Apple is often unpredictable when it comes to beta releases, especially with public betas. Developers receive their updates first, then public testers have to wait and see if Apple will do the same for us. Sometimes, the iPhone OEM makes us wait until the following day, but not with iOS 13.3 public beta 2. This update is now available to download and install.

It was a long time coming, but we finally have a meaningful conclusion to the legal case against augmented reality startup Meta Company.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.
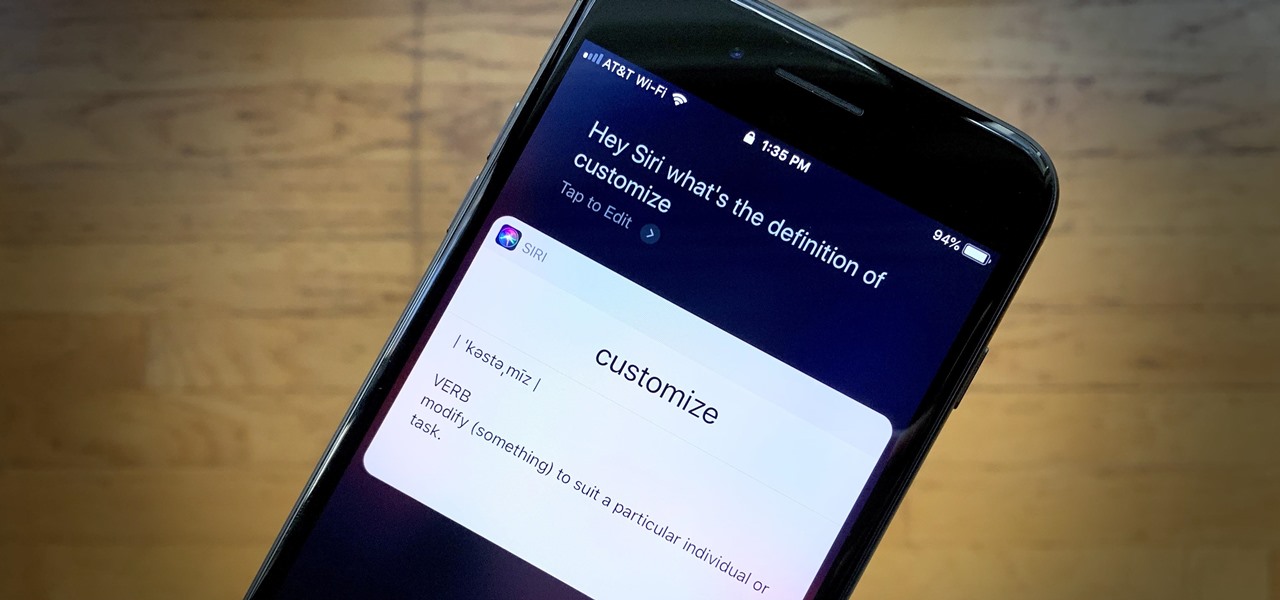
Out of the box, Apple's digital assistant could be a godsend or a nuisance, depending on your daily interactions it. No matter which camp you fall into, Siri can always be better suited to your personal needs with a little customization. You can make Siri a powerhouse not to be reckoned with, or you can minimize its presence if you only need Siri help sometimes — all without any jailbreaking.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

Instagram stories are a great way to share your day-to-day experiences with your followers. However, it can be disappointing to see them go after 24 hours, especially if you shared something really special. Now, Instagram has a way for you and your followers to relive those great stories you've created with a new feature called Story Highlights.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

As the world goes into a frenzy over the latest strain of WannaCry ransomware, it might be a good time to remember to update all your devices. Yes, those little reminders your phone and computer throw at you every now and then to update your junk can be really annoying, but not without merit.

Rumor has it that a gang of hackers—or possibly, one lonesome individual—holds the power to remotely wipe millions of iPhones and iCloud accounts, unless Apple coughs up some ransom money by April 7.

