. Once finished, click "create account". After this, you will be able to follow people you want as well as have other people follow you. Once you are ready to tweet you can type whatever is on your mind in 140 ...
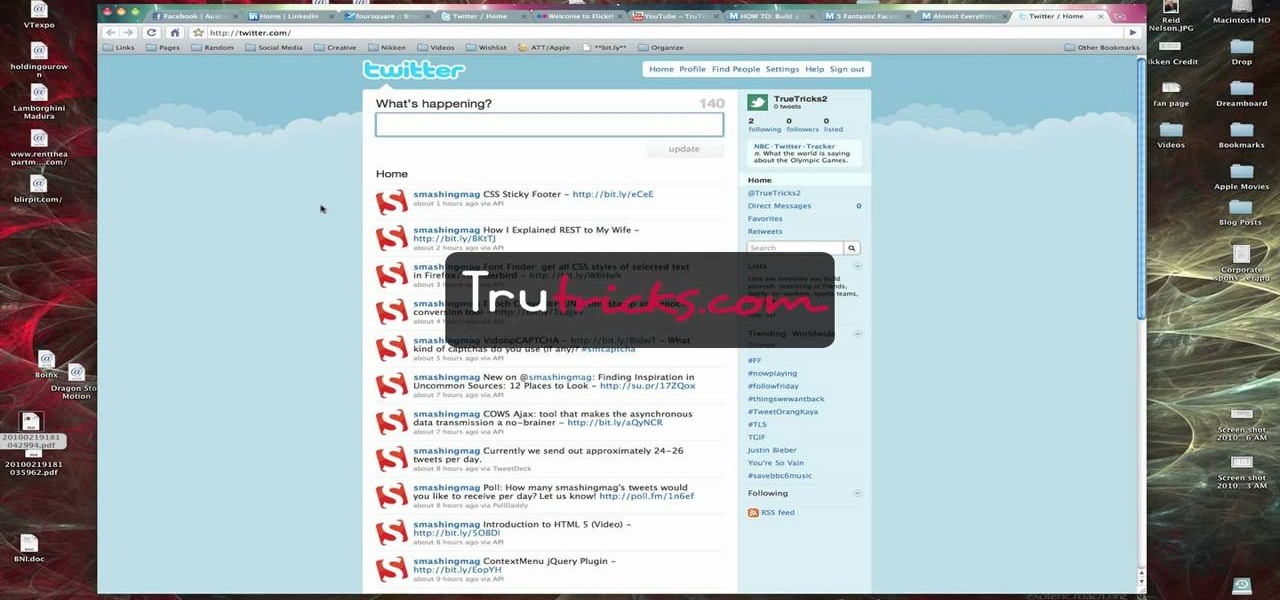
Brian explains us how to use Twitter, one of the best social media networks out there. One thing to notice is that Twitter allows you to send text messages up to 140 characters. In the right corner you can see you account name and your avatar which can be changed from the settings menu. Twitter allows you to follow people and be followed by people. Basically when you follow people you will be able to see messages they post and when people follow you, they will see what you post. Twitter is a ...

Stay tuned for the always enjoyable Cooking With Dog. This cooking show is hosted by a DOG named Francis! The show demonstrates how to make popular Japanese dishes.

Stay tuned for the always enjoyable Cooking With Dog. This cooking show is hosted by a DOG named Francis! The show currently focuses on how to make popular Japanese dishes. This video demonstrates how to make Katsudon (Tonkatsu Deep Fried Pork and Egg Bowl).

Stay tuned for the always enjoyable Cooking With Dog. This cooking show is hosted by a DOG named Francis! The show currently focuses on how to make popular Japanese dishes. This video demonstrates how to make kakiage soba (mixed tempura soba noodles).

Stay tuned for the always enjoyable Cooking With Dog. This cooking show is hosted by a DOG named Francis! The show currently focuses on how to make popular Japanese dishes. Learn how to prepare Japanese Ichigo Daifuku, aka strawberry Daifuku. This is a Japanese dessert.

This video tutorial is in the Computers & Programming category where you will learn how to secure your wireless internet connection. If you don't secure your wireless internet connection you are allowing others to enter in to your network. Open the set up CD and first change the network name from the default name to anything that you like. For this go to step 3 of 'naming your network', type in your network name and click 'next'. Then you enable security on the network by choosing 'WPA2'. Nex...

