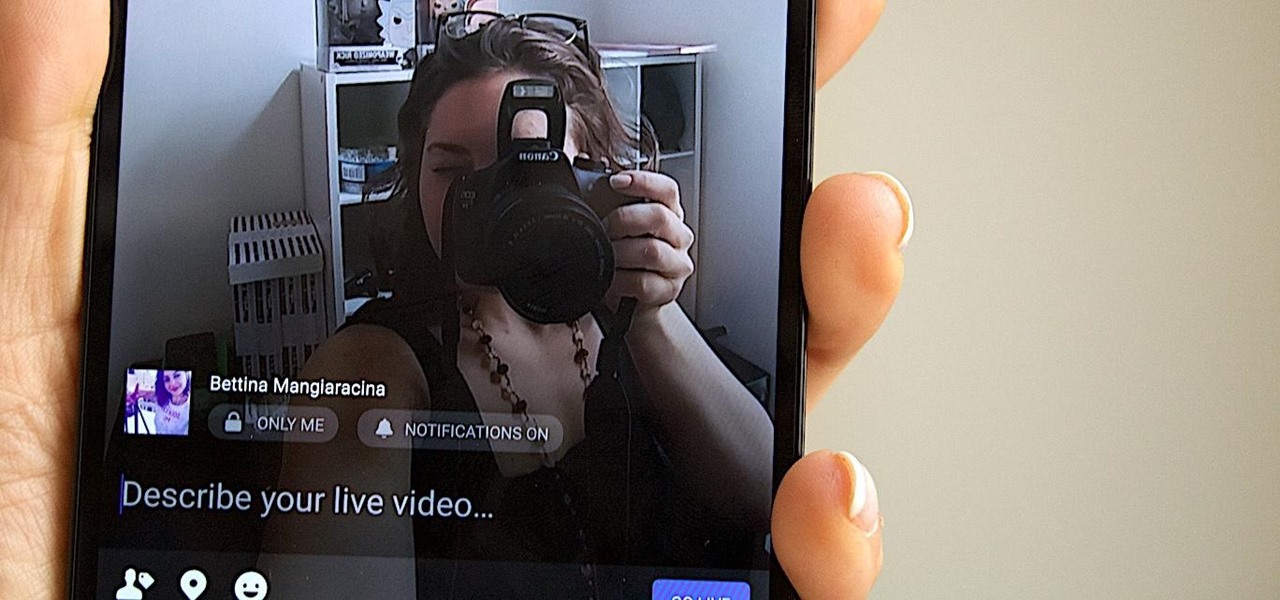
It looks like "going live" is another thing we all have to figure out how to do to remain relevant in this very Facebook-driven world. But why would you ever want to go live? That's really up to you.
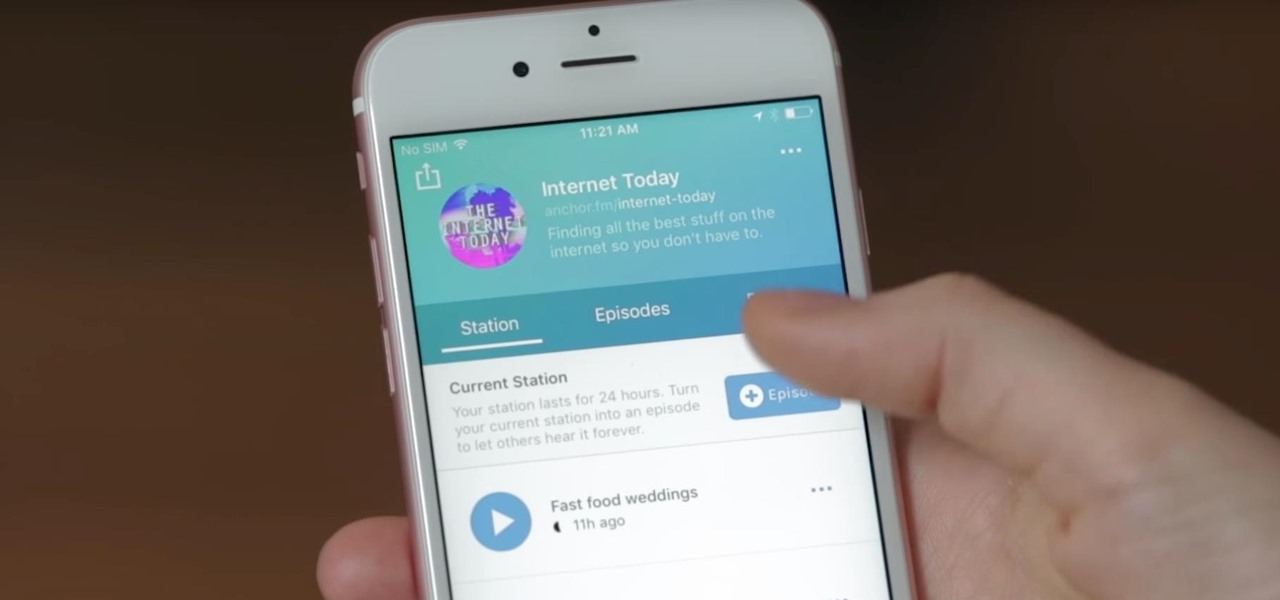
Anchor has been called the audio equivalent of Snapchat. The app lets you record audio and broadcast it to whomever you follow. If you haven't heard of the app, get