
How To: Make yellowtail teriyaki and pickled turnip
Ingredients for Yellowtail Teriyaki & Pickled This tutorial video will teach you how to make your very own teriyaki yellowtail.


Ingredients for Yellowtail Teriyaki & Pickled This tutorial video will teach you how to make your very own teriyaki yellowtail.

Okay, you failed anatomy 101, but you still want to know more about anatomy of a human. Well, you can simply watch this video tutorial that will show you how to cut up a human cadaver, dissecting its leg and foot, getting a good look at the science of the muscles.

Since its founding in 1984, Cisco Systems has been a global leader in information technology. From networking hardware and software to domain security and energy management, the company dominates the IT field.
Everything you post on social media lives there forever — even if you delete it. Just ask anyone that's ever posted something stupid. Instagram does not provide built-in tools to save or download images and videos from other users, but there are workarounds. Third-party tools make saving other people's photos and videos easy, and there are always screenshots.

Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a tool called Arjun can be used to discover hidden HTTP parameters in web apps.
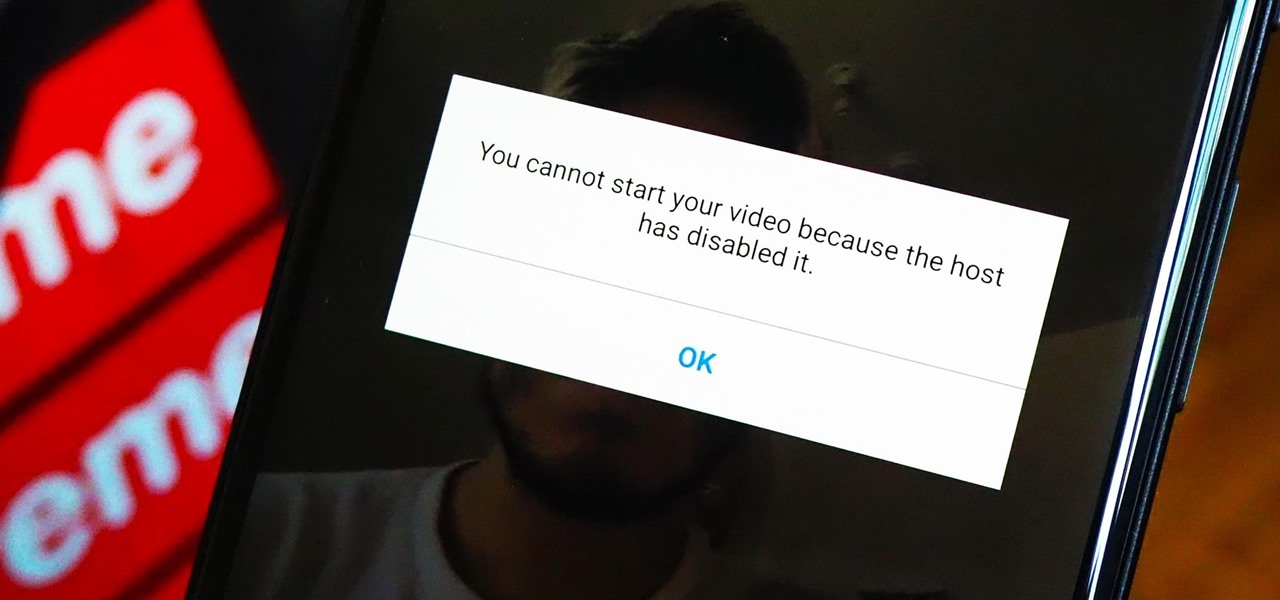
As a meeting host on Zoom, you can't control what a participant does during your live video call, but you do have the power to turn off their camera so that other people aren't subjected to distractions. So if you catch someone in your call purposely making obscene gestures or accidentally exposing themselves while using the bathroom, you can block their camera, as long as you know how.

