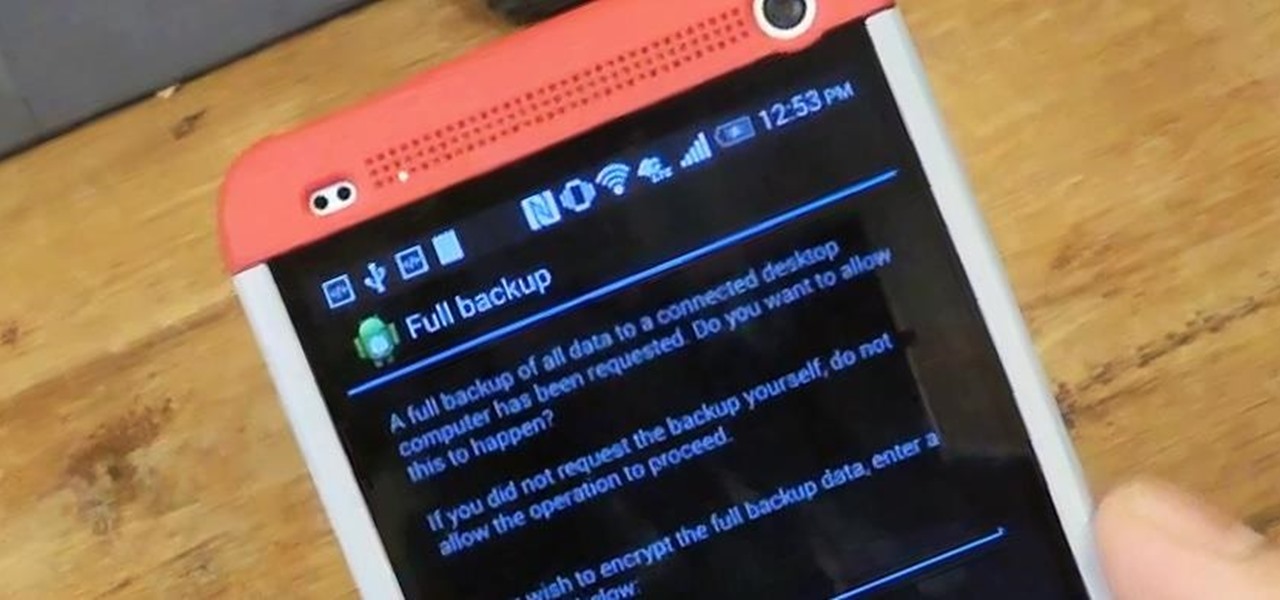
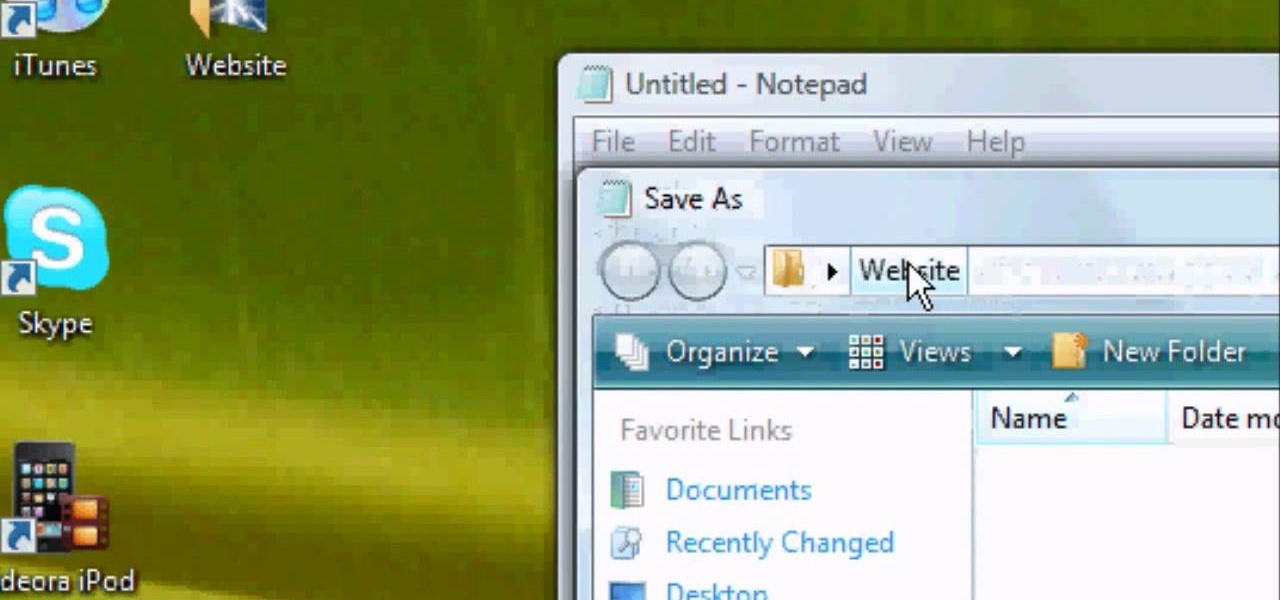
The misconception that macOS is more secure than the Windows operating system is far from the truth. With just one small command, a hacker can completely take over a MacBook and control it remotely.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

