1. The following Steps shows how to open a URL in a Web Browser, using a Button Click from a Flash Application. 2. Open a new Flash Application and place a Rectangle Shape from Tools and inside place a Text Box and Enter a Text named "URL". 3. Then convert it to Symbol by Right Click->Convert to Symbol and selecting type as Button. 4. Goto Button Properties and Name the button instance as "btnurl" 5. Then in the Action Screen Create a OnRelease() Event function for Button "btnurl" 6. use a me...

Bid Whist can be a fun game for family or friends. It's challenging enough for adults, but enjoyable for kids too. Bidding and predicting wins are what make playing Bid Whist fun and exciting, whether you win or lose.
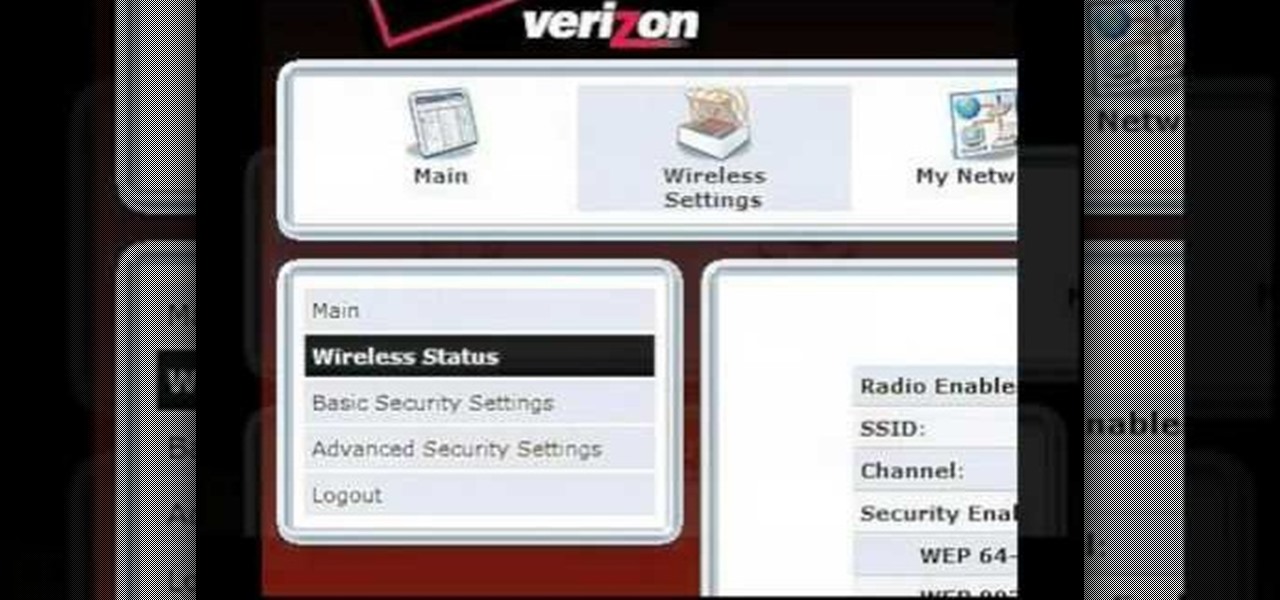
Learn how to change your wireless network name on Verizon's FiOS Router. You'll see the easy steps on how to change your wireless network name and / or password for your MI424WR Verizon FiOS Router, manufactured by Actiontec Electronics, Inc.

Learn how to play "Remember the Name" by Fort Minor on piano or keyboard with this tutorial. This popular Fort Minor song is made up of basic minor arpeggios. Watch this quick how to video and you will be playing "Remember the Name" in no time

