The Mac OS's Disc Utility allows for the encryption of files. To open Disc Utility click on the magnifying glass (spot light) up in the top right hand corner, and search for Disc Utility. Click on the first result in the list. Once Disc Utility is open, click on "create a new image" in the top tool bar. A new window will drop down, where you choose what you want to save the new image as. Give it a name, and choose the size you want it to be. Moving down, choose the encryption you want to use ...

Krazyboytx shows viewers how to make self-igniting spell incense! First you need an incense burner and place your incense in this. You then light this mound and it will ignite itself. One should note that this soap is very thick but it will light. First, to make this incense you need to base which is just sawdust. Next, you can add mugwart in this, or whatever choice you would like to add. Next, you should add in some potassium nitrate or a common name for this is 'peter salt'. For a stronger...
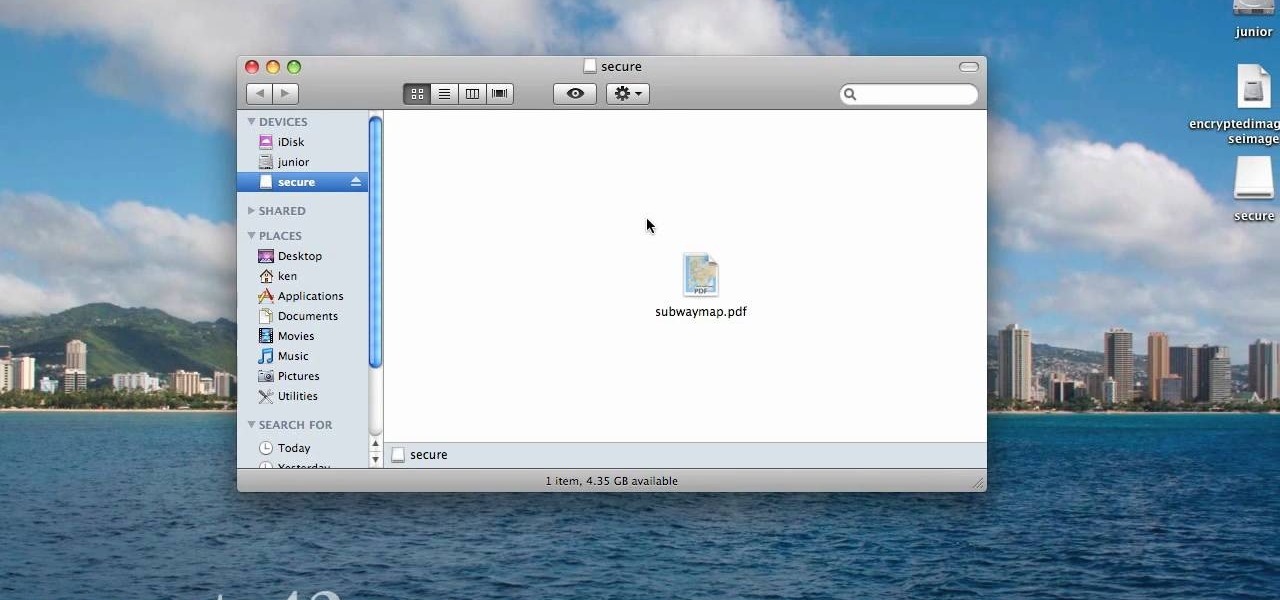
When you are sending any files over a network it is advised to encrypt it so that no can read it even if they get hold of it. You can encrypt files in Mac OS for this purpose. So first take any file or program that you want to encrypt. Open your hard disk and go to the applications. In the applications, under utilities open the Disk Utility program. Using this disk utility program you can create an encrypted disk image. Now this image will act as a disk image or other flash drive, but we can ...
This video describes how to create a new account on Windows 7. In this video it is shown the whole procedure and all you need to know to crate new user account.

Learn to draw Pokémon Oddish with these simple and quick steps. Start your drawing project by placing the Pokémon Oddish name somewhere on the page. Oddish is a round or onion shaped object. Place this basic shape in the center of your space. Add the feet which are shaped like little shovels at the bottom of the Oddish body. Go to the lower central area of the body and add a triangular shaped tongue. For the eyes, use little circles placed proportionately in the upper central area. Place seve...

