
How To: Fix a scratched CD or DVD with Urawaza secrets
This how to video shows us how to fix a scratched cd or dvd using toothpaste. Don't throw out that scratched cd or dvd, just fix it with this DIY home project.


This how to video shows us how to fix a scratched cd or dvd using toothpaste. Don't throw out that scratched cd or dvd, just fix it with this DIY home project.
Whether you're a social type with a loooonnng list of friends or a PR gal with a bunch of people you've got to contact all at once to notify them of an event, it can often get time-consuming to type out the name of every single person you have to send the same email to.

See how to do Salah Prayer for Muslims by Sheikh Adly, with instructions in English. Sunni way!

Learn the names of animals in French. Part 1 of 6 - How to Talk about animals in French.
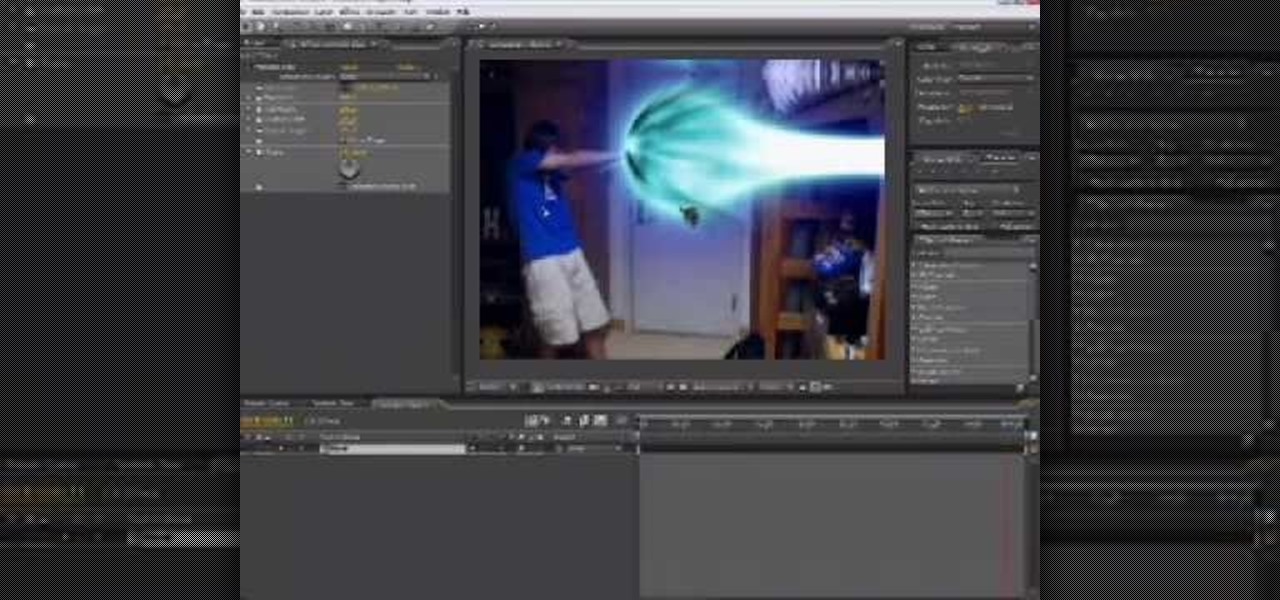
No, the Kamehameha is not the famous Hawaiian king who united all the islands under his rule from 1795 to 1819. Nope. However, it is named after him. But in this case, Kamehameha is an energy blast attack shown in the Dragon Ball Z series. And with this After Effects tutorial, you're going to learn how to recreate this energy attack.

In this video you will see how to use FTP client to move files to GoDaddy.

A parachute-style dry fly has several advantages over a standard hackled dry fly. The parachute name comes from the fly's propensity for soft, upright landings that don't spook trout. The body of the fly rides lower the surface film like a real mayfly and some people find the parachute wing is easier to see. Another important quality is that because the hackle rests horizontally on the water, parachute flies float well and also imitate mayfly spinners laying flush in the water, as well as dun...