Bloatware is a problem on Android, and it's not just a Samsung thing. Removing apps that have the Uninstall or Disable button grayed out in Settings has always involved sending ADB commands to your phone from a computer, which itself was always such a pain to set up. Thankfully, that has finally changed.
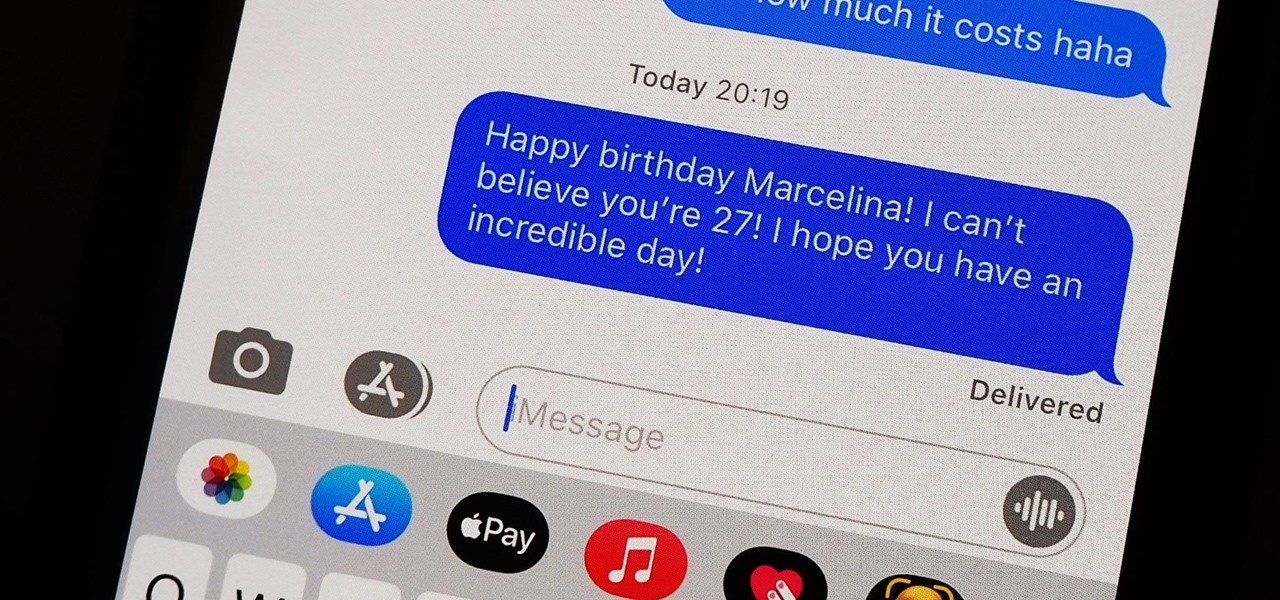
You should know the birthday for a parent, sibling, child, or significant other, but there are just too many people in your family and contacts to remember everybody's yearly birth anniversary. Still, everyone expects you to remember their birthday. To stop looking like a jerk, go a step further than putting birthdays in your calendar and make your iPhone help you send birthday wishes when their big day pops up.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

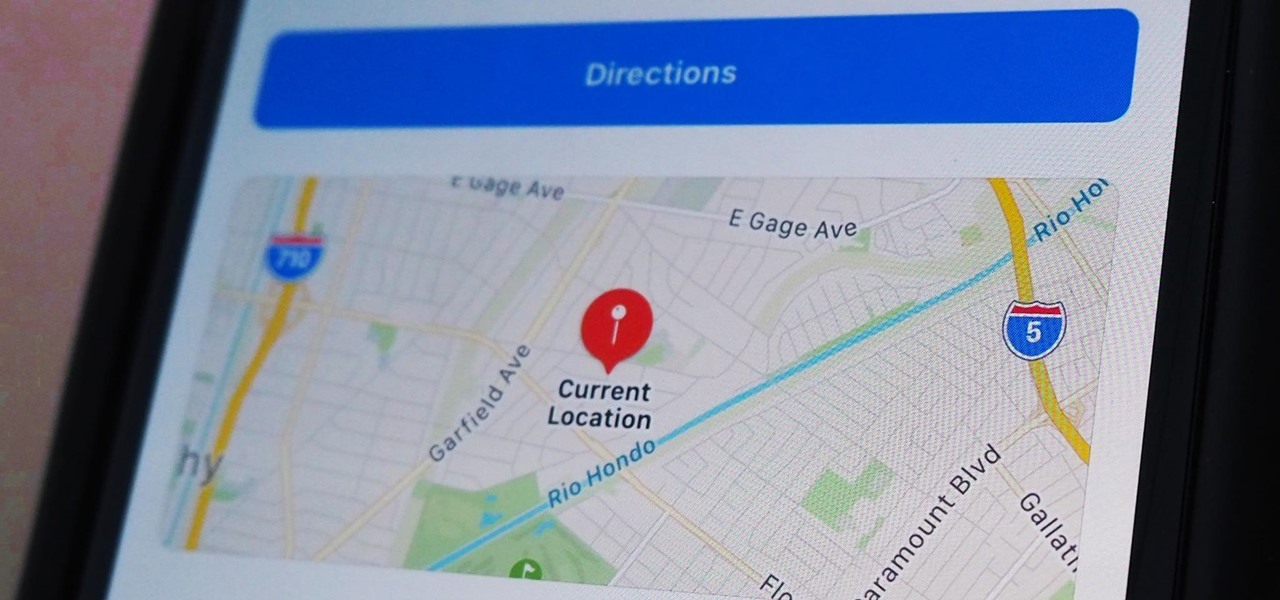
Apple makes it simple to share your location with your family and friends using tools built into the "info" page for each conversation thread in Messages. With those tools, you can send your current location or share trackable real-time coordinates. But iOS always has a few hidden tricks to make things easier than they seem, and that's precisely the case if all you need to do is share your current location.