Pronunciation is key to learning any new language. Before diving into the vocabulary and basic phrases, a good approach is to listen and try and get your aural perception honed in. A new word or phrase, like "je m'appelle" in French, is awesome to learn, but it's important to learn it correctly: that starts and ends with pronunciation.

Every home is a little different, and for a smart home app to work, it has to be able to be customized to work with each person's unique setup. With the iPhone's Home app, everyone can set up a smart home just how they want, including the number and names of rooms, and where those rooms are in the house.

Ever since the introduction of Google's SafetyNet feature, it's been an ongoing battle with apps trying to detect root access. For a while, there was a lot of back and forth between Magisk and certain apps. Pokémon GO was a high profile example of an app aggressively checking for anything related to root. Luckily, Magisk has made great strides to keep apps from detecting root for good.
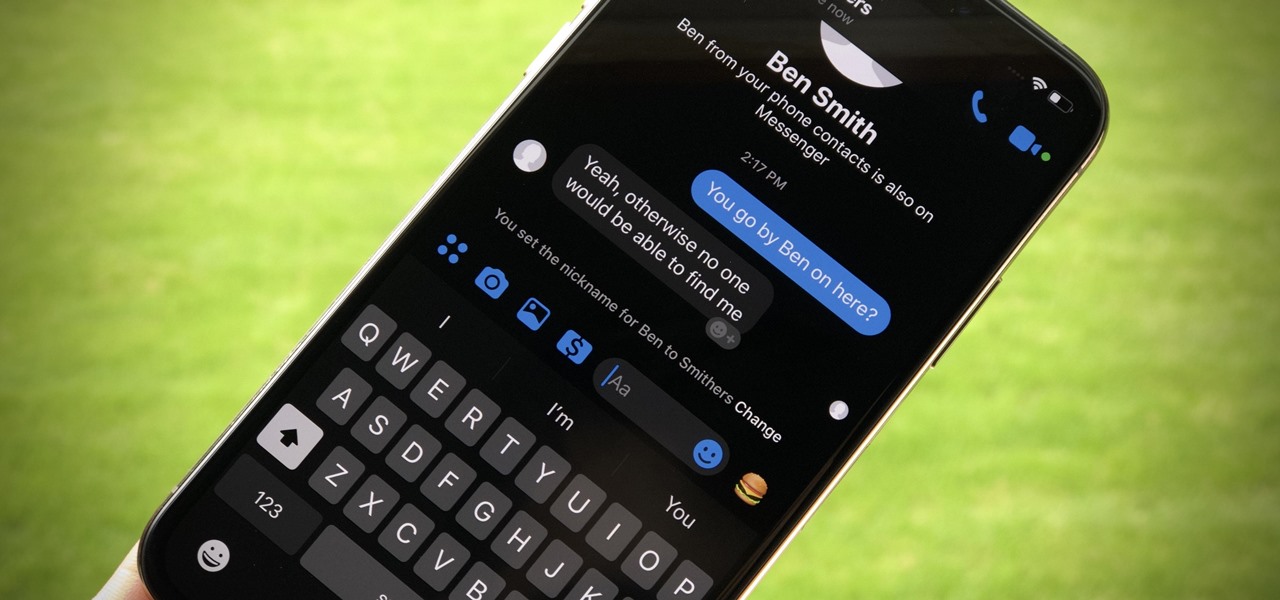
For the most part, people use real names on Facebook. That's all fine and well for keeping tabs on those you know, but it can make friendly Messenger chats feel oddly formal. Skirt around this stiffness by giving your friends nicknames in Messenger for Android and iOS, so your conversations reflect the way you and your friends communicate in real life.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.
Deep down inside, Android is really just a fork of Linux, the popular open source desktop OS. You can see traces of its roots everywhere, and this lineage still holds a certain appeal with many Android fans. If you're in that boat, you'll love the newest notes app we just found.
Unless you're experienced using the Linux terminal, running ADB and Fastboot commands can get confusing very fast. The problems often stem from having to hunt for various files — usually IMG or ZIP files that you need to mod your Android phone — and then move them to your platform-tools folder, which, depending on how you installed ADB in the first place, could be anywhere.