Tech tends to move forward without looking back, but that doesn't mean new is always better. One feature that dominated mobile phones in the late '90s had made a comeback thanks to Apple, and you can take advantage of it on your iPhone when making calls.

Apple offers many ways to customize the Home Screen on your iPhone, from adding widgets and scheduling rotating wallpapers to hiding apps and entire pages. But some of the best ways to customize your Home Screen are options Apple won't even tell you about, either because they haven't become official features yet or because Apple is OK with the workarounds.
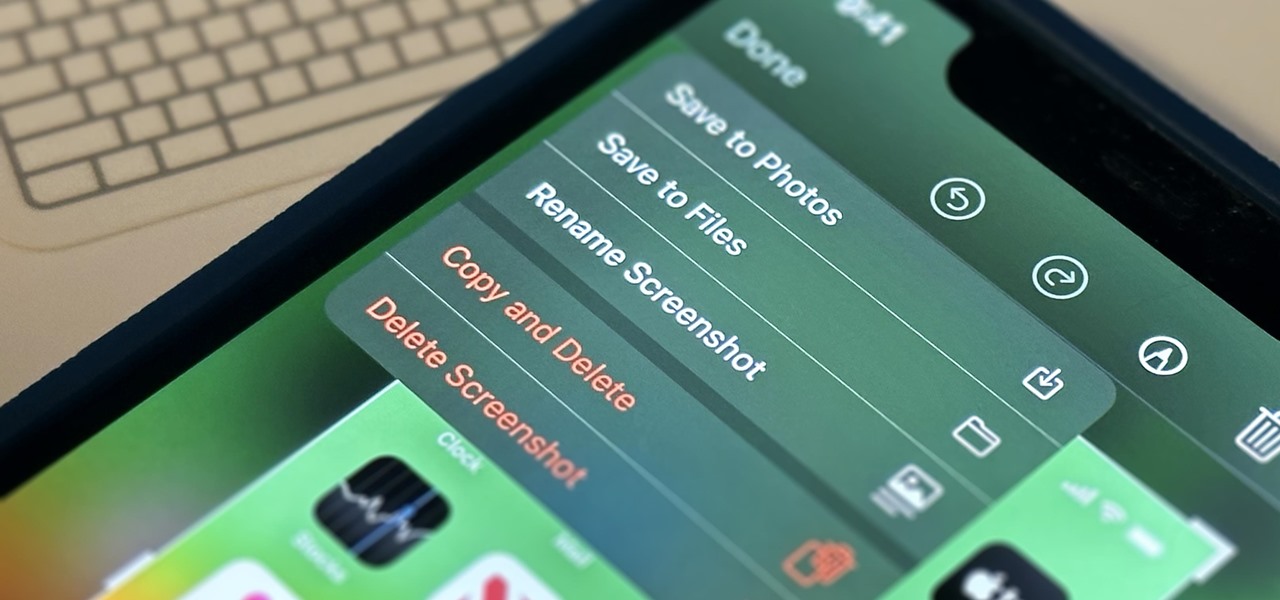
Apple's screenshot feature is a near-perfect tool for saving images of your iPhone's screen to keep for yourself or share with others. But iOS is missing one thing that would make it almost flawless: a way to rename your screenshots from their original IMG_1234.PNG file name.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.
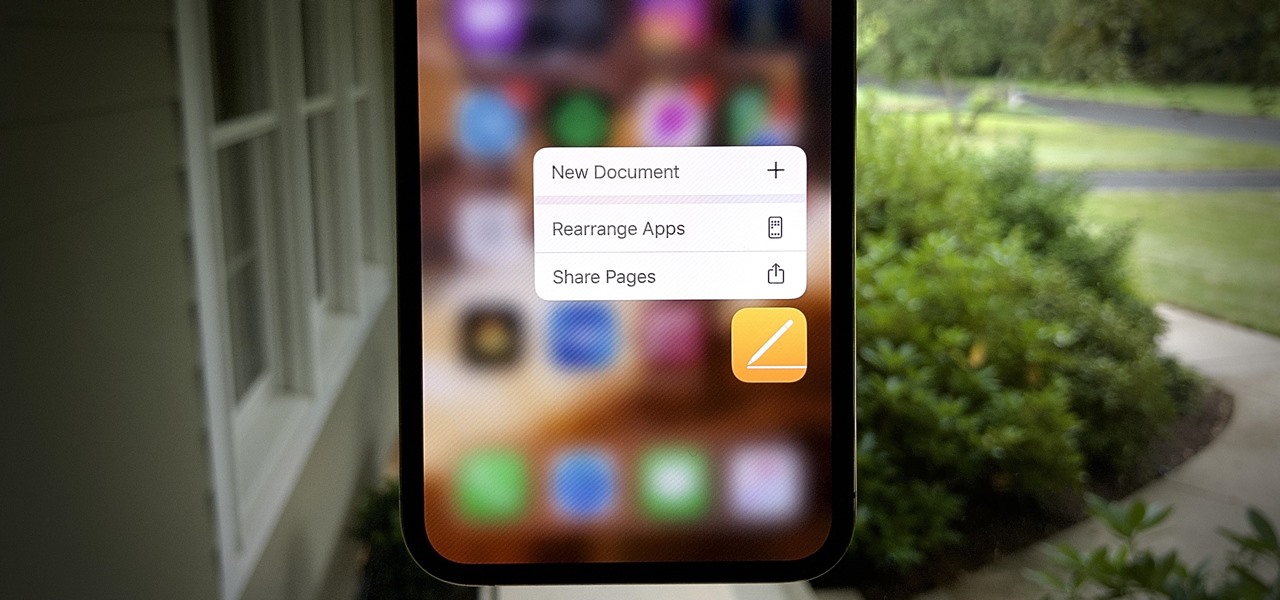
We're basically living in the future, so let's work like we are. For decades, we have, without question, opened a word processor like Pages, and clicked or tapped our way to starting a new document. What's wrong with that? It's unnecessary. We all have a digital assistant living in our iPhone, one that can start up a new Pages doc by verbal request.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