familiar with it because it has announced an easy way for you to record and publish podcasts from your smartphone.
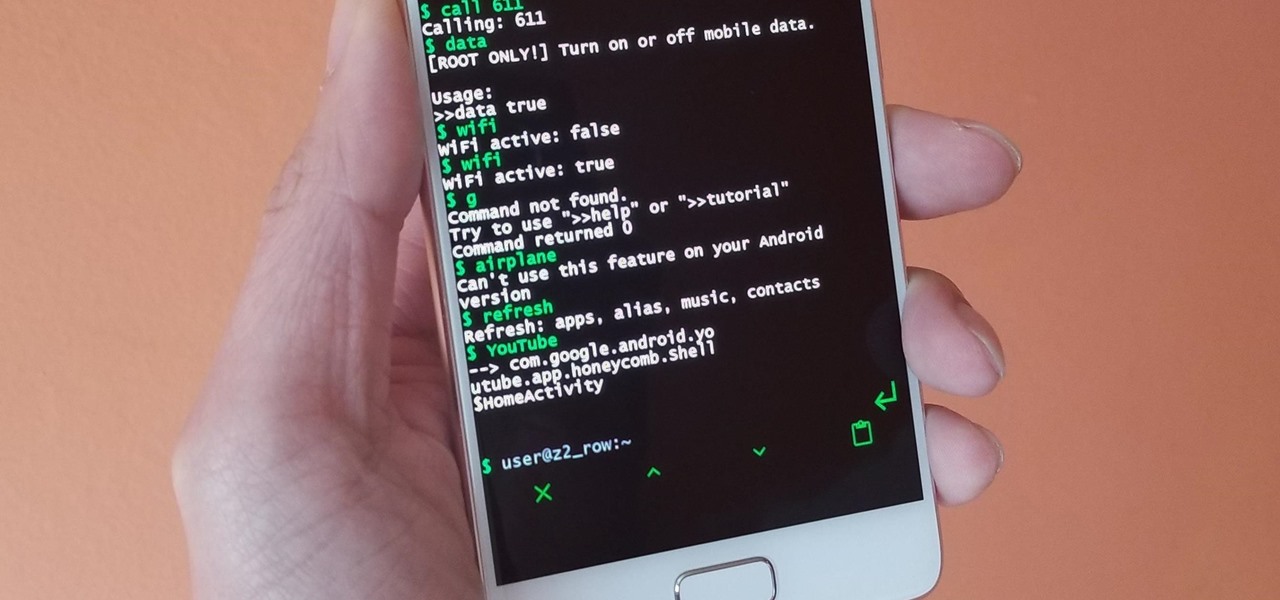
Running commands on Linux seems so complicated for the layman that it may as well be a foreign language. But for the die-hard terminal users, or for those who are just curious about the Linux experience, there's a new Android launcher that gives your home screen a command line makeover.

