With Gboard, Google created a keyboard with more functionality than just inputting words. The app includes features such as GIF search and live text translation, but it gets even better when you let it learn more about you. With this data, Gboard grows from a good keyboard to one that can complete your sentences.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

As advanced as the Galaxy S9 is, it can still be susceptible to the occasional hiccup. Several factors can cause your smartphone to behave erratically or become unresponsive, such as buggy apps or updates that didn't properly install. Luckily, most of these issues can be easily resolved with a press of a button — or two, to be exact.

It turns out that coming up groundbreaking technology and raising billions may actually be the easy part for Magic Leap, as a new report has revealed yet another legal entanglement at the Florida-based company.

Mobile World Congress is a four-day event that is both a showcase and conference starring prominent figures in the mobile industry. Oftentimes, OEMs will use this event to announce new products for the upcoming year — and this year shouldn't be any different. Here are all the phones we expect to be announced.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

Following up on a preview of the deal we reported during last week's CES, Dell has officially announced the details around its role as the first company to resell the Meta 2 augmented reality headset.

If you've read our list of the best email clients for iOS, you'll know Apple's Mail app doesn't cut it when it comes to third-party integration. If you want to use some of your favorite apps directly in your mail client's calendar, go with Outlook.

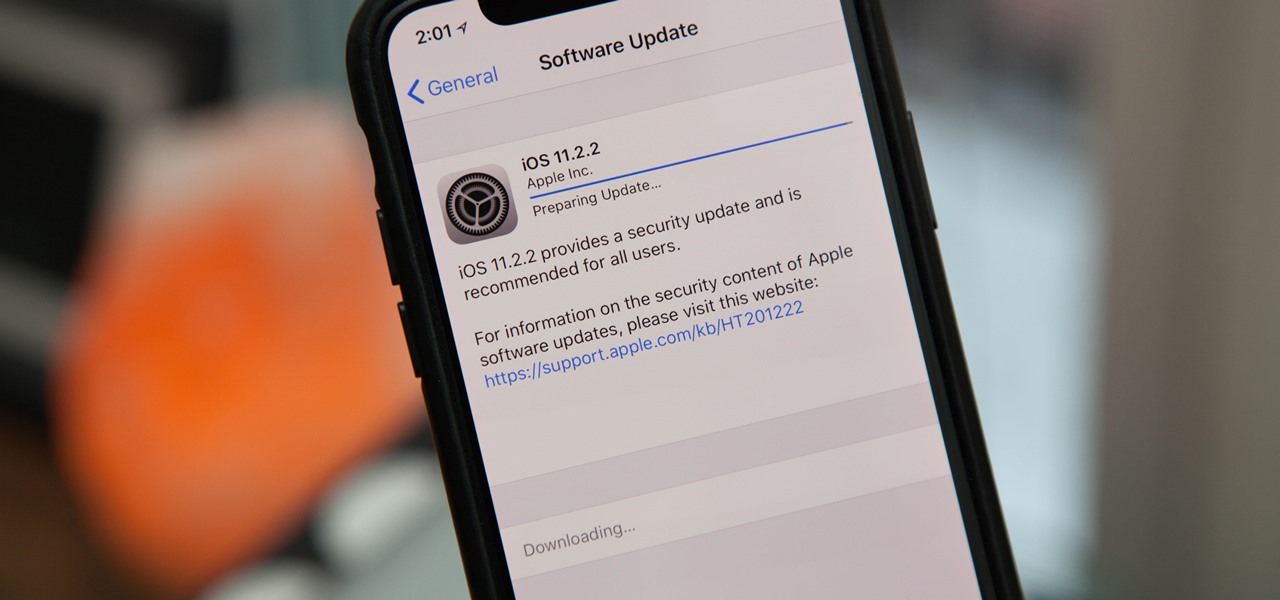
Apple released an iOS 11.2.2 update on Monday to iPads, iPhones, and iPod touches. The update comes as no surprise since news broke last week of a massive security vulnerabilities, named Meltdown and Spectre, which are found in smartphone chips throughout the industry. This update in large part addresses the security risks imposed by these chip flaws.