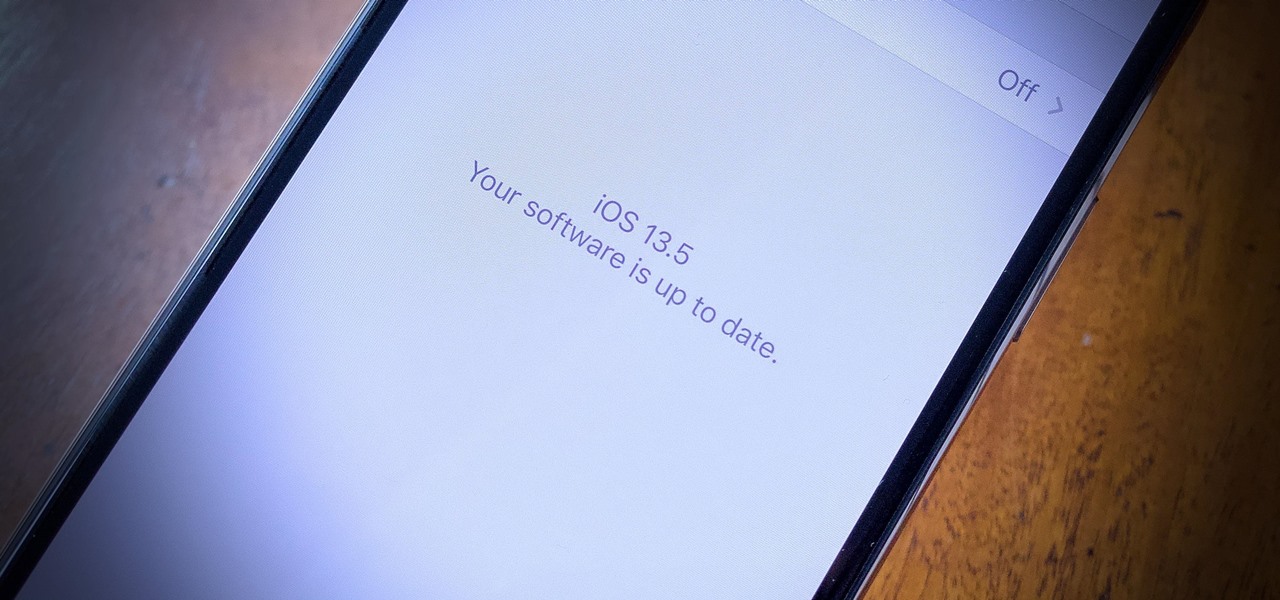
If you're a public beta tester, you woke up this morning with your iPhone running iOS 13.4.5. Today, Apple released the second beta for iOS 13.5. No, Apple didn't skip a version — 13.5 public beta 2 is essentially 13.4.5 public beta 2. So why the name change? Apple included the first API for its joint COVID-19 contact-tracing and exposure notification program with Google.

If you're using or need to use Zoom, the popular video teleconferencing service, you've almost certainly heard about "Zoombombing" by now. While Zoom has been adding security measures to address the problem, there are other things you can do to prevent or stop Zoombombers in their tracks so that your video meetings and chats go undisturbed and uninterrupted.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