Cyanogen, Inc., the for-profit company that spun off from its CyanogenMod roots several years ago, has announced that they're shutting down all of their services. The company's impending demise shouldn't directly impact many Android users, but the announcement does have one major repercussion: The servers that used to host the popular CyanogenMod custom ROM have now been shut down.

It's about that time again. Spring weather is here, a new season of Game of Thrones is upon us, and we're getting ready for the next version of Android.
Before I start a series on remote exploitation, I think we should learn the basics of Perl. Perl, Ruby, C, C++, Cython and more are languages that some penetration testers just need to learn. Perl is a great language for multiple things, sadly, like many other scripting languages, it is limited by the environment in which it is designed to work in.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.
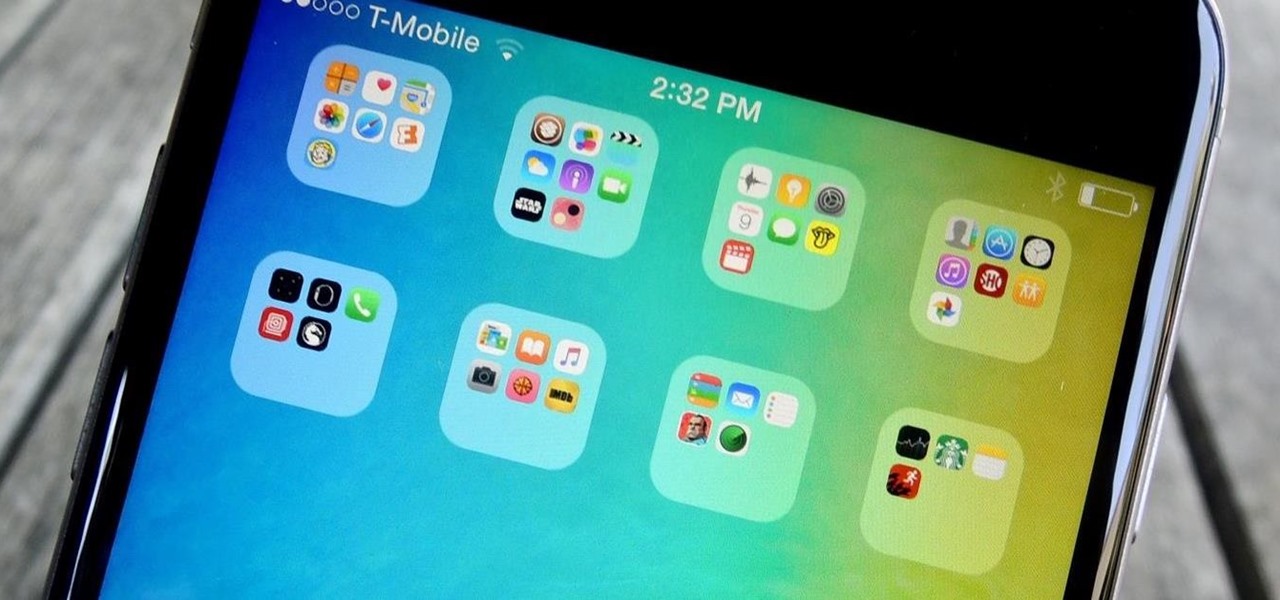
You know what's in your folders, so it's not always necessary to label them and ruin that clean look you're going for on your iPhone's home screen. I mean, how many folders am I going to have to title "Stuff" or "Junk"?