Samsung has kept us busy with their Android 8.0 Oreo beta testing program for the Galaxy S8, and most recently, the Galaxy Note 8. As the beta continues to receive new updates, stability has improved continuously, and new features keep on creeping in for both devices.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

Ever since the update that turned Google Keyboard into Gboard rolled out, a lot of people have been noticing that word suggestions and auto-correct features are downright slow. The issue seems to affect users with multiple languages installed more than anyone, though it can also happen if you have a midrange phone or older device with only one language installed.

Hello Friends … My name is Suresh Senarathna and this is my first “How-To” post,

John Oliver sunk his teeth into Republican presidential candidate Donald Trump during the long segment on the latest Last Week Tonight. The whole 21-minute video is definitely worth a watch, but the real fun starts around the 18-minute mark.

Android's Google Play Games app has let you track your feats and accomplishments in the games you play for quite a while now, but for some, the immersion experience might be broken after you finish dominating a game only to see your regular-ass name from your Google account on the leaderboard.

Welcome to the first coding tutorial on SQL here on Null Byte. Typo:

What's up, peeps? In this quick tutorial, we will be looking at structs, a special kind of data type.

Welcome to a tutorial explaining functions. This article will help clarify some things we have already been exposed to such as function prototypes, function calls, return values, etc.

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them

Welcome, in this tutorial we shall we looking at creating a safe(r) way to back up your important files. The contents we will be covering are as follows;

Welcome back, my novice hackers! Episode 6 of Mr. Robot has come and gone and, as usual, it did not disappoint. Once again, our hero, Elliot, has used his extraordinary intellect and hacking skills to awe and inspire us.

I spend a lot of time helping friends and family with their tech problems, like clearing a browser's cache, scanning a Windows computer for malware, and speeding up a Mac. However, the issue I deal with most frequently revolves around forgotten network passwords.

Doxing is the act of finding one's personal information through research and discovery, with little to no information to start with. You may have seen doxing in the news, for instance when not so long ago, hacker team Anonymous doxed and reported thousands of twitter accounts related to ISIS. Doxing can be useful for finding the address of a coworker, or simply investigating people on the internet. The tutorial I will provide to you now will teach you the basics of doxing and how you can prot...

When you press the "Call" button on most Bluetooth headsets, the majority of Android devices will launch a built-in Voice Dialer app. This app has been around since the dawn of Android, and has received very few interface or functionality updates.

Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often offer an entire point to the internal network and resources.

If you've haven't had your fill of Apple's security issues in recent weeks, Siri is now the latest to join the slew of problems with the most recent version of iOS (7.1.1).

Now that the Chromecast development kit has been out for over a month, more and more Android apps are being released or updated to work with the Chromecast.

Today, I'm going show you how to back up all of your apps and their data using Android Debug Bridge (ADB)—an essential function for all softModders. These commands will be especially useful when you are updating your version of Android, since they don't require a third-party program to run on your device.