At least one hurdle to China-based augmented reality startup Nreal going mainstream in the United States may be about to be knocked down, thanks to behind the scenes legal movements Next Reality has uncovered.

In iOS 13, Apple finally took the built in Files app from an extremely rudimentary file browser to a full featured app that can serve the needs of most any user. Among the new features is the ability to compress a file or series of files into a standard ZIP archive right from your iPhone.
Your Pixel has a few hidden features you probably don't know about, like the ability to clean up your funky contacts list. Since I'm sure you haven't manually organized your contacts since the inception of Android, there are likely some incomplete and duplicate contacts. Thankfully, your phone can fix this automatically.
You may have noticed your Note 10 came with quite a bit of bloatware. Even the unlocked version of the phone comes with Facebook preinstalled, and if you bought it from a carrier, it's much worse. Luckily, there's a way to remove any apps you don't want, and you don't need root or a paid app to do it.

The biggest feature in the iOS 13 update is a new system-wide Dark Mode. It's a simple switch that you enable to turn system menus and Apple apps dark, but it can also darken third-party apps if their developers elect to support it. Trouble is, most haven't yet, so half of your apps likely still have a blinding white background.

If you've ever used the Find My iPhone and Find My Friends apps in iOS 12 and below, you may be surprised to hear that those apps have joined forces in iOS 13. Now, instead of two separate apps, they're combined into one convenient package. But what does that mean for you and your privacy and security?
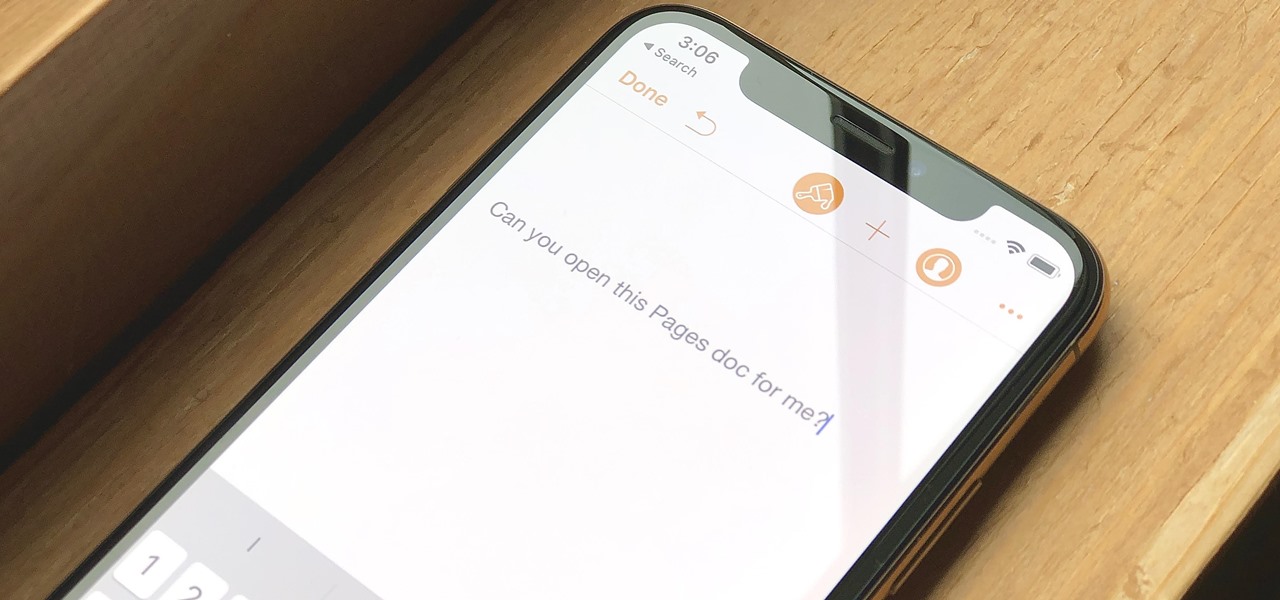
Let's say you have an important report to submit, but you want to check it over for any last-minute edits or changes. Times running out, and you simply can't find this Pages document anywhere. Wouldn't it be great if you could just ask your iPhone to open the report for you, so you could stop wasting time searching and finish the paper? Well, thankfully, Siri can help you out with that.
Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tracking link, Grabify can even identify information leaked from behind a VPN.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.
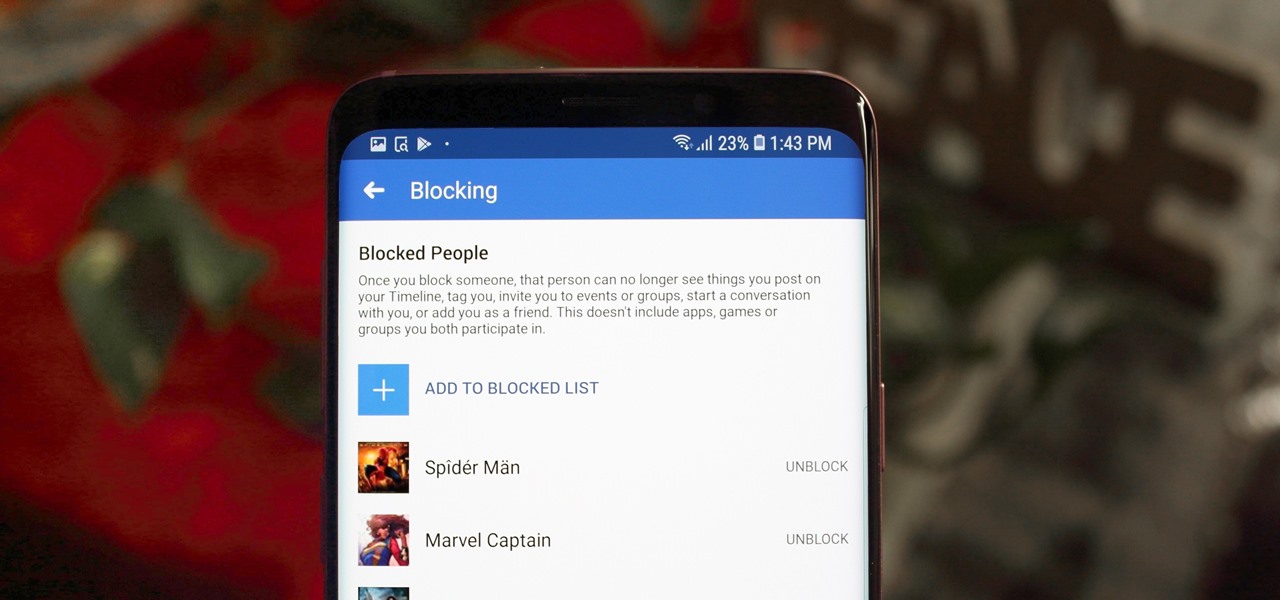
Whether it's an ex you can't stand, that annoyingly political friend of a friend, or good old fashioned trolls, the block feature on Facebook can be a great way to de-stress your feed. It will keep people from contacting you, and it will also prevent them from viewing your profile altogether. It's not just a tool for the full desktop website — in fact, the blocked list is easy to manage right from your phone.

On Thursday, Mojo Vision, a startup comprised of former engineers from Apple, Amazon, Google, and other Silicon Valley mainstays, emerged from stealth backed by $50 million in funding for a hands-free augmented reality platform that runs without smartphones, tablets, or other devices.

