The "Plattsburgh" knot is named after the small town in up-state New York where Thomas Fink, inventor of the knot and co-author of the book "The 85 ways to tie a tie", is born. In contrast to its narrow close relative the "St. Andrew", the "Plattsburgh" produces a symmetric knot characterized by a broad cone with a narrow opening.

Invented in 1948 at Harry's Bar in Venice, the Bellini's name honors the sheer pink shades in the work of Italian painter Giovanni Bellini. It's also a great drink to celebrate slightly lesser art forms—like, say, brunch.

The Red Cine Application is essential to learn if you plan on shooting with the RED ONE camera. This tutorial goes over output settings, including path, name, size and format.

Cinderella's plight has given mopping a bad name—but don't let poor PR keep you from a bright, shiny floor.This video will show you how to mop a wood floor.

With its psychedelic name and shocking color, an Electric Lemonade might be a mind-blowing potion dreamed up by some mad hippie scientist—but who cares? It's a great drink to light up your summer night.

An excellent dessert drink, the Sombrero is basically a White Russian with one less alcoholic ingredient—and a south-of-the-border name.

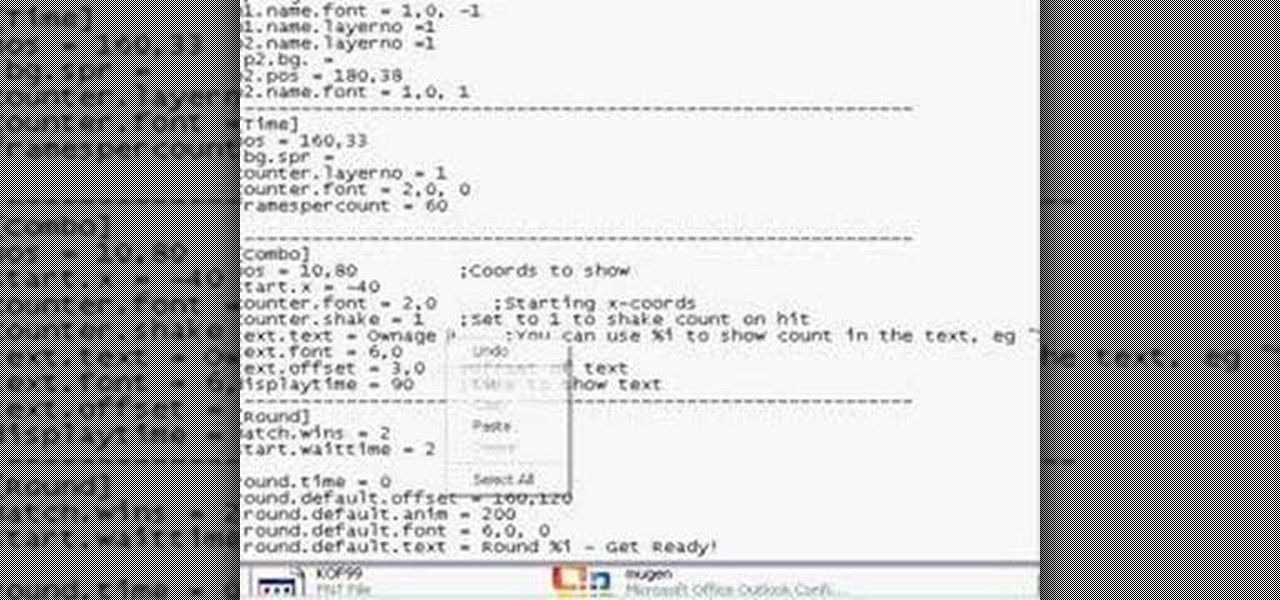
how to change the Mugen combo marker in that displays on your screen when you complete multiple hit combos into any name or phrase to your liking.

A string trimmer is a useful tool for maintaining your lawn. Learn how to use it correctly and safely with this tutorial. Another name for this tool is a weed whacker.

Benny from askbenny.cn teaches you the names of the four seasons in Mandarin Chinese and how to talk about them.