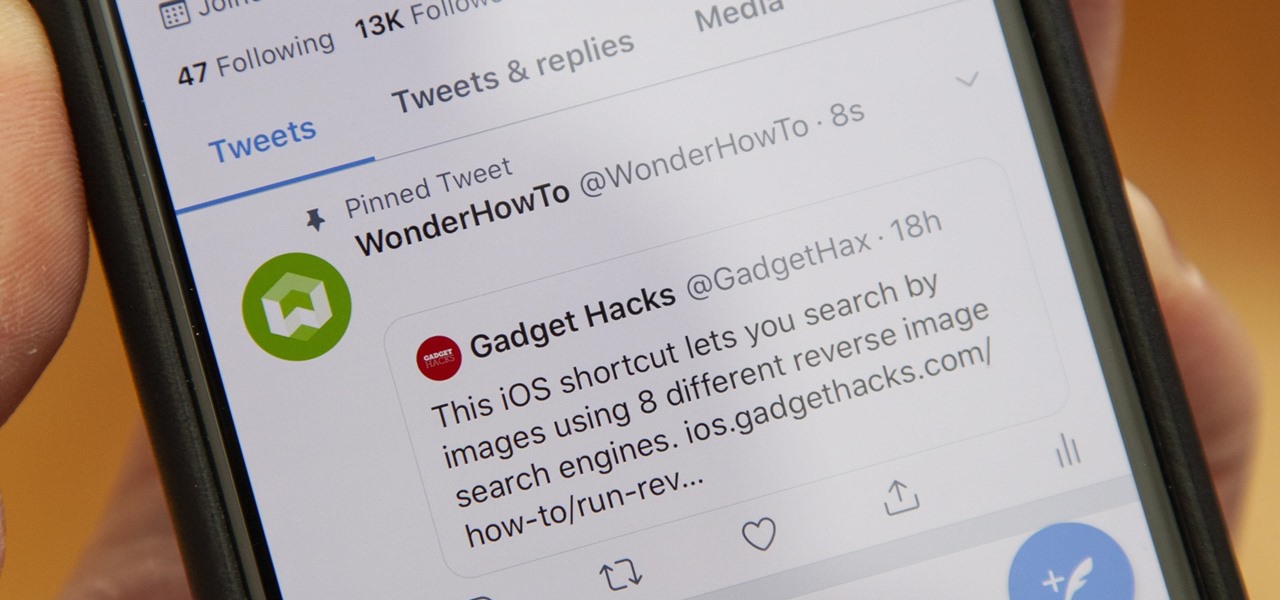
On Twitter, you can pin one of your tweets or replies to your profile, so it's the first post people see when they visit your page. However, Twitter prevents you from pinning someone else's tweet. You can't even pin something you retweet. There is a clever workaround, though, and it also works for posting empty tweets.

While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

What if you went to an art installation at one of the coolest venues in New York that you could then take with you anywhere in the world?

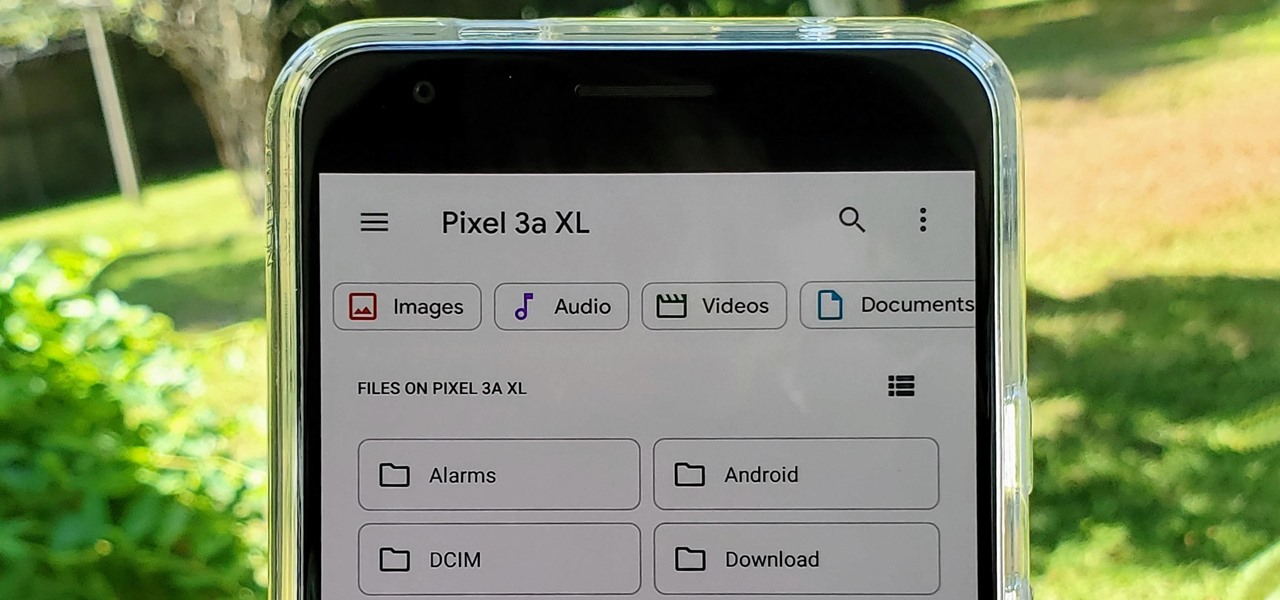
With the files on our devices getting more important as the years go by, the need to keep things organized continues to rise. The longer you have a device, the messier the internal storage might become. Having a file manager would be extremely useful in this situation. You could also reorganize the folder structure as well, just like you could on a desktop computer.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

There's something about alcohol that compels you to contact people. Most of the time, the drunken calls or messages you send out will have you cringing hard tomorrow morning. But if you have a jailbroken iPhone, you can help prevent this potential embarrassment with a free tweak.