Facebook really wants your phone number, nagging you for one as soon as you join. This isn't all bad since it can help secure your account with two-factor authentication. On the flipside, this makes it easy to reveal the private phone numbers of virtually anyone on Facebook, including celebrities and politicians. We're going to look at how a hacker would do this and how to protect yourself.

With the V30, LG has really delivered an amazing smartphone that hits all the major features consumers want. Amazing camera, beautiful edge-to-edge display, great battery life, water resistance, and smooth performance — there isn't much not to like about the LG V30. Unfortunately, it does suffer from heavy bloatware thanks to the carriers. The good thing is, unlike in the past, you are not stuck with it.

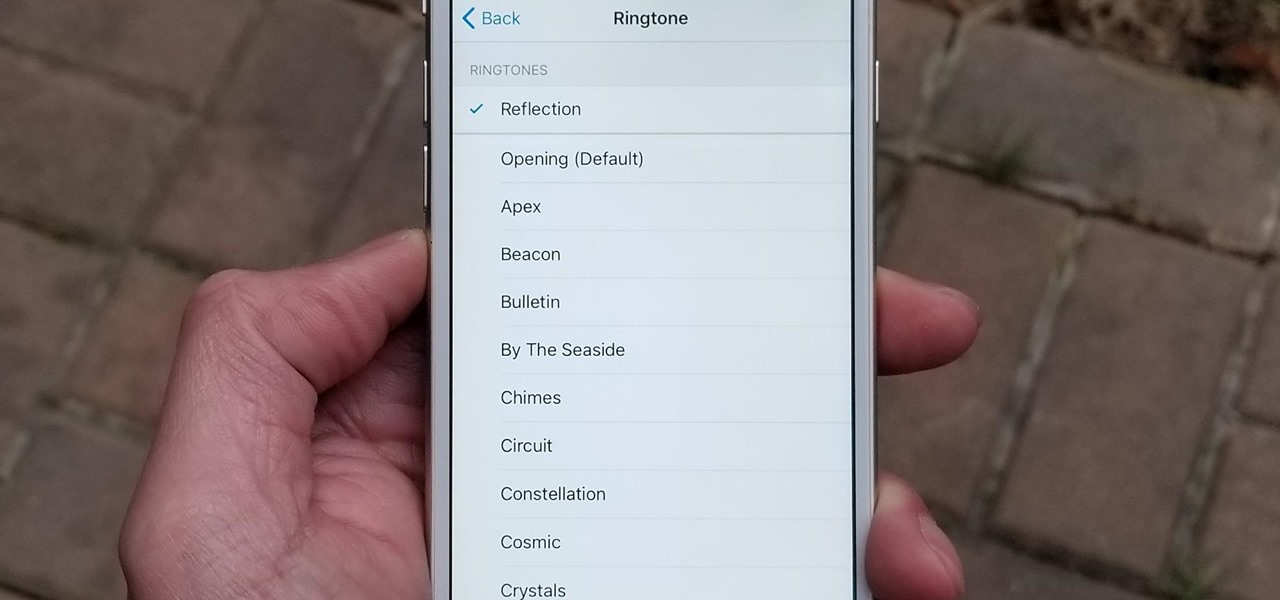
The new iPhone X sets itself apart from its predecessors not only as the first Apple smartphone to use an AMOLED screen, but also as the first iPhone to cost over $1,000. True to form as an exclusive device, Apple's latest flagship also features a distinct ringtone. With a little tinkering, however, you can make the new "Reflection" ringtone your very own, regardless of which iPhone you may have.

Despite mounting scientific evidence that viruses can cause changes in learning and memory, the reasons have remained elusive.

In the SoundCloud app, when you find an awesome song, you can build off of it by creating one killer music station that will give you like-minded songs you might not have ever discovered otherwise. And finding cool new songs and artists isn't the only reason to create a SoundCloud station — it's a great opportunity to set the tone of your workday or your party without ever worrying about the music ending.

The Sharknado franchise is, somehow, releasing a fifth movie "Sharknado 5: Global Swarming" (groan) next month. In anticipation of the film's release, the company has decided to create an augmented reality mobile game called, prepare yourself, "Sharknado: ShARkmented Reality".