At this point in our series on creating a customized hacking container, you should be able to use Docker to save and retrieve customized instances of Ubuntu from your own machine. Make sure to revisit part one and part two if you need a refresher.

Welcome back everyone! It's been awhile hasn't it? Sorry for being so quiet, but my CCNA courses have really picked up recently. In the last article we covered how to import modules and how we can use them. In this article, we'll actually be covering a module that is essential to the hacking aspect of Python, sockets.

Welcome back, everyone! In this lesson, I'm going to go over the use of the echo function and variables, as well as basic syntax.

Hello again, reader! In this post, we are going to cover some data types and how to declare variables. It shouldn't be too hard so just sit back, relax, grab some popcorn and enjoy the ride (while you still can!).

Welcome back! In the last iteration of how to train your python, we covered error detection and handling. Today we'll be diverging from this and discussing functions. More specifically, we'll be creating our own functions. First we'll need to understand exactly what a function is, then we'll get on to making our own! So, let's get started!

Welcome back, my tenderfoot hackers! WordPress-based websites are among the most numerous on this planet (maybe other planets too, but I can't vouch for that). According to WordPress's own website, WordPress powers 23% of the top 10 million websites. That's approximately 2.3 million sites using WordPress!

Cooking Steak directly on the coals with no grill. Given many different names including caveman steaks or dirty steaks, this method involves placing the steak directly on red-hot lump charcoal to obtain a fantastic texture & taste that's as good as most restaurants.

At last, what you all finally waited for! Hi! Fire Crackers,

On the internet, everything is possible, even if it's not grounded in reality (check no further than anything The Onion publishes). Witty headlines combined with clever photo edits make even the most absurd topic seem like a serious news story. Some of these stories are so convincing that they even fool news organizations, such as the New York Times and even the official newspaper of the Chinese Communist Party. While some of us can tell when something sounds a bit off, others (like our paren...

YouTube's main player interface got a pretty big makeover recently, but chances are, the new UI hasn't made it your way just yet. Google has a habit of slowly testing the waters as they roll out new features, so cool tweaks like this can take some time to reach all users.

For some odd reason, the Netflix app likes to disable the Nexus Player's built-in screensaver. It doesn't use its own, it simply keeps your screen on indefinitely, which of course can lead to screen burn-in. This is not just an Android TV issue, as the Netflix app does the same thing on Roku and smart TVs.

This video has 7 fraction hacks that can save you time when working with fractions. The hacks are: Adding fractions without a LCM

Hello, my name is PortalsUnite I made a mod review about a awesome minecraft mod called The Incredibles mod. I would appreciate it if you checked it out, liked, shared and subscribed. Feedback is always welcome!

Back in the day when computers relied on CRT monitors, having a static image displayed for too long actually resulted in the image being burned into the screen. For this reason, screensavers were developed, which display animated images in constant motion to prevent burning in when you stepped away from your computer.

Welcome back, my tenderfoot hackers! In continuing my series on digital forensics using Kali, I want to introduce you to two complementary tools, both built right into Kali Linux. These are Brian Carrier's tools Autopsy and Sleuth Kit.