Sure, Tony Stark was able to build the original Iron Man suit in a cave with a box of scraps, but can the average do-it-yourselfer replicate the EDITH smartglasses from Spider-Man: Far From Home in a similar fashion?

Businesses that have adopted enterprise-grade wearables for their workforces now have a new option among the multitude of AR productivity apps that can help their team members communicate in AR.

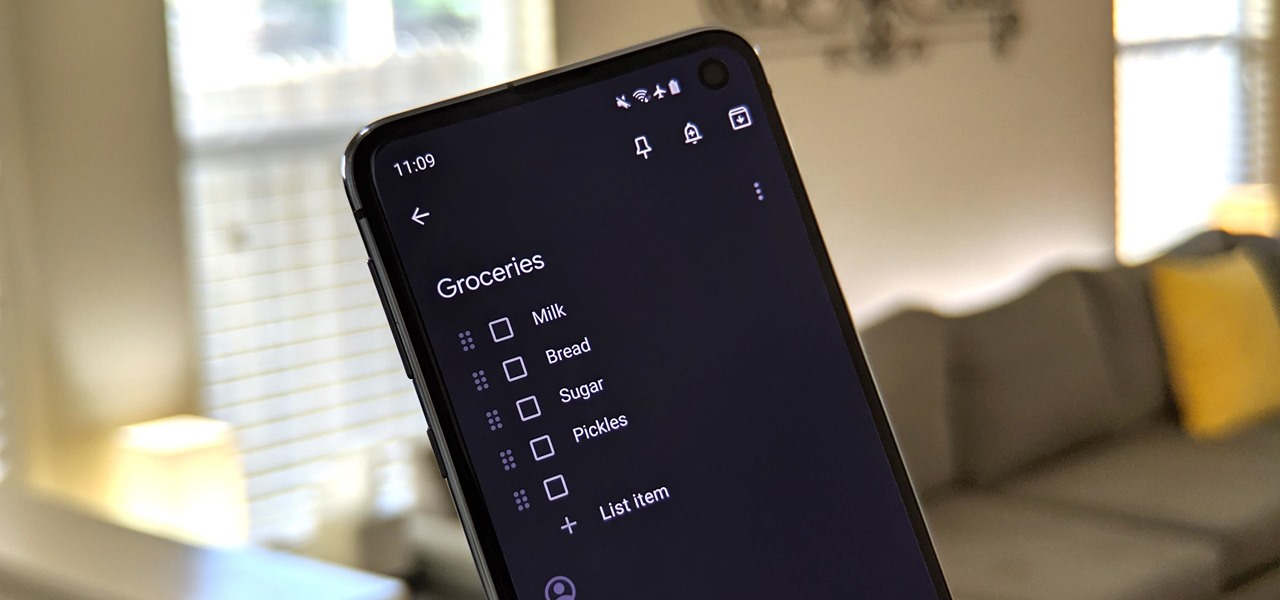
Life can get busy. Between work, school, and all the extracurricular activities, weekly chores like making a grocery list can get pushed to the back burner. But with a little help from the Google Keep app for Android or iPhone, you can at least make one thing easier.

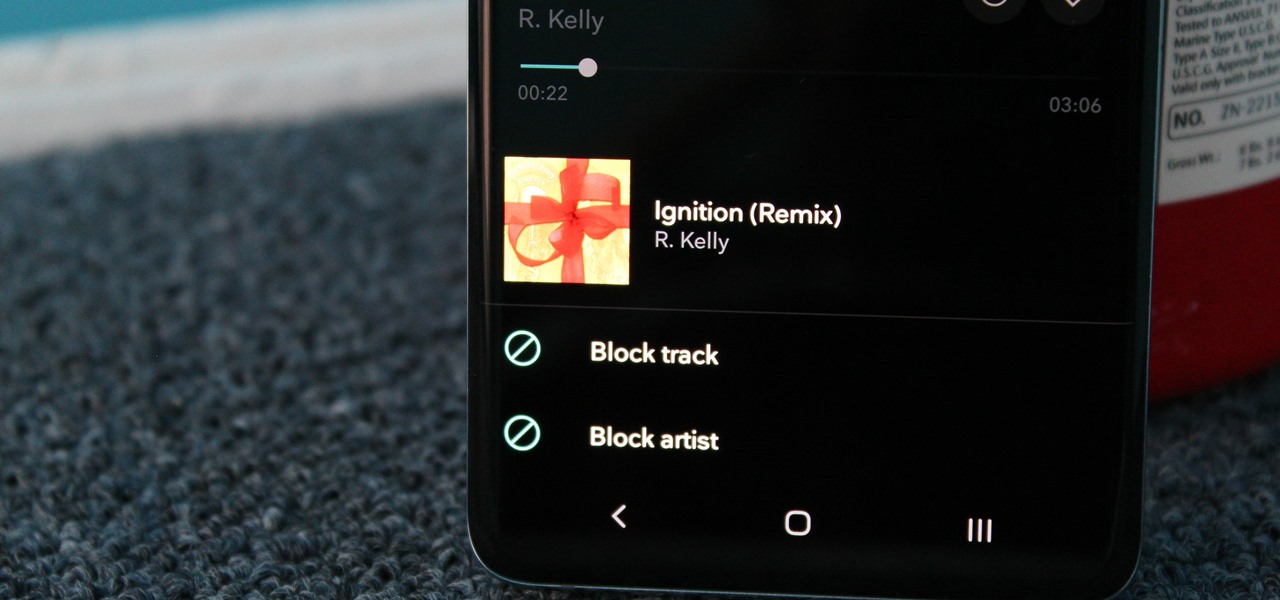
From XXXTentacion to R. Kelly, many artists have been accused of inappropriate actions, so some of us just don't want to hear their music anymore. However, each time streaming services attempt to ban such artists, they face heavy backlash. Recognizing this, Tidal decided to offer a different solution.