Benny teaches you how to introduce yourself - including your name and age and where you and your family are from - in Mandarin Chinese

Chef Sanjay is celebrating the success of his webcast by making you one of his favorite Indian chicken dishes: chicken 65. Learn how to make it and how it got such an odd name!

Known by a few names, the "Von Flue Choke" is a great defense against a guillotine from side control.

San Chin No Hojo-Undo is one of the requirements for the 10th kyu (technically still a white belt, but with a yellow stripe) in Pan Gai Noon Ryu (Japanese name: Han Ko Nan Ryu) form of Okinawan Karate. This video breaks down how to execute it properly.

In this video you will learn how to do a stretch called bo flexibility (or bo flex). It is pretty clear from the name, that you are using the bo weapon to do stretching exercises to increase flexibility.

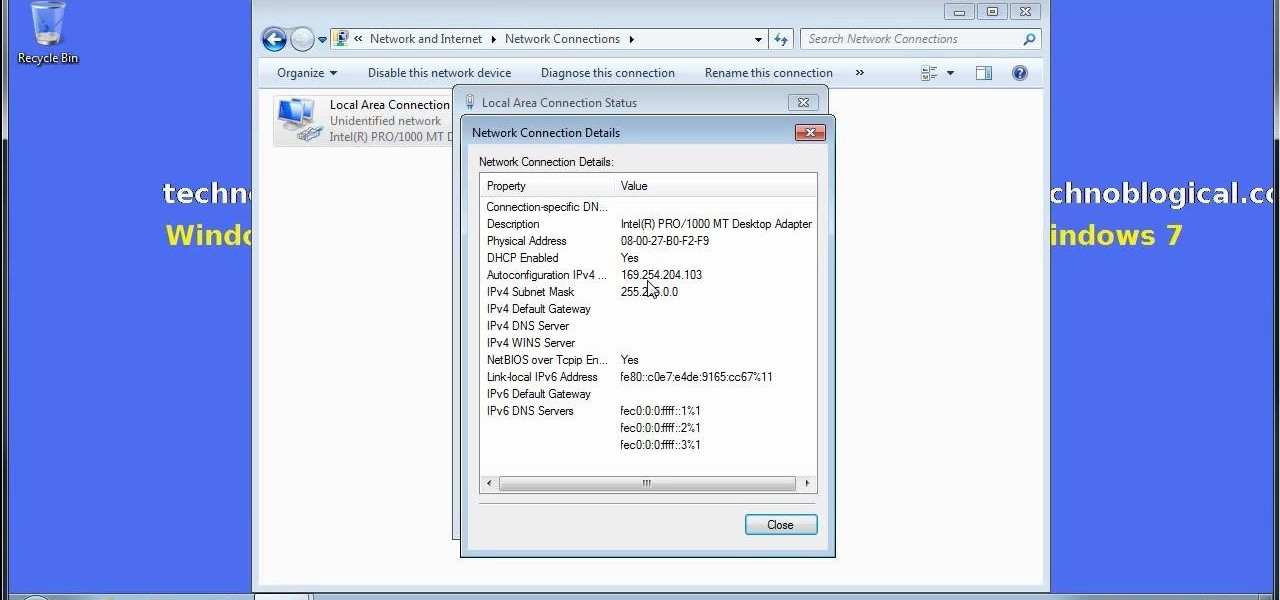
DNS spoofing - how to use the hosts file in Windows XP to block unwanted spyware/popups/etc, block programs from reporting to a site, filter/block/redirect websites, and locally create forward lookups (IP to name resolution in network)

It's been called the "Sin City" effect, and a myriad of other names, but really all you're doing is adding selected color to black and white photos or comic-type images. See how Bert suggests achieving this effect in his tutorial.

This "glow swirl" effect is doable via drawing a flashlight really fast at night and then taking snapshots of its path (we used to draw fun doodles and write our names in "glow" lighting with our roommates in college). However, since such night snapshots are hard to capture on camera, Photoshop can do you for you instead in far less time.

Want to share Internet connectivity between two computers without a wireless network but have an extra CAT5 ethernet cable? You're in luck. This home networking how-to will show you what to do to get your machines talking not only to one another but the web at large.