Augmented reality app developer Laan Labs has shared a preview of a beta app that achieves 3D scanning with just an iPhone and produces highly-detailed models for sharing with others.
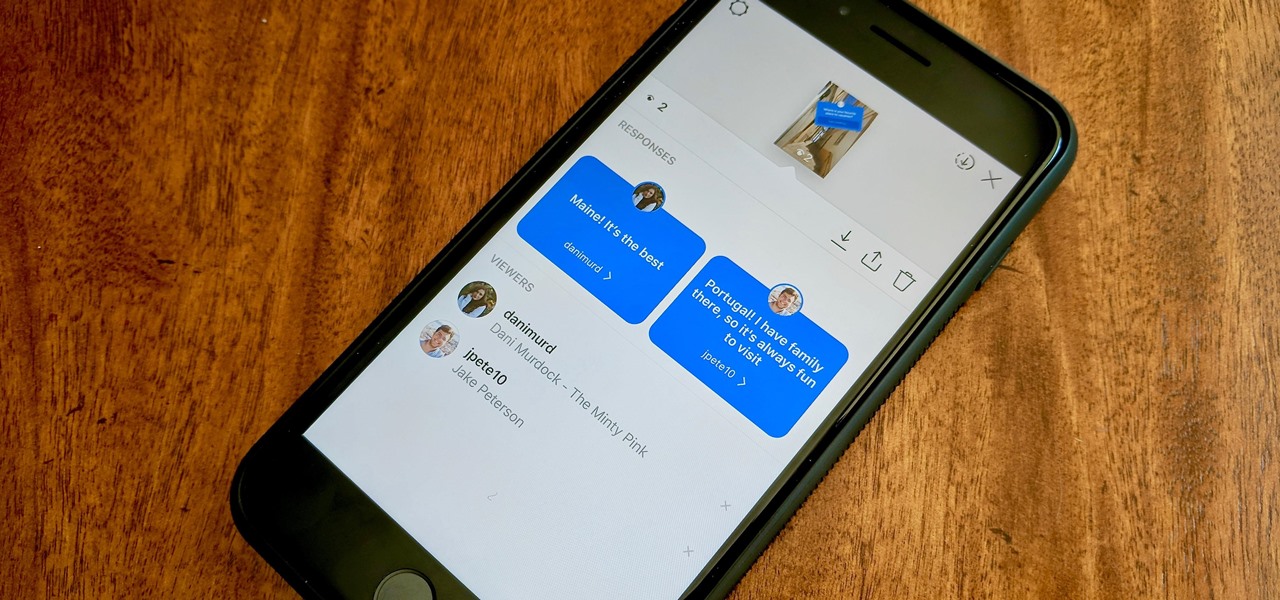
Users on Instagram have taken the app's new "Questions" sticker and run with it — it's tough to find a story in your feed that doesn't proudly sport "Ask me a question." However, it appears there's some confusion when it comes to the anonymity of your answers to these questions. News flash — your username is attached to every response.

Data breaches are all too common now, and the latest one you need to know about involves Timehop, a mobile app that makes it easy to reminisce over old photos. The breach, which took place on July 4, was revealed on Sunday, July 8. At the time, Timehop disclosed that 21 million users had been affected by the breach, but it now appears that all users were impacted in some way.

With the macOS stager created and the attacker's system hosting the Empire listener, the malicious AppleScript can be designed and disguised to appear as a legitimate PDF using a few Unicode and icon manipulation tricks.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

When you don't want somebody you're calling to know the real phone number associated with your iPhone, whether it's for privacy reasons, to avoid being called back, or to prevent being ignored, there are multiple things you can do to block it on their caller ID.