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

Changing an app's name on your home screen is not something you can do on stock Android or TouchWiz, but it should be. If you think of it merely from a customization angle, sure, it's not a big deal, but having the ability to alter an app shortcut's name can do wonders for cleanliness and being able to distinguish from similar icons.
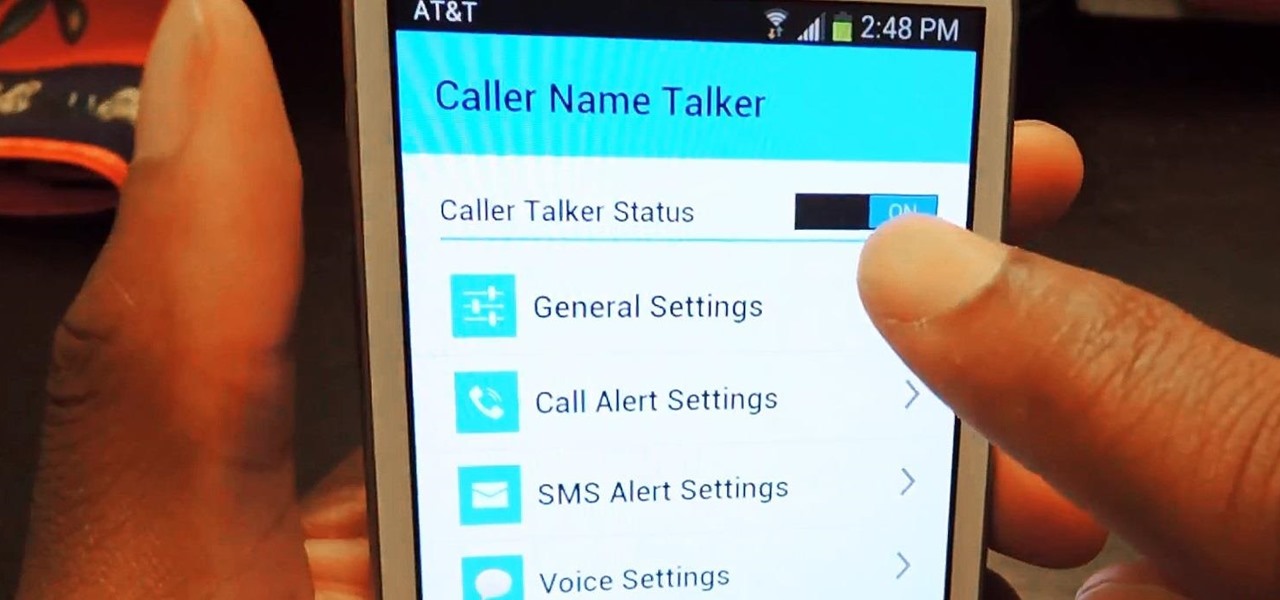
Wouldn't it be cool to know exactly who is calling or messaging you without ever looking at your phone? It'd be a great way to keep you from reaching into your pocket or purse every time you get a message, and an efficient method to ignore people you'd rather not deal with.

In 2006, everything that revolved around my world shattered into tiny pieces as I learned that scientists had decided to rescind Pluto's planetary status. Given the ol' Jeff Probst treatment, Pluto was officially voted off our solar system in the blink of an eye, leaving us with only eight planets and a whole load of useless textbooks. The primary reason that Pluto was demoted down to a "dwarf planet" was due to Pluto's largest moon, Charon, being about half the size of Pluto; all the other p...
Change object colors via ActionScript in Flash 8