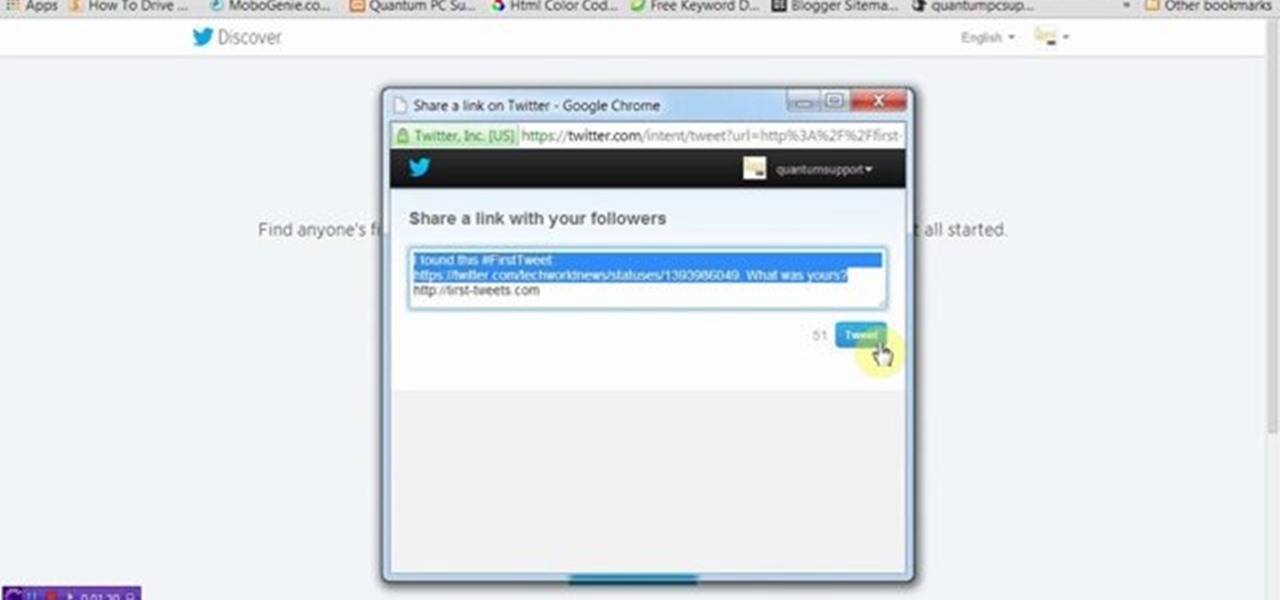
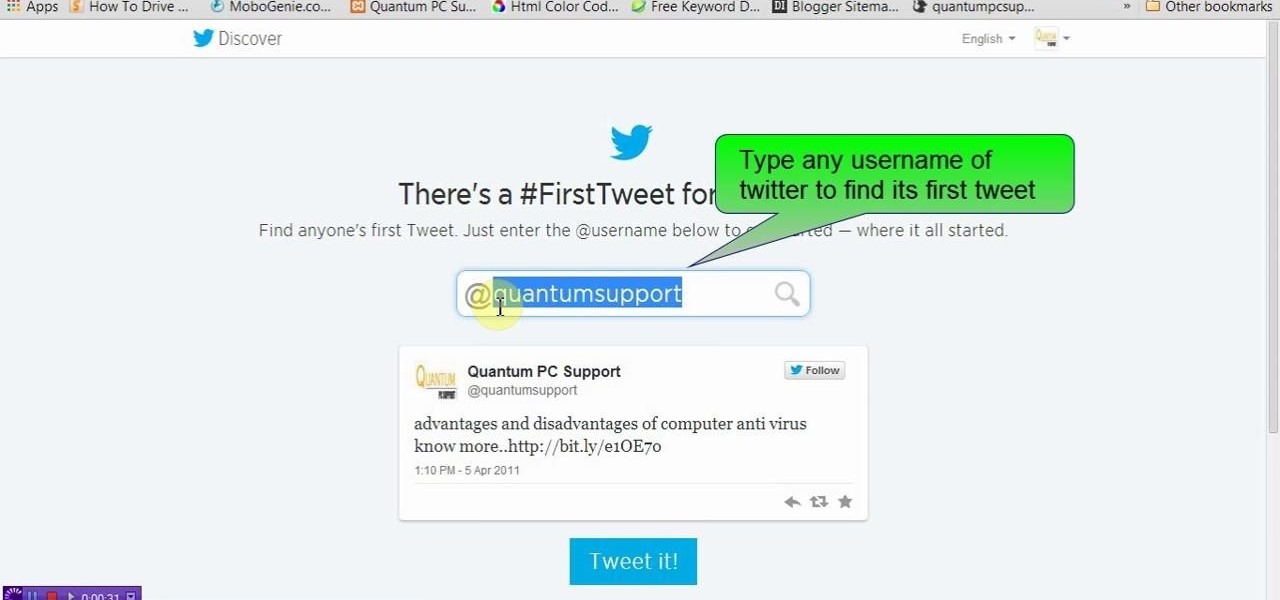
This tutorial video will show you how to find first tweet of any user in Twitter. You have to type first-tweets.com in address bar of your browser. The site will be redirected to discover.twitter.com/first-tweet page. Just type any user name and twitter will show the first twit of that user. Watch the video and try it yourself.