Last week, the internet was ablaze with talk about the Galaxy S8's home button, because it subtly changes positions without the phone alerting you. This feature was included to stop burn-in issues with the screen, and the general consensus from tech sites was the screens would not experience any burn-in at all.

Those of us with modern smartphones know that 4G LTE networks have provided us with a phenomenal experience. One light years beyond what we had access to before. For some time, AT&T has been teasing its dive into the next iteration of network speeds, agonizingly doing so without any specific dates for when they would actually deliver. But today, AT&T confirmed what they call the "5G Evolution," and it's available now.

Our quest to find novel compounds in nature that we can use against human diseases —a process called bioprospecting — has led a research team to a small frog found in India. From the skin slime of the colorful Hydrophylax bahuvistara, researchers reported finding a peptide — a small piece of protein — that can destroy many strains of human flu and can even protect mice against the flu.

Over the past eight months, ten infants at UC Irvine Medical Center tested positive for the same strand of methicillin-resistant Staphylococcus aureus (MRSA). Despite the danger of this superbug due to its high resistance to most antibiotics, this information was only released to the public on Thursday. Thankfully, all ten babies survived and are currently healthy.

In this first part of our tutorial series on making physical objects come to life on HoloLens, we are going to set up Vuforia in Unity.

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.

The freezer section at your local grocery store may have plenty of popsicle flavors, but they're mostly going to be the same old fruit-flavored varities you've been shoving in your mouths for years. None of those will truly get your tastebuds rolling like some creative homemade versions will. We've already shown you some crazy sounding ones made with Oreos, veggies, and coconut flakes, but now we're back with some more chilling ideas. Just wait until you get down to the corn one!

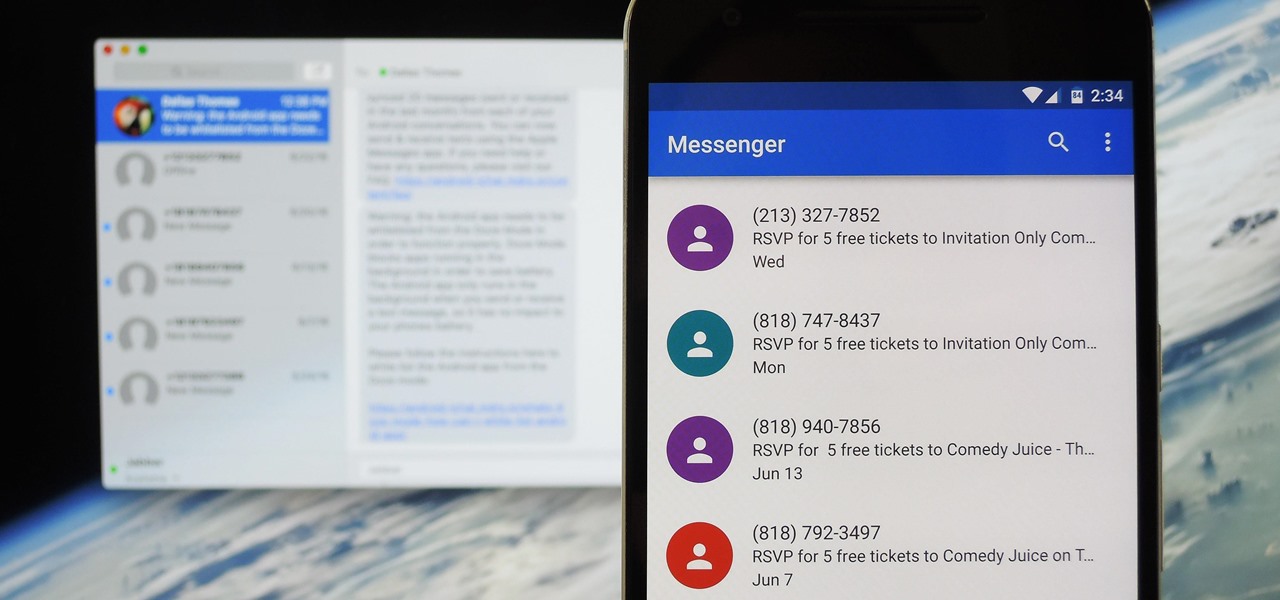
Prior to this year's WWDC, there were lots of rumors that Apple might finally be making a version of iMessage for Android. While that never came to fruition, a few big updates to a very useful app have now ensured that we can seamlessly send and receive Android texts in Apple Messages on our Macs.