Krazyboytx shows viewers how to dress and fix a love candle or come to me candle. First, you need to have a love mix, that is either prepared by you or that you have bought. You also need to use a sedative or a hallucinogen - such as salvia. You will also need dove's blood and some love oil. You will also need something to pierce the candle with. You need to inscribe on a piece of paper your name three times on the parchment paper. Now, write love over your name three times. It maybe messy so...
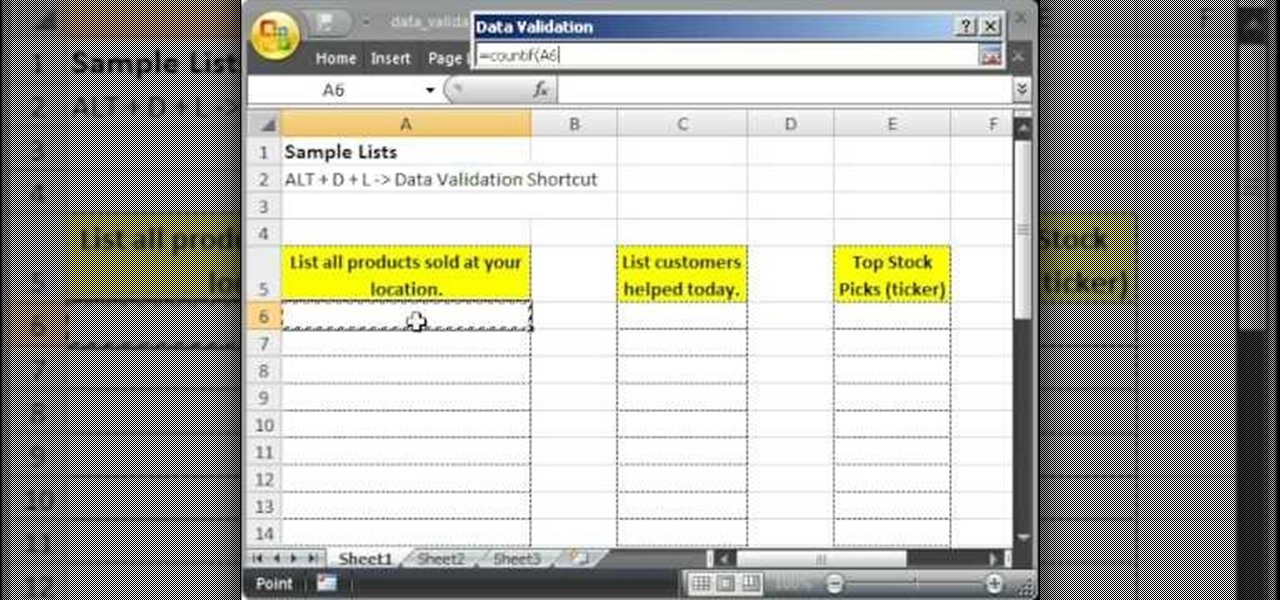
This tutorial describes how to make a list with unique values in Excel.This procedure makes the defined cells in a column (called as list) NOT to accept repeated values, which makes the list more simple, readable, easy to manipulate when preparing a worksheet.
Now you can find your IP address if you need it and you don't know it, it very easy. Or if you have problem with a person on the internet, now you can discover who that person is. You can find her/his IP address and after that you can find her/his real name. But after you find the IP that you were looking for, you have to check if the person who own this computer is in your network, because if you want to find his/her name, the program works only if the owner is on your network. So if you are...

Join professional skateboarder Ryan Smith as he teaches you how to perform a big spin on your board. This video tutorial will how you just how to do the big spin trick, perfectly.
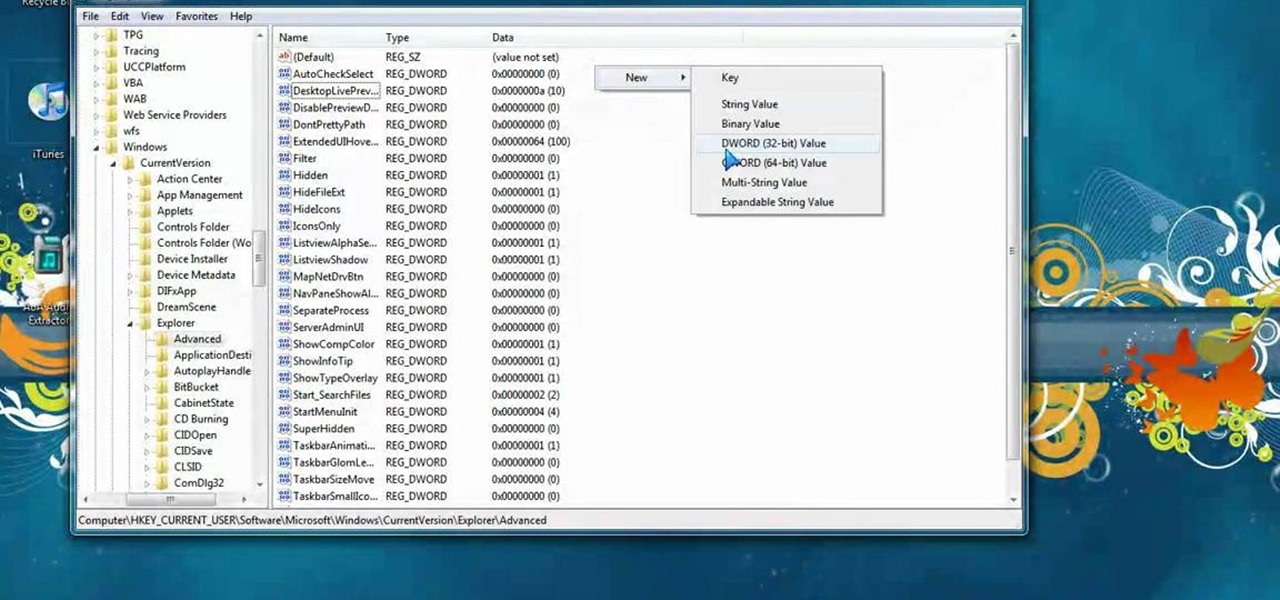
In this video, we learn how to tweak Aero Peek and Desktop Live Preview on Windows 7. First, go to registry editor, then current user, then software, then Microsoft, and go down to Windows. After this, click on current version, explorer, and advanced. Now, right click on the white space and click "new keyword value" and name it "desktoplivepreviewhovertime". After this, double lick and change it to decimal, then change the value data to 10. Next, create another keyword value and name it "Exte...