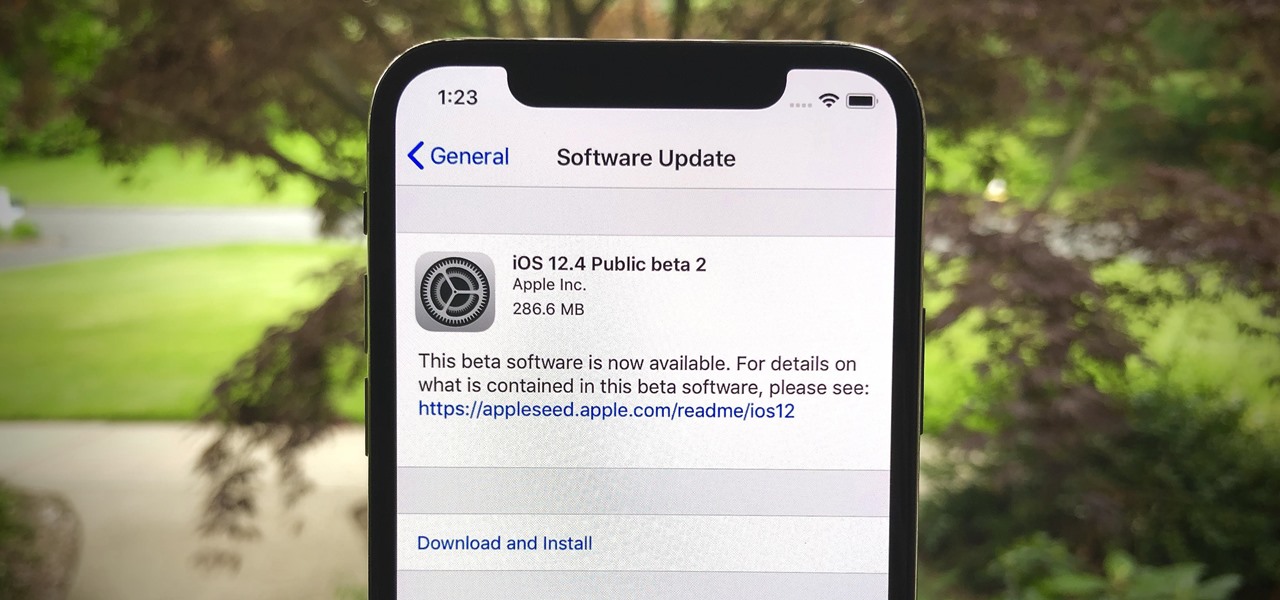
Public beta testers, you're in luck. Apple just released the second iOS 12.4 public beta today, May 20. The update comes five days after the release of the first developer beta for iOS 12.4 and seven days after the release of iOS 12.3. Public beta 2 and dev beta 2 were both released at the same time, something that doesn't happen often.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