Whether you've stumbled upon an interesting location you want to bookmark for later, need to remember where you park your bicycle or vehicle, or want to keep track of your favorite food truck locations, Apple Maps makes it easy.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.
Have you ever been listening to the radio and a song comes on that you can't identify? But you're driving, so you can't open your phone and use your favorite app to find the song's name. Well, with a feature called "Now Playing" on Pixel phones, Google has solved this problem.
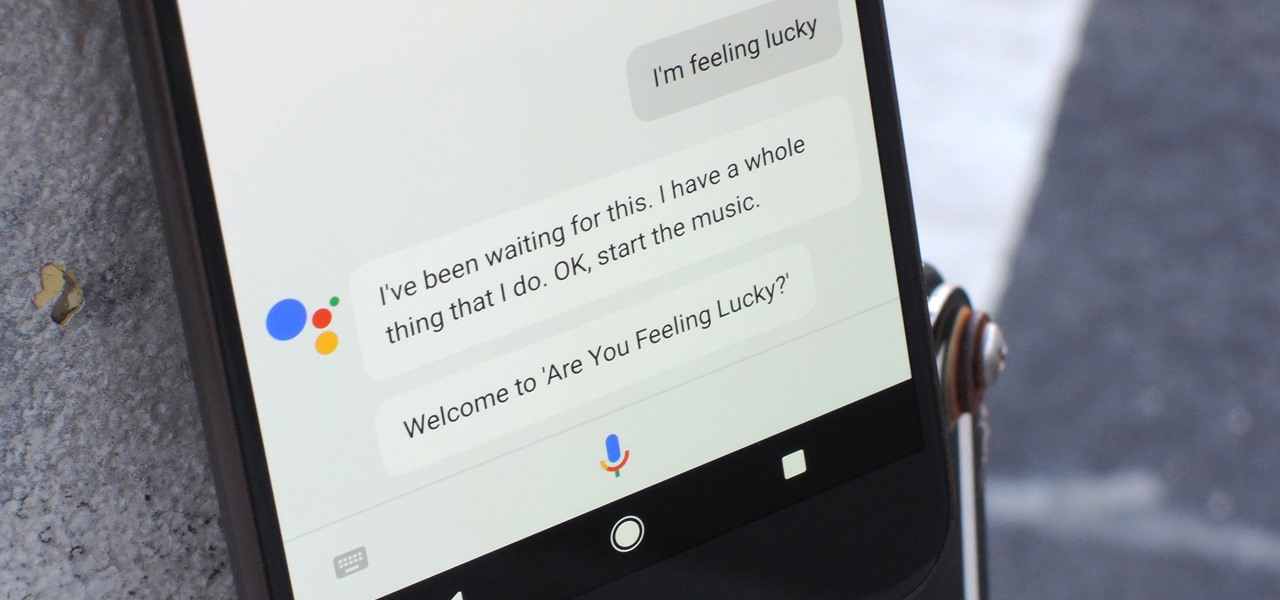
Despite a rocky start with plenty of feature disparity, the Google Assistant now provides a pretty consistent experience regardless of what device you're using it on. Be it Android, iPhone, or Google Home, the AI behind the Assistant is virtually identical — including its quirky commands and funny responses.