These past few days have brought more bad news for our national parks. Interior Secretary Ryan Zinke confirmed that there will definitely be big cuts to national park budgets. This comes after Donald Trump's budget request revealed a call for $300 million cuts to national parks.

Admit it — many of us have not gotten in the Uber's we've requested. Sometimes, you just need to get someone else a cab that you're not going to be going with. No biggie ... but your friend doesn't have any connection to Uber or the driver, which can be a little awkward. Uber is addressing this slight issue today, with an update that allows you to officially request Ubers for others.

Combine the word "fake" with the word "Instagram" and you get what's called a "Finsta." If you are concerned about posting pictures on social media that you wouldn't want your family or boss to see, then a finsta account might be the thing that you need.

Instagram can be pretty exact when it comes to where you are located. That's why, sometimes, it's best never to geotag your precise location, but a broader area where you are less likely to get, well, um ... stalked?

Meet Android Excellence, Google's latest platform with the ability to showcase the highest quality apps and games on a quarterly basis. Sound familiar? It should.

Three variants of the Pixel 2 have appeared in Google's Android Open Source Project (AOSP) code, confirming various suspicions about which processor will power the Pixel 2.

HTC is working on another flagship device that's expected to be released in mid-April. After the disastrous reception of the recently released HTC U Ultra and HTC U Play, this new model could be the true HTC 10 successor we've all been waiting for.

Hear me out. No, really. Before you sharpen your pitchforks and give me anecdotal evidence of your Chinese restaurant syndrome, I think you need to know a few things about monosodium glutamate. First of all, it's a naturally-occurring chemical compound that can be found in anything from tomatoes to cheese, and is used in all kinds of foods from KFC to breakfast sandwiches. So spare me the comments on MSG and Chinese food—you probably eat MSG on a daily basis without even knowing it. (And also...

A company known as Cyanogen, Inc. has been in the news numerous times over the past year, and almost every time their name is brought up, it's amid reports of an impending doom. The writing is on the wall for the makers of Cyanogen OS, as it appears that there is little that can be done to prevent the company from going belly-up in the near future.

Since Ive started to learn about nmap and metasploit and other tools I was learning well but I had one problem,
Hi, I am Robel, I am here to let you know about how to hack windows admin password with out Sam files, this requires physical access and any boot operating system...I used Kali 1.8 , if it doesn't work make sure you have shuted it down properlyor use backtrack.

Even if you haven't heard of ube (pronounced "OO-beh"), you've probably seen pictures of desserts made with this brilliant purple yam.

Right, So i've been asking alot of questions here on Null-Byte and everyone has been really helpful to me.

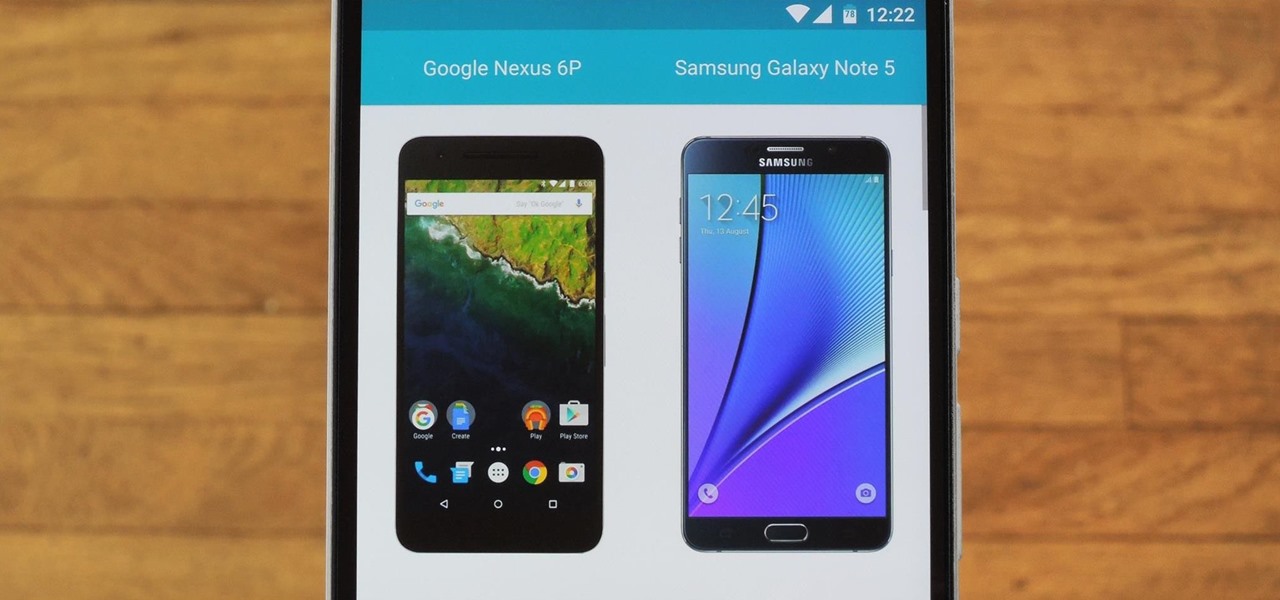
Shopping for a new phone is an entire ordeal. Even when you've narrowed it down to a few choices, comparing the finalists can be difficult, because specs and prices are scattered around on various different manufacturer websites, and if you're trying to do this on your current phone, most of these websites aren't optimized for mobile viewing.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the attacker portion of the shell. In this article, we'll just be testing it to see if everything works correctly.