Business hours and addresses change, but they're not always updated on Yelp by business owners for the rest of us to see. Showing up when a business is closed or going to the incorrect address is a major annoyance, which is why the company allows us, the customers, to help update business information through the Yelp mobile app on iOS and Android. If owners won't do it, somebody has to.

Although the Galaxy Note 9 is an amazing phone, many members of the Android community won't even look at it. This isn't just because of the Samsung Experience skin, but the large amount of bloatware that comes with this device. However, with a little work, you can remove all of it.
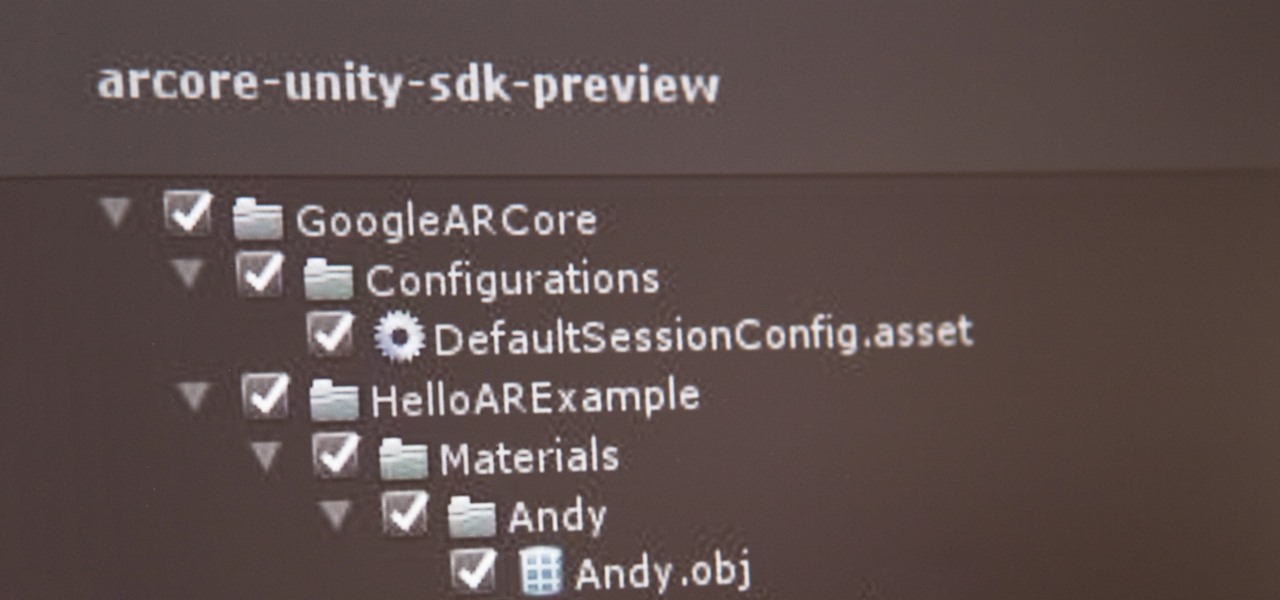
If you've contemplated what's possible with augmented reality on mobile devices, and your interest has been piqued enough to start building your own Android-based AR app, then this is a great place to to acquire the basic beginner skills to complete it. Once we get everything installed, we'll create a simple project that allows us to detect surfaces and place custom objects on those surfaces.

As we aim for a wireless world, technology's reliance on cloud computing services is becoming more apparent every day. As 5G begins rolling out later this year and network communications become even faster and more reliable, so grows our dependency on the services offered in the cloud.

WordPress did not become what is arguably the most popular blogging and CMS platform on the planet because it was difficult to use. Rather, its user-friendly and rich feature set led to it finding a home on somewhere north of 70 million websites—and that's just counting blogs hosted on WordPress.com.

When Microsoft release an update to the HoloLens Development Edition at the end of May, there were a bunch of cool new features added in. Among them: New voice controls that make working in the HoloLens operating system much easier.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...
When anyone brings up Tasker, the first topic that always gets discussed is how powerful the Android automation app can be. But all of that power can be overwhelming for some people, so even if you're a Tasker pro, it's hard to share your awesome creations with friends that don't quite understand what's going on.

Android has a single text file named build.prop that determines tons of various system-wide settings on your device. You need root access to edit this file, since it's stored on the system partition—but the various lines of codes it contains are actually fairly easy to interpret and modify.

In the last iteration of how to train your python, we covered if/else and conditional statements. We're going to diverge a little today and cover lists. Lists are simply that, lists. It is a set of values located under one variable. Now that we know the definition of a list, let's learn about them! List Basics

In most cases, when the free trial of software is over, that's it—you're left to either pay for it or find an alternative. But what happens if the trial wasn't long enough to sell you on the product? It'd be nice if there was a way to test it out again without having to whip out your credit card.

Microsoft's new voice-enabled virtual assistant, Cortana, is a lot like a blend of Siri's personality and Google Now's predictive capabilities—but the best part is it's baked right into the taskbar in Windows 10.

While you may not have loads of secret files hiding on your computer, there might be one or two items that need a little extra security, like a file of website logins or a folder of risqué photos.

If you took a big step back and really looked at the world, you'd see how downright silly our nations look when they put up fences to separate themselves from one another. Creatures big and small roam free while respecting each other's space, but humans create borders and physical barriers to delineate their cultures.