In this video the instructor shows how to make a simple flash click-through photo gallery with Action Script 3. First the instructor shows a sample gallery that you can make using this tutorial. To do this open a new flash action script 3.0 file. The first thing you have to do now is, in the right hand side change the document size to 750 by 500 pixels and give it a dark back ground color like dark gray. Now open the image that you want to use in this album by dragging them on to your flash w...

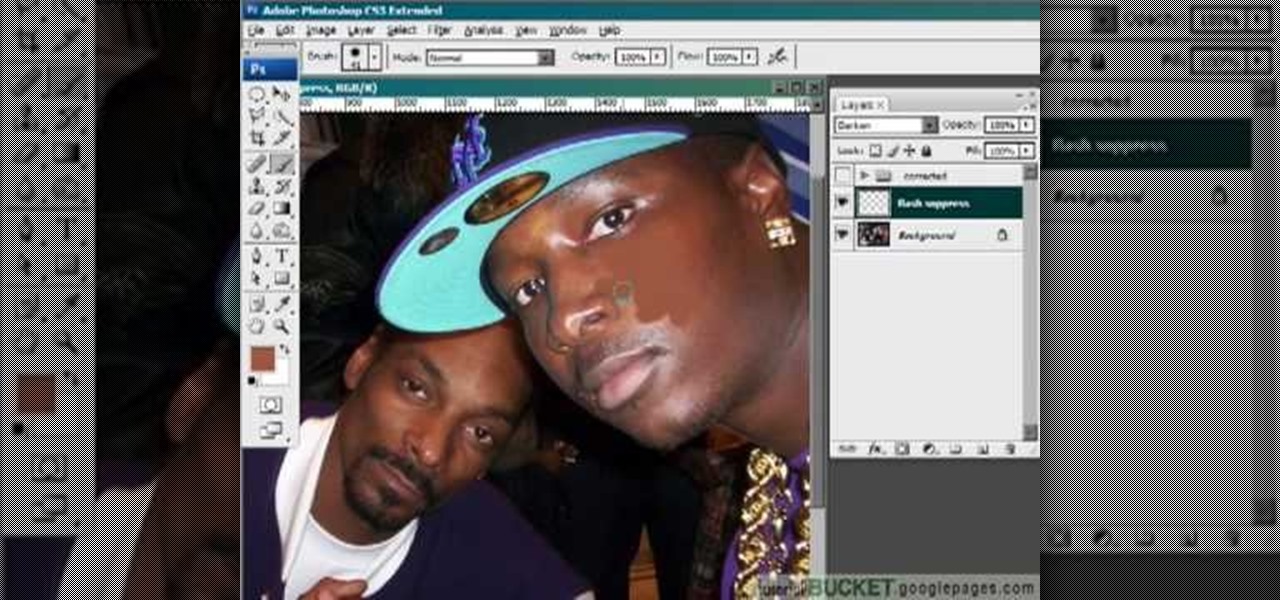
This video gives detailed instructions for removing a hotspot or flash reflection in a photo by using layers and masks. Start by adding a new blank layer and naming it something like Flash Suppress. You will use a special blending mode for this layer called darken. With your paintbrush you will loosely paint out the hotspot, having selected the color tone that you need with the eyedropper tool. Later on you can use layer masks to clean this up. Adjust the opacity of the layer until you have t...

This how-to video is about how to make PS3 controller work on the computer that have either Windows XP, or Vista or 7 as their operating system.

This video explains the method of preparing the Pakistani shaljam or another name called turnip gosht. The main ingredients of this item are 3 or 4 turnip, 500grams of mutton, one medium size of tomato chopped and one onion chopped, ginger garlic paste, one spoon of sugar to add at the end, take a spoon of tamarind powder, garam masala, chilly and coriander powder and some oil and salt. Take some era also take a pot boil it and pour some oil onto it. Put the era and garam masala powder onto i...

Defeat Iustitia in this installment for the Xbox 360 game Bayonetta. In Chapter 11 - The Cardinal Virtue of Justice, attack the tongue. The first part of this fight is against one Ardor and a bunch of smaller enemies. After defeating them you'll see another cinematic and face the boss named Iustitia.