This is the second installment of the short series on how to remove user passwords in Windows. Once again this has only been tested on Windows 7. If I can find some time between two jobs and school I'll test all the ways on Windows 10 and Windows 8/8.1.

Welcome back everyone! It's been quite a while hasn't it? Today we're going to kick off the second part of the Python training series by introducing modules. We'll start off by explaining what a module is and we'll give an example. So, let's get started!

Welcome back, my budding hackers! Digital forensics is one of IT's most rapid-growing disciplines. All hackers should be familiar with digital forensics if for no other reason than to protect themselves. More than one hacker has been apprehended because they were unaware of the evidence trail they left behind.

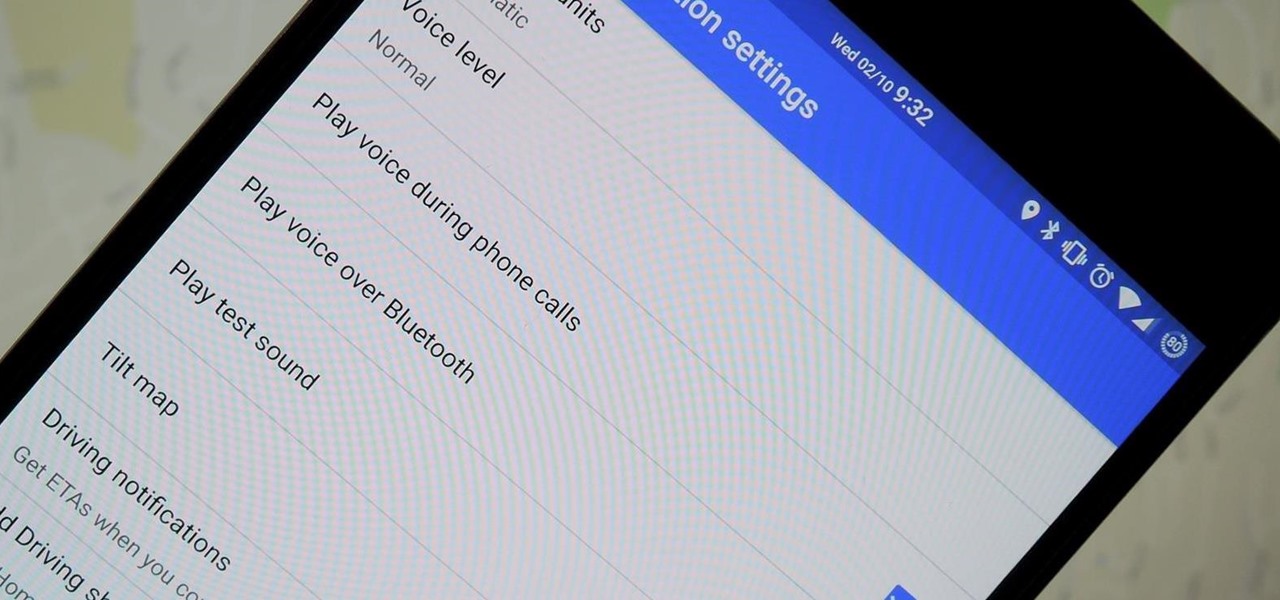
We've all been there. You're driving along with Google Maps pointing the way when you get a call from your friend asking you how much longer it'll be until you show up. You try to offer some lame excuse about how something came up last-minute, but you're interrupted, quite rudely, by Maps's voice guidance. The voice butts in again, and again, and again, to the point that you consider having Maps navigate you to the nearest cliff so that you can drive off it.