Remember those old vinyl records? Remember jumping on the 8-track bandwagon? Switching over to cassette tapes? How much money you spent converting your music collection to compact discs? To MP3s?

Has you rent check bounced again for no apparent reason? It happens to everyone, but if you're roommate needs the money fast, you need to fix it fast, and wire transfers are the fastest way to give money to someone else. Executing a wire transfer is as easy as making one phone call.

Ipad is a revolutionary device from Apple with some amazing features. One of the major functions of Ipad is to serve as a E-book reader. Apple provides an application called Ibooks using which you can read ebooks on your device. You can also browse and purchase new ebooks using this applications. Launch Ibooks from your applications menu and it will take you to the collection of books that you already have on your device. Click the store button to visit the books store. From the store you can...

Do you love music and need a little extra cash? Do you think you have a knack for entertaining others with your rockin' playlists? Check out this video and learn how to turn that musical mind into a career as a wedding DJ. The most memorable part of the wedding reception is the music and dancing and you could be a part of it! Follow these steps and have people complimenting you on your awesome tunes as they leave the reception.

Starting an independent record label, like starting any other business, requires a well-conceived plan with clear goals. Check out this tutorial and learn how to take your love of music and turn a profit.

If you love hip hop and break dancing, you are already almost there. The steps to becoming a B-Boy are pretty easy, and if you check out this video you will learn exactly how to become one.

Plagiarism is a serious offense, even if you are copying from the web. With this tutorial, learn how to cite websites properly using MLA format and avoid any trouble.

In this economy being competitive for a job means your application must stand out above the rest. Here's how to write a cover letter to successfully introduce your resume. Make sure your cover letter follows business letter format. Your name and address must be written at the top left corner. The employer's name and address are written just below. The letter should be addressed to a specific person within the company. Paragraphs in a business letter are not indented, but instead are left just...

Hello, my name is Nicole Valentine and on behalf of Expert Village, I'm here to talk to you about how to coordinate birthday games for a birthday party. We're going to now talk about how to play the game think fast. This is a very simple game. Just use a ball that you have at home, go to your kids room, go to the toy box and choose an easy ball and you would like to line the guest of the party in a circle. Choose a theme. If it's a boy's party, you might want to go with Power Rangers, or spor...

Hello, my name is Nicole Valentine and on behalf of Expert Village, I'm here to talk to you about how to coordinate birthday games for a birthday party. Now we're going to discuss another birthday game and this one also happens to be an oldie but goodie. And this game is called connect the dot. This is a perfect game if you want the kids in your birthday party to kind of calm down. Let's say after they've eaten, or even the birthday cake. But you want to draw about 4 lines of dots containing ...

Directing a message at a specific person in a group conversation, or to a select few people in the group, can be difficult if you're in a particularly active or hectic chat. Notifications and badges on your iPhone can help you keep track of important messages, but it's still easy to miss one meant for you and not the entire group — which is why you can now mention contacts, or get tagged, in Messages on iOS 14.