Want to stop accidentally calling people with your BlackBerry device? Want to cure butt-dialing? There's a simple explanation. Best Buy has answers. The Best Buy Mobile team explains how simple it is to lock and to unlock your BlackBerry keyboard to prevent dialing calls from inside your pocket.

Want to forget about always pulling out your credit card to purchase something on your BlackBerry? There's a little application that can do it all for you? But how? Best Buy has answers. The Best Buy Mobile team explains how to use the BlackBerry Wallet application. This application can store personal information such as credit card information and shipping addresses on a secure website for easy access when shopping online.

Battery life is a precious thing on your BlackBerry. You use your phone for all types of tasks, so you need your battery to keep up with your pace. But how? Best Buy has answers. The Best Buy Mobile team explains how you can save battery life by closing applications that are running in the background of your BlackBerry device.

Syncing your bluetooth earpiece to your BlackBerry device can be tricky. But pairing your bluetooth enables BlackBerry with your earpiece is actually quite easy. Best Buy has answers. The Best Buy Mobile team explains how to connect a Bluetooth earpiece to your mobile device. See how to access connections set-up on your Blackberry and also see how to wear a Bluetooth headset.

This is a great playthrough of The Saboteur for the Xbox 360. In the fourth mission in Act 2: Jailbreak, you will need to do the obvious… jailbreak. Once you acquire the papers to enter Area 2, you'll be able to start this mission by visiting the resistance in the Western District. They will charge you with freeing a man named Bryman from a Nazi prison. Grab a car and follow the GPS to the destination. Here you'll find a heavily occupied Nazi area. Bryman's cell is within the courtyard surrou...

You've written the great American novel, and you want to make sure that your story stays yours. Register your copyright and preserve your intellectual rights. In this video, learn how to copyright produced material.

In this video by Dogmantics, dog trainer Emily Larlham goes over how to get rid of the lure to food.

Does your dog bark out of control at objects he finds threatening? Not fear. Dog trainer Emily Larlham of Dogmantics, is here to go over tips on how to calm your dog around objects he or she might find scary.

Dog trainer Emily Larlham from Dogmantics teaches how to paint your pet's portrait without having a background in art. Colors used in this tutorial include Titanium White, French Ultramarine Blue, Burnt Sienna (a brown), Burnt Umber (a dark brown), Alizeran Crimson (a red), Cadmium Yellow, and Cadmium Orange. Other colors that are a good beginners palate include Cadmium Red and Yellow Ochre.

There's plenty of reasons why one would want to convert a webpage to a PDF document. And there's numerous ways on how one can convert that web page (HTML) into a PDF file. Check out this video tutorial on how to convert webpage HTML to PDF on Ubuntu Linux.

Pull off this easy prank, and – without causing any permanent damage – watch your coworker squirm with frustration.

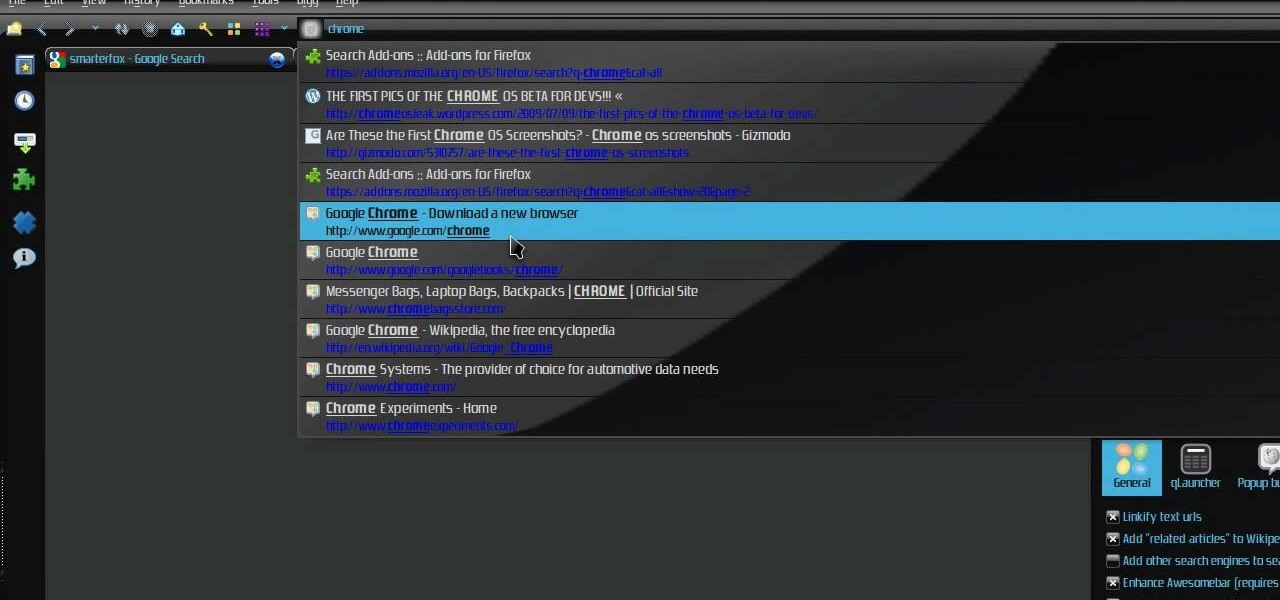
Check out this video tutorial on how to make your Firefox smarter using SmarterFox. Wikipedia sidebar SmarterFox adds a "related articles" sidebar to the left side of Wikipedia.