Gmail is a free, advertising-supported email service provided by Google. Users may access Gmail as secure webmail, as well as via POP3 or IMAP4 protocols. Gmail initially started as an invitation-only beta release on April 1, 2004 and it became available to the general public on February 7, 2007, though still in beta status at that time. The service was upgraded from beta status on July 7, 2009, along with the rest of the Google Apps suite.

Every iPhone, iPad, and iPod Touch owner has that one folder which contains those never used apps. You know what I am talking about, the folder that contain Stocks, Voice Memos, Game Center, Compass, Newsstand (That's right, iOS 7 allows Newsstand to be placed in a folder!!). What do you call that folder? "Junk," "Hardly Used," "CrApple?" Why not call it nothing at all.

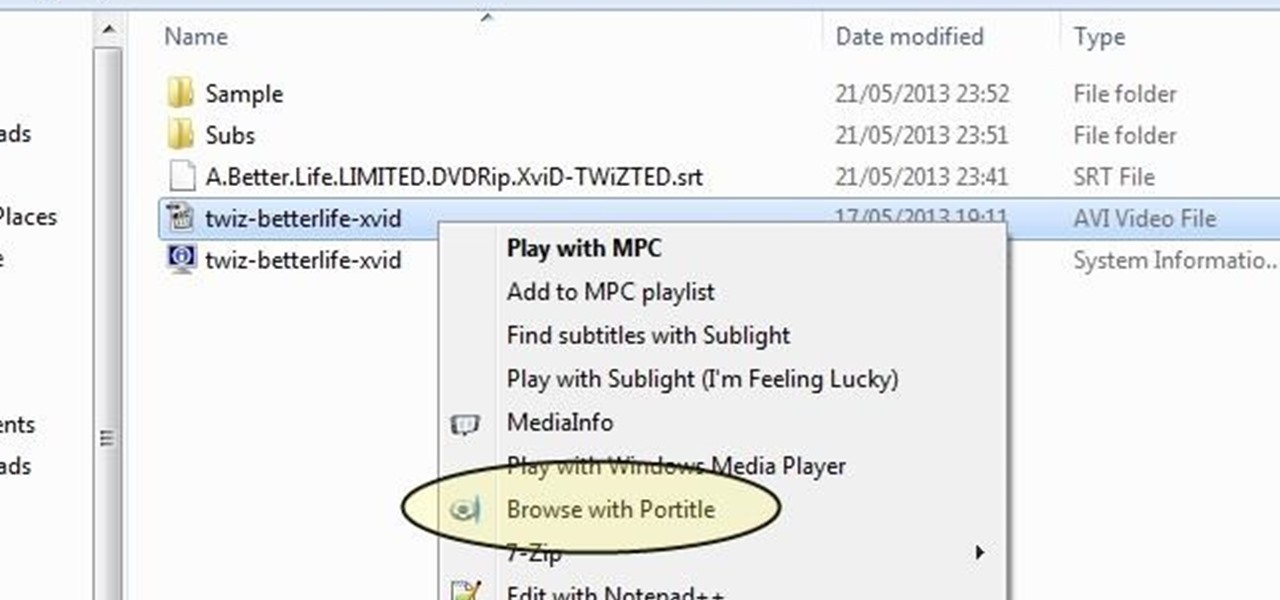
Understand the Problem of Couch Potatoes I have a lot of movies stored on my PC and when I have to finally have the time to watch something, I do not always remember which movie is which. So now I have to google for each movie with the keyboard or search in IMDB.