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

Hello readers, in this tutorial, we will be discussing how to perform file operations such as reading and writing.

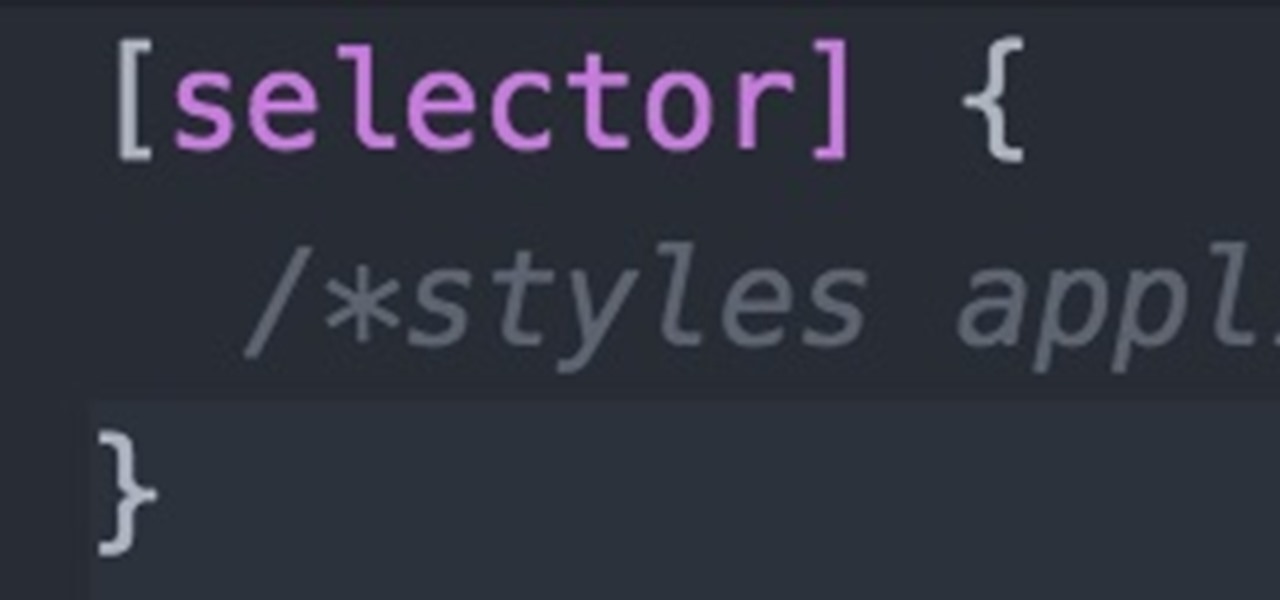
Welcome back Null-Byters! You finally have the pre-basics of CSS and we can begin with styling our web page. If you did not read our last adventure, I suggest you go and read it.

Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.

Video covering how to set up a Venn diagram. The video covers how to draw the diagram and then look at a set of data and place the data in the correct part of the Venn diagram. The sample problem is as follows.

If you're a U.S. expat living, traveling, or studying abroad, or just someone who typically uses virtual private networks (VPNs) in order to access the North American video libraries of services like Hulu or Netflix, you were probably surprised to see that these video streaming services don't work on your Chromecast or Chromecast 2.

So, how does someone keep their hacking life completely secret? What This Is:

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.

Is this what happens when lightning hits sand? It turns out that when lightning hits sand, it makes little holes in it. Sadly, this picture was part of an internet hoax that circulated in 2013.