Do you have coworkers who use the hunt-and-peck method of typing? This trick is guaranteed to drive them completely bonkers.

New to Windows? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to protect Windows from viruses without an antivirus software.

Learn how to tune your guitar using a Korg tuning box. To accurately tune your guitar, you will first need to locate a correctly tuned instrument to provide a reference note. A piano or electric keyboard will work if one is available. (You have to know the names of the keys to use this method.) Otherwise, you can use the fret board below to get your reference note. We'll use the "Low E" for your reference note.

Everyone remarks upon the hands of the skilled pianist, but even the most dexterous keyboard artist couldn't pull off Schubert without using some fancy footwork.

Check out this episode of Brian Brushwood's Scam School from Revision3 to find out how to pull the best cons, bar scams and magic tricks. It's rare to find a trick that you can actually fool yourself with...and that's exactly what you get with this episode!

Take a lesson in architecture from renowned architect Doug Patt by watching this video tutorial. If you want to learn about drawing and designing, without going to school, Doug's just the teacher. Watch to see how to design and draw like an architect.

Pyramid Head. You've heard the name before. You've saw him in action. Now cosplay as him. This costume could be used for Halloween, cosplay, or just for the hell of it. Pyramid Head is a fictional monster from the Silent Hill video game and movie. So watch this four-part video tutorial to see how to do it. If you can follow these instructions, you could never need another cosplay getup again. Unless you want to try out some anime or manga.

Learn how to do incline calf presses. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do reverse flys on a pec deck. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do dumbbell skull crushers. Presented by Real Jock Gay Fitness Health & Life. Benefits

By now you're probably already an expert at creating cover images for your Facebook Timeline, especially if you've taken advantage of those free Facebook cards that were (and still are) being offered. But just in case you need some help making eye-grabbing cover images, there's a few tools you can try out to streamline the process.

A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).

If you loved The Da Vinci Code by Dan Brown, then listen up— there's been a new discovery found hidden within Leonardo da Vinci's most famous painting— the Mona Lisa.

In this how to video, you will learn how to tag pictures on Facebook. To do this, first open up Facebook and log in to your account. Next, click on a friend's profile page and look for a picture that you may be on. Once you are there, select tag and the click on your face in the picture. From there, type in your name and click okay. Once you are done tagging, click done tagging. You have now successfully tagged yourself in a photo in Facebook. Now when you mouse over your face, a square will ...

In this tutorial, we learn how to integrate Facebook chat with iChat. To do this, go into your Facebook account and copy your profile name. Now, go into your iChat account and click on "preferences". Next, click on the "add" button and select "jabber" from the drop down menu. Now, add your account name with "@chat.facebook.com" and type in your Facebook password the same as you would do so in Facebook. Under server options, enter "chat.facebook.com" and the port will be 5212. Now your Faceboo...

This video shows the viewer how to fill in a standard golf score card. The video shows a man filling in a score card with fictitious scores to demonstrate how a card should be filled in correctly. The video also shows how to incorporate a player’s handicap into a scorecard.

You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information inside of plain text, and we can even figure out who's leaking documents online.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.