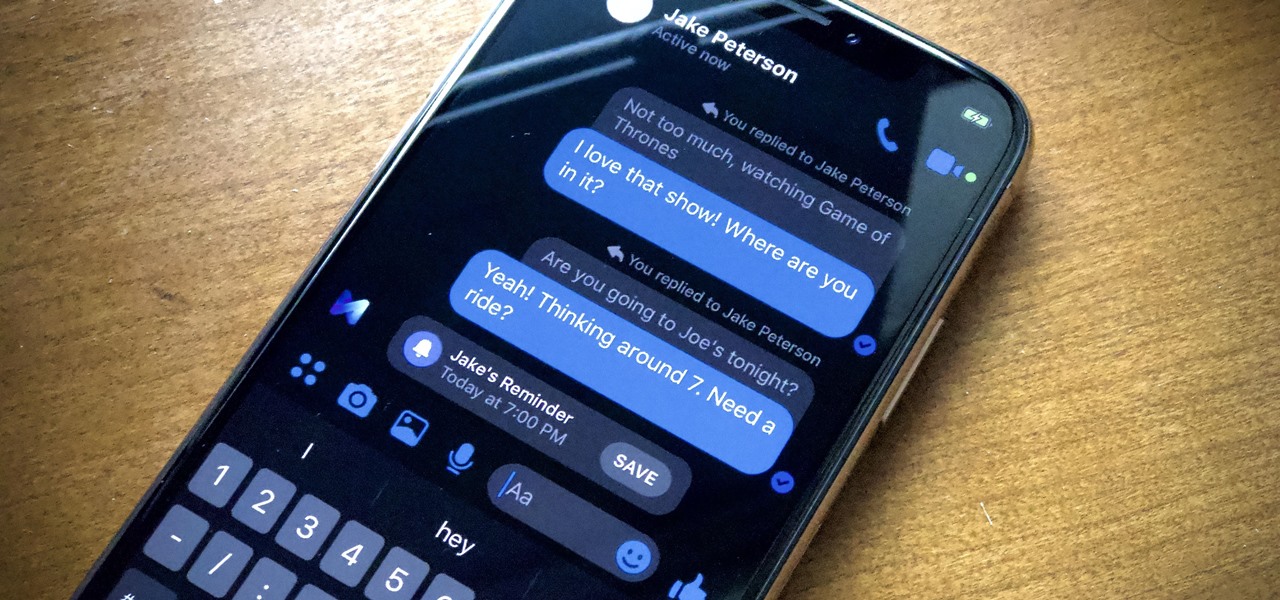
Text conversations can get confusing fast. In the time it takes to type up a response to your friend, they can send you one, two, three, or more messages. Once you send the original reply, it no longer makes sense in the context of the chat. Clear up the confusion with Facebook Messenger's "new" quote reply feature, which shows both you and your friend exactly what message you're responding to.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

Traditionally, if you were looking for end-to-end encrypted messaging, you'd stick with something like iMessage, WhatsApp, or Signal. However, if you already use Facebook Messenger, you have all you need for truly private chats with its built-in E2E encryption. It's available to all users, on Android and iOS — you just need to know where to look.

Intel's RealSense family of depth tracking cameras has a new addition with a different set of sensory capabilities.

An augmented reality system developed by Lyft might make it less awkward for drivers to figure out who they are supposed to pick up.

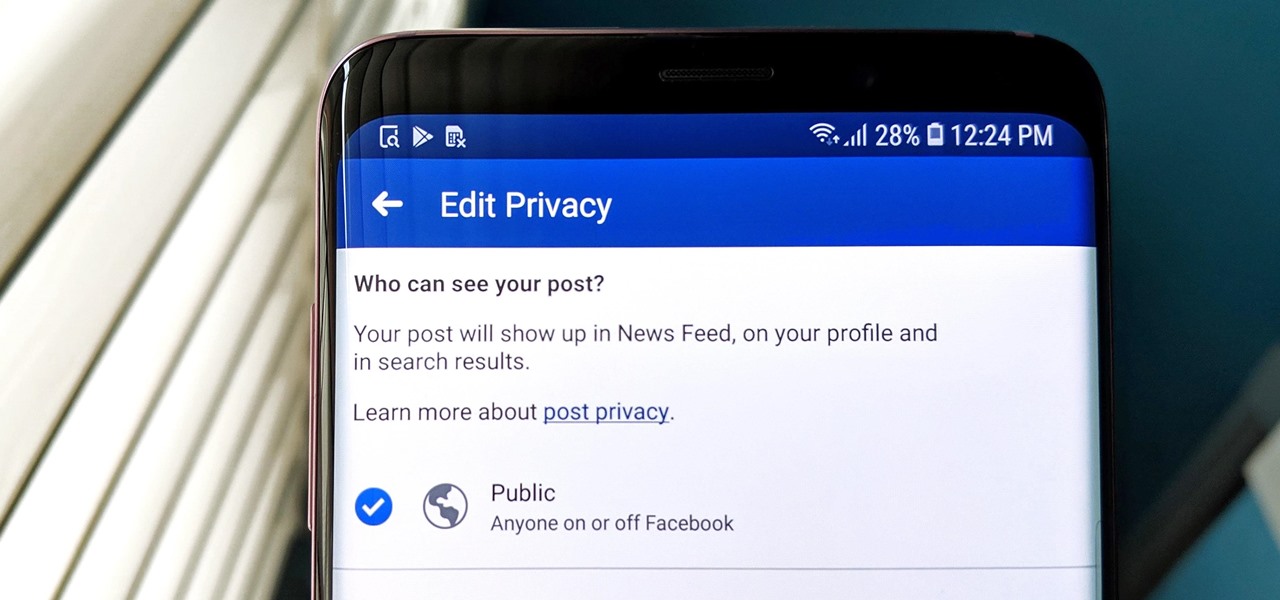
Facebook has grown into one of the central hubs of the internet where ideas are shared with others. But with the rise of brand development, individuals and companies need to get their messages out beyond their group of Facebook friends so it can be seen by more of the world.