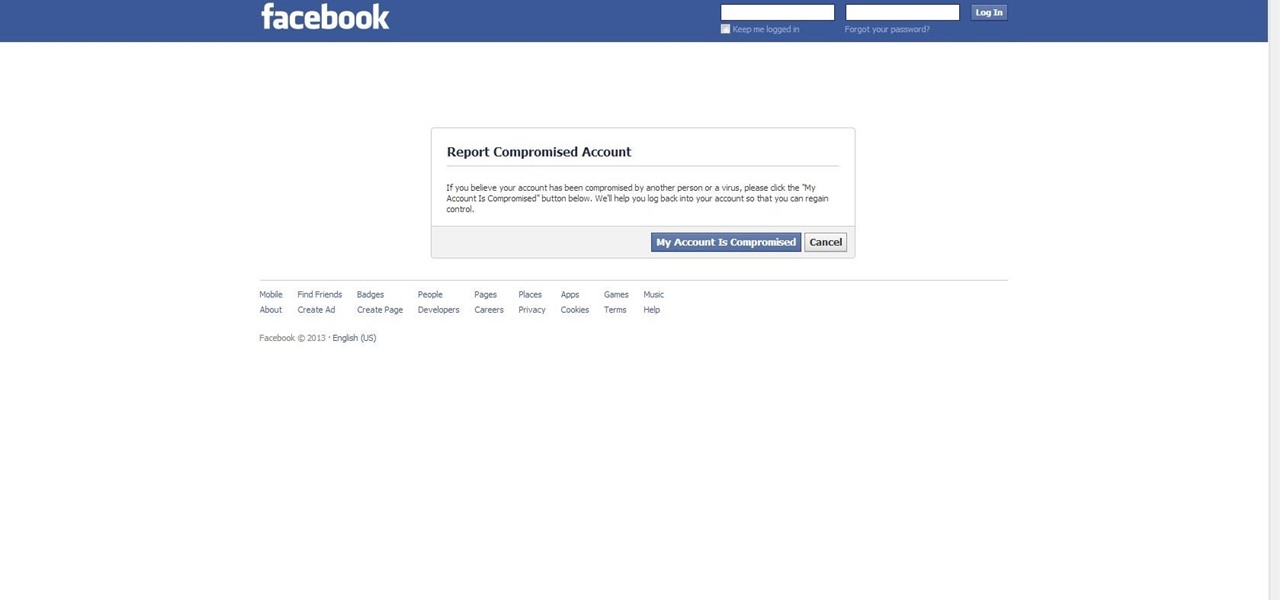
If your facebook account was hacked by someone and you really want it back this tutorial would help you get it back.

ATTN: HUMOUR ALERT Jules Verne was an author of immense imagination, who had a profound effect on speculative fiction, whereas Victoria was a stodgy & pampered royal who led a sheltered and traditional existence. Boring, frumpy, grumpy royal! (Photo from The Guardian, UK)

Have you ever wanted to be famous? Of course you have! Now you can make your Twitter profile look like it's verified, just like professional skater Lil' Wayne. With Twitter's new header, you can now upload a cover photo onto your profile to be seen online and on mobile devices. Just click here and change your header with the images below to get "verified" in seconds! Note that this will not work on the newer Twitter profile designs, since the verified symbol is located outside of all images.

First of all you have to open the 'notepad'. Now you have to type in "<html>" in first line. Write "<head> in second line. Write "<title>this website contains text wrapped around images</title>". In the fourth line you have to type '<body bgcolor="#999999">'. This shall add a light orange color. Now find out the name of the image. Here the name of the file is 'image.png'. Then in the next line you have to type in "<img src="image.png">this text should hopefully wrap around the outside of the ...

Check out this awesome tip from CNET on getting FREE eBooks of the web and onto your Amazon Kindle for easy and cheap reading. They show you the exact process for getting free ebooks for your Kindle, so watch and learn. It's worth it!