One of the most popular things to do on Snapchat is to earn a Snapstreak. This occurs when you and one other friend have sent snaps (not chatted) to each other within 24 hours for at least three consecutive days. One you've passed the three-day mark, then you and your friend will receive a fire emoji next to your names.
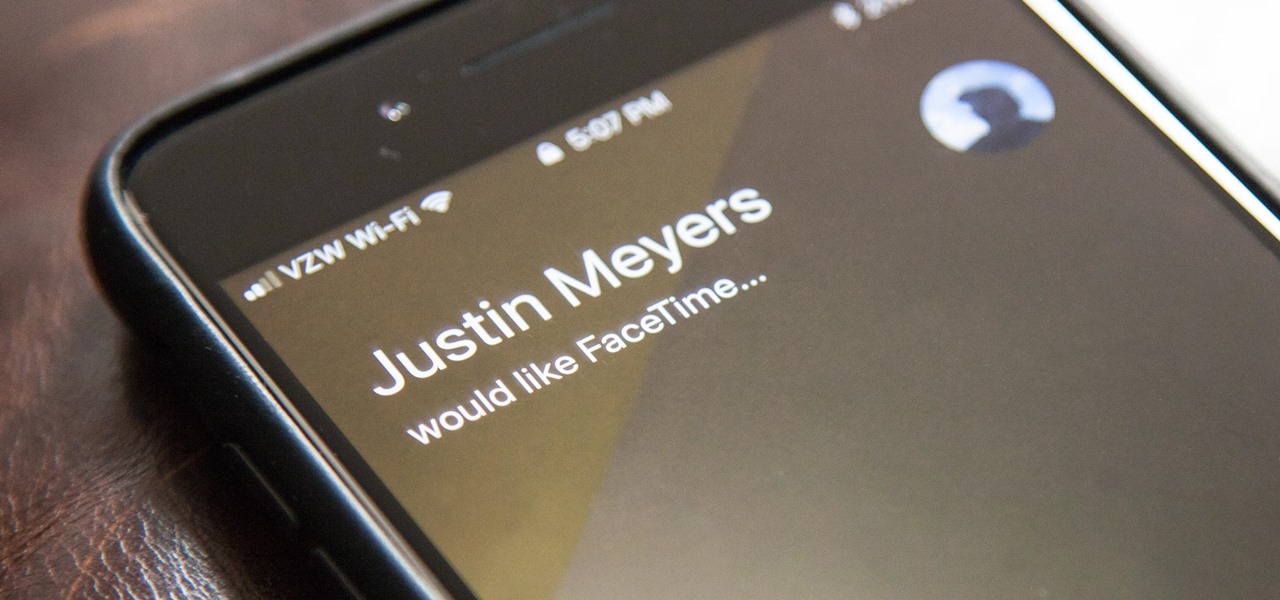
Whenever you make FaceTime audio or video calls from your iPhone, Apple automatically uses your phone number or Apple ID email address as the caller identification. So when someone that you're calling sees the incoming call, they'll see it's from your phone number or email address. But what if you'd rather it be a different identifier?
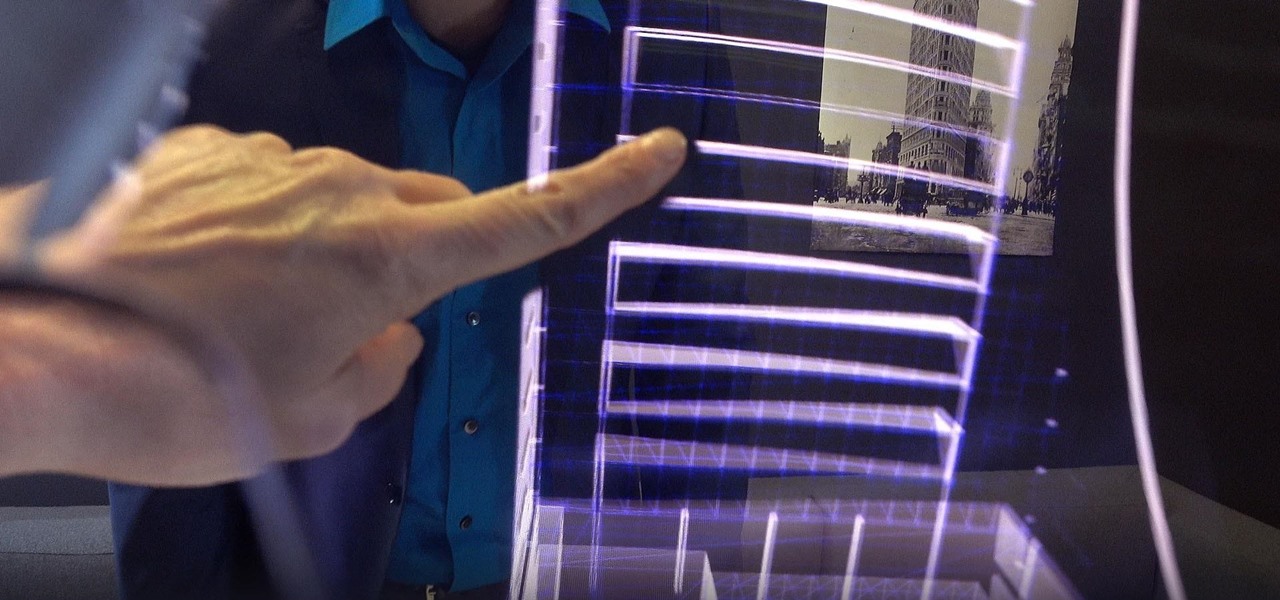
While two augmented reality companies were recently recognized for their innovative technologies, other companies have turned to augmented reality to innovate in their respective fields. Over the past week, use cases have ranged from selling snacks and video games to raising awareness for public health issues.

Thanks to a $100 million deal, you could be seeing more original shows on your Snapchat soon. Already, Snap has been producing super short shows in order to compete with social media outlets like Twitter and Facebook who have also been attempting to create their own content. While musical.ly has so far had the biggest success in this area, this deal with Time Warner is certainly promising for the beleaguered platform.

Open your Spotify app, search for an artist, view its "Spotify Code," and display it to that friend lurking over your shoulder. Sound familiar? Probably not ... yet.

Any parent with a rambunctious child who may have at one point racked up a hefty bill on their Kindle or Android device can now breathe a sigh of relief. One, Jack Black has had it happen to him too, and two, Amazon will be refunding up to $70 million of in-app purchases made by children after downloading apps from the Amazon AppStore.
Google has already issued a few updates to Android 7.0 Nougat. There aren't many headlining features, as these minor updates are mostly bug fixes and performance improvements. But there's a few security enhancements as well, so staying up-to-date with the latest patches is important for a number of reasons.
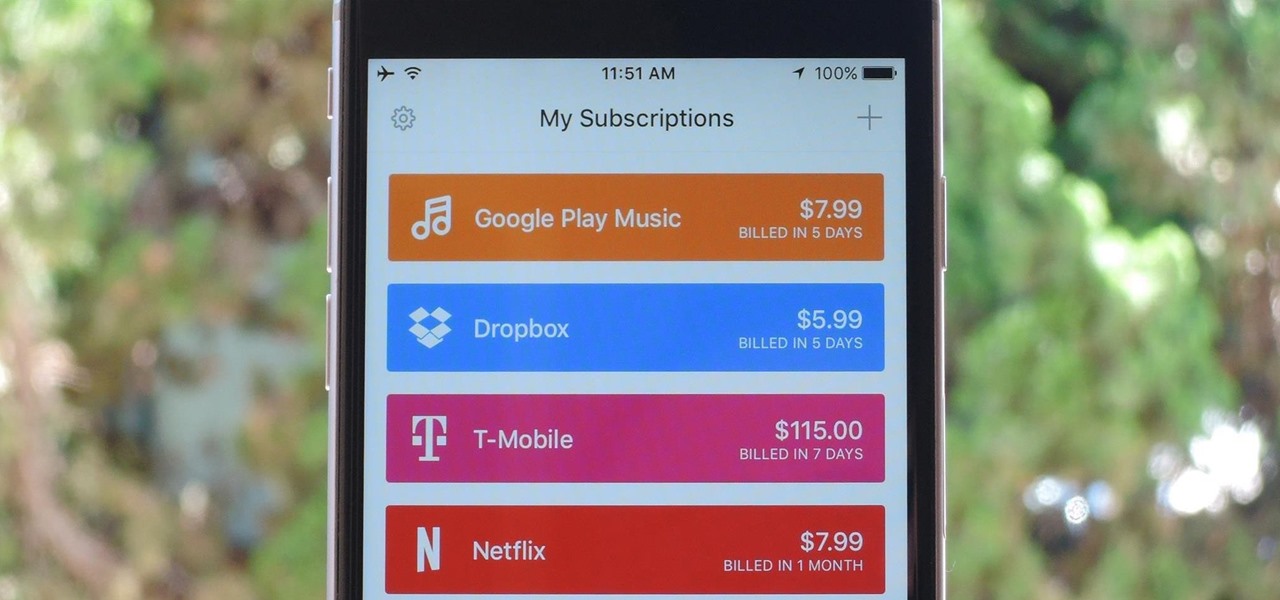
As the internet continues to become a bigger part of our day-to-day lives, we slowly but surely start to rack up a bunch of web-based subscriptions. These internet subscription services—Netflix, Hulu, and Amazon Prime, just to name a few—may seem innocuously cheap individually, but when combined, they actually comprise a significant portion of our monthly bills.

Welcome back, my hacker novitiates! If you have been following this new Snort series, you know that Snort is the world's most widely used intrusion detection/protection system. Now a part of the world's largest network equipment company, Cisco, it is likely to be found everywhere in one form or another. This makes a compelling argument for learning how to use it, as it will likely be a necessity in any security-related position.
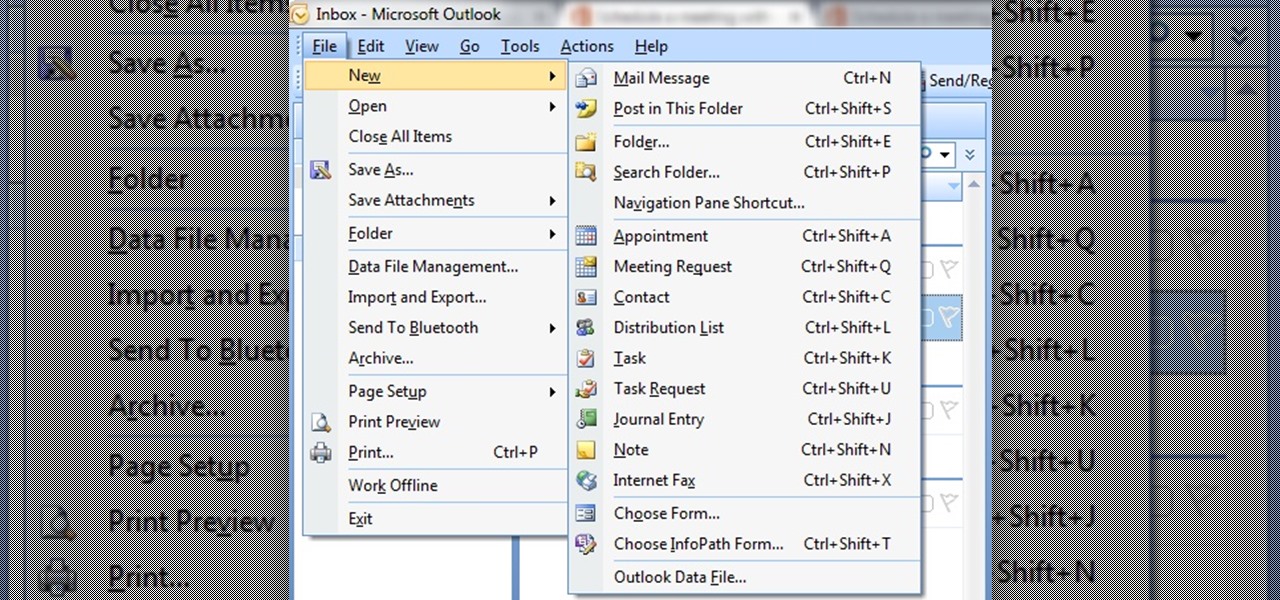
In this tutorial First, we will discuss what a meeting is, How can we schedule it in Outlook. A meeting can be defined as a mass of two or more people have a common motive. All the people present in a meeting can share their ideas and exchange information, to carry out the actions to achieve their goal. This tutorial helps those people who are looking for the steps to Schedule a Meeting in MS Outlook.

Welcome back to another episode of Java Tutorials, In today's tutorial, we'll be learning about what methods are, proper syntax when writing Methods, and why they are beneficial in a program's code.

Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, this is an excellent way to learn how to hack Wordpress, Joomla, and Dupral plus many more!

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/