Your iPhone is just that — yours. Why should your home screen look like everyone else's? While iOS, and by extension, Apple, famously locks its users into its way of doing things, there's a lot more room for customization than you'd think. Before you make the switch to Android, you might want to see what you can do with the iPhone you already have.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

One developer has taken the formal name of the Magic Leap One: Creator Edition quite literally with an app that enables users to create a custom universe in their own living room.

The new iPhone XS and XS Max have more issues than just their hefty price tags. Customers have only had the phones for a handful of days, but some are already complaining of cellular and Wi-Fi connectivity issues on both models. If your experience is the same on your XS or XS Max, there are steps you can take to get your iPhone reliably back online.

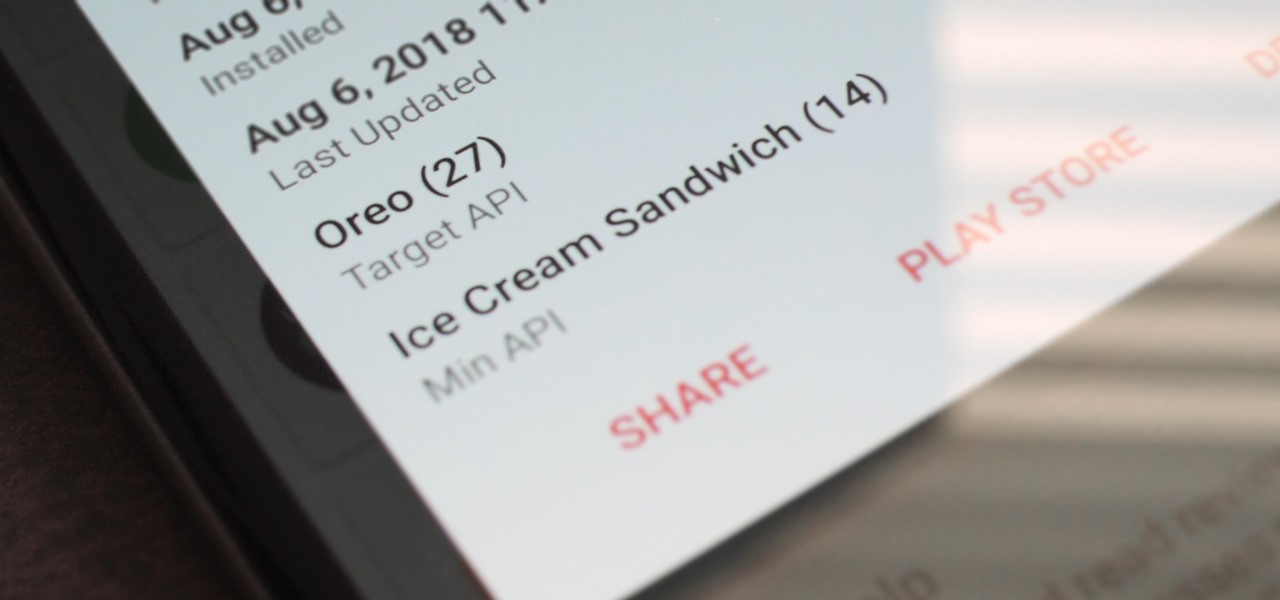
Starting November 1, 2018, Google will require that all new apps and updates to existing apps target Android 8.0 Oreo or higher. This move means the developers behind many of your favorite apps are now scrambling to get their software modernized, while others are considering abandoning outdated apps altogether.

Samsung has made curved displays a signature element of their flagship phones, but the Edge Screen, as it's called, has proven to be a magnet for accidental touches. Fortunately, Samsung has developed a little known app to help prevent this problem.

Instagram integrated Stories back in 2016, and it flew right by Snapchat as a whole, becoming a bigger success itself than the whole entire Snapchat app. Still, the constant bombardment of information can be tiring in Instagram, so much so that you may want to mediate what Stories are shown to you. Fortunately, there's a way to do just that — without unfollowing accounts or hashtags.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.