Welcome back, my aspiring hackers! In recent tutorials, I have made reference to the name and location of the Linux devices in the file system, such as sda (first SATA or SCSI drive). Specifically, I have mentioned the way that Linux designates hard drives when making an image of a hard drive for forensic purposes.

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.

Now that iOS 7 is out, what can you do that you couldn't do before? In this softModder guide, I'm going to cover all that's new and noteworthy about iOS 7. I've been playing around with it on my iPhone 5 since the first beta came out, so I'm excited to show you some of the secrets that are lurking within Apple's newest mobile operating system.

This video turtorial is on how to make a free website (without any cost at all). There are two ways to make a website and you can choose whichever one you want. First, go to Webs.com. Go down to "pick a site address" and create a password. Click "create a website". Fill in the information requested. Choose a template. Agree to terms of service. Click create site. Press "No thanks" and continue to next page and start to build. Click content box button. Choose page options. Edit template.

In order to play the game Risk, begin by setting up. Name a banker. Players choose a color. The number of players determines the number of armies. Remove the jokers from the country card packs. Shuffle the cards. Deal them face down. Players may not get an equal number.
If you're tired of the boring old ringtones on your iPhone but don't want to shell out extra dough to buy a new one, here's an easy way to make your own.

It's never too early to put away money for your child's education. Consider these options before choosing a plan. Watch this video to learn how to get started with a college savings plan.