Programming is an essential thing in hacking/pentesting, and at times, I do not feel that it is being addressed enough here, at Null-byte. I understand that this is a forum dedicated for hacking, but I'll address some of the stuff I feel is muy importante about programming. I am not a professional programmer, but I do have experience and I do want to share some of the stuff professionals have taught me.

SET is great when you have a short space of time at hand, however sometimes you want to know whats actually going on under the hood or have found a site you can't clone with SET.

Why did I write this when they're tons of scanning tools available.

Welcome back, my novice hackers! As most of you know by now, a notorious commercial, legal hacking group named "Hacking Team" was recently hacked. As part of the hack, thousands of emails and other material on their servers was divulged. Among the material released were three zero-day exploits. In this tutorial, we will walk through the steps to load one of them, which has become known as the CVE-2015-5119 exploit.

Disclaimer: All information in this tutorial is for entertainment and educational purposes ONLY. You pesky teenagers.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

Hi there, Crackers, Welcome to my 7th post (Part-1), this tutorial will explain about the basics of Batch Scripting.

One shrinks their nose when the name of Durian fruit is brought up but are you aware of all the health benefits it can provide? The Durian fruit on its own can help control Blood pressure, blood sugar, Anaemia and depression. Not only this, the fruit has the miraculous qualities that can prevent cardiovascular diseases, better the digestive system, better the Libido and provide instant energy. For all the skin conscious people, here's news for you! The fruit can delay ageing process and make ...

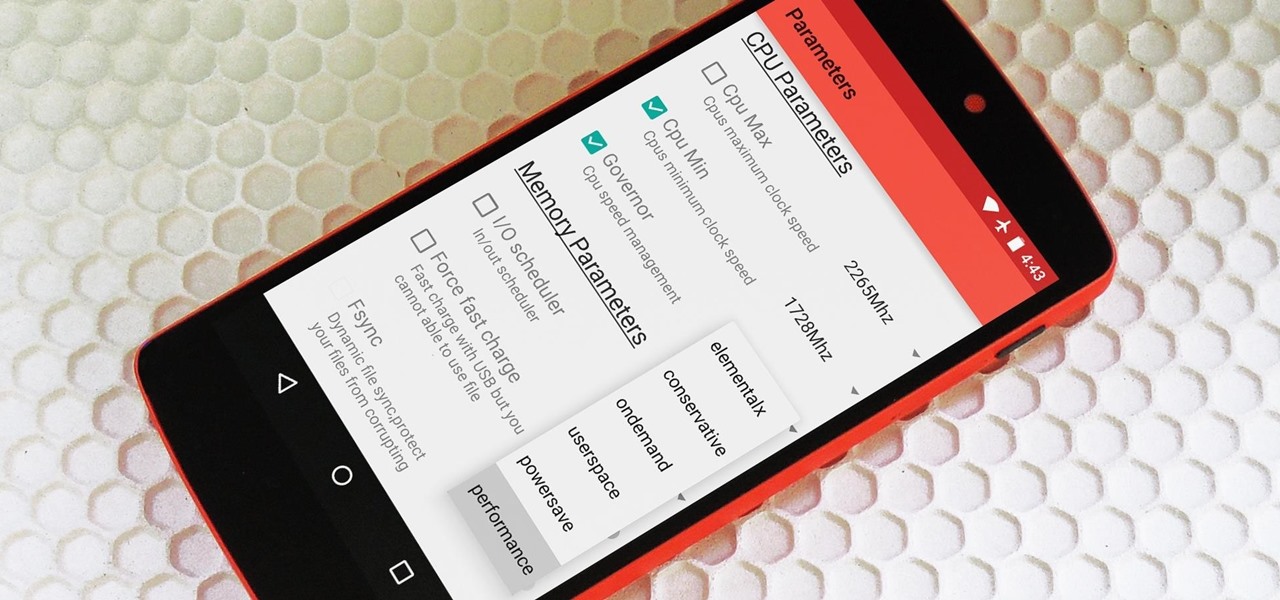
Deep down at the core of Android lies the system kernel, which serves as a bridge between software and hardware. Custom kernels can be installed in place of the stock offering, and these are generally optimized for better performance or increased battery efficiency.