In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

Android's main UI is looking so good these days that you hardly ever see developers spend time creating themes anymore. But even with the beauty of Material Design working in our favor now, there's always room for improvement, right?

Yes, I understand some people may consider this a repost. However, I have been searching for this answer for 3 weeks and after reading numerous reddit post, Kali Forums post and Null byte post I finally have gotten it to work for me. I would like to compile and share this information with you guys.

Hi guys. Hope you all had a good Christmas , today i have a tutorial for you.

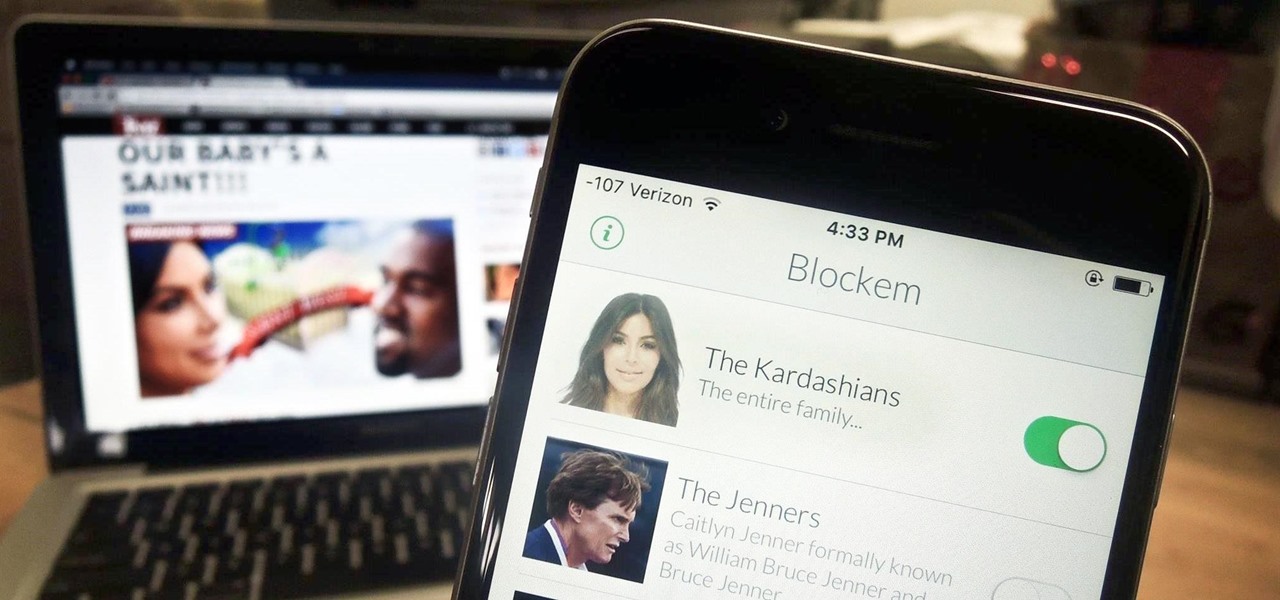
Kim Kardashian and Kanye West have fittingly named their second child "Saint," but I'm sure you don't care about that—and neither do I. Unfortunately, regardless of our pop culture interests, we're forced to know these types of stupid facts because the internet is so densely populated with Kardashian-related content that it's impossible to avoid. It's enough to make you puke.