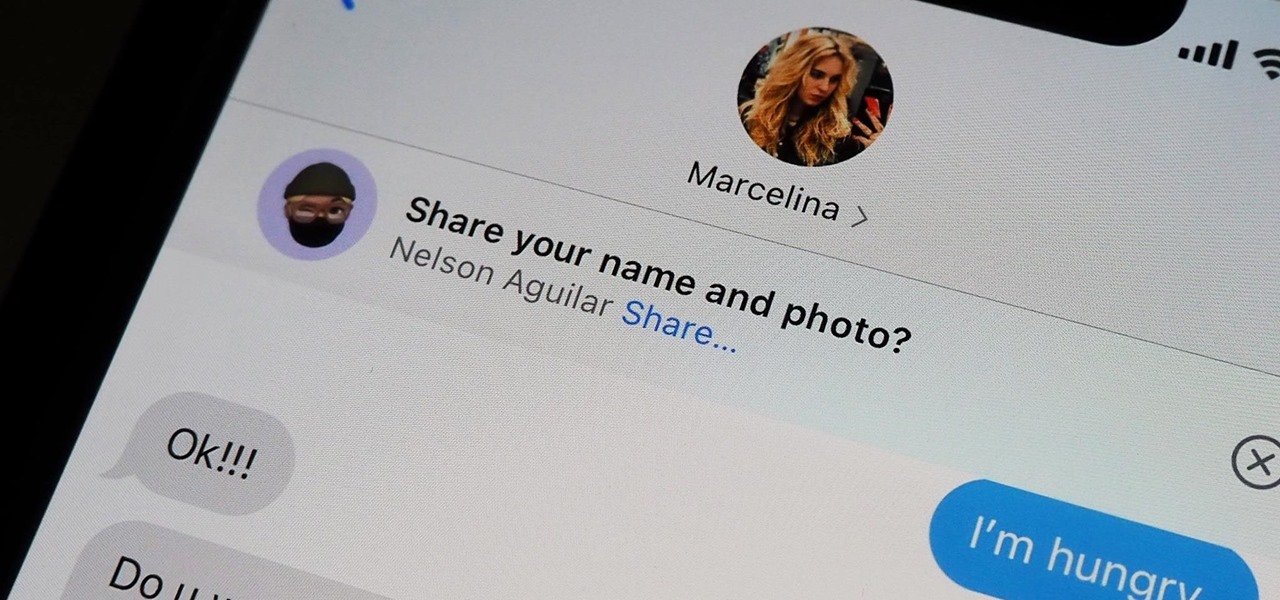
Your iPhone comes with a feature that allows you to share your name and photo with anyone you iMessage in Messages. It's a useful feature if you want people to see a customized name or fun image that you pick, but seeing all those "Share your name and photo" alerts in conversations can get real annoying quickly. There's a way to stop that from happening, thankfully.

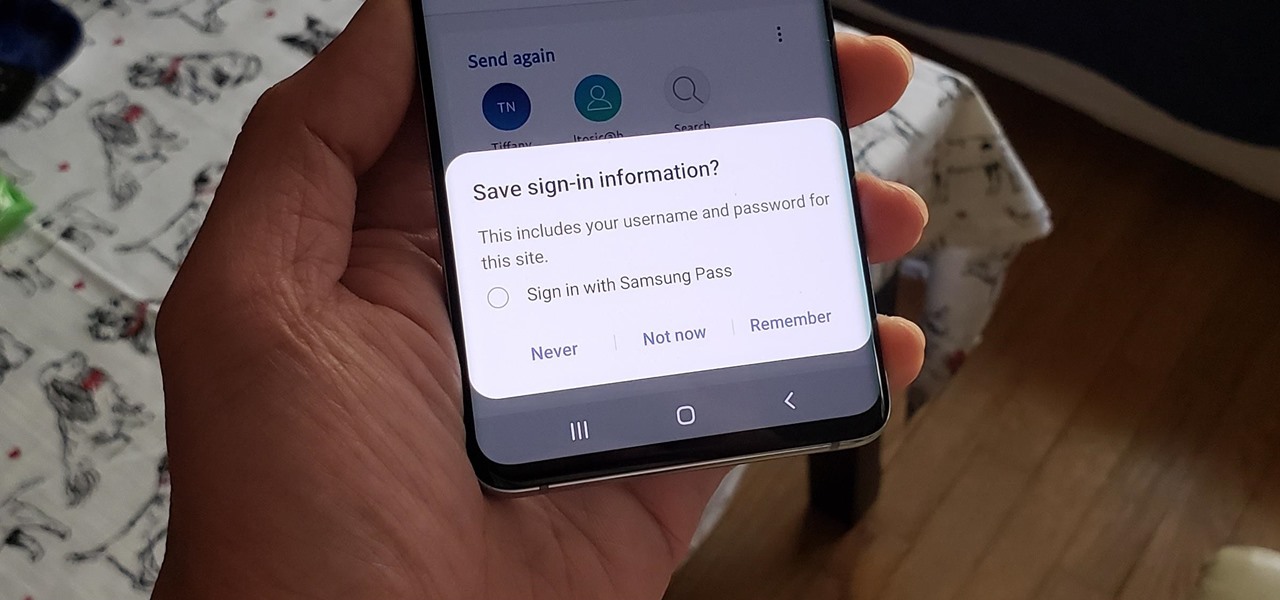
If you use Google Chrome on your computer, you've undoubtedly saved a ton of passwords since the browser always prompts you to. But Samsung uses their own password service on their phones by default, so you'll have to change a setting if you want to use your Chrome passwords to log into apps and sites on your Galaxy.