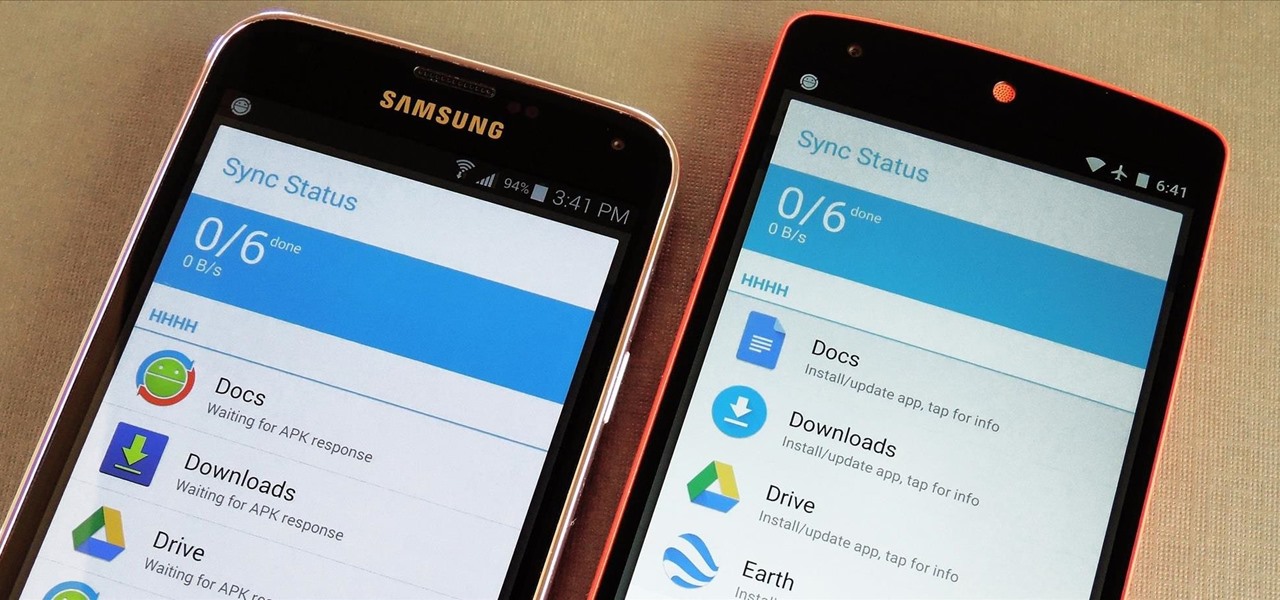
If you own multiple Android devices, you're surely familiar with the struggle of keeping apps and games in sync. While games with proper Google Play Games support will indeed sync progress across your phone and tablet, many developers neglect to include this feature in their wares.

Apple scrubbed the floor clean of all existing text-bombing apps in the iOS App Store, and even though there were once a ton of these apps in Cydia, the go-to store for jailbroken devices, there few and far between these days. If they do exist, they either cost money or don't work as advertised.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

To play Minecraft with mods you will need to install Forge. Most people think this is hard to do, not so. It is very simple and in less than 5 minutes you can be playing Modded Minecraft.

Emojis have transformed the way we laugh and cry, tell stories, give responses, and express excitement to get a drink after work — without any actual text required. Heck, in an incredibly meta move, the Oxford Dictionary even named the "Face with Tears of Joy" emoji as their word of the year at one point. So how could you not want to be an emoji character for Halloween? Emojis are everywhere. The ubiquitous symbols are already on smartphones, tablets, and social networks, so why not help them...

Voicemails are like chores for me. I have to listen to them, but never really feel like doing it. When I finally do, most of them get deleted right away, but every so often they'll be one I save and listen to over and over again, whether it's a cute birthday wish from grandma or a hilarious joke from my friend.