This video will show you how to see first twit of any user in twitter. You could type https://www.first-tweets.com in address bar and the site will be redirected to another place https://www.discover.twitter.com/first -tweet page. You have to enter the user name and twitter will fetch the first twit of that user. Watch the video and employ it yourself.

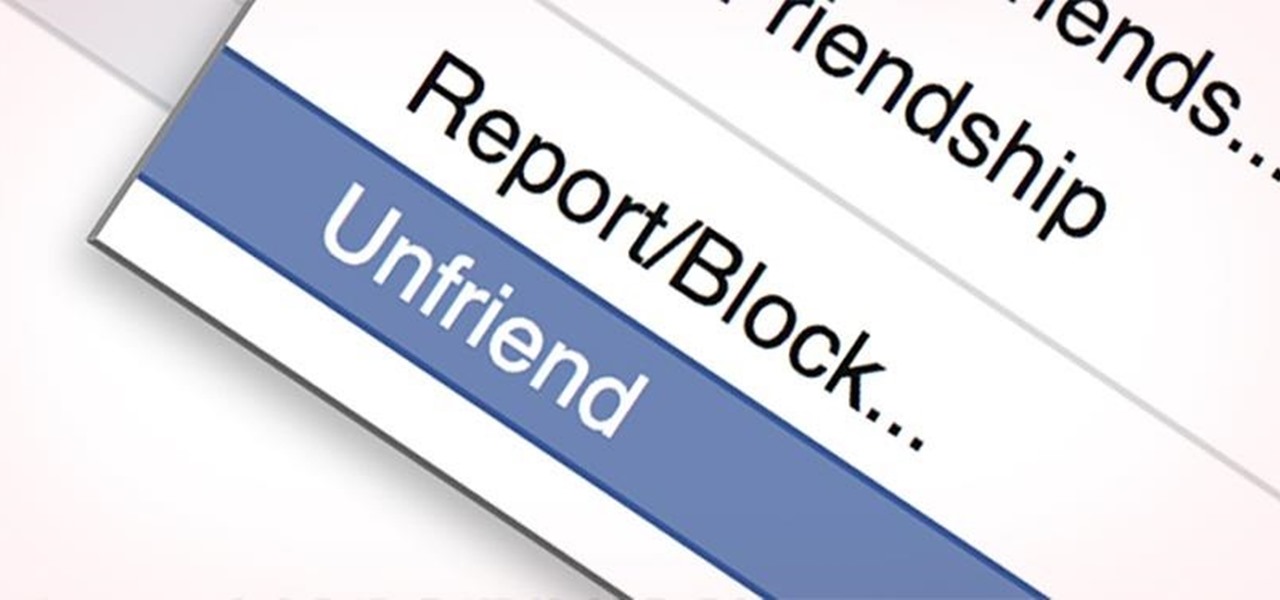
Admit it: you haven't talked to more than 70 percent of your Facebook friends in the last year. Whether you barely know the names crowding your friends list, or have vague memories of high school Spanish class with them, Facebook friends are easy to find and difficult to get rid of.

Welcome back, my hacker noviates! In a recent post, I introduced you to Shodan, the world's most dangerous search engine. Shodan crawls the globe from IP to IP address, attempting to pull the banners of each web-enabled device and server it finds.