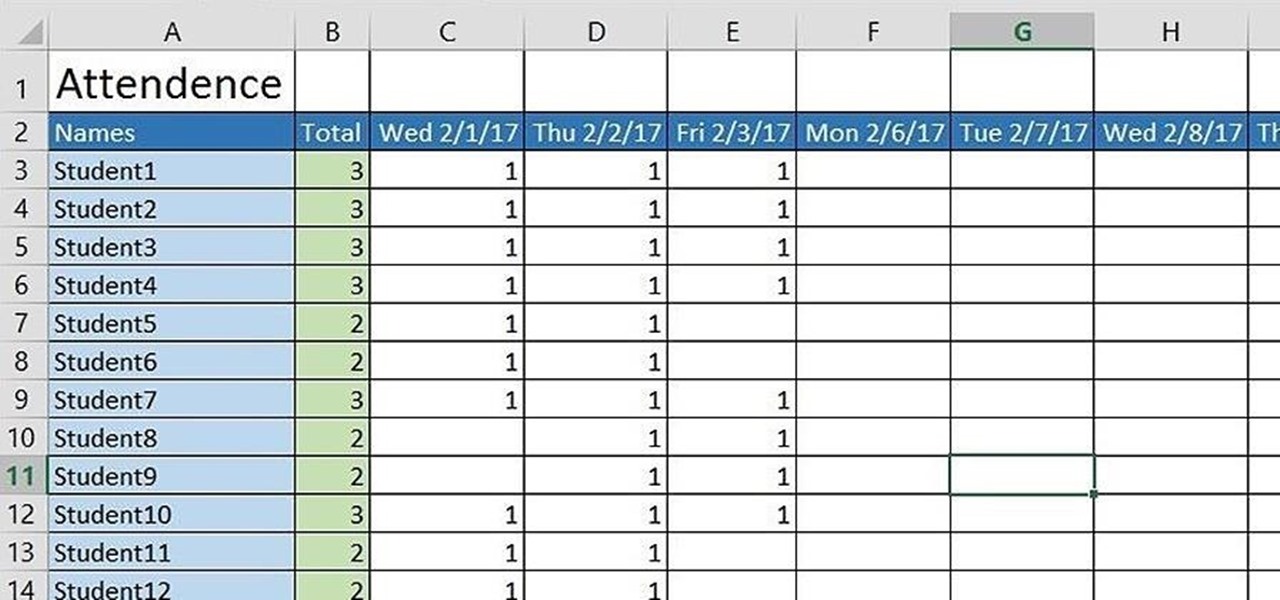
If you're a teacher in any type of school, whether it's high school, college, or middle school, it's imperative that you keep an attendance sheet. The paper and pen route can get pretty messy, and very disorganized, and that's where Microsoft Excel comes in. With this software, you can create a simple yet functional attendance sheet to keep track of your students.

This video includes instructions on how to get your PlayStation Portable (PSP) onto the BGSU wireless network.

This Dragon Age 2 sidequest, entitled 'First Sacrifice', is pretty aptly named. You'll be helping a man named Ghyslain search for his lost wife, whose fate has not been entirely pleasant. Check out these four videos for a full walkthrough.

This is a Computers & Programming video tutorial where you will learn how to change your NAT to OPEN with a Linksys router. Go to your browser and type in 192. 168. 1. 1 and that will take you to the basic set up. The authentication dialog box comes up. Type in ‘admin’ for the username as well as the password. These are default settings. In the Linksys page, go to ‘applications and gaming’ and on the Port Range page fed in these information. Your application you can name anything. Start 80, E...

This video has a man by the name of Dr. Neder and he has a book by the name, ‘how to be a man in a woman’s world.’ He answers a series of questions. The first question asked is how to get a girl with a boyfriend. The answer this video provides is simply that all girls are looking to date up. Meaning your value and assets, if there is a greater attraction then the girl will end up with you and dump the guy that she is with. Does size matter? The average size of most man is five inches to five ...

Learn How to draw Zero no Louise of Zero no Tsukaima Zero no Tsukaima, or The Familiar of Zero as it is popularly known in the west, is a fantasy comedy-romance anime that tells the story of a young female mage named Louise. For the full tutorial with step by step & speed control visit: how to draw.

Whether you like the name "worm" or "dolphin", the moves the same— a cool and trendy breakdance-style dance move where you lay on the ground and act like a slippery worm (or dolphin). This dance tutorial covers the "froward worm" move, with David Norseworthy from the Fresh Dance Workshop.

You may not know it, but one of the silliest dance moves you've probably seen out around town actually has a name. It's called the Roger Rabbit, and done with style and as part of a good dance routine it can be cool. Watch this video to learn how it works.

We all remember these neat little devices from elementary school. It has many names, the paper fortune teller, the scrunchie, chancer, chatterbox, but the most notorious is the cootie catcher. It's easy to fold, but funner to play with it. Watch and learn this origami masterpiece! Remember your youth!