In this how to video, you will learn how to convert DVD movies to AVI or any other type of file for free. First, you will need to download DVDx 2.1 and the install it. Next, open the program and insert the DVD disc you want to copy. Go to file and click DVD root. Find the video and select the video_ts folder. You will see the IFO files. Look for the one with the longest time. Click on this one and press select. If you have a DVD already ripped on your hard drive go to file and click open IFO....
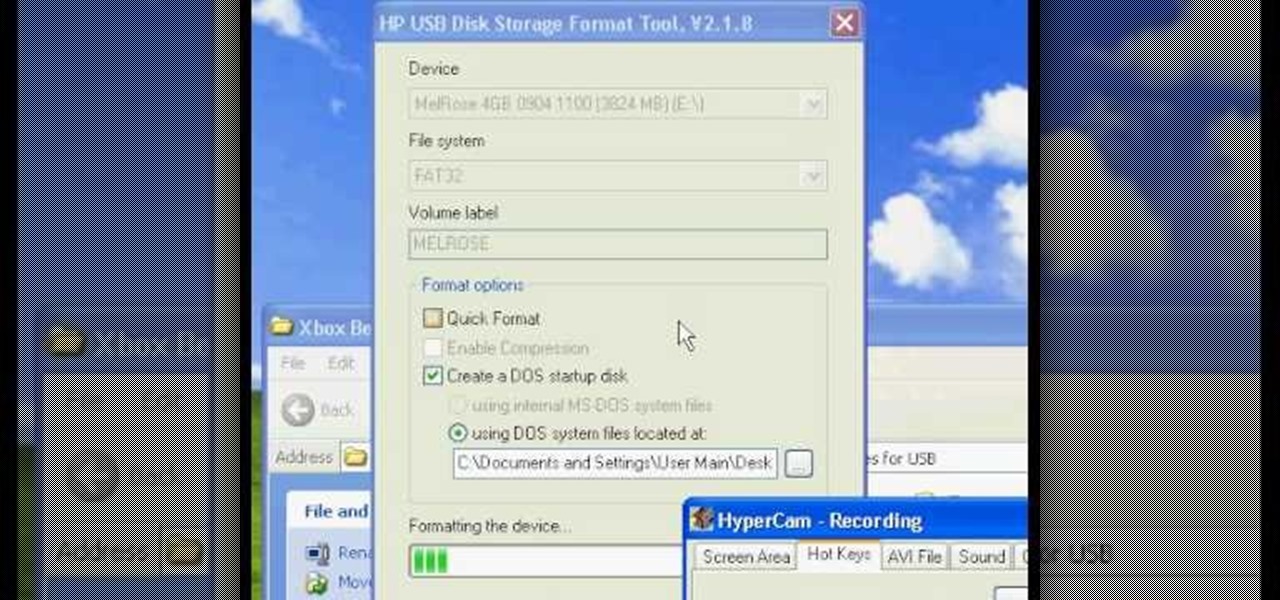
Have you ever wondered how to prepare a USB drive to flash an Xbox 360? Here is the how-to -video on how to create an USB drive for flashing your Xbox 360 benq drive. To make a bootable flash drive and to prepare it to flash XBox benq drive you have to download the “Xbox benq flashing files for USB” folder from the below mentioned link.http://www.MegaShare.com/1721713