Windows 10 definitely has a sleek and modern look to it, but some of these visual changes have been made at the expense of functionality. For instance, the slider that appears when you click the volume icon in your notification tray now sports a completely minimalist look that lacks the quick link to the full volume mixer from past Windows versions.

When there's a crappy stock app you want to hide, the easiest thing to do is just bury it in the back of a miscellaneous folder. But what if there's an app you want to hide on your home screen that you actually use? For instance, what if you don't want everybody in eyeshot to see what banks you use, or don't want anyone to know about your "dating" apps or porn shortcuts?

What you probably don't know is when you remove a file on your system, it is actually still saved, and not entirely removed. Let me tell you how to get rid of it completely.

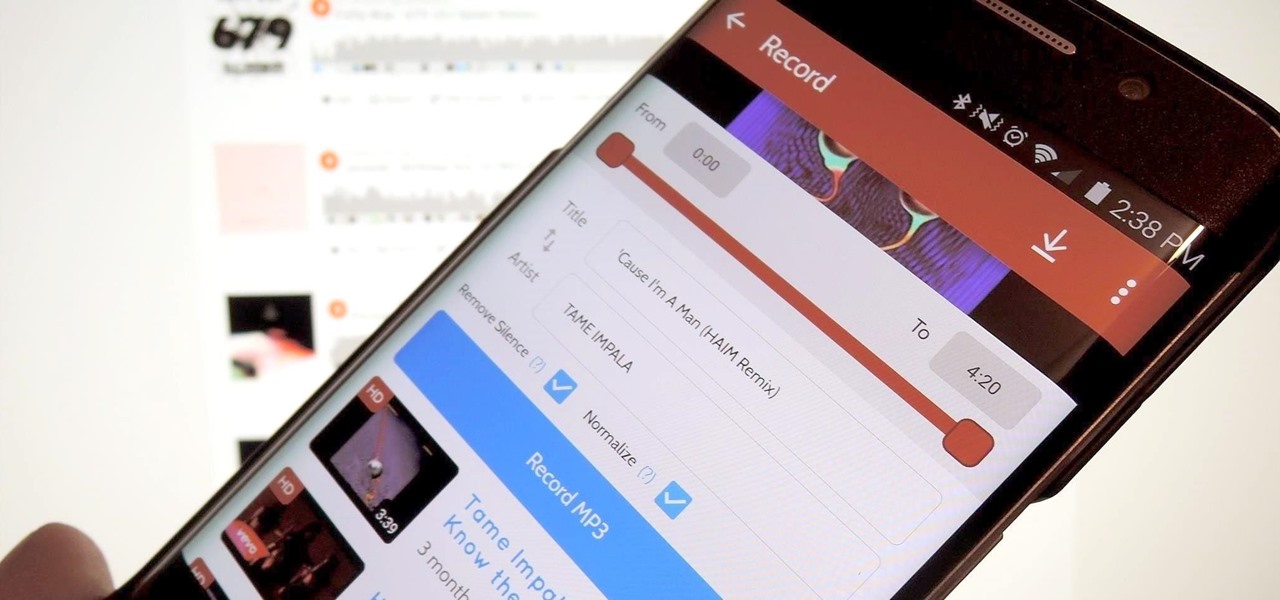
A growing trend for many artists (most recently Kanye West) is to offer exclusive or experimental tracks on music streaming sites like SoundCloud or YouTube before releasing them anywhere else. On rare occasions, some of these great songs never make their way onto an official album, which can be disappointing for die-hard fans who need to download every song available from their favorite artist or band.

Task Manager got revamped quite a bit in modern versions of Windows. First introduced in Windows NT 4.0, it's become pretty popular among more advanced users. In Windows 10, Task Manager is not just a task manager anymore, it's also a system monitor, startup manager, history viewer, user controller, and the list goes on.