In this video I'm turning the pages of a magazine about Macrame. Relax, unwind, and enjoy this old journal about Macrame. I hope some ideas from the Magazine come in handy. (Name of this journal: "Masche Die Makramee" 1984)

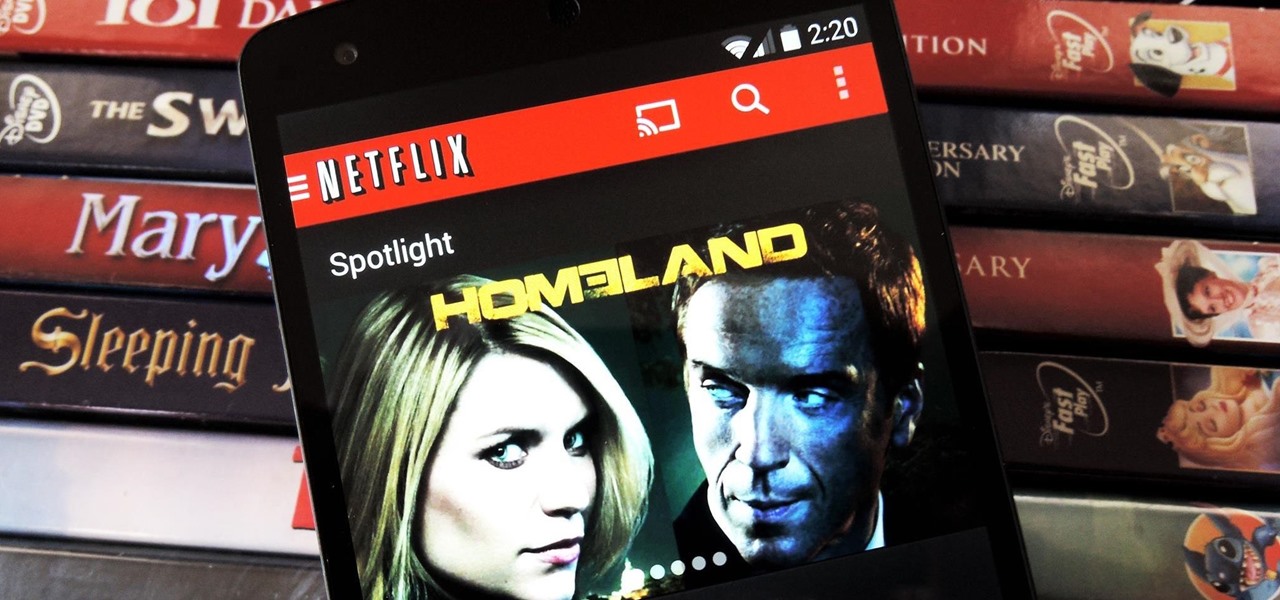
Out amongst the ether of the internet lies a completely different version of the Netflix library you've come to know and love. Because of licensing and rights fees, the streaming media giant maintains separate libraries for each country it services. Ultimately, this means that certain movies and TV shows are only available in certain countries.

Hi again everyone, this lesson will be about the names of body parts in Lebanese Arabic. I hope you will enjoy it and find it interesting. Have fun and don't forget to share it if you like it :)

The Alternating Half Hitch is tied to form a chain, also called a sennit. Other name of this knot is the Chain Stitch or Zig-Zag braid. This knot can be used to make a simple bracelet or necklace and other items can also be made with this knot.

in this Zipper bracelet is used Half Hitch knot or oldest name - Basket Stitch. They can be used as part of plant hangers, or to make belts, bracelets, and other items. This is very easy to make (: can be used as a friendship bracelet and good for beginners :)

How to Henna Your Hair Tutorial Pt.2 Please Dont forget to Watch Pt. 1

Video: . How to Henna Your Hair Tutorial #1

Matthew Whelan changed his name to "His Royal Majesty Body Art, King of Ink Land" and he is a strong supporter of body branding and face branding. He even got his eyeball tattooed!