Skype is definitely a revolutionary software for keeping in contact with your loved ones. It's a phone on the internet! What couldn't be good about that? If you are in Orlando, your spouse is at a conference in El Paso, your daughter’s at college in Raleigh, and your son is working in Dubai, you can keep the family in touch with Skype, a software application that lets you make free video calls over the internet.
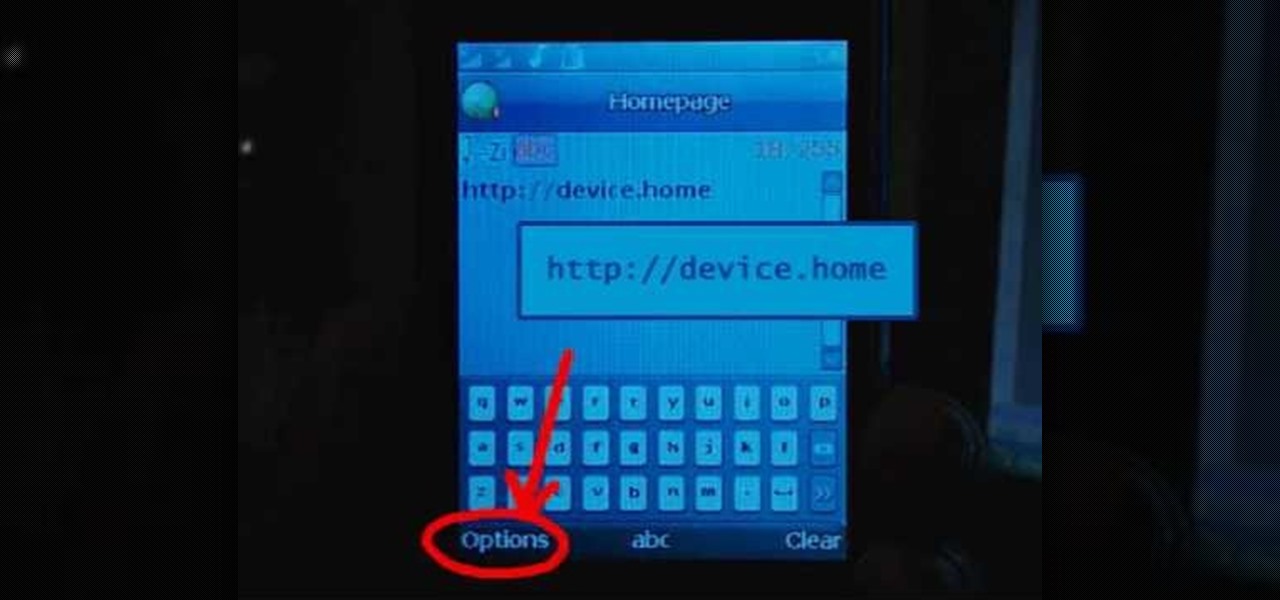
Learn how to set up Internet on iPhone clones with this video. *First thing you need to do is to make an AT&T GPRS data account.

Teach your dog the names of objects. Sometimes puppies need to learn about the world around them in the same way that humans perceive the world. How else could you communicate that the vacuum is safe? With words, of course!

LEarn how to say the names of the modes of transportation in French