When you have a personal Instagram account but also manage other profiles — like ones for work, your entrepreneurial startup, an alter ego, or your famous pet, to name just a few examples — how do you manage them all from the same device?

When watching stories in your Instagram feed, there's a high probability that you'll come across an AR filter that you'll want to try out for yourself. A quick browse and search in the Effect Gallery will bring up nothing in most cases. But all of that unproductive work isn't necessary because there's a faster and simpler way to get the AR effect in Instagram Stories, and it works all of the time.

As we predicted this time last year, Magic Leap is finally moving from consumer entertainment hype to making a firm commitment to enterprise customers.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

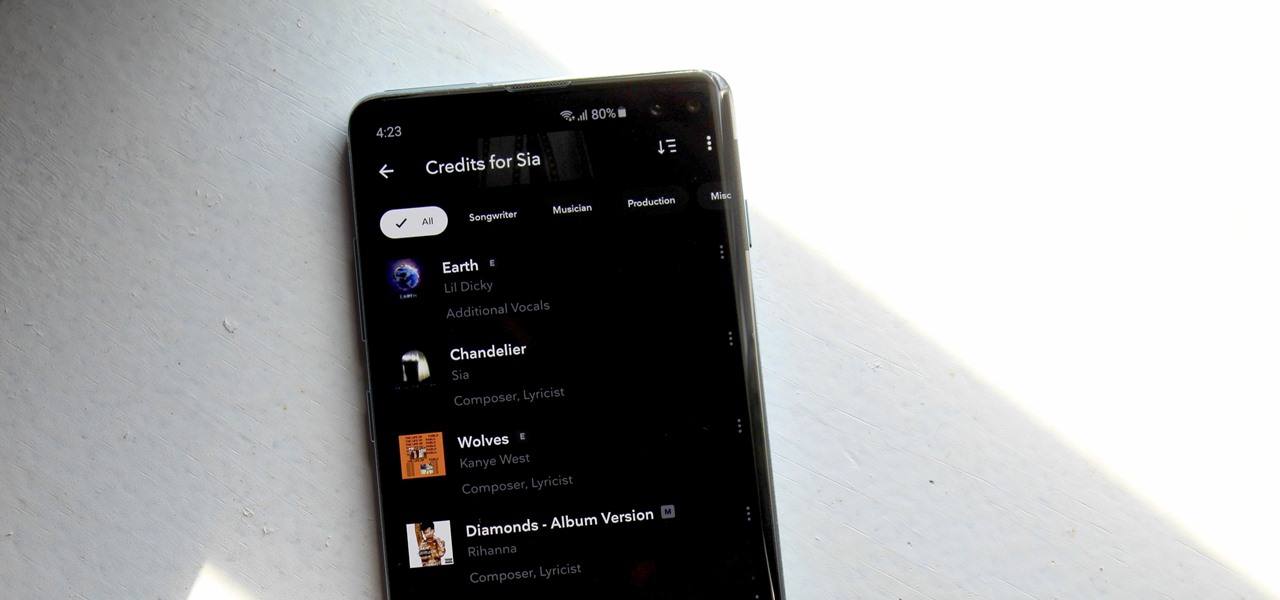
Contrary to popular belief, it takes more than just one artist to create the sound, lyrics, and vocals of a song. With most music being enjoyed digitally nowadays, it's harder to know all of a track's collaborators, as this info used to be in the CD booklet. Well with Tidal, you can now easily find this information and more.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

Front and center for iOS 12 this year is Group FaceTime, which allows users to chat with up to 31 additional people at once. While that ambitious feature is sadly delayed, don't cast away FaceTime just yet — you can always pick up your iPhone and start a call with any single contact directly from the Messages app.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.