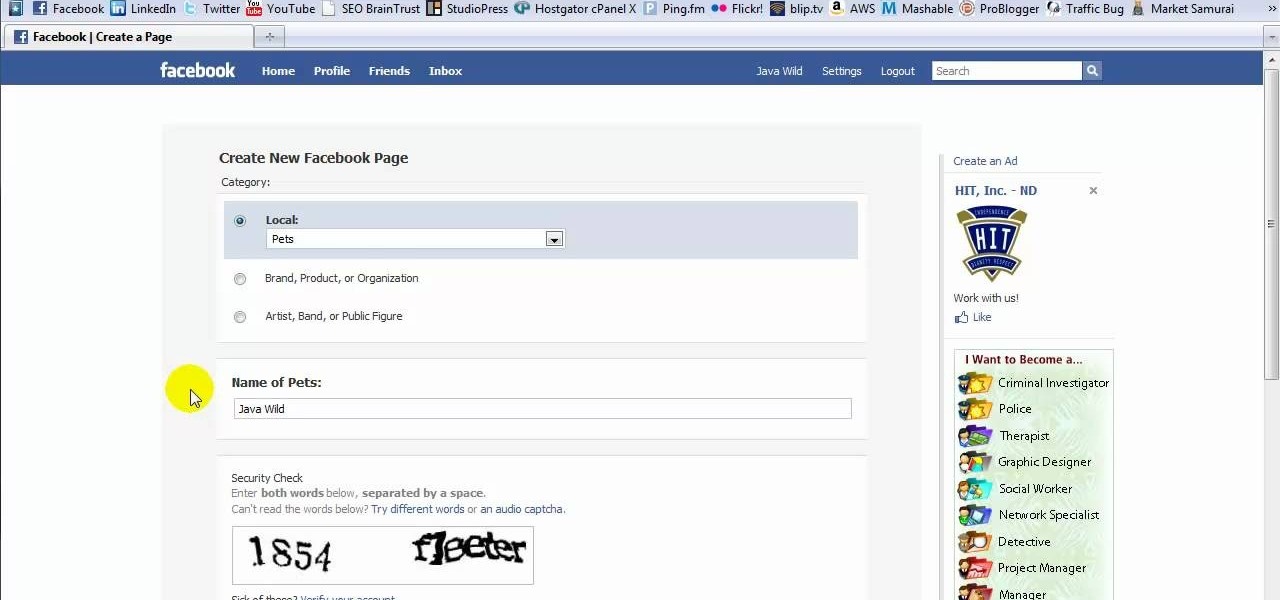
This tutorial is in response to mail to Facebook. Scott Wilde leads you through the process. You can start by creating a brand new profile page. In this case, Mr. Wilde created a profile page for his dog Java Wilde so he could have a fresh new page without having to alter his initial profile page. Fan pages are different than your base profile. Your base profile is not indexed, it is not public, it is private and limited to 5000 friends. A fan page is unlimited up to millions of fans and it c...

Having a boring Facebook profile is lame! Impress your friends and flaunt your social networking skills by sprucing up your Facebook profile.

Some Chinese dishes that sound healthy are surprisingly fat-laden. These tips will help you